What is DFU, and how is it different from the recovery mode? How do you switch the device to recovery, DFU or SOS mode, what can you do while in these modes and what do they mean in the context of digital forensics? Can you use DFU to jailbreak the device and perform the extraction if you don’t know the passcode? Read along to find out.
iOS Recovery Mode
The recovery mode is the easiest to explain. According to Apple, you can put your iOS or iPadOS device in recovery mode to restore it using your computer.
The recovery mode comes handy if one of the following situations occurs:
- Your iOS or iPadOS device is locked after multiple unsuccessful unlock attempts and displays the infamous “Connect to iTunes” message. In many cases, connecting the device to iTunes will be unsuccessful because the data connection of the device is blocked with USB restricted mode. If this is the case, you must switch the device to recovery mode and connect to iTunes to restore.
- You forgot the screen lock passcode and want to reset the device to factory settings. Activation lock: following the reset, you’ll have to provide the Apple ID/iCloud password of the device’s Apple ID account.
- The device cannot fully boot; the display is stuck on the Apple logo for several minutes with no progress bar. I have personally seen this multiple times after unsuccessful iOS updates (the latest case being the almost-full iPhone 7 updated from iOS 9 straight to the latest iOS 13.3).
- Your computer doesn’t recognize your device or says it’s in recovery mode, or you see the recovery mode screen.
How to switch the device into recovery mode
The recovery mode is well-documented in “If you can’t update or restore your iPhone, iPad, or iPod touch” (link). Connect the device to a computer with iTunes installed. Perform a force restart of the device by following instructions laid out in “If your screen is black or frozen” (link):
If your screen is black or frozen
If your screen is black or frozen, you might need to force-restart your device. A force-restart won’t erase the content on your device. You can force-restart your device even if the screen is black or the buttons aren’t responding. Follow these steps:
- iPad models with Face ID: Press and quickly release the Volume Up button. Press and quickly release the Volume Down button. Then press and hold the Power button until the device restarts.
- iPhone 8 or later: Press and quickly release the Volume Up button. Press and quickly release the Volume Down button. Then press and hold the Side button until you see the Apple logo.
- iPhone 7, iPhone 7 Plus and iPod touch (7th generation): Press and hold both the Top (or Side) button and the Volume Down buttons until you see the Apple logo.
- iPad with Home button, iPhone 6s or earlier and iPod touch (6th generation) or earlier: Press and hold both the Home and the Top (or Side) buttons until you see the Apple logo.
After following the force-restart instructions, do not release the buttons when you see the Apple logo, wait until the recovery mode screen appears:
- iPad models with Face ID: Press and quickly release the Volume Up button. Press and quickly release the Volume Down button. Press and hold the Top button until your device begins to restart. Continue holding the Top button until your device goes into recovery mode.
- iPhone 8 or later: Press and quickly release the Volume Up button. Press and quickly release the Volume Down button. Then, press and hold the Side button until you see the recovery mode screen.
- iPhone 7, iPhone 7 Plus, and iPod touch (7th generation): Press and hold the Top (or Side) and Volume Down buttons at the same time. Keep holding them until you see the recovery mode screen.
- iPad with Home button, iPhone 6s or earlier, and iPod touch (6th generation) or earlier: Press and hold both the Home and the Top (or Side) buttons at the same time. Keep holding them until you see the recovery mode screen.
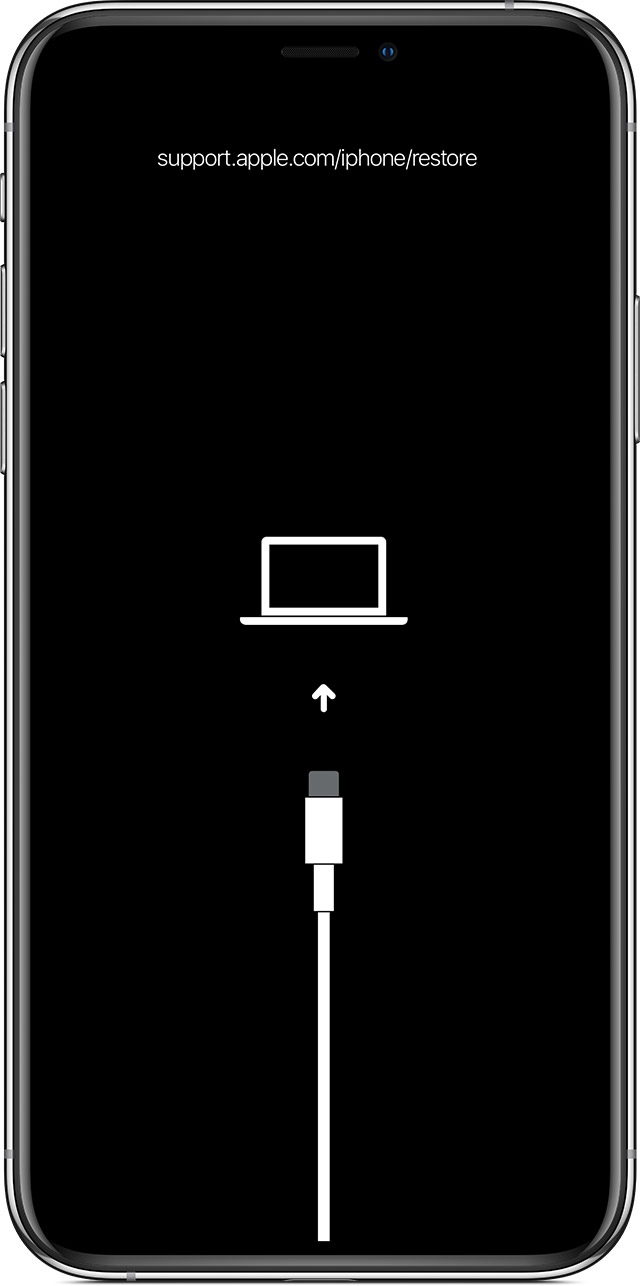
(source)
How to use the recovery mode
We know of several viable usage scenarios for the recovery mode.
