Introduction to BitLocker: Protecting Your System Disk
January 20th, 2020 by Oleg Afonin
Category: «Security»
If you are a Windows user and ever considered protecting your data with full-disk encryption, you have probably heard about BitLocker. BitLocker is Microsoft’s implementation of full-disk encryption that is built into many versions of Windows. You maybe even using BitLocker without realizing that you do – for example, if you have a Surface or a similar thin-and-light Windows device. At the same time, BitLocker encryption is not available by default on desktops if you are using the Home edition of Windows 10. Activating BitLocker on your system disk can be tricky and may not work right away even if your Windows edition supports it. In this article, we are offering an introduction to BitLocker encryption. We’ll detail the types of threats BitLocker can effectively protect your data against, and the type of threats against which BitLocker is useless. Finally, we’ll describe how to activate BitLocker on systems that don’t meet Microsoft’s hardware requirements, and evaluate whether it’s worth it or not security-wise.
Threats Covered by BitLocker Encryption
BitLocker encryption is not the be-all and end-all type of protection. While BitLocker securely encrypts your data with industry-standard AES encryption, it can only protect your data against a set of very specific threats.
BitLocker can effectively protect your data in the following circumstances.
Your hard drive(s) are removed from your computer
If, for any reason, your hard drives (or SSD drives) are removed from your computer, your data is securely protected with a 128-bit encryption key (users requiring higher-level security can specify 256-bit encryption when setting up BitLocker).
How secure is this type of protection? If you’re using TPM protection (more on that later), it is very secure; just as secure as the AES algorithm itself (in layman view, 128-bit or 256-bit encryption are equally strong).
If, however, you have enabled BitLocker on a computer without TPM, then BitLocker encryption will be just as secure as the password you set. For this reason, make sure to specify a reasonably strong, reasonably long and absolutely unique password.
The entire computer is stolen
If your entire computer is stolen, the security of your data depends on the type of BitLocker protection you are using as well as on the strength of your Windows password. The most convenient method is “TPM only” (more on that later); this is the least secure method as well, because your computer will decrypt the hard drive(s) before you sign in to Windows.
If you are using “TPM only” protection policy, anyone who knows your Windows account password (or your Microsoft Account password, if you are using a Microsoft Account as your Windows 10 login) will be able to unlock your data.
TPM + PIN is significantly more secure; in a way, it is practically as secure as a bare hard drive.
If you set up BitLocker protection without a TPM or Intel PTT installed, you’ll be forced to using the password. In this case, the data will be as secure as your password. BitLocker is designed to slow down brute-force attacks, so even a 8-character password can provide secure protection to your data.
Other users on the same computer
If anyone can log in to your computer and access their account, the disk volume has been already decrypted. BitLocker does not protect against peer computer users.
Malware/ransomware and online threats
BitLocker does nothing to protect your data against malware, ransomware or online threats.
In other words, BitLocker is great when protecting your data against the removal of the hard drive(s); it’s perfect if you want to protect your data if you sell or RMA your hard drives. It’s somewhat less effective (depending on your policies) when protecting your data if the entire computer is stolen. This is it; other usage cases are not covered.
System Requirements
Most of us are used to “System Requirements” being a mere formality. This is not the case with BitLocker. In order to protect your boot device with BitLocker, you must be running Windows 10 Professional or higher. Windows 10 Home does not support BitLocker system encryption.
To make things more confusing, Microsoft does support BitLocker device protection even on devices with Windows 10 Home. Effectively, this is the same encryption, just with some limitations. BitLocker device protection is available on thin and light devices (e.g. Microsoft Surface) supporting Connected standby and equipped with solid-state storage. Those devices must be equipped with a TPM2.0 module or Intel PTT technology.
If you are using Windows 10 Professional or higher with TPM2.0 or Intel PTT, you can enable BitLocker straight away. However, most computers are not equipped with TPM modules, and only newer-generation computers (think Intel 8th and 9th Gen motherboards; some higher-end motherboards may support Intel PTT with older processors) support Intel Platform Trust Technology. Intel PTT is not even enabled in BIOS by default; you must manually enable the thing to use it for BitLocker protection.
