The previous publication talks about the basics of using the bootloader-level exploit for extracting iOS devices. In this article, we are posting a comprehensive step-by-step guide of using the new checkm8 capability of iOS Forensic Toolkit for performing forensically sound extractions of a range of Apple devices.
Pre-requisites
Before you begin, make sure you have everything required to perform the extraction. Since checkm8 is a very specific exploit, you’ll need all of the following to do the job.
- A Mac computer. You will need a Mac to install the exploit and perform the extraction. We support both Intel and M1-based Macs, with a universal build of iOS Forensic Toolkit expected at the time of the final release. At this time, Windows is not supported.
- iOS Forensic Toolkit 8.0 beta for Mac (or newer). Note that you will need the Mac edition of the tool. Note: the checkm8 extraction functionality is in active development, so frequent updates are expected for the time being.
- A supported iPhone or iPad device (see below). The device must be functional enough to be placed into DFU mode. Locked, disabled and USB-restricted devices are supported.
- Screen lock passcode must be known or empty. Otherwise, limited BFU extraction may be available, but very little information can be obtained this way.
- A supported version of iOS. At this time, we support all official and most beta versions of iOS that could be installed on supported devices, with a sole exception of the iOS 7 range (iPhone 5s).
- A USB-A to Lightning cable. Note that Type-C to Lightning cables are incompatible with this extraction method. The cable must be connected directly, absolutely no hubs. The use of USB-A to Type-C adapters is allowed if your Mac only has Type-C ports.
- You will have to determine the exact version and build number of iOS installed on the iPhone. If you don’t know it, it will be detected automatically during the unlock (see “Detecting iOS version” for details).
- You must be able to download the official Apple firmware (download link will be provided during the extraction) that matches iOS version installed on the device.
Supported devices
All models of iPhone 5s, iPhone 6, iPhone 6 Plus, iPhone 6s, iPhone 6s Plus, iPhone SE (original model) are supported including the following devices:
- iPhone 5S (iPhone6,1): A1453, A1533
- iPhone 5S (iPhone6,2): A1457, A1518, A1528, A1530
- iPhone 6 (iPhone7,2): A1549, A1586, A1589
- iPhone 6 Plus (iPhone7,1): A1522, A1524, A1593
- iPhone 6s (iPhone8,1): A1633, A1688, A1691, A1700
- iPhone 6s Plus (iPhone8,2): A1634, A1687, A1690, A1699
- iPhone SE (iPhone8,4): A1662, A1723, A1724
Unofficial support for the following models:
- iPod touch 6th gen: A1574
- iPad Air: A1474, A1475, A1476
- iPad mini 2/3/4: A1490, A1491, A1599, A1600, A1601, A1538, A1550
- iPad 5th gen: A1822, A1823
We’ve been able to test the toolkit with all supported iPhone models running all major versions of iOS. The support for iPad and iPod Touch models is unofficial as we’ve been unable to source every iPad model running every version of iOS.
You may have noticed that the iPad Air 2 and iPad Pro (1st gen) are missing from the list. This is because these devices are built on the A8X/A9X platforms unlike the rest of the models that are using SoC that are similar to those used in the corresponding iPhone models. The list of similar devices is available in Apple Mobile Devices Cheat Sheet | ElcomSoft blog.
Detecting iOS version
Our extraction solution does not use the operating system installed on the iPhone to boot the device. Instead, a separate, patched version of the original Apple firmware is booted in the device RAM. This process requires you to have a copy of the original Apple firmware image that matches the device’s iOS version and build number exactly.
In many cases, the iOS version will be detected automatically by EIFT during the first stage of the exploit. The detection is based on the detected iBoot version and device hardware. However, in some cases the iBoot version may correspond to several iOS builds.
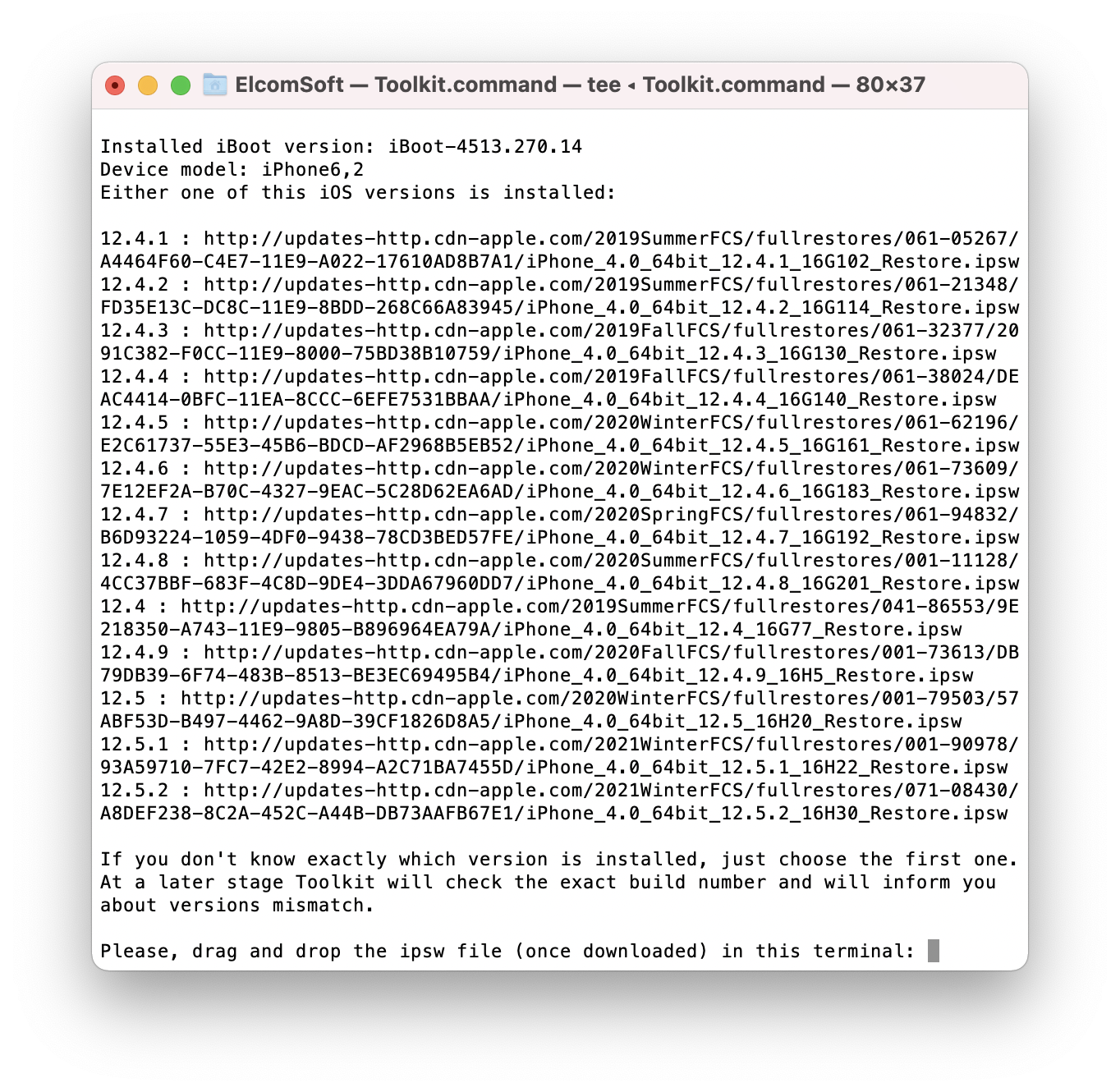
If this is the case, you can attempt to use the first version of iOS suggested by EIFT. After you boot and unlock the iPhone using the downloaded image, EIFT will either be able to unlock the disk, or will display the correct iOS version.
