With little news on physical acquisition of the newer iPhones, we made every effort to explore the alternatives. One of the alternatives to physical acquisition is over-the-air acquisition from Apple iCloud, allowing investigators accessing cloud backups stored in the cloud. While this is old news (we learned to download data from iCloud more than two years ago), this time we have something completely different: access to iCloud backups without a password! The latest release of Phone Password Breaker is all about password-free acquisition of iCloud backups.
Update 25.07.2019: things have changed! The most up to date information on this topic is now available at:
But don’t get overly excited: this feature is mostly intended for our law enforcement and forensic customers, as using a password-free entry into iCloud requires a binary authentication token that must be extracted from the suspect’s computer. Don’t get me wrong: over-the-air acquisition from Apple iCloud without requiring the user’s Apple ID or password is great news, and no other company in the world can do it. But you’ll still need the suspect’s PC with iCloud Control Panel installed.
Acquiring iCloud Authentication Tokens
You’ll need the original Windows or Mac computer that was used to log into iCloud, and the Forensic edition of Elcomsoft Phone Password Breaker ($399 for North American customers) in order to extract iCloud authentication tokens. Of course, just any random PC won’t do the trick. You’ll need a computer which has iCloud Control Panel installed, and the user must’ve been logged in to iCloud Control Panel on that PC at the time the computer is seized. If the user logged out of the Panel, the authentication tokens are then deleted. You may be able to carve them; this is something we’ll look into in future versions of Phone Password Breaker.
What is iCloud Control Panel? It’s an integral part of iTunes, but requires a separate installation on Windows PCs. Mac OS systems have it pre-installed. Most users will stay logged in to their iCloud Control Panel for syncing contacts, passwords (iCloud Keychain), notes, photo stream and other types of data between their iOS devices and their computer. In other words, you have a high chance of obtaining authentication tokens from a computer that has iCloud Control Panel installed.
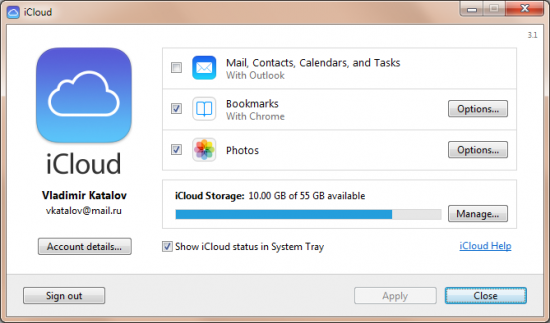
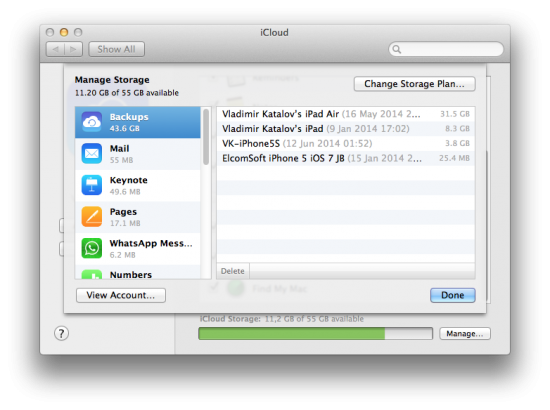
Below are the screenshots of iCloud Control Panel. As you can see, while the backups are “available” in the Control Panel, the only thing you can do with them is viewing the list of available files and deleting selected backups (and even then, you can only view the date, time and size of the latest backup out of the three versions stored, and can only delete all three versions at once).
Opening iCloud Control Panel in Windows:
Opening iCloud Control Panel in Mac:

And here is the iCloud Control Panel itself (Win/Mac):

These are the actual backups as listed by iCloud Control Panel (Win/Mac):
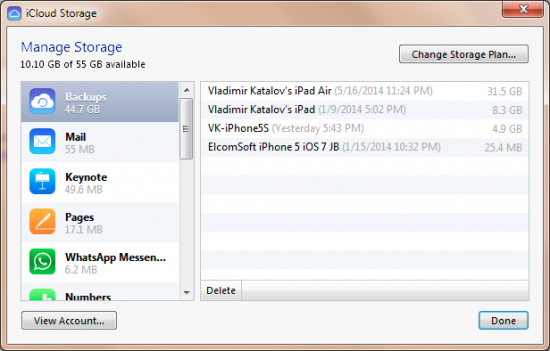
If you are not familiar with iCloud, you can get more information from Apple’s official Web site:
How It Works
So now you have the right PC, and are pretty sure it has iCloud authentication tokens. What next?
You’ll need to use command-line tools supplied with Elcomsoft Phone Password Breaker to search for and to extract authentication tokens. Note that you can extract tokens that belong to all users on that system, including domain users (if you have their system login and password).
