Accessing a locked system is always a challenge. Encrypted disks and encrypted virtual machines, encrypted files and passwords are just a few things to mention. In this article we are proposing a straightforward workflow for investigating computers in the field.
Note: you may be able to perform live system analysis if the computer being investigated is turned on. Our scenario assumes that the computer is initially powered off, or powered on and locked/inaccessible.
Pre-requisites
The computer you are about to analyze is powered off. At least one available USB port. You must be able to access the computer’s BIOS/UEFI setup to enable booting from USB media.
The workflow
Using Elcomsoft System Recovery, you will be able to perform a wide range of tasks. We recommend the following workflow on computers without BitLocker protection:
- Prepare ESR bootable USB drive.
- Configure target computer to boot from a USB device.
- Boot target computer to ESR.
- ESR will attempt to collect existing passwords.
- ESR will run a quick recovery attack on the system’s Windows accounts.
- Extract hashes to Windows accounts of interest (if password not discovered in previous step) for subsequent attacks.
- Extract page and hibernation files.
- Search for encrypted disks. If discovered, extract encryption metadata (you will be able to scan page/hibernation files for on the fly encryption keys).
- Search for encrypted virtual machines. If discovered, extract encryption metadata for subsequent password attacks.
- Create forensic disk images for further in-lab analysis.
- Optional: after a risk assessment, perform live analysis by resetting selected account password, booting into the main system and signing in with the newly set password.
Let’s have a closer look at this workflow.
Prepare ESR bootable flash drive
If you don’t have a bootable flash drive, create one by launching Elcomsoft System Recovery setup on your computer (not the computer being investigated) and click through the wizard. You’ll need a reasonably large and reasonably fast flash drive (32GB or larger).
Once the bootable flash drive is created, insert it to the available USB port of the computer you are about to analyze.
Prepare the target computer for booting from the USB drive
Power on the computer being investigated, immediately entering BIOS setup. To enter BIOS, you will typically need to hit the Del key early during the boot stage. On some systems, you may be using the F10, F11, or F12 keys. We’ve also seen the F2 combination open the list of bootable devices; however, this combination is also system-specific.
Enable USB boot
For security reasons, most computers are configured to only boot from internal media. In order to boot from the ESR flash drive, you will need to allow the computer booting from a USB device. In order to do that, locate the appropriate setting in the computer’s BIOS (typically named as “Boot order”), add “USB” to the list of devices the computer is allowed to scan during the boot sequence, and bring that entry to the top of the list (typically using Page Up/Page Down keys).
Boot from the USB device
Save settings and exit BIOS. The computer should start booting from the USB device containing Elcomsoft System Recovery. On some systems, you may be able to select the boot device by hitting the F2 key repeatedly.
Windows account passwords: collect the low hanging fruit
Once Elcomsoft System Recovery is launched, the tool automatically scans the system for available passwords, and runs a fast pre-configured attack that may reveal weak account passwords.