Alternatively, you can check the iOS version in Settings – About on the iPhone itself.
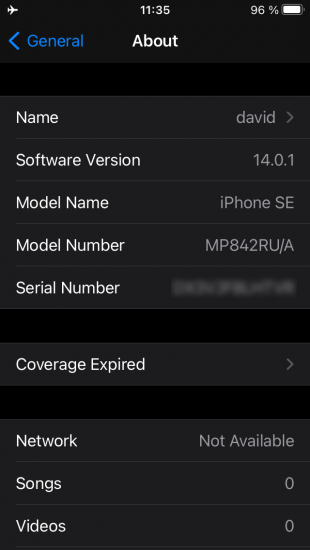
Tap iOS version to see the build number:
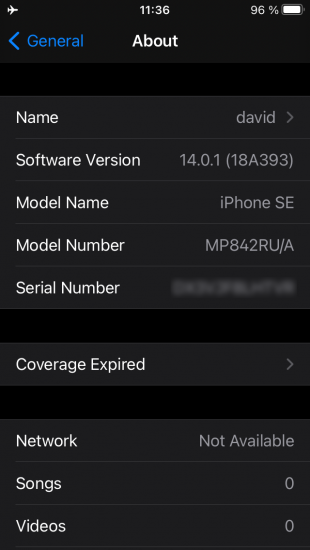
Note that you can still boot the phone using a close enough iOS build suggested by EIFT. If the wrong build is used, EIFT will be able to detect and display the correct build number at a later stage of the exploit.
What is extracted
If you know the screen lock passcode (or if the passcode is empty), Elcomsoft iOS Forensic Toolkit 8.0 can extract the file system image and decrypt the keychain. Otherwise, limited BFU extraction is available.
Note that the location of the extracted information has changed in EIFT 8.0 compared to previous versions. EIFT will create a folder named “ElcomSoft” in your home folder on the Mac. The following subfolders will be created:
- logs
- eift_logical
- eift_physical
- eift_checkm8
- eift_legacy
- eift_jailbreak
For checkm8 extraction, the “logs” folder will contain the debug logs, while “eift_checkm8” will receive the data extracted (the file system and keychain).
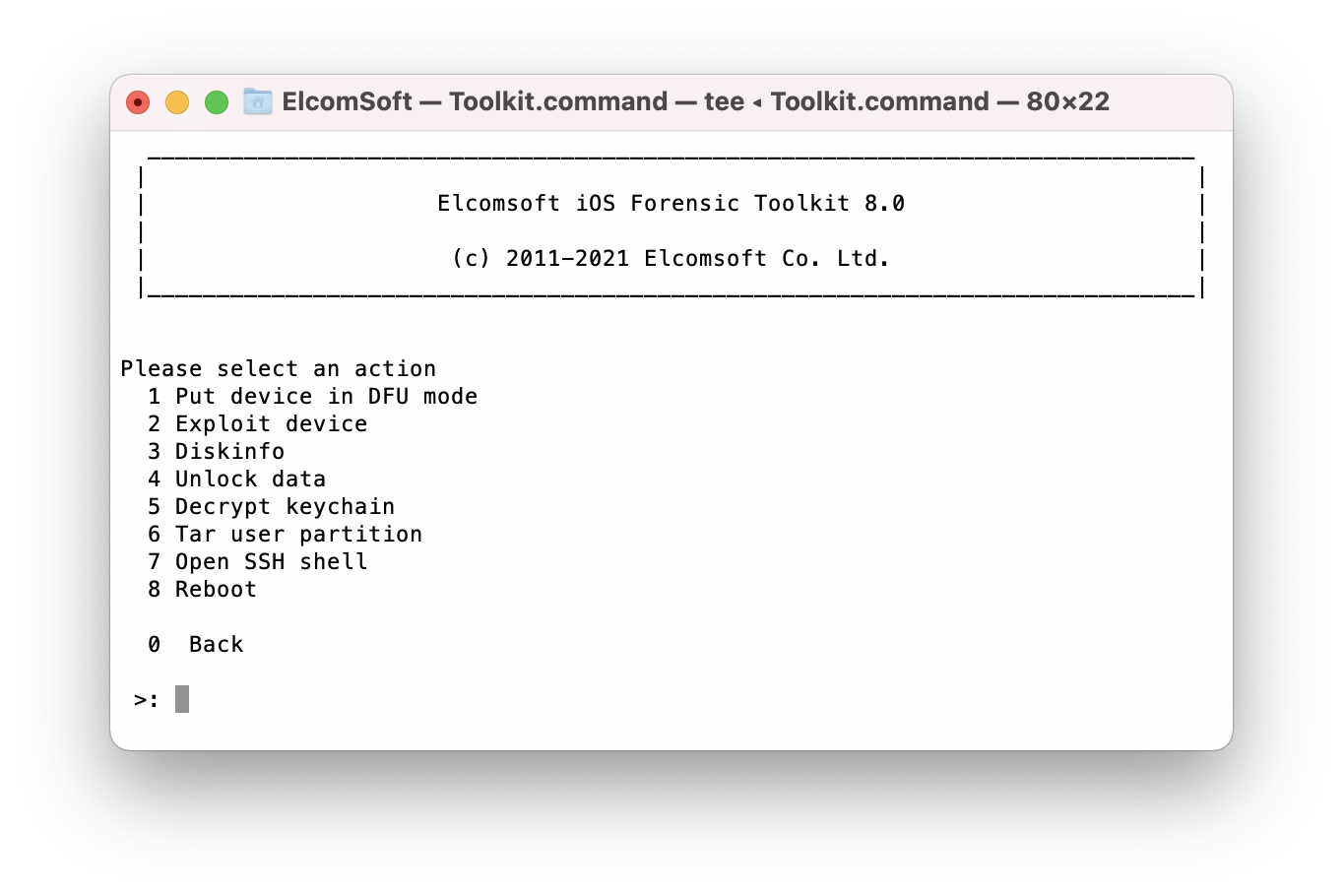
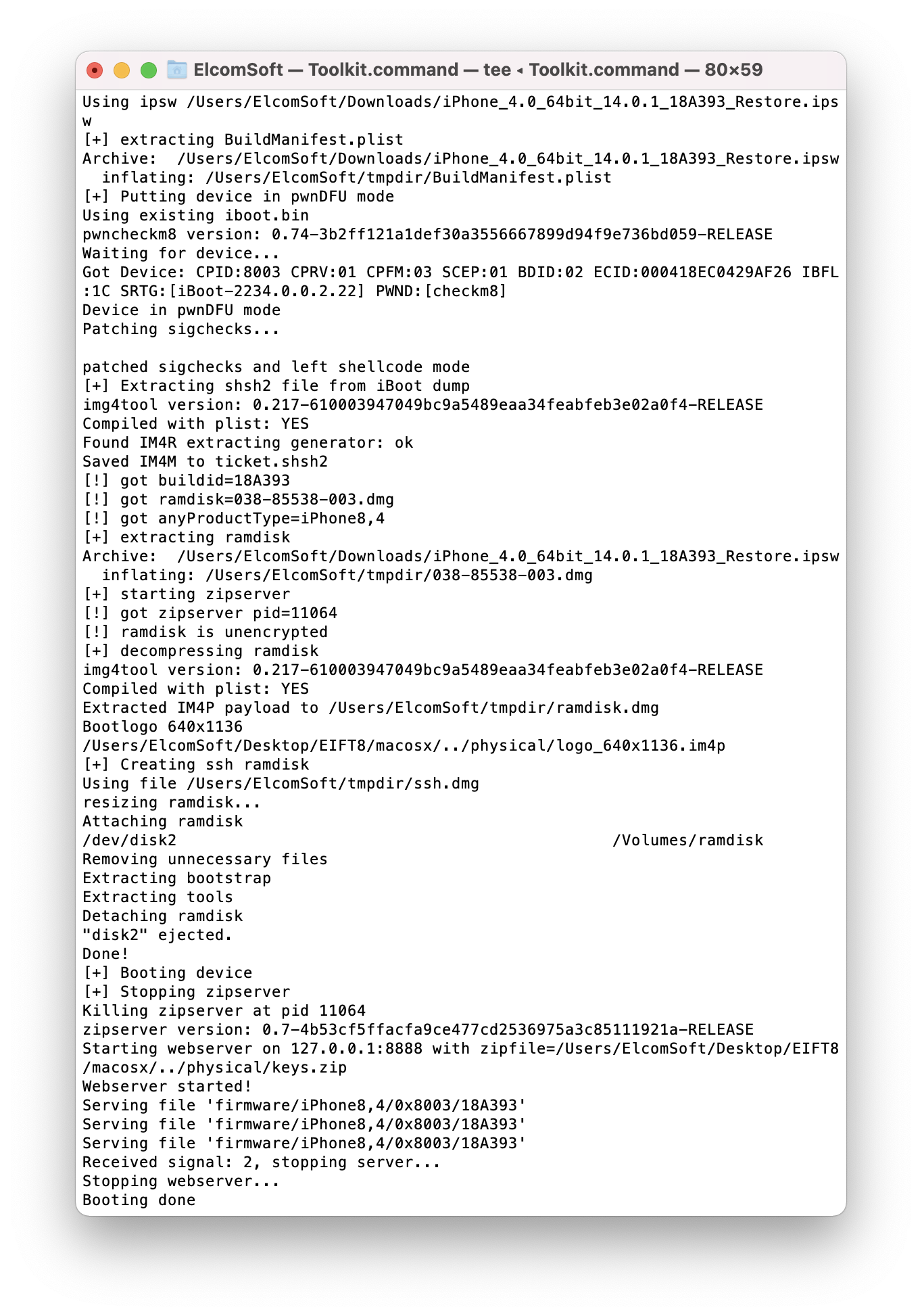
Step 1: exploiting the device
- Launch Elcomsoft iOS Forensic Toolkit 8.0 (or newer).