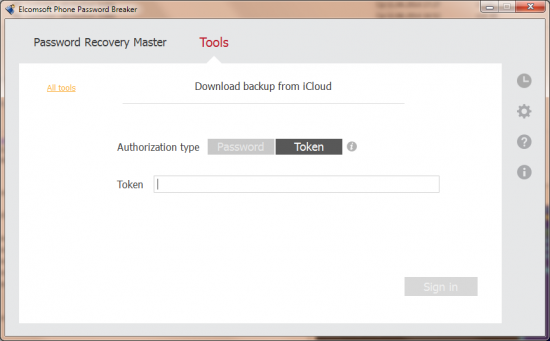
After extracting the authentication tokens, just save them somewhere (e.g. on a USB flash drive), launch Elcomsoft Phone Password Breaker and start iCloud acquisition. You will be prompted for authentication credentials. Instead of entering login and password, you’ll need to paste the authentication token files you’ve just extracted. Done! Phone Password Breaker will now use the extracted authentication tokens to access iCloud – no login and no password needed.
The tool for extracting authentication tokens is called ATEX (Apple Token Extractor). The file is saved into the same folder where Elcomsoft Phone Password Breaker is installed under the following name:
- atex.exe (Windows)
- atex.dmg (MacOS X)
Most likely, you wouldn’t want to run the token extraction tool from the folder where it is installed. In Windows this is simply impossible, as the token file cannot be saved into the Program Files folder (unless you have administrative privileges; even if you do have them but UAC is enabled, the token might not be saved). The tool is fully portable and works on any computer without requiring installation. We recommend saving the relevant tool (atex.exe for Windows, or mounting atex.dmg on a Mac by double-clicking the file) onto a USB flash drive, and running them from that USB drive plugged to the computer you are acquiring.
Windows
Assuming you already put the tool onto a USB drive, open command prompt (cmd.exe) and launch the tool:
>atex.exe <parameters>
-h // Shows help message
-l // Shows system users with iCloud tokens
-t [username] [password] // Get auth token for specified user
In order to extract the token for currently logged in Windows user, you may simply launch atex.exe with no parameters. Normally, you will see the following output:
>atex
Authentication Token is successfully saved to \\?\C:\TOKENS\icloud_token_20140611_145234.txt
Press any key to exit...
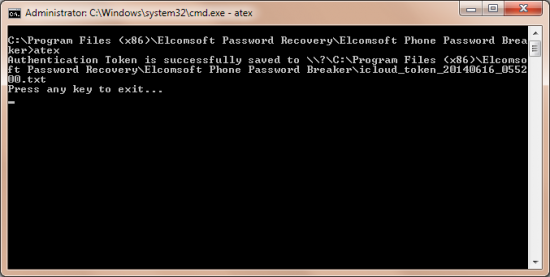
In order to list users with authentication tokens, launch ATEX with “-l” option:
>atex -l
iCloud users:
v.katalov@ELCOMSOFT
Administrator@ELCOMSOFT
Press any key to exit...
In order to retrieve the token for a different Windows user, specify that user’s password (in our example the user is a domain user):
>atex -t v.katalov@ELCOMSOFT password
Authorization Token is successfully saved to \\?\C:\TOKENS\icloud_token_20140611_151109.txt
Press any key to exit...
You will need administrative privileges to retrieve another user’s token, even with the correct password. ATEX will automatically request elevated privileges, so you may see a UAC prompt as well.
This is how a token file looks in Windows:
vkatalov@mail.ru
564819206:AQZACBBTmG6cyv/2g+zNTg1FNgn8V2bLa3y+hLM=
MacOS X
In MacOS X, ATEX comes as a .DMG (disk image) with ‘atex’ (Mac executable) only. We did it on purpose in order to preserve rights to execute on that file (Windows does not support that). In order to extract the executable file (atex with no extension), simply double-click on the DMG file to mount it (on MacOS X). You can then copy the executable file onto a USB flash drive; if you want to preserve execution rights, make sure the flash drive is formatted with HFS+. Alternatively, you can use it from any folder on that Mac computer.
Using ATEX on Mac systems is similar to Windows usage. The differences are slim. In Windows, if you want to extract a token from a different user, you’ll be specifying the password in the command line. On a Mac, the password is prompted by the system in interactive mode. In addition, in Mac environments, you’ll be using the “-u” option before the user name. The final difference is in the output format. In Windows, you’re getting a plain text file. On a Mac, you’ll receive a .plist (XML) file.
The correct way of launching ATEX on a Mac is launching the console, changing the current folder (‘cd’) to one where ‘atex’ is stored, and then launching APEX.