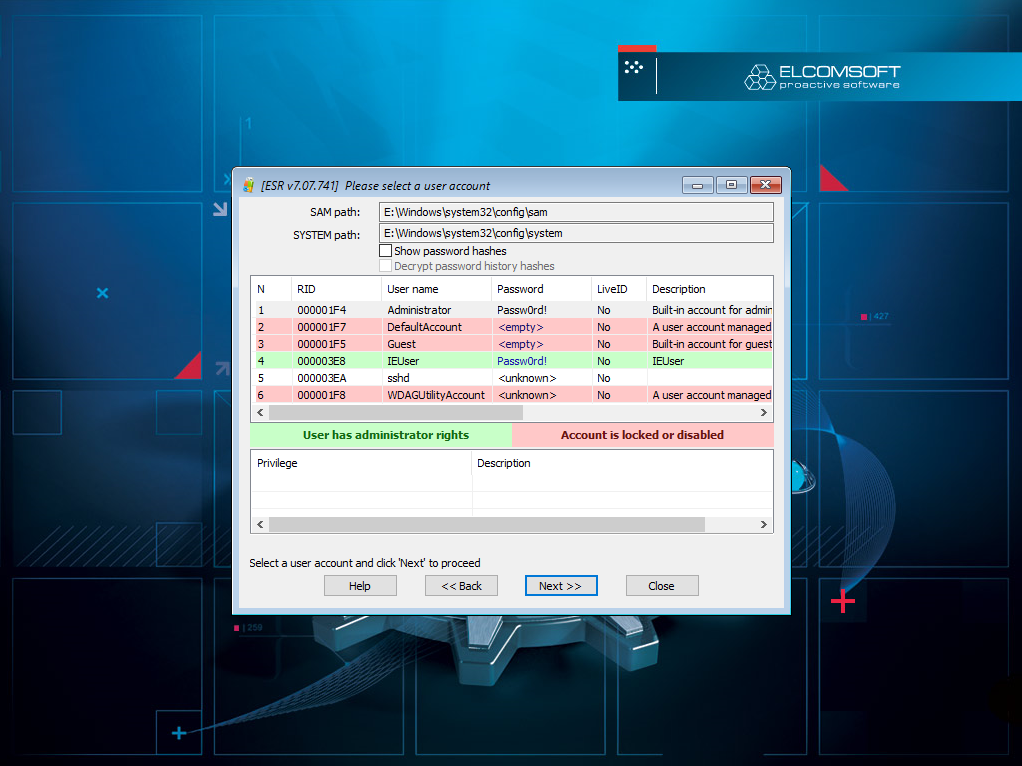
Windows account passwords: extract hashes
If the tool is unable to discover passwords to all user accounts, you can extract encryption metadata (hashes) for subsequent password recovery with Elcomsoft Distributed Password Recovery.
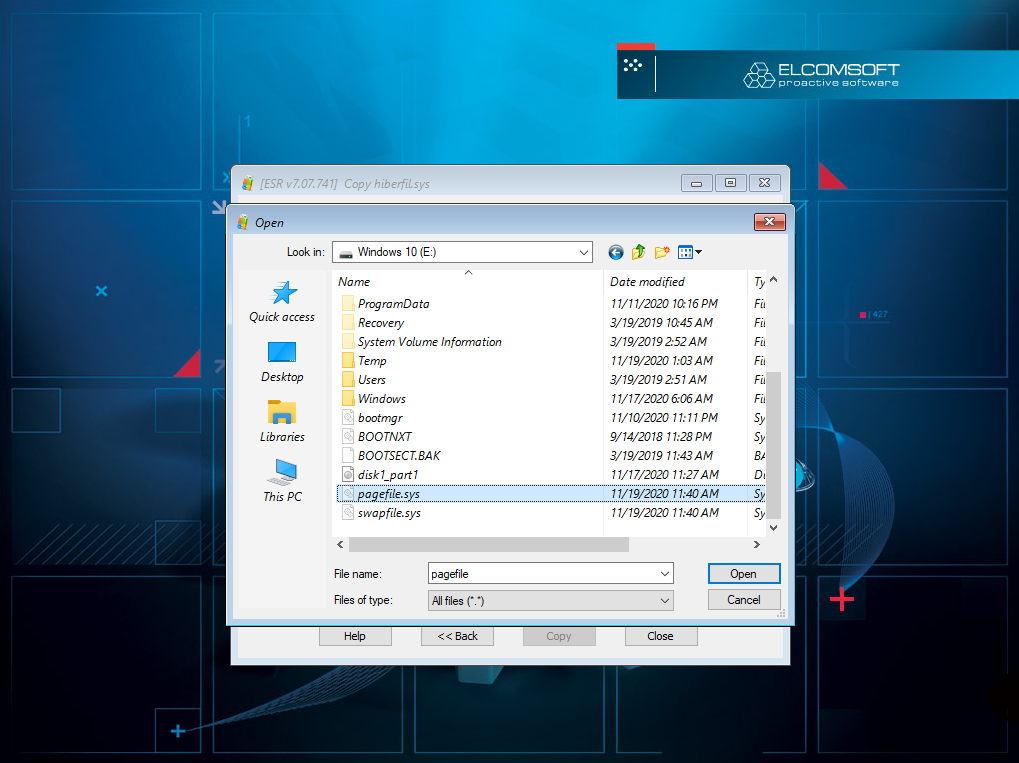
Hibernation and page files
The hibernation and page files may contain on-the-fly encryption keys used by various disk encryption tools such as VeraCrypt, TrueCrypt, PGP or BitLocker. Extract these files and save them on external media for further analysis with Elcomsoft Forensic Disk Decryptor.