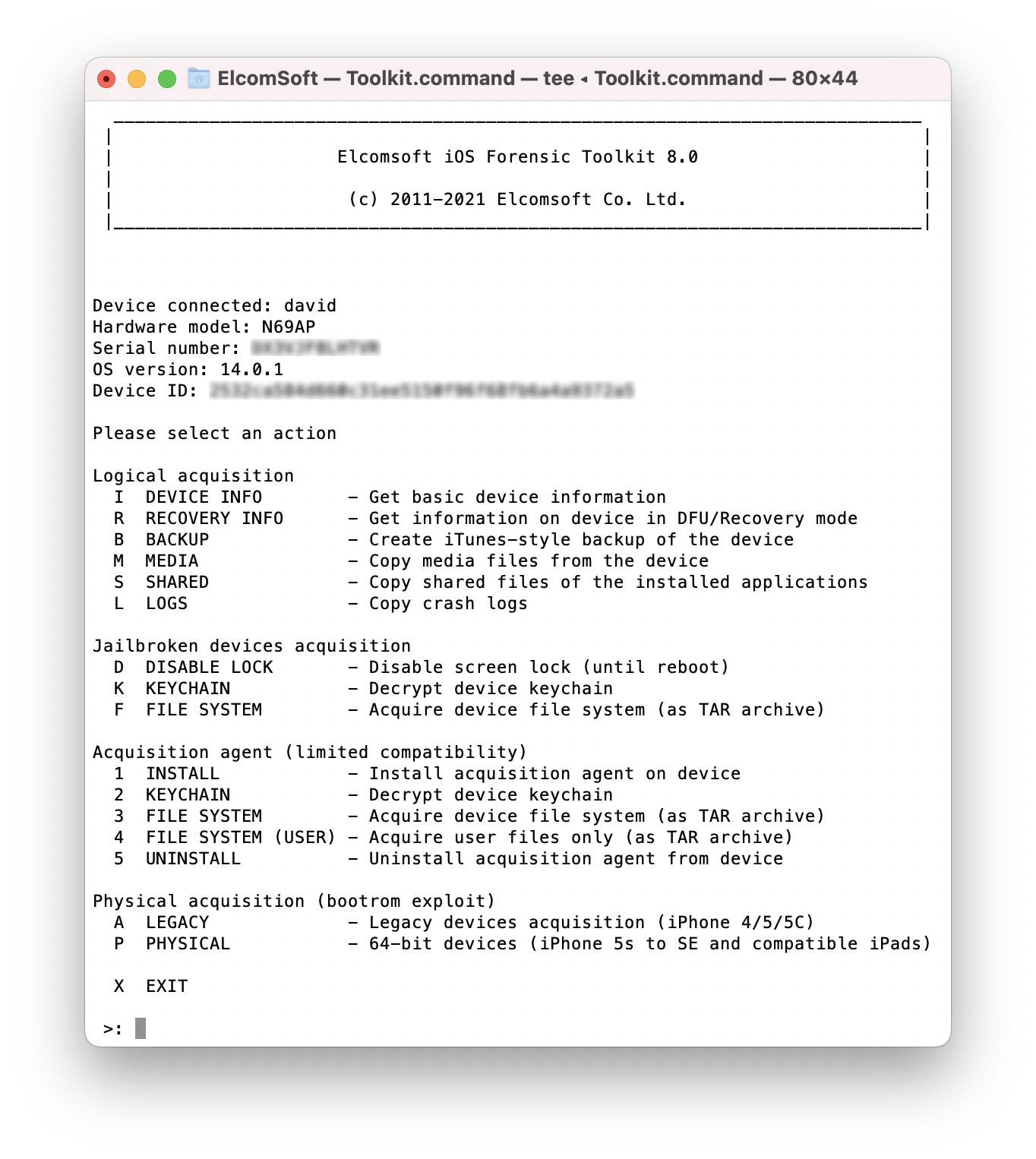
- Enter “P” access the checkm8 functionality.
- Prepare to put the iPhone into DFU. Initial state: the iPhone is powered on and connected to the computer with a USB-A to Lightning cable (locked, disabled and USB restricted devices are OK).
- The procedure is the same for all supported devices. To receive on-screen guidance with timed instructions, enter “1” in EIFT.
- Follow the on-screen instructions appearing in EIFT.
- Press Power and Home buttons for 8 seconds (exact timings are crucial at this step).
- Release Power, keep holding Home for another 8 seconds (exact timings are less important here).
- The iPhone screen should be black. If the device reboots or displays the “iTunes” icon, repeat the procedure.
- In iOS Forensic Toolkit, use the “2” command to perform the exploit.
- The toolkit detects iBoot version and device model. Based on this information, the toolkit attempts to detect the iOS version, and displays the corresponding link or links to download the original firmware. You must download the version of iOS that matches the iOS build installed on the device (see “Determining iOS version” for details).
- Download the iOS firmware image using the link(s) displayed.