Here’s how you activate Intel PTT on Gigabyte Z390 boards (latest BIOS):

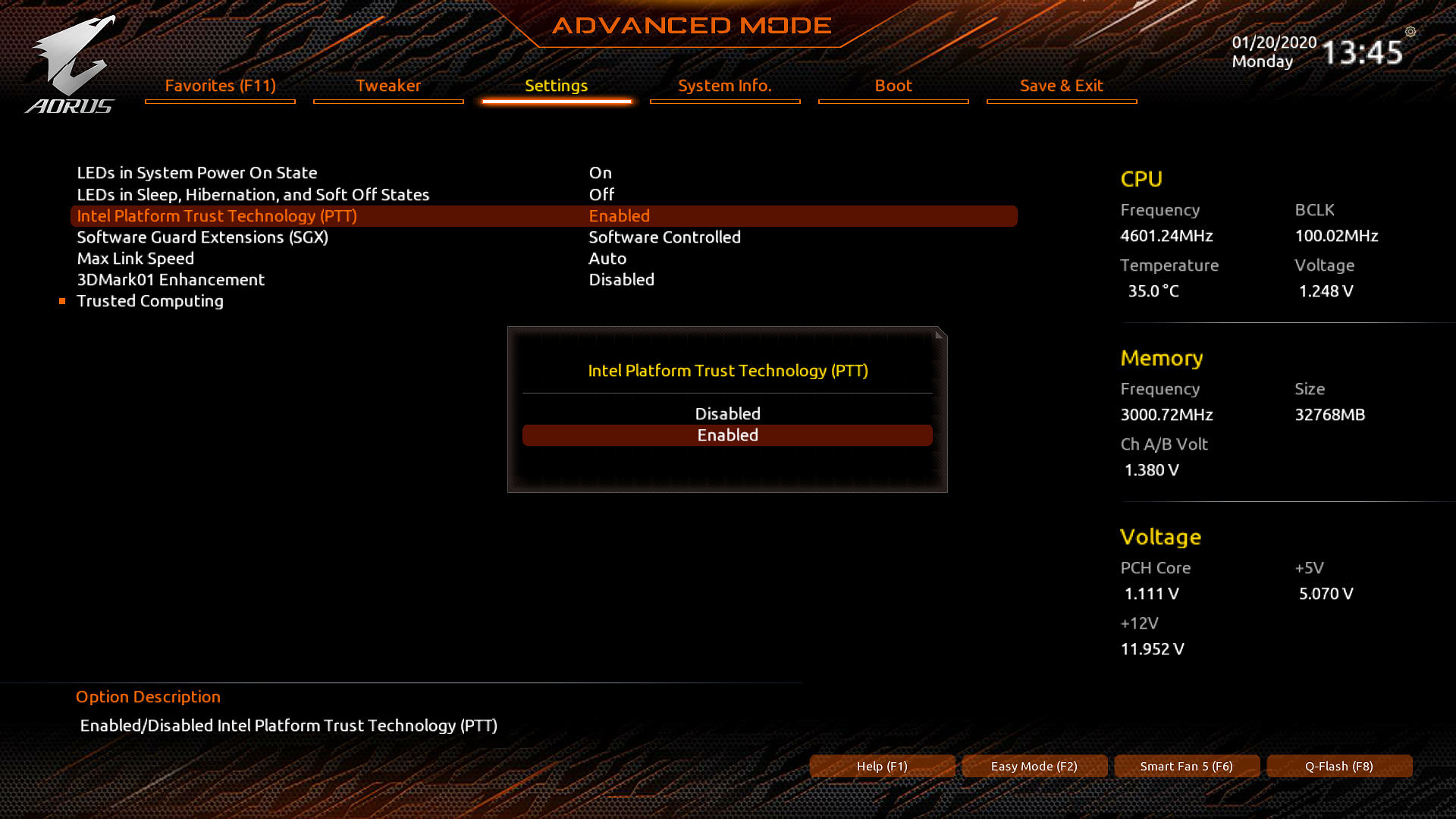
Alternatively, you can perform a Group Policy edit to enable BitLocker without hardware protection modules.