Search for encrypted disks
Disk encryption is commonly used in the criminal world. ESR can search for encrypted disks, identity protection methods and extract encryption metadata. In many cases, the encryption metadata can be used to launch a password recover attack on the encrypted disk.
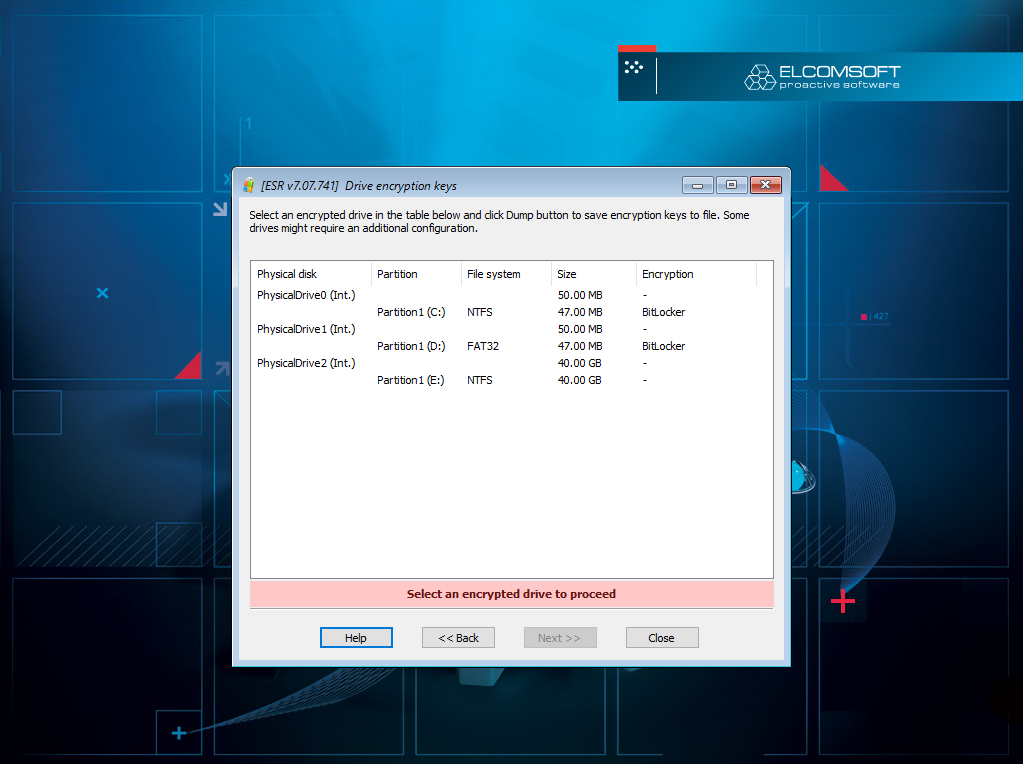
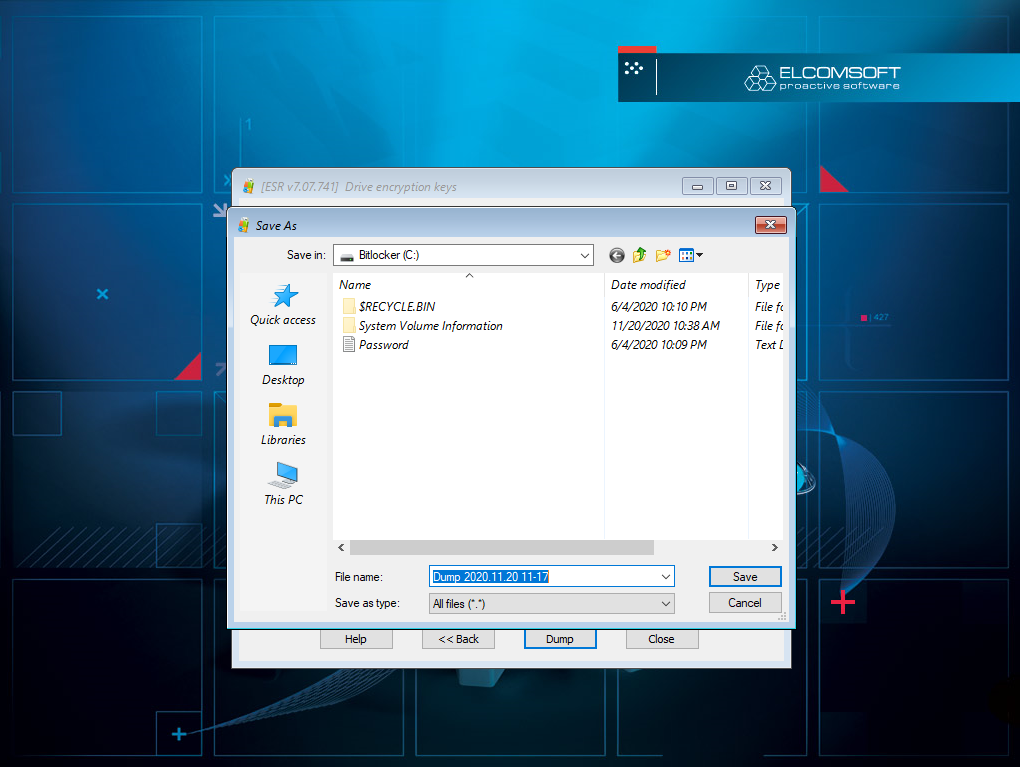
If the encrypted disk was mounted immediately before the analysis, the binary on-the-fly encryption keys might be available in page or hibernation files. Use Elcomsoft Forensic Disk Decryptor to scan these files for disk encryption keys.