- Drag and drop the downloaded IPSW file onto the EIFT window. The EIFT console will display comprehensive debug information while patching and booting the build. You may use this information when contacting support.

- The iPhone screen will remain black for a while, then display the Booting screen.

- Once the exploit is installed, the following information will be displayed on the iPhone screen:

- The console will contain an entry reading “Booting done”.
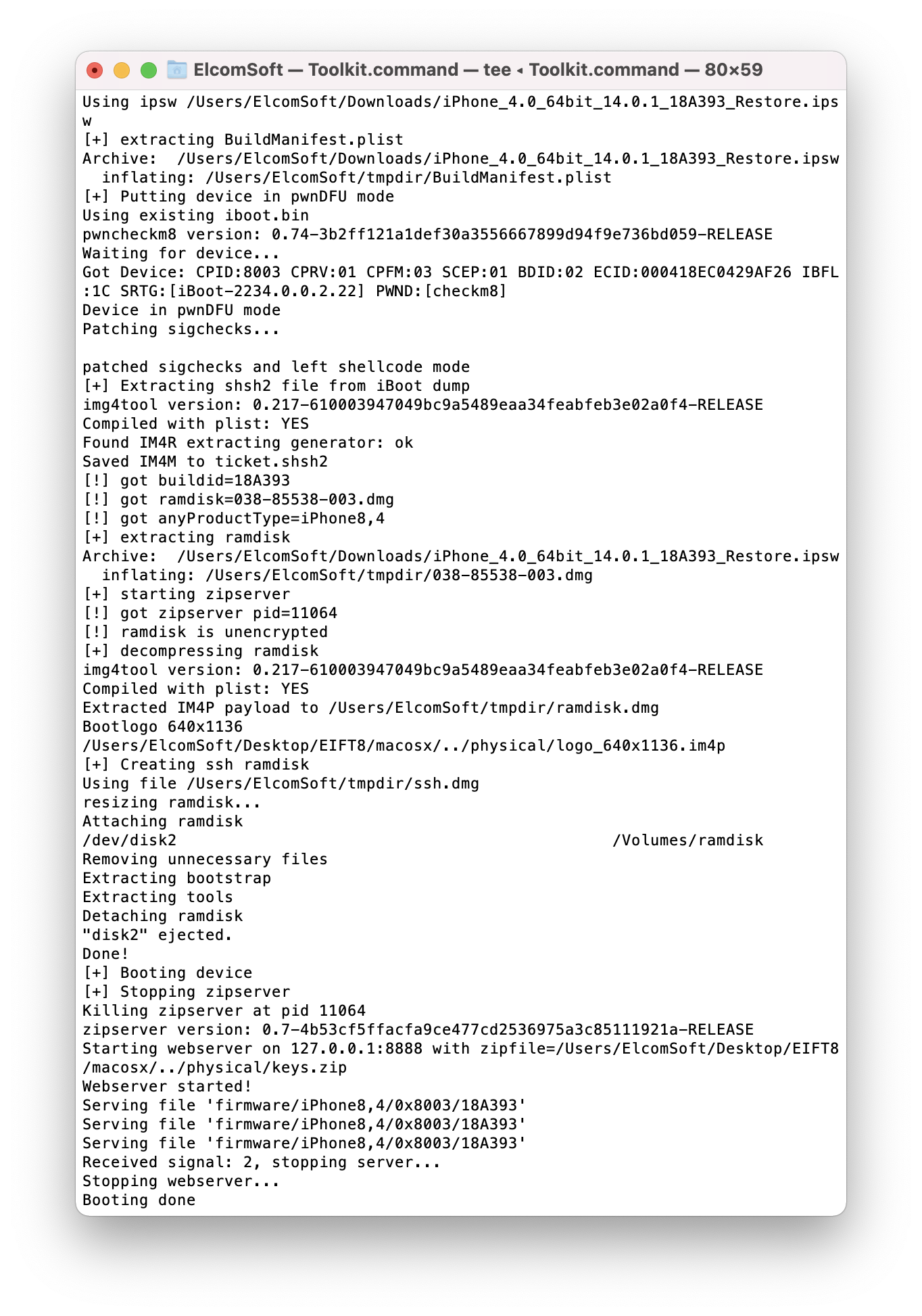
At this point, you have successfully exploited the device.
Step 2: exploring and extracting the device
Once the exploit is installed, you will be able to list partitions, unlock and extract data.
[3] Diskinfo
This optional command displays the list of partitions available on the iPhone after you exploit the device. Newer versions of iOS use APFS as a file system, in which case the number of partitions can be up to 7. EIFT will only extract DATA partitions.
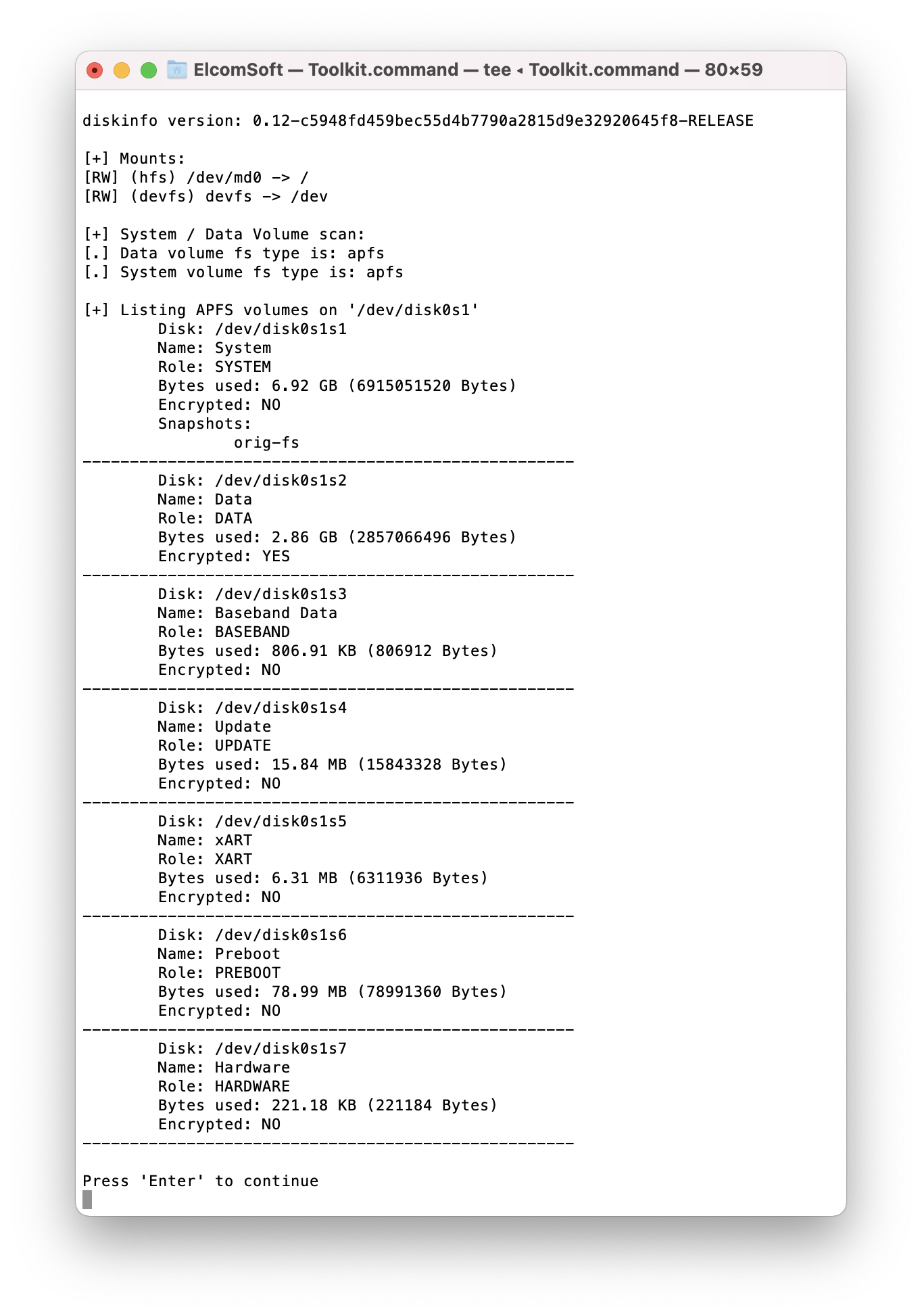