If your computer meets the requirements (namely, the presence of a hardware TPM2.0 module or software-based Intel Platform Trust Technology), enabling BitLocker on your computer can be as easy as opening the Control Panel and launching the BitLocker Drive Encryption applet. Note that not all editions of Windows 10 can use BitLocker protection.

Once you click on “Turn on BitLocker”, Windows will prompt you to create an escrow key (BitLocker Recovery Key). It is highly advisable to do so. On a balance, storing the recovery key in your Microsoft Account might be a good enough option for most home users, while employees will store their recovery keys in their company’s Active Directory. Saving the key into a file or printing it out are also valid options that will provide just as much security as your personal safe box.
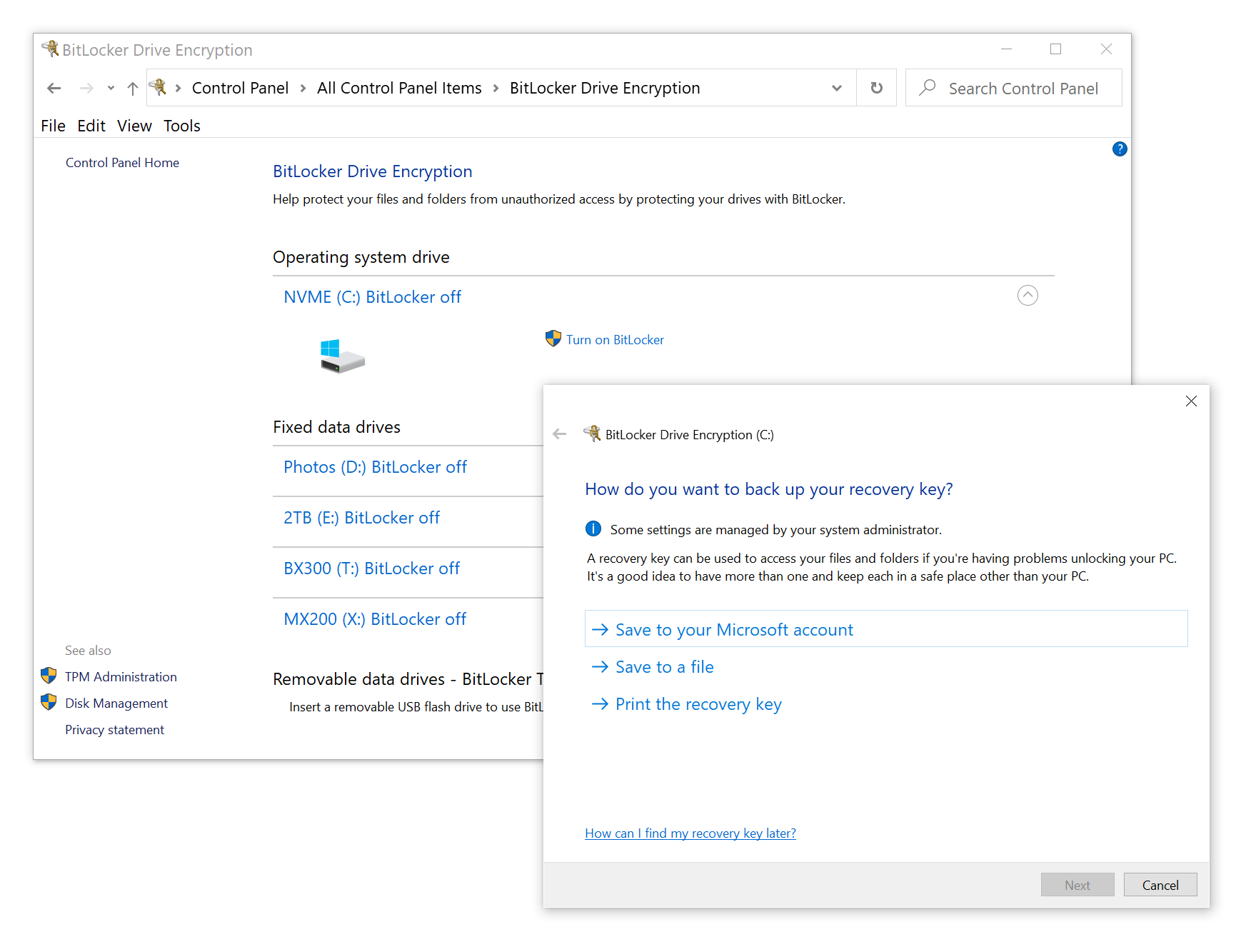
Thin and light devices (such as Windows tablets and ultrabooks) may be protected with device encryption as opposed to BitLocker Drive Encryption. The algorithm is essentially the same; however, the compatibility requirements are different. Device encryption is available for thin and light devices running any Windows 10 edition, while BitLocker Drive Encryption is not available to Windows 10 Home users. If you have data to protect, you’ll need to pay a fee for an in-place upgrade to Windows 10 Professional.