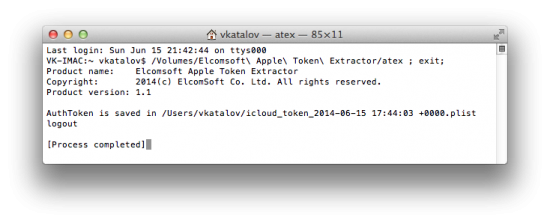
In order to list users with authorization tokens, and in order to extract tokens for users other than the currently logged in user, you’ll need root privileges. As a result, you’ll need to use sudo to launch ATEX (you’ll be prompted for root password):
sudo atex -l
or
sudo atex --iCloudUserList
To extract a token for a certain user:
sudo atex --getToken -u <username>
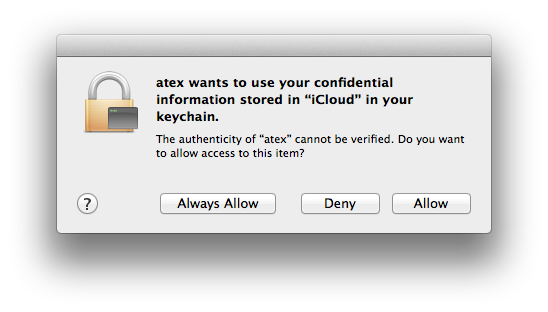
Finally, when you first launch ATEX on a Mac, the system will prompt you to allow access to keychain. Naturally, you’ll have to allow access.
Using the Token
So now you have extracted one or more tokens. How do you actually use them? Let’s start from what’s inside the token file. On Mac, you’ll see a .plist file with the following content:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>vkatalov@mail.ru</key>
<string>564819206:AQZACBBTkK40ICFpLxkH/iDbAPEnTtlLyWbXLEw=</string>
</dict>
</plist>
In this file, the following line is a token. You’ll need to enter the entire line into EPPB:
564819206:AQZACBBTkK40ICFpLxkH/iDbAPEnTtlLyWbXLEw=
The second part of the line is the actual token; the first part is the user’s Apple ID in Apple’s internal notation.
Everything else in that .plist file (such as the user’s actual Apple ID) is stored for your information only, and is not used for the acquisition process.
The rest is simple, and has no differences from acquiring iCloud backups using the Apple ID and password. There are several notes to take:
- There is no way to recover the original password from the token.
- If the user logs out of iCloud Control Panel, the system deletes the token, and Elcomsoft Phone Password Breaker cannot obtain it. However, you can try carving the disk.
- A new token is created every time the user logs in to iCloud Control Panel with their login and password. Interestingly, existing tokens are not invalidated, and can be used to retrieve iCloud backups just like the latest token.
- If the user logs in to iCloud Control Panel on different computers (but using a single Apple ID), the tokens will be different, but any of them will work with EPPB.
- While the tokens may expire after awhile, we don’t know their exact expiration.
- If the user changes their password, old tokens will no longer work.
- You can use ATEX from a USB flash drive with no installation. The tokens will be stored onto the same flash drive.
What Else Is New
Did I just say the new Phone Password Breaker is all about iCloud access? While password-free access is major news, we have many new improvements made to the latest Phone Password Breaker. In particular, we added GPU acceleration support for the latest generation of NVIDIA Maxwell video cards and updated our Open SSL code to a new version non susceptible to the Heart Bleed bug. There are other additions and enhancements. The full list includes:
Added GPU acceleration support for NVIDIA Maxwell video cards. The new Maxwell architecture is fantastic! At this time, only one board based on this architecture is available. This is the entry-level GTX 750. However, we expect new high-performance cards (the 800-series) to come soon. I think they are going to beat top AMD cards which, at the time, are power-hungry beasts.
Open SSL has been updated to a version not vulnerable to HeartBleed. You probably heard about HeartBleed. If not, you can get more information here. EPPB uses OpenSSL to download iCloud and Windows Phone backups. The latest release uses an updated version of OpenSSL having no HeartBleed bug.
The current password and the number of remaining passwords are displayed during the attack. This progress data can come handy during the attack.
More reliable iCloud acquisition over slow connections. iCloud is not the fastest cloud on the market. Combined with a slow, unreliable connection it could become a true headache. We have much improved our algorithms to make acquisition over slow, unreliable connections much more reliable.
Improved reliability on multi-GPU configurations. Fixed intermediate crashes when two or more GPUs were used.
Multiple GUI improvements. We gold-plated the bells and whistles, coloring some UI controls to make them more readable.
Keychain data loaded and decrypted much faster. The beta version had a delay opening the keychain in the “Keychain explorer”. We fixed the bottlenecks to eliminate the delay.
No authentication is required when re-downloading iCloud backups. While no substitute for true multi-user acquisition (please stay tuned!), we implemented a mechanism allowing you to re-download information from iCloud (e.g. with different options applied, such as categories) without having to enter the password again.
More information in the Journal. We expanded information stored in the Journal, in particular adding snapshots processing data.
Bug fixes. We fixed a few annoying bugs here and there, for example, fixing the crash when displaying the keychain in full screen.













