
Today’s smartphones collect overwhelming amounts of data about the user’s daily activities. Smartphones track users’ location and record the number of steps they walked, save pictures and videos they take and every message they send or receive. Users trust smartphones with their passwords and login credentials to social networks, e-commerce and other Web sites. It is hard to imagine one’s daily life without calendars and reminders, notes and browser favorites and many other bits and pieces of information we entrust our smartphones. All of those bits and pieces, and much more, are collected from the iPhone and stored in the cloud. While Apple claims secure encryption for all of the cloud data, the company readily provides some information to the law enforcement when presented with a legal request – but refuses to give away some of the most important bits of data. In this article we’ll cover the types of data that Apple does and does not deliver when served with a government request or while processing the user’s privacy request.
What’s Stored in iCloud
Apple uses iCloud as an all-in-one cloud backup, cloud storage and cloud synchronization solution for the user of iOS, iPasOS and macOS devices. iOS 12 and 13 can store the following types of data in the user’s iCloud account:
iCloud backups
iCloud backups contain a lot of data from the iPhone, which includes device settings and home screen icons, the list of installed apps and individual apps’ private data (if allowed by the app developer).
The content of iCloud backups is mostly exclusive. Many types of data that are synchronized with iCloud will be excluded from cloud backups. For example, if the user enables the iCloud Photo Library, pictures and videos will synchronize to iCloud and will not be included in iCloud backups. The same is true for many other categories. Here’s what Apple says in What does iCloud back up?
Your iPhone, iPad, and iPod touch backup only include information and settings stored on your device. It doesn’t include information already stored in iCloud, like Contacts, Calendars, Bookmarks, Mail, Notes, Voice Memos, shared photos, iCloud Photos, Health data, call history, and files you store in iCloud Drive.
In iOS 13, iCloud backups do not include any of the following:
- Keychain *
- Health data
- Home data
- iCloud Photos **
- Messages **
- Call logs
- Safari history
* While the keychain is still physically included, records marked as ThisDeviceOnly are encrypted with a device-specific key and can only be restored onto the same physical device they were saved from.
** Photos and Messages are not included if (and only if) the iCloud sync of those categories is not enabled in device settings.
Synchronized data
iOS allows synchronizing many types of data with the user’s iCloud account. While users can enable or disable the sync for some of the data categories (as defined in Change your iCloud feature settings), some other types of data (e.g. the call log) are always synchronized unless the user disables the iCloud Drive feature entirely.
The following types of data are synchronized to iCloud:
- Photos
- Safari History & Bookmarks
- Calendars
- Contacts
- Find My (Devices & People)
- Notes
- Reminders
- Siri Shortcuts
- Voice Memos
- Wallet passes
- iCloud Mail
- Maps
- Clips
- Data covered by the iCloud Drive category (e.g. Call logs)
Files
There are two distinct data types that fall under the “Files” category.
The first category includes files the user stores in their iCloud Drive (e.g. by using the iOS Files app). These files are user-accessible, and can be downloaded by using the iCloud Drive app on a Mac or Windows PC.
The second category includes files stored by system apps (e.g. downloaded books and documents in the Books app) and third-party apps (e.g. stand-alone WhatsApp backups, game saves etc.) While large amounts of data may accumulate under this category, users have no direct access to these files. For example, any files stored by third-party apps are only displayed as toggles in the iCloud | Apps section. The only control the user has over these files is the ability to disable sync (and remove stored files) for a certain app.
End-to-end encrypted data
Apple uses end-to-end encryption to secure sensitive types of data such as the users’ passwords, Health data or credit card information. The data is secured with an encryption key derived from some device-specific information and the user’s screen lock passcode. Users must enroll their devices into the trusted circle in order to enable the sharing of end-to-end encrypted data.
The following types of data are covered by end-to-end encryption as per iCloud security overview:
- Home data
- Health data (iOS 12 or later) *
- iCloud Keychain (includes saved accounts and passwords)
- Payment information
- QuickType Keyboard learned vocabulary (iOS 11 or later)
- Screen Time password and data
- Siri information
- Wi-Fi passwords
- Messages in iCloud **
* iOS 11 devices synchronize Health data as a regular data category without using end-to-end encryption. According to Apple, “End-to-end encryption for Health data requires iOS 12 or later and two-factor authentication. Otherwise, your data is still encrypted in storage and transmission but is not encrypted end-to-end. After you turn on two-factor authentication and update iOS, your Health data is migrated to end-to-end encryption.”