What if you already have Windows 10 Professional but don’t have a hardware TPM2.0 module? If you are using one of the latest boards based on Intel chip sets, you may be able to activate Intel Platform Trust Technology (How To Enable BitLocker With Intel PTT and No TPM For Better Security) or perform the following Group Policy edit to enable BitLocker:
- Open Group Policy Editor (type gpedit.msc in the Windows Search box)
- Open Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives
- Edit the Require additional authentication at startup policy
- Set the policy to Enabled and check Allow BitLocker without a compatible TPM as shown on the screen shot
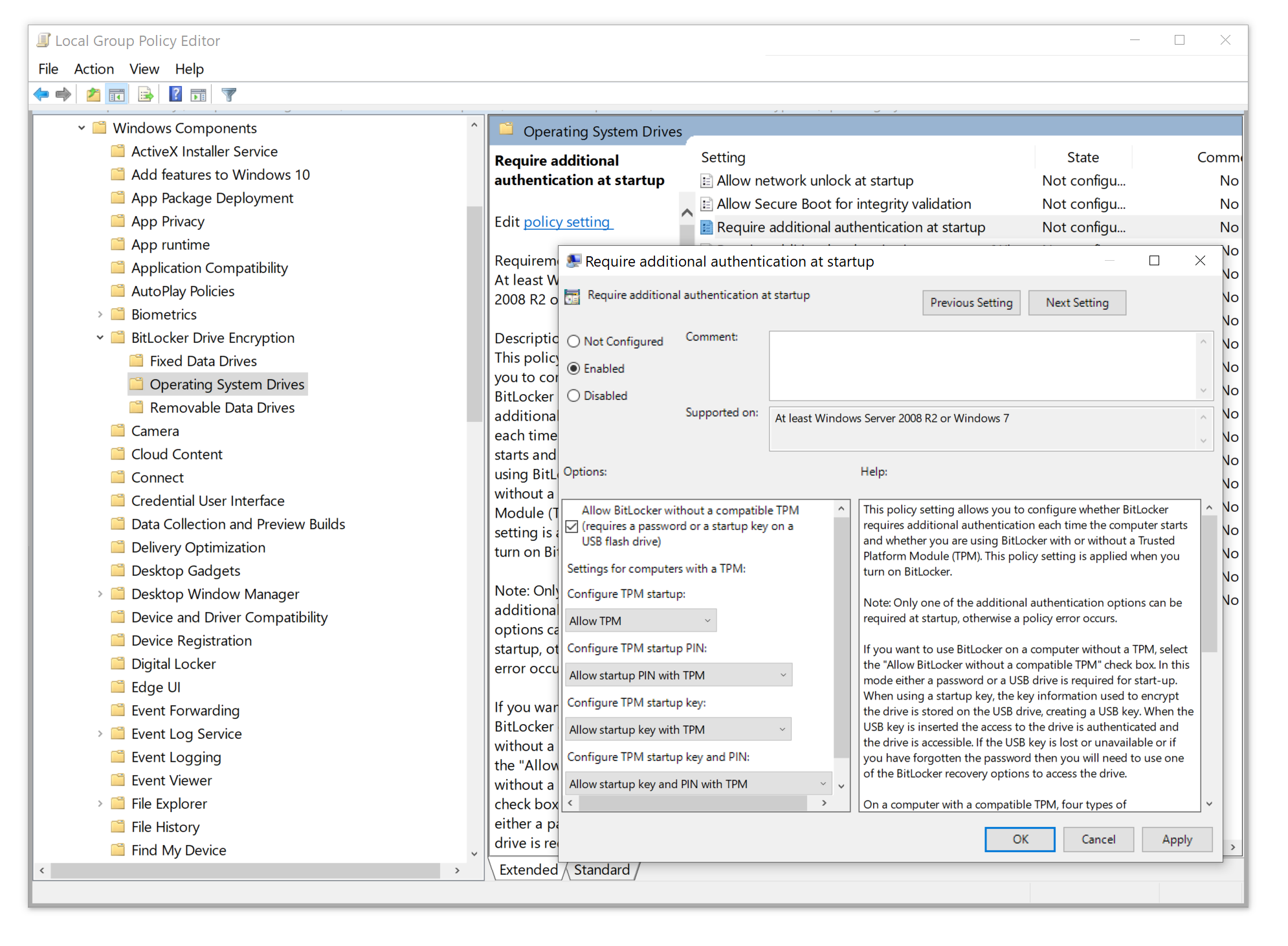
Speaking of the policies, BitLocker supports various methods of authentication, each offering a unique trade-off between security and convenience.