This command may be useful in a case the file system is marked as “dirty”. The “file system dirty” flag can be set by iOS if the device had not been shut down correctly, e.g. after a forced shutdown, interrupted boot, and similar cases. If this is the case, you will see the following information:
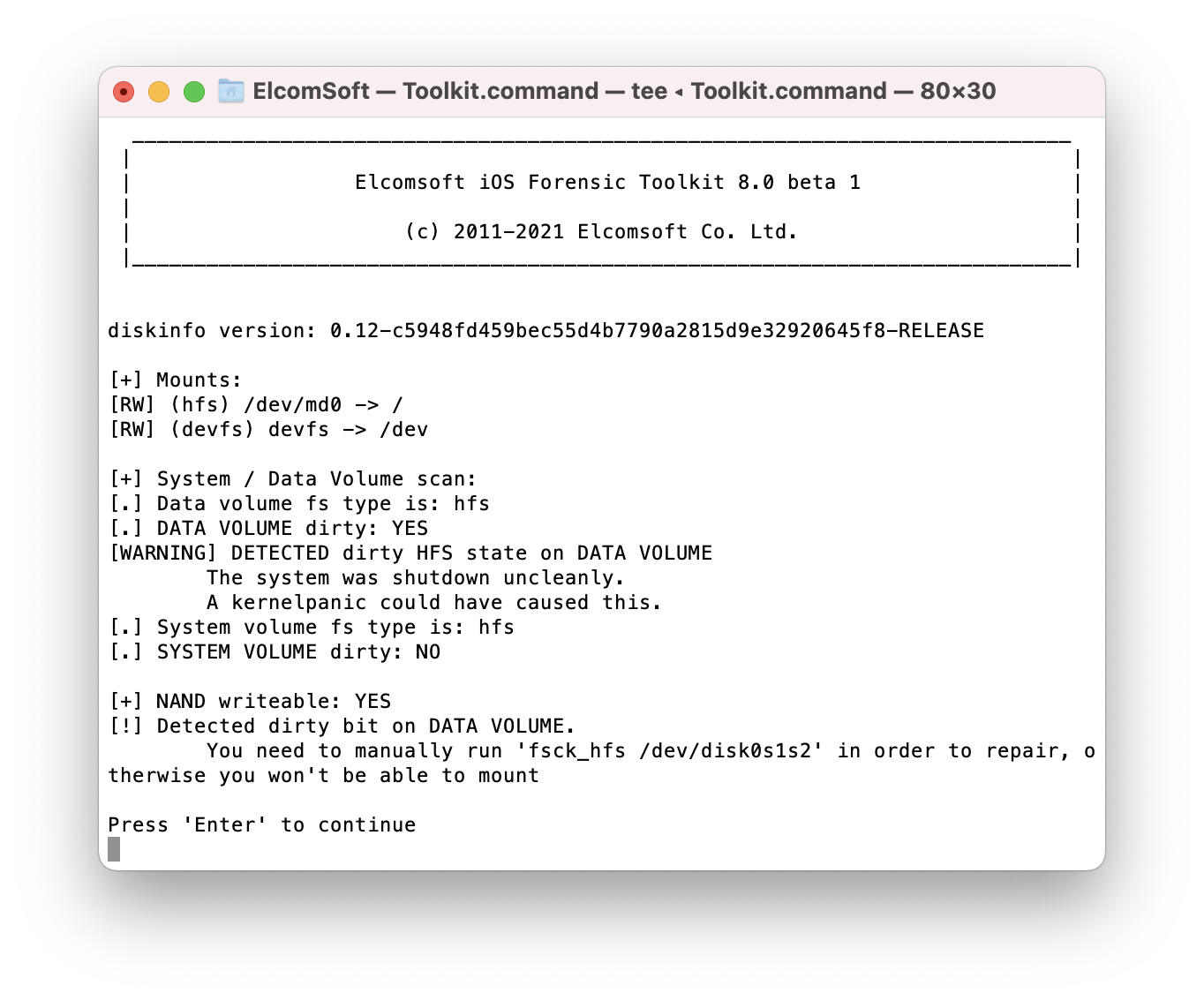
Note that, contrary to what you see on the screen shot, you won’t have to manually run any commands. Instead, EIFT will initiate a file system check in order to mount the system/data partitions read-only.
[4] Unlock
This option is mandatory for subsequent extraction. In all iPhones, the data is stored encrypted. In order to access the data, you need to unlock the device. Since the iPhone is in the “Before First Unlock” (BFU) state, you must provide a valid screen lock passcode in order to access the data.
EIFT will first prompt if the passcode is known. If you do know the passcode, or if the passcode is empty, type “Y” or “y”. If, however, the passcode is set but unknown, enter “N” or “n” for BFU extraction.
If the passcode is empty, EIFT will automatically unlock the disk.