- Reinstall iOS (if the iOS device is running the latest version), perform an in-place update or switch from a beta version of iOS to the current release version using the iTunes app. In this scenario, the data is preserved.
- Restore the device. This is what you want if you forgot the passcode. The passcode will be removed and USB restrictions disabled, but the data will be already erased by that time. Mind the activation lock.
- Perform a (limited) forensic extraction through recovery mode. You’ll need a reasonably up to date version of iOS Forensic Toolkit (EIFT 4.10 or newer).
Information available in recovery mode
When performing a forensic extraction of a device running in the recovery mode, note that only a very limited set of data will be available. The following information is available:
Device Model: iPhone8,1
Model: n71map
ECID: XXXXXXXXXXXXXXXX
Serial Number: XXXXXXXXXXX
IMEI: XXXXXXXXXXXXXXX
MODE: Recovery
The Recovery mode may return the following information:
- Device model: two representations of the device model, e.g. iPhone7,2 (n61ap), iPhone10,6 (d221ap) etc.
- ECID (UCID): XXXXXXXXXXXXXXXX. The ECID (Exclusive Chip Identification) or Unique Chip ID is an identifier unique to every unit, or more accurately, to every SoC.
- Serial number: XXXXXXXXXXX (or N/A)
- IMEI: XXXXXXXXXXXXXXX (or N/A). Note that we have not seen IMEI information on any of our test devices, with or without a SIM card.
- Mode: Recovery
How to exit recovery mode
The procedure for leaving the recovery mode is different for different devices. In general, you’ll use the following steps:
- Unplug the USB cable.
- Hold down the sleep/wake button or side button depending on device model until the device turns off.
- Either keep holding the button combination or release and hold it down again until the Apple logo appears.
- Let go of the buttons and let the device start up.
This is the Apple-recommended procedure for exiting the recovery mode:
- iPhone 6s and earlier, Touch ID equipped iPads: hold the Home button and the Lock button until the device reboots.
- iPhone 7 and iPhone 7 Plus: hold down the Side button and Volume Down button until the device reboots.
- iPhone 8 and newer: click the Volume Up button, then click the Volume Down button, then hold down the Side button until the device reboots.
Forensic implications of iOS recovery mode
The recovery mode has a positive yet limited value for mobile forensic specialists.
- Enables obtaining device information without a passcode.
- Allows bypassing the USB restricted mode (albeit accessing limited amounts of information).
- For newer iOS devices (A12 and newer), returns more information compared to the DFU mode.
Interestingly, when users install the checkra1n jailbreak from the device GUI, the jailbreak first switches the device into recovery (unlike DFU, the recovery mode is available through the API). Only after the device is switched to recovery, the jailbreak prompts for a switch to DFU and displays step-by-step instructions and timings. Alternatively, the jailbreak can be installed from the command line, which will bypass the intermediary recovery mode.
iOS DFU Mode
The undocumented DFU stands for “Device Firmware Upgrade”. Unlike the recovery mode, which is designed with an ordinary user in mind, the DFU mode was never intended for the public. There is no documentation about DFU anywhere in Apple Knowledge Base. Entering the DFU more involves a complicated sequence of pressing, holding and releasing buttons with precise timings. Wrong timings during any of the multiple steps would reboot the device instead of switching it to DFU. Finally, there is no on-screen indication of DFU mode. If the device is successfully switched to DFU, the display remains black. Entering DFU mode can be difficult even for experts.