- TPM only. Your system will boot to login prompt; the data will be decrypted with a key stored in the TPM (or Intel PTT) module. This is the most convenient option that effectively protects hard drives, but offers weaker protection if the intruder has access to the whole system (computer with TPM and the hard drive).
- TPM + PIN. In this mode, the TPM module will only release the encryption key if you correctly type the PIN code during pre-boot phase. Even though the PIN code is short, entering the wrong PIN several times makes TPM panic and block access to the encryption key. This option arguably offers the best balance between security and convenience, combining “something that you have” (the TPM module) with “something that you know” (the PIN code). At the same time, this option may not be convenient in multi-user environments.
- TPM + USB Key. This option requires both the TPM and a USB flash drive (or CCID smartcard) to be present in order for the system to boot.
- TPM + PIN + USB Key. Just as the name suggests, this option requires all three of the TPM, PIN code and USB key/smartcard in order to boot your computer. While this is probably the most secure option, the additional security benefits are hardly worth it compared to the TPM + PIN option if you consider the reduced convenience and reliability (you’ll have to use the recovery key if a USB key or smart card gets lost or corrupted).
- USB Key. This option is only recommended if your computer is not equipped with a TPM module and does not support the Intel PTT.
- Password only. Just like the previous option, “password only” authentication should only be used if no TPM or Intel PTT is available. Note that the “password” option is different from the “PIN” as there is no enforceable limit on the number of password attempts without a TPM, which allows a brute-force attack on the password.
Advanced users and system administrators can refer to BitLocker Group Policy settings in Microsoft Knowledge Base.
What caveats are there when it comes to securing data against physical extraction? The thing is, while BitLocker is nearly a 100% effective solution for protecting the bare drive, it might not be as secure if the intruder has access to the entire computer with the hard drive installed. Even if your computer is equipped with a TPM2.0/Intel PTT module, Windows will still unlock the encrypted hard drive if Secure Boot conditions are met. This in turn opens numerous vectors of attack that may allow the intruder to intercept the on-the-fly BitLocker encryption key and decrypt the hard drive. These vectors of attack include:
- Making a RAM image of a running computer with BitLocker volume(s) mounted. This can be done via a Thunderbolt attack (Windows, by default, does not disable Thunderbolt DMA access when locked) or a cold boot attack.
- Breaking or extracting your Windows logon password (e.g. extracting from your Google account, your smartphone, or from another computer you have logged in and synced your data to).
- Obtaining your BitLocker Recovery Key from your Microsoft Account or Active Directory.
Advanced users and system administrators can read the following guide to secure their BitLocker volumes: BitLocker recovery guide
Conclusion
Reliable data protection is impossible without protecting your boot device. BitLocker is the perfect choice. It’s secure, convenient and highly configurable, allowing you balance security and convenience to your precise requirements. If you are concerned about security of your data, protecting your boot device with BitLocker is an absolutely mandatory step and the most important security layer.