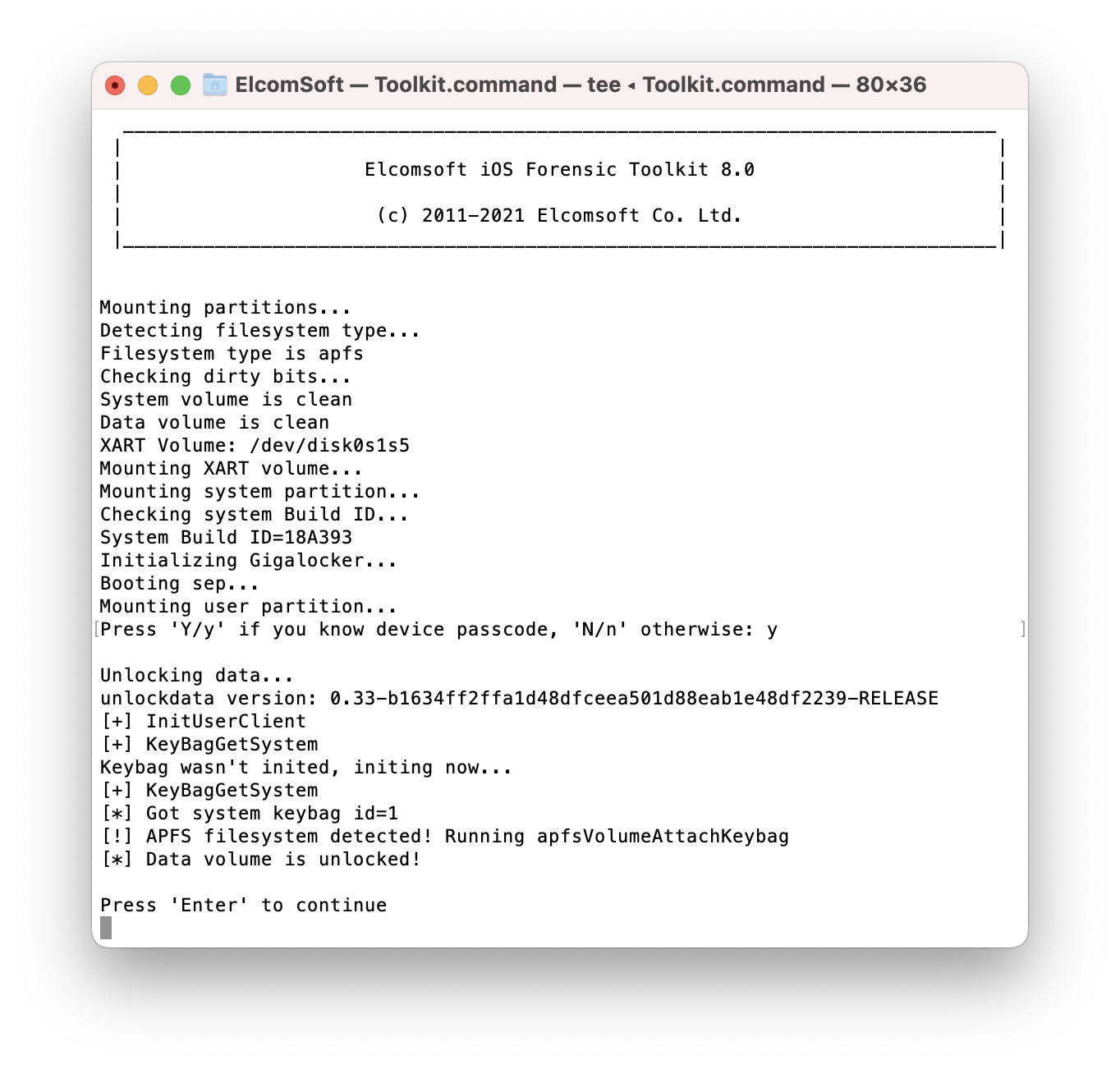
For non-empty passcodes, you will have 7 attempts to enter the passcode. Once the correct passcode is entered, the toolkit will automatically mount the disk.
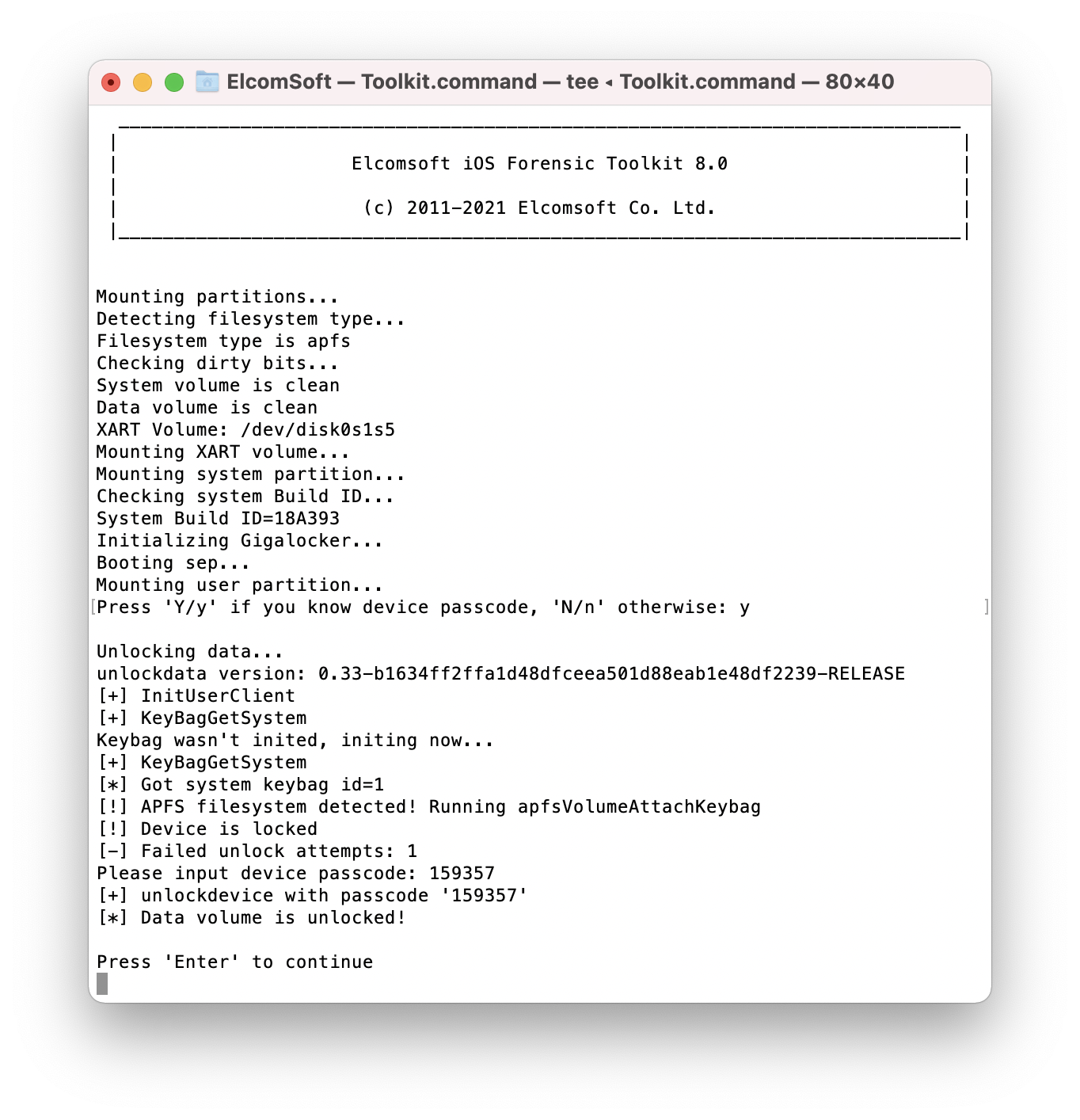
WARNING: After 10 incorrect passcode attempts the iPhone will be permanently locked, and only BFU extraction will be available. This is why EIFT stops after only 7 unsuccessful attempts.

On successful unlock, you will see the following screen on the iPhone:

Troubleshooting
There are several specific conditions that may prevent unlocking the disk and extracting the data.