DFU is part of the bootrom, which is burned into the hardware. On A7 through A11 devices, a vulnerability has been discovered allowing to bypass SecureROM protection and jailbreak the device via DFU mode. More in our blog: BFU Extraction: Forensic Analysis of Locked and Disabled iPhones.
Steps for entering DFU mode differ between devices. Some devices have several different methods to invoke DFU, making it even more confusing. The differences in procedures may be severe between device generations. Since no official instructions are available, we have to rely on third-party sources for information.
Note: the device screen will be completely black while in DFU mode. The iPhone Wiki explains steps required to enter the DFU mode in a dedicated article. According to the article, this is how you enter DFU mode on the different device models. If you are more of a visual learner, check out this link with video tutorials instead: How To Put An iPhone In DFU Mode, The Apple Way
Apple TV
- Plug the device into your computer using a USB cable.
- Force the device to reboot by holding down the “Menu” and “Down” buttons simultaneously for 6-7 seconds.
- Press “Menu” and “Play” simultaneously right after reboot, until a message pops up in iTunes, saying that it has detected an Apple TV in Recovery Mode.
A9 and older devices (iPad other than the ones listed below, iPhone 6s and below, iPhone SE and iPod touch 6 and below)
- Connect the device to a computer using a USB cable.
- Hold down both the Home button and Lock button.
- After 8 seconds, release the Lock button while continuing to hold down the Home button.
- If the Apple logo appears, the Lock button was held down for too long.
- Nothing will be displayed on the screen when the device is in DFU mode. If open, iTunes will alert you that a device was detected in recovery mode.
- If your device shows a screen telling you to connect the device to iTunes, retry these steps.
Alternative method 1:
- Hold the Lock Button for 3 seconds
- Continue holding the Lock button and also hold the Home button (15 seconds)
- Release the Lock button while continuing to hold the Home button (10 seconds)
- Your device should enter DFU mode
Alternative method 2:
- Connect the device to your computer and launch iTunes. Turn the device off.
- Hold down the Lock button and Home button together for exactly 10 seconds, then release the Lock button.
- Continue holding the Home button until iTunes on your computer displays a message that a device in recovery mode has been detected. The device screen will remain completely black.
A10 devices (iPhone 7 and iPhone 7 Plus, iPad 2018, iPod touch 7)
- Connect the device to a computer using a USB cable.
- Hold down both the Side button and Volume Down button.
- After 8 seconds, release the Side button while continuing to hold down the Volume Down button.
- If the Apple logo appears, the Side button was held down for too long.
- Nothing will be displayed on the screen when the device is in DFU mode. If open, iTunes will alert you that a device was detected in recovery mode.
- If your device shows a screen telling you to connect the device to iTunes, retry these steps.
A11 and newer devices (iPhone 8 and above, including the iPhone Xr, Xs and Xs Max; iPad Pro 2018, iPad Air 2019, iPad Mini 2019)
- Connect the device to a computer using a USB cable.
- Quick-press the Volume Up button
- Quick-press the Volume Down button
- Hold down the Side button until the screen goes black, then hold down both the Side button and Volume Down button.
- After 5 seconds, release the Side button while continuing to hold down the Volume Down button.
- If the Apple logo appears, the Side button was held down for too long.
- Nothing will be displayed on the screen when the device is in DFU mode. If open, iTunes will alert you that a device was detected in recovery mode.
- If your device shows a screen telling you to connect the device to iTunes, retry these steps.
If your device shows a screen telling you to connect the device to iTunes, retry these steps.
Sources: iphonewiki and other third-party sources
Information available in DFU mode
The DFU mode returns even less information compared to the recovery mode.
Device Model: iPhone8,1
Model: n71map
ECID: XXXXXXXXXXXXXXXX
Serial Number: N/A
IMEI: N/A
MODE: DFU
To obtain this information, use iOS Forensic Toolkit 4.10 or newer.
- Device model: two representations of the device model, e.g. iPhone7,2 (n61ap), iPhone10,6 (d221ap) etc.
- ECID/Unique Chip ID: XXXXXXXXXXXXXXXX
- Serial number: not available in DFU mode
- IMEI: not available in DFU mode
- Mode: DFU
- Exiting DFU Mode
How to exit DFU mode
The process of exiting DFU mode is also different across devices.
For devices with a physical Home button (up to and including iPhone 6s and iPhone SE): hold the Home button and the Lock button until the device reboots.
For iPhone 7 and iPhone 7 Plus: hold down the Side button and Volume Down button until the device reboots.
For iPhone 8 and iPhone 8 Plus, iPhone X: click the Volume Up button, then click the Volume Down button, then hold down the Side button until the device reboots.