Search for encrypted virtual machines
Along with disk encryption tools, encrypted virtual machines are among the most common cover-up tools. Manually locating such virtual machines can be an involving and time-consuming process. ESR simplifies this task by finding many types of encrypted virtual machines automatically. Once an encrypted VM is discovered, ESR automatically saves the encryption metadata. You can use that data to launch a password recovery attack on VM encryption in Elcomsoft Distributed Password Recovery. We have an article on the subject: Breaking Encrypted Virtual Machines: Recovering VMWare, Parallels, and VirtualBox Passwords
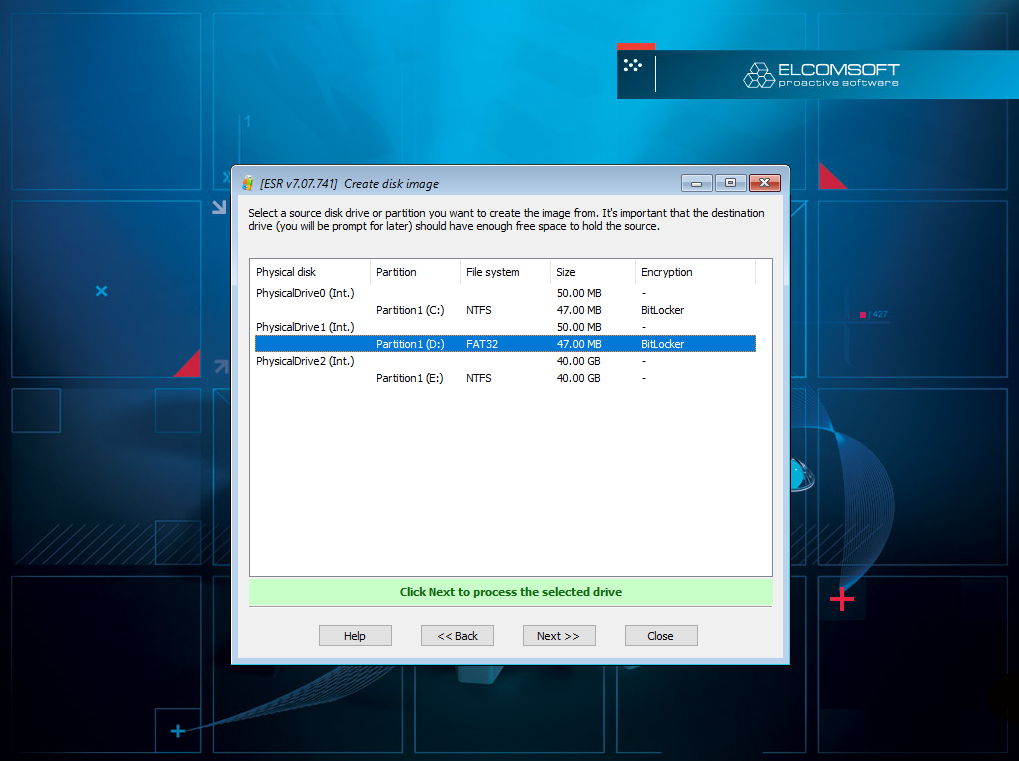
Create forensic disk images
When investigating incidents, you are more likely to analyze a disk image rather than a physical hard drive. Use Elcomsoft System Recovery to capture the disk image and start the analysis without the need for opening the computer and taking the disks out.
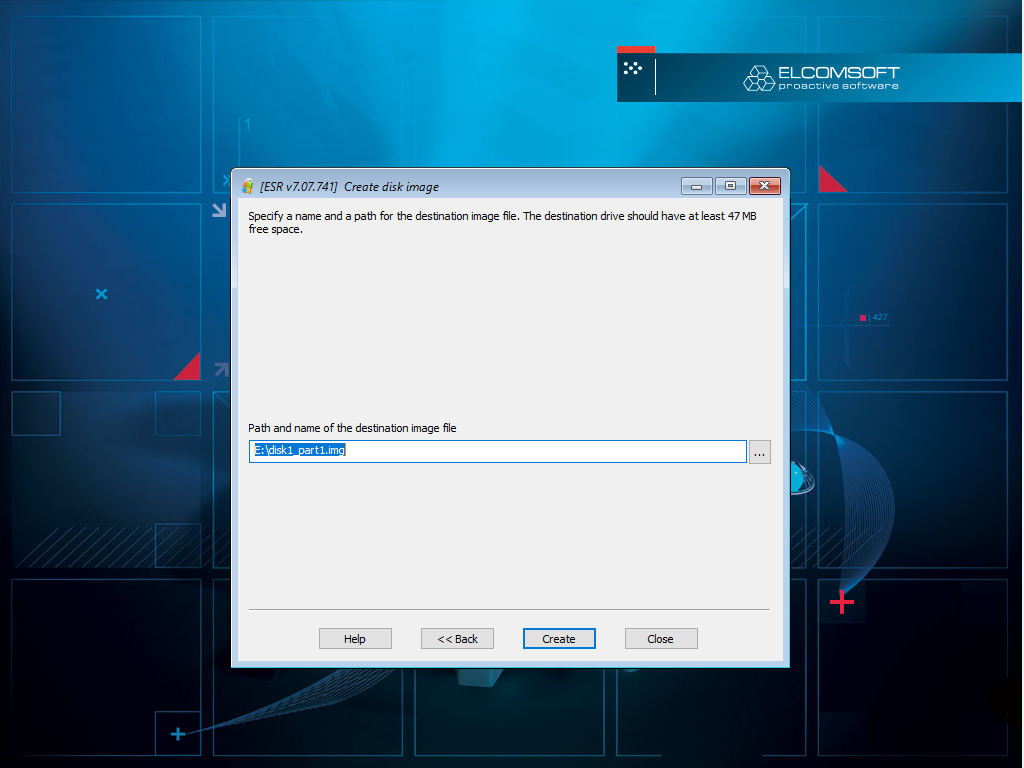
Note: you will need an appropriately sized external storage media to store the disk images.