Version mismatch
While EIFT attempts to detect (“guesstimate”) the correct version of iOS installed on the iPhone based on the device hardware ID and bootloader version, there may be no concrete match between versions of iBoot and iOS. If this is the case, EIFT will list several possible versions of iOS along with download links. If you don’t know the exact version of iOS installed on the iPhone (as could be seen in the Settings – About on the iPhone), you may try using one of the listed firmware images. In many cases, this is enough to unlock the disk and extract the data. In some cases, there could be a mismatch between SEP and iOS versions. If this is the case, you will see the following error message:
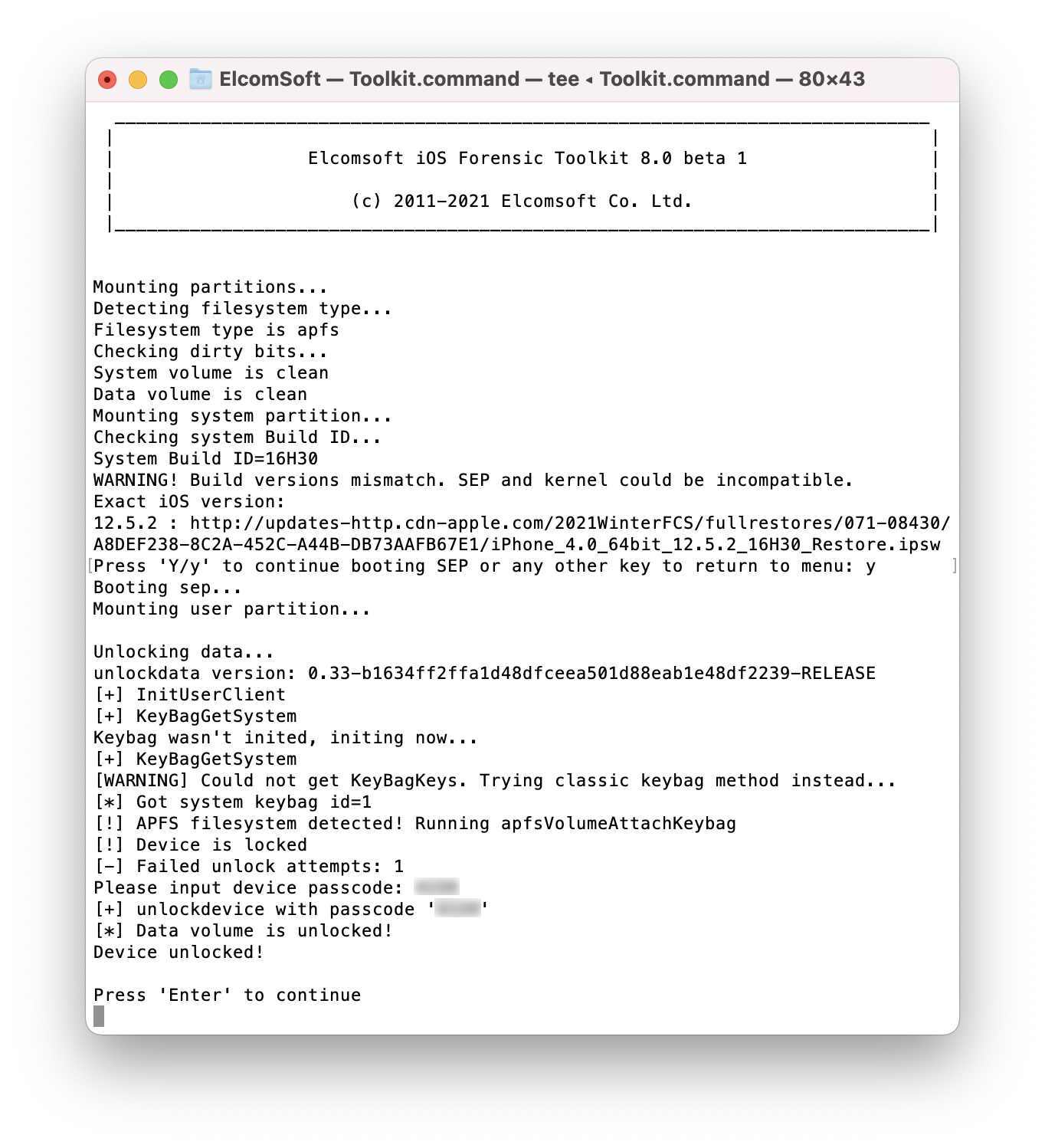
If this occurs, download the exact version of iOS that is listed in the error message as shown on the screen shot above, and try again. However, you may still try the current version of iOS; there will be no risk, and the extraction may still work.
Dirty file system
On very old versions of iOS using the HFS file system, iOS may raise the “file system dirty” flag if the device had not been shut down correctly, spontaneously rebooted of did not finish the boot sequence. This is not applicable to 64-bit devices running iOS 10.3 and up; there is no ‘dirty’ bit in APFS that replaced HFS since iOS 10.3.
If the file system is marked ‘dirty’, the device will refuse to boot the supplied disk image. For this reason, initiate a file system check to mount the system/data partitions read-only. This is performed automatically during the unlock.
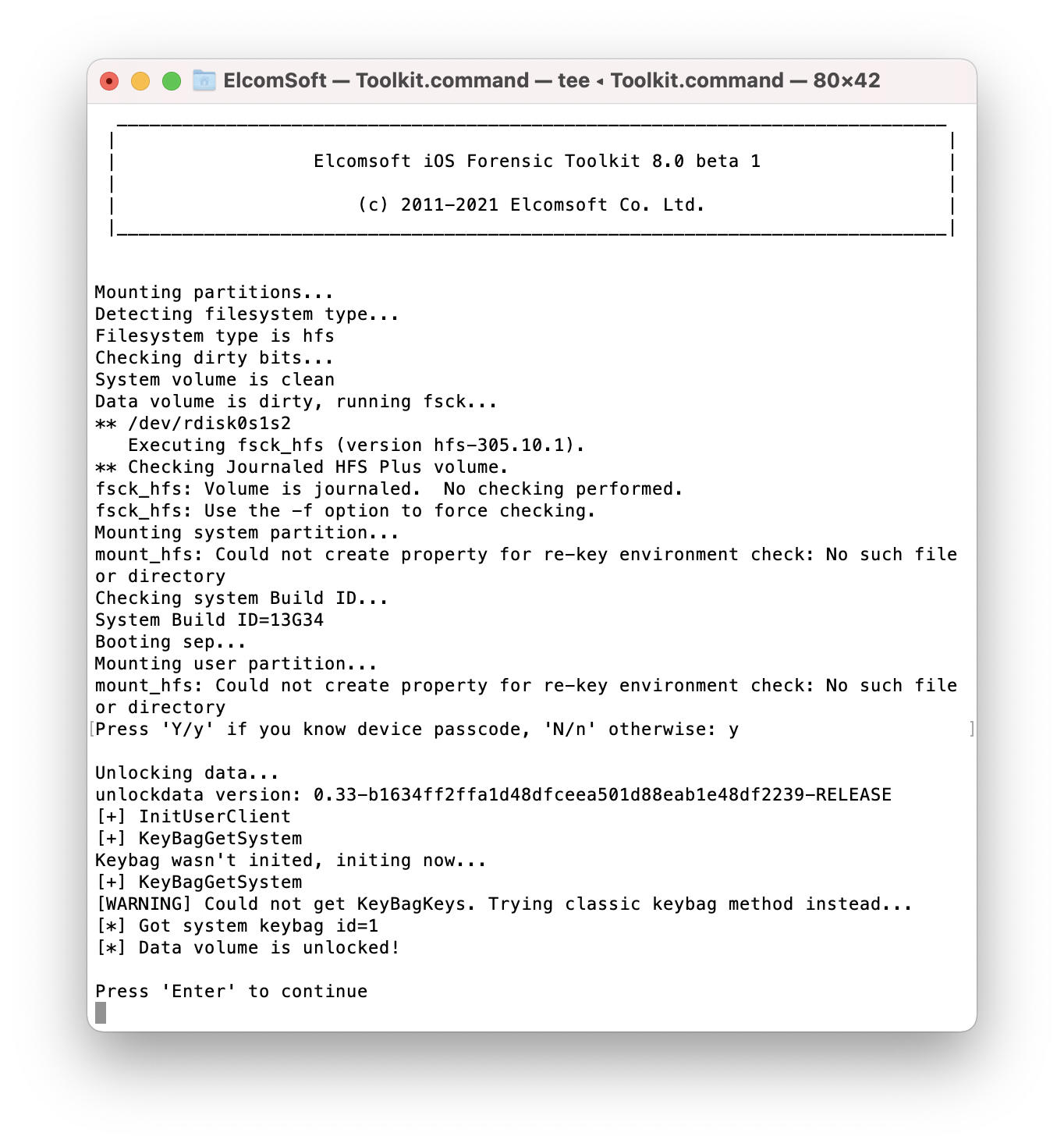
Once you have unlocked the disk, you can extract the keychain and image the file system. Subsequent commands are very similar in form and function to agent-based extraction except you won’t need to perform any actions on the iPhone.