** According to Apple, “Messages in iCloud also uses end-to-end encryption. If you have iCloud Backup turned on, your backup includes a copy of the key protecting your Messages. This ensures you can recover your Messages if you lose access to iCloud Keychain and your trusted devices. When you turn off iCloud Backup, a new key is generated on your device to protect future messages and isn’t stored by Apple.” Since iOS 13, Apple no longer stores Messages in iCloud backups if the user activates Messages in iCloud.
What Apple Provides When Serving Government Requests
Apple discloses certain types of information when serving a valid government request. This data typically includes information that falls into iCloud backups, Synchronized data and Files categories.
When serving government requests, Apple also delivers iCloud backups. End users exercising their rights under the European Data Protection Directive (EDPR) or requesting their personal data via Apple’s Data & Privacy portal do not receive a copy of their iCloud backups.
The following principles apply when Apple serves government requests: https://www.apple.com/privacy/government-information-requests/; of particular interest are the following excerpts:
Apple will notify customers/users when their Apple account information is being sought in response to a valid legal request from government or law enforcement, except where providing notice is explicitly prohibited by the valid legal request, by a court order Apple receives, by applicable law or where Apple, in its sole discretion, believes that providing notice creates a risk of injury or death to an identifiable individual, in situations where the case relates to child endangerment, or where notice is not applicable to the underlying facts of the case, or where Apple reasonably considers that to do so would likely pervert the course of justice or prejudice the administration of justice.
The second category includes files stored by system apps (e.g. downloaded books and documents in the Books app) and third-party apps (e.g. stand-alone WhatsApp backups, game saves etc.) While large amounts of data may accumulate under this category, users have no direct access to these files. For example, any files stored by third-party apps are only displayed as toggles in the iCloud – Apps section. The only control the user has over these files is the ability to disable sync (and remove stored files) for a certain app.
Apple defines information provided to the LE as follows:
iCloud stores content for the services that the subscriber has elected to maintain in the account while the subscriber’s account remains active. Apple does not retain deleted content once it is cleared from Apple’s servers. iCloud content may include email, stored photos, documents, contacts, calendars, bookmarks, Safari browsing history, Maps Search History, Messages and iOS device backups. iOS device backups may include photos and videos in the Camera Roll, device settings, app data, iMessage, Business Chat, SMS, and MMS messages and voicemail. All iCloud content data stored by Apple is encrypted at the location of the server. When third-party vendors are used to store data, Apple never gives them the keys. Apple retains the encryption keys in its U.S. data centres.