The extra step: live system analysis
In certain cases, you may need to perform the analysis of an authenticated user session. If ESR was able to recover the original password to one of the user accounts, you may use that password to sign in. Alternatively, you can use ESR to reset the password of a Windows account. Before you do, make sure that you fully realize the consequences and perform the risk assessment.
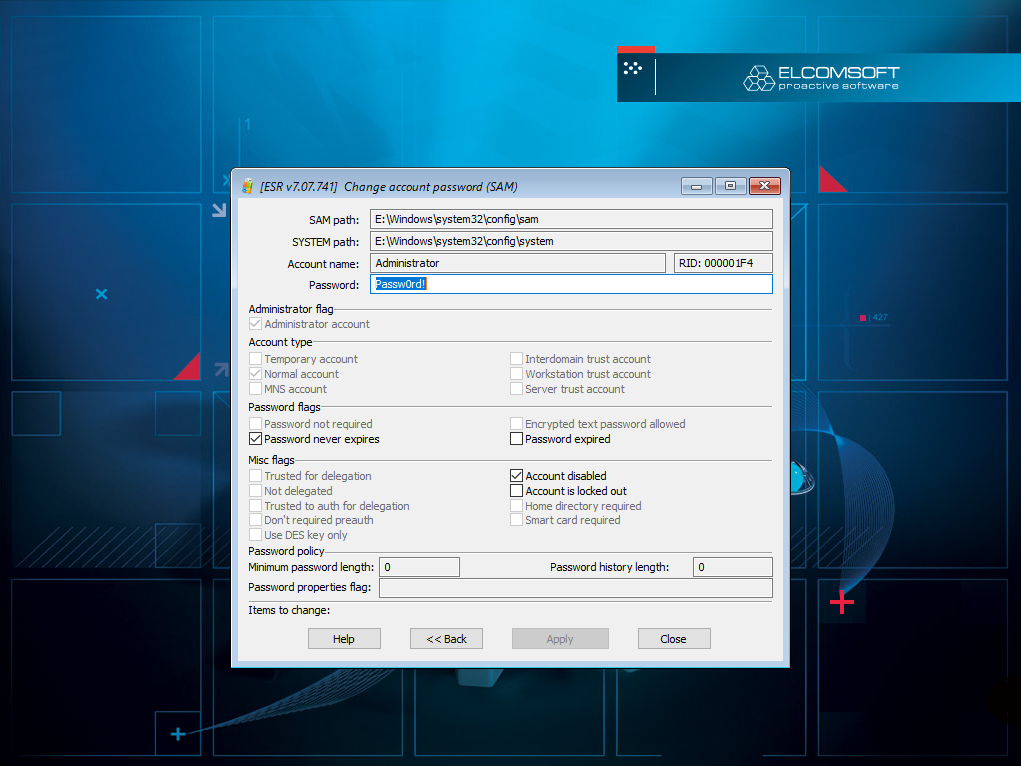
Consequences of resetting a Windows account password
If you choose to reset the password to a certain user, you will lose access to information protected with DPAPI (Windows Data Protection API). This information includes:
- EFS (Encrypted File System) access. Any NTFS-encrypted files will be rendered useless after resetting the account password. You absolutely need the original password to decrypt those files.
- Items stored in the Protected Storage including but not limited to: Microsoft Edge Legacy passwords; access to Google Chrome and Edge Chromium password database; passwords to network shares; passwords to email accounts.
In order to access any of that data, you will require the user’s original account password.



