Locked and disabled devices
If the iPhone is disabled after multiple incorrect passcode entries, you will be unable to unlock the disk even after the device is exploited due to SEP protection.
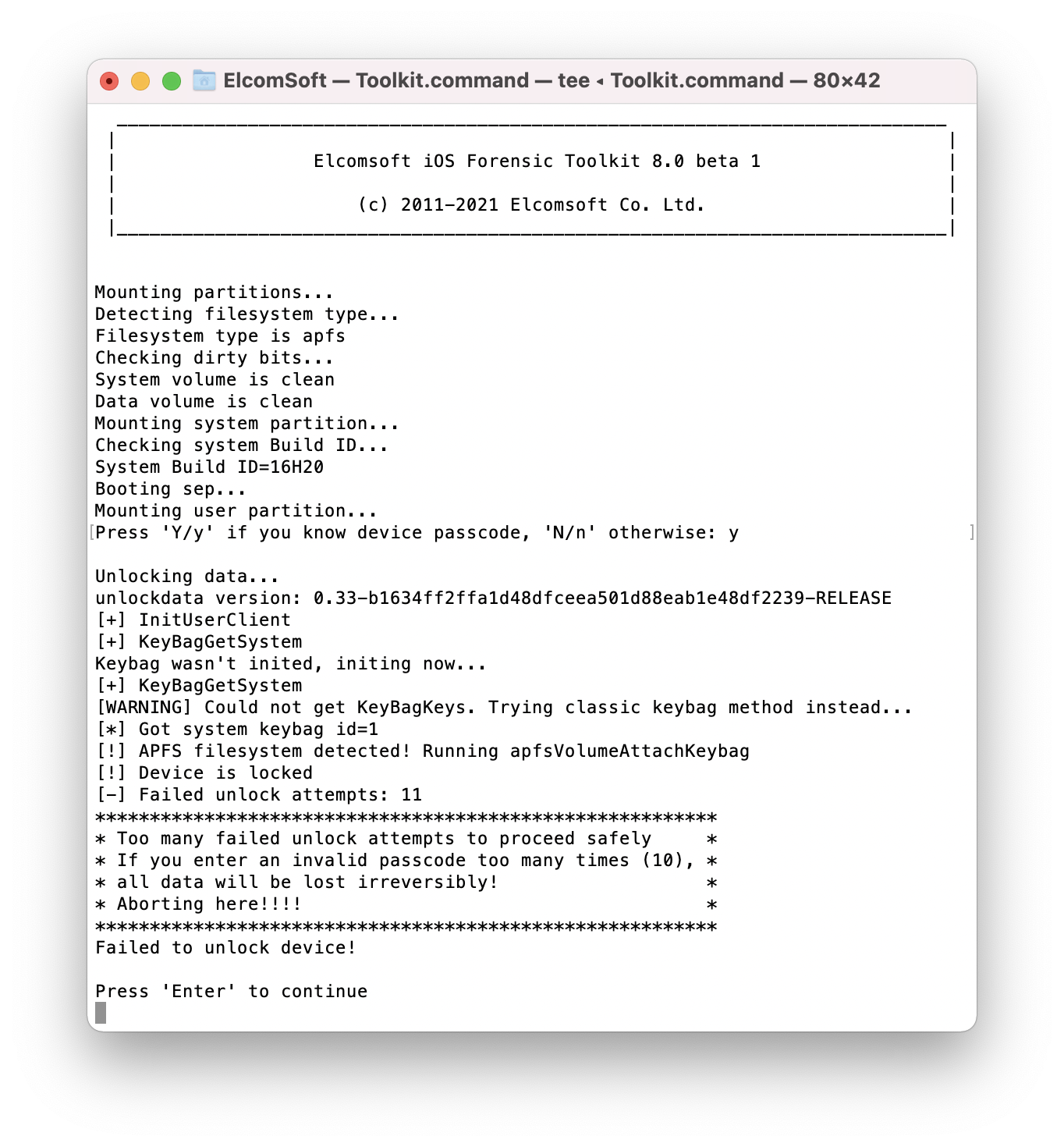
There is no known workaround. The only option for locked and disabled devices is BFU extraction. To invoke BFU extraction, answer “N” or “n” to the prompt asking if you know the passcode.
Device is running a beta version of iOS
There is no official support for iOS betas. However, more likely than not, the closest official iOS release will allow to unlock the disk and extract the data. You can try one version down and one version up. For example, for devices running iOS 11.2 beta, try iOS 11.1 and 11.2.
[5] Decrypt keychain
Run this command to extract and decrypt the keychain.
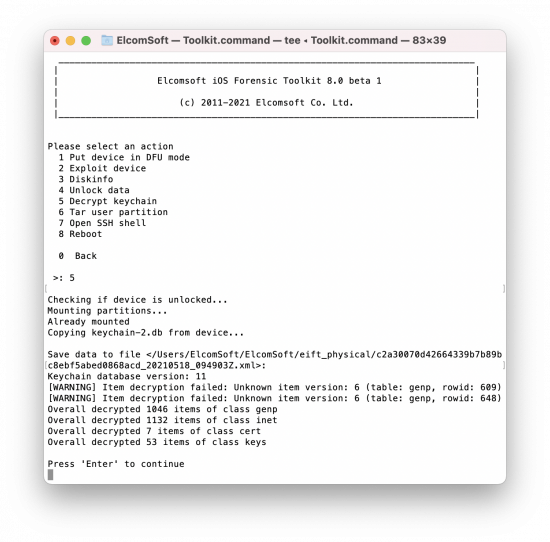
[6] Tar user partition
Run this command to extract a file system image and save it into a .tar file.
[7] SSH
This is a highly optional command allowing to establish SSH connectivity between the computer and the iPhone. For advanced users and support inquiries only.
Other notes
- No support for iOS 7 (iPhone 5s), at least for the time being.
- You may encounter errors when attempting to boot and unlock the device. Since there are multiple combinations of hardware and software, we decided to leave the full debug output enabled by default. If you encounter a problem booting or unlocking the device, please contact our technical support and provide the debut output from the EIFT window.
- The iPhone 6s and iPhone SE were built using Samsung and TSMC chips. Both chips are supported transparently. You can see which chip it was in the boot log (CPID on the screen shot below). 0x8000 corresponds to Samsung chips, 0x8003 to TSMC.
- If you experience problems placing the device into DFU or applying the exploit, try using a different Lightning cable and/or USB port. If that does not help, try again on a different Mac. If that fails, try placing the iPhone into Recovery before DFU.
- On iPhone 6s and iPhone SE devices in particular, there are two slightly different DFU modes. Try the following sequences if the exploit does not work:
- Recovery mode first, DFU after
- Directly to DFU, immediately after rebooting the iPhone (before unlocking the phone)
- Directly to DFU but after unlocking the phone
- Directly to DFU with the iPhone initially powered off
- If you experience problems during the unlock stage, it may indicate a problem in our software. Please contact our technical support with the full debug log copied from the EIFT window.
- Note that passcode unlock is not currently possible. The device will be locked down permanently after exhausting the 10 unlock attempts. We are well aware of the issue, and are working hard searching for a workaround.






