While Apple correctly claims that it does not keep deleted content once it is cleared from Apple’s servers, we have found that, in many cases, some content may still be available on Apple servers. As a result, tools such as Elcomsoft Phone Breaker can access and download such content.
Additionally, Apple does not explicitly mention certain types of data such as the phone-to-cloud communication logs. These logs record the phone’s dynamic IP address and store records going back some 28 days.
What Apple Provides When Serving Privacy Requests
Apple is committed to disclosing information to end users according to the European Data Protection Directive (EDPR) or serving a request for personal data submitted via Apple’s Data & Privacy portal. Users can request a download of a copy of their data from Apple apps and services. This, according to Apple, may include purchase or app usage history and the data users store with Apple, such as calendars, photos or documents. Below is the list of information disclosed by Apple:
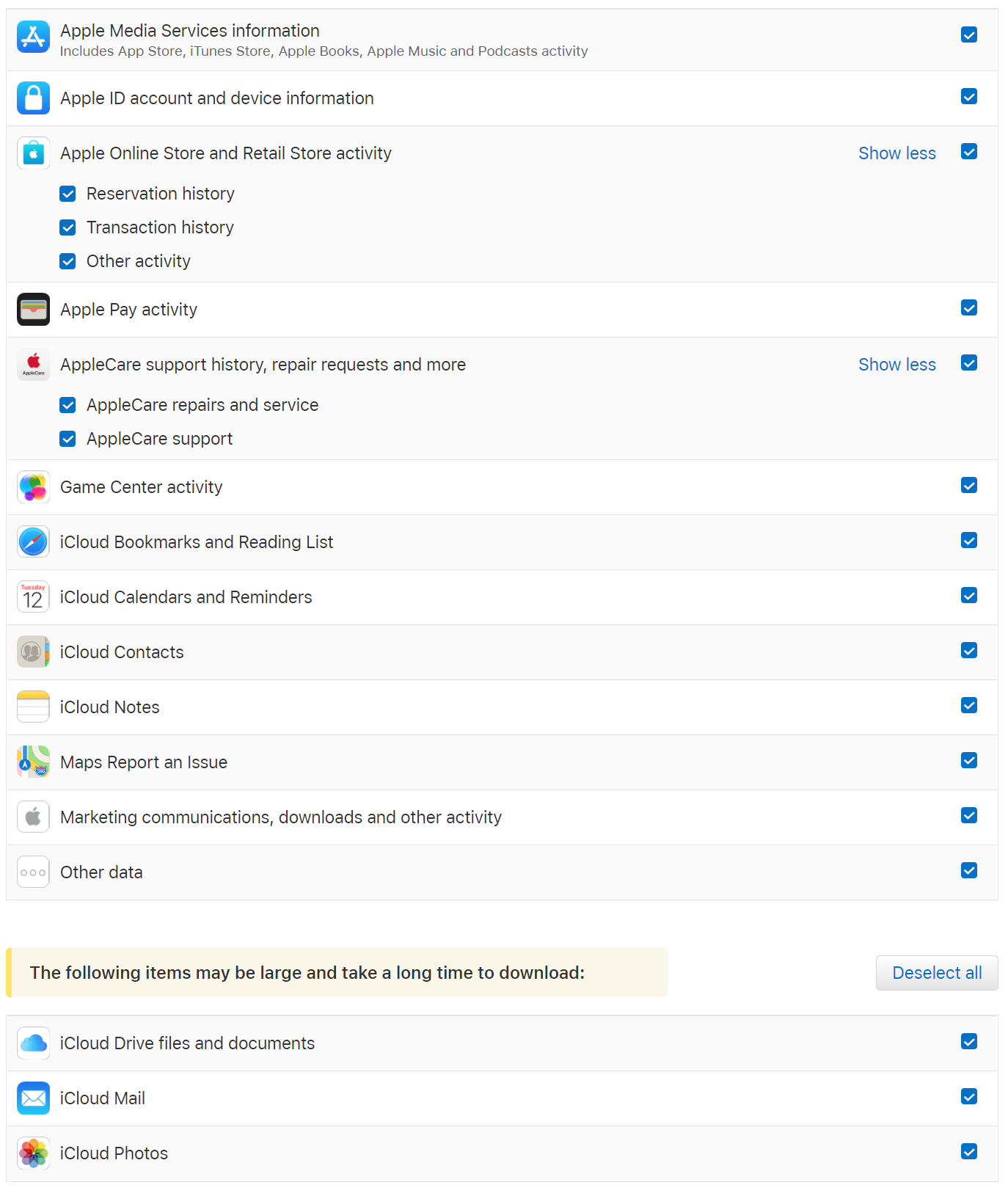
Note: iCloud backups are only provided when Apple serves government requests. End users exercising their rights under the European Data Protection Directive (EDPR) or requesting their personal data via Apple’s Data & Privacy portal do not receive a copy of their iCloud backups.
What Apple Does Not Provide
Any information that falls under the End-to-end encrypted data category as defined in the iCloud security overview is never disclosed to the law enforcement. End users may only obtain end-to-end encrypted data by setting up a compatible Apple device and typing a screen lock passcode of their past device.
Obtaining End-to-End Encrypted Data
Since Apple refuses to provide legal access to any of the data the company protects with end-to-end encryption, experts must use third-party tools to extract this information from iCloud. Elcomsoft Phone Breaker is one of the few tools on the market that can touch these encrypted categories. Elcomsoft Phone Breaker can extract the iCloud backups, files and synchronized data. In addition, the tool can download and decrypt the following types of end-to-end encrypted data:
- iCloud Keychain
- Health
- Messages in iCloud
- Screen Time password
- FileVault2 recovery token
In order to access end-to-end encrypted data, the following information is required:
- The user’s Apple ID and password
- A valid, non-expired one-time code to pass Two-Factor Authentication
- The user’s screen lock passcode or system password to any current or past device enrolled in the trusted circle
More information:
Conclusion
In this article, we described the discrepancy between the data Apple collects from its users and stores on its servers, and the data the company gives away to the law enforcement when serving a government request. Some of the most essential categories are not disclosed, particularly the user’s passwords (iCloud Keychain), text messages and iMessages (Messages in iCloud), the user’s physical activity logs (Health), device usage patterns (Screen Time) and Home data. Most of this information can be only accessed by using third-party tools such as Elcomsoft Phone Breaker, and only if the complete set of authentication credentials (the login and password, 2FA code and screen lock/system password) are known.