Forensic implications of DFU mode
The DFU mode may have a huge value for mobile forensic specialists depending on the device model. iPhone, iPod Touch and iPad devices based on A5 through A11 generations of Apple processors (iPhone generations from iPhone 4s through iPhone 8, 8 Plus and iPhone X, as well as the corresponding iPad models) have a non-patchable, hardware-based bootrom vulnerability. This vulnerability allows installing a jailbreak on affected devices regardless of the version of iOS that is installed. This also makes it possible to extract a limited but still significant amounts of data through DFU mode without knowing or breaking the passcode.
- All devices: enables obtaining device information without a passcode
- All devices: allows bypassing the USB restricted mode (albeit accessing limited amounts of information)
- Vulnerable iOS devices (A5 through A11 generations): returns significantly more information compared to the recovery mode
- Criminals exploit the vulnerability to remove Activation Lock from vulnerable devices (A5 through A11 generations) running older versions of iOS. Reportedly, this vulnerability has been fixed by Apple in iOS 13.3; however, considering the nature of the exploit, this functionality may reappear.
The following information is extractable from vulnerable iOS devices:
- Limited file system extraction: the list of installed applications, some Wallet data, the list of Wi-Fi connections, some media files, notifications (these may contain some chat messages and other useful data), and many location points.
- Keychain records with kSecAttrAccessibleAlways and kSecAttributeAccessibleAlwaysThisDeviceOnly
- Oxygen Forensic Detective additionally processes files such as /private/var/wireless/Library/Databases/DataUsage.sqlite (apps’ network activities), /private/var/preferences/ (network interfaces) or /private/var/mobile/Library/Voicemail/ (voicemail messages) to display even more information.
More information in BFU Extraction: Forensic Analysis of Locked and Disabled iPhones and iOS Device Acquisition with checkra1n Jailbreak.
Differences between DFU and recovery modes
While both DFU and recovery are designed to fulfil essentially the same goal of recovering a non-bootable device by flashing known working firmware, they are very different in the way they work.
The recovery mode boots into the bootloader (iBoot), and works by issuing commands through the bootloader. The bootloader is part of the operating system, and can be flashed, updated or patched if there are any vulnerabilities discovered. The recovery mode will only accept signed firmware images, so going back to firmware that is no longer signed by Apple is not possible. While the device is in recovery mode, the user gets a clear visible indication on the device:
DFU or Device Firmware Upgrade, on the other hand, allows restoring devices from any state, including devices with corrupted bootloader. DFU does not operate through a software-upgradeable bootloader. Instead, DFU is burned into the hardware as part SecureROM. DFU cannot be updated, patched or disabled. As a result, the bootrom vulnerability and the corresponding checkm8 exploit cannot be patched by Apple, allowing experts extract certain data from affected devices while bypassing passcode protection and USB restrictions.
DFU will also accept only signed firmware packages. As long as a package is still signed by Apple, the user can upgrade and downgrade firmware at will since there is no downgrade protection in DFU. There is no indication on the device that the device is in DFU mode. During DFU interfacing, the device screen remains black.
The recovery mode was designed for end users and Apple facilities, while the DFU mode was never meant for the end user at all. Entering the recovery mode is easy; any reasonably experienced user can follow the instructions. Entering the DFU mode is not only significantly trickier, but requires precise timings. Hold a button one second too long, and the device simply reboots instead of entering DFU.
The S.O.S. mode
The third and final special mode we’re about to discuss today is the S.O.S. mode. The S.O.S. mode can be manually invoked by the user while the device is running. Apple has a comprehensive description of S.O.S. mode in Use Emergency SOS on your iPhone.
Activating S.O.S. mode
On newer devices without the Home button (as well as the iPhone 8 and 8 Plus), the S.O.S. mode is activated in exactly the same way as the power-off sequence. Users press and hold one of the volume buttons and the side button. The power off/emergency screen appears.
On older devices, the S.O.S. mode is activated by rapidly pressing the side (or top) button five times. The Emergency SOS slider will appear. Users in India only need to press the button three times, after which the iPhone automatically makes an emergency call.
“If you use the Emergency SOS shortcut, you need to enter your passcode to re-enable Touch ID, even if you don’t complete a call to emergency services.” (Source: Use Emergency SOS on your iPhone)
How to exit S.O.S. mode
To exit the S.O.S. mode, users tap on the “Cancel” icon. The device will prompt for the passcode (biometric identification methods are disabled). Alternatively, one can slide the Power off slider to the right to switch off the device.
Forensic implications of S.O.S. mode
Once invoked, the S.O.S. mode has the following forensic implications.
- All biometric authentication methods (Touch ID and Face ID) are disabled. The device must be unlocked with a passcode.
- Data transmission on USB port is switched off (USB restricted mode is immediately activated). This makes traditional acquisition efforts fruitless, potentially affecting passcode recovery solutions offered by companies such as Cellebrite and GrayShift.



