Each iteration of iOS is getting more secure. With no jailbreak available for the current version of iOS, what acquisition methods are available for the iPhone 7, 7 Plus and other devices updating to iOS 10? How does the recent update of Elcomsoft iOS Forensic Toolkit help extracting a locked iOS 10 iPhone? Read along to find out!
iOS 10: The Most Secure iOS
When iOS 8 was released, we told you that physical acquisition is dead. Then hackers developed a jailbreak, and we came up with an imaging solution. Then it was iOS 9 that nobody could break for a while. The same thing happened: it was jailbroken, and we made a physical acquisition tool for it. Now it’s time for iOS 10.2 and no jailbreak (again). While eventually it might get a jailbreak, in the meanwhile there is no physical acquisition tool for iOS 10 devices. Considering that iPhone 7 and 7 Plus were released with iOS 10 onboard, your acquisition options for these devices are somewhat limited.
Plan “B”
With no jailbreak available for iOS 10, what are your options? If you have the latest Elcomsoft iOS Forensic Toolkit, use “plan B” instead!
By using the “B” command from the main menu, you’ll force the iPhone to dump its content into a local backup. Once the local backup is created, you’ll be able to view it with Elcomsoft Phone Viewer or another forensic tool.
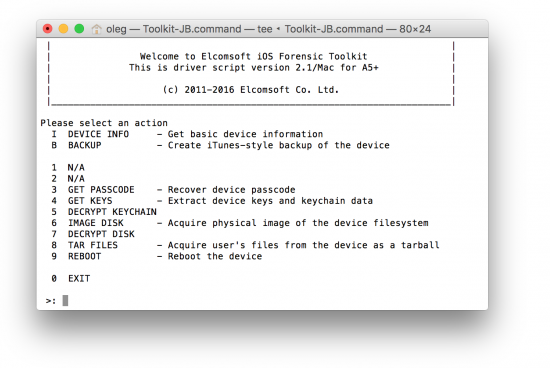
The “plan B” attempts to produce a backup, which is great if you have an iPhone that you can unlock by using a passcode or Touch ID. But what if you don’t know the passcode and don’t have access to a fingerprint, or if the fingerprint has already expired and the phone requires a passcode to unlock? In this case, you would have to use a so-called lockdown record.
Lockdown Records
Lockdown records, or pairing records, are simply files that are stored on the computer to which the iOS device syncs to. These files are created the first time the user connects their iOS device to a Mac or PC that has iTunes installed. Lockdown records are used to re-establish a pairing relationship between the computer and iOS device, allowing the user to conveniently sync their iPhone by simply connecting it to their computer without repeatedly unlocking the device.
If you can obtain a valid lockdown record, you may be able to force the iPhone produce a local backup even if you cannot otherwise unlock it. However, you’ll be only able to use lockdown records if the iPhone in question was unlocked with passcode at least once after it was powered on or rebooted. Otherwise, the local backup service (com.apple.mobilebackup2) will not be started, and you’ll be unable to use lockdown records or initiate a backup.
In macOS, lockdown records are stored at /var/db/lockdown. Starting with macOS Sierra, Apple restricts access to this folder. If you are analyzing a live system, you’ll need to manually grant access rights to this folder.
In Windows, lockdown records are usually stored at the following locations.
Windows Vista, Windows 7 and newer: %ProgramData%\Apple\Lockdown
Sample path:
C:\ProgramData\Apple\Lockdown\
6f3a363e89aaf8e8bd293ee839485730344edba1.plist
Windows XP: %AllUsersProfile%\Application Data\Apple\Lockdown
Sample path:
C:\Documents and Settings\All Users\Application Data\Apple\
Lockdown\6f3a363e89aaf8e8bd293ee839485730344edba1.plist
When analyzing a live system, iOS Forensic Toolkit will attempt to extract lockdown records for the current user. If the system you are investigating is offline or if you’re using a disk image, your best option is extracting the content of these folders and copying it to a convenient location on your computer. We recommend using short paths and file names (e.g. “d:\lockdown\file1.plist”) for convenience as you’ll have to type in the full path.
By using a lockdown record, you can force the phone make a full device backup without using the passcode or fingerprint to unlock.
Password or No Password?
When using iTunes to create a local backup, you are given an option to encrypt the backup with a password. If no backup password is set, we always recommend going for the second option and setting a known password to encrypt the backup. When parsing password-protected backups you can decrypt keychain items, while backups without a password encrypt keychain with a hardware-dependent key that’s impossible to crack.
iOS Forensic Toolkit automatically sets a simple password (“123”) if backup password is not specified. If there is a backup password already and you don’t know what it is, you’ll have to use Elcomsoft Phone Breaker to recover it first.
Physical or Logical? The Compatibility Matrix
It’s hard to keep pace with all the recent developments. Is physical acquisition available for a given iPhone? Is this or that version of iOS supported? We made a compatibility matrix to give you an idea of what we can do at this time.
|
iOS 5…7.x |
iOS 8…9.3.3 |
iOS 9.3.4/9.3.5 and 10.x |
| Legacy (iPhone 3…4) |
No restrictions, full imaging |
– |
– |
| 32-bit (iPhone 4s…5c) |
Jailbroken: full imaging; passcode recovery
No jailbreak: logical acquisition (if unlocked)
|
Jailbroken: full imaging; passcode recovery
No jailbreak: logical acquisition (if unlocked)
|
Logical acquisition (if unlocked) |
| 64-bit (iPhone 6/6s/7/Plus) |
– |
Jailbroken: file system extraction via “TAR Files”
No jailbreak: logical acquisition (if unlocked) |
Logical acquisition (if unlocked) |
*) (if unlocked) means known or empty passcode; unlocked with Touch ID; or unlocked with a valid lockdown record (only available if device was unlocked with Touch ID at least once after last reboot).
Locked Out
What happens if you’re completely locked out? This can happen if the device was rebooted and never unlocked afterwards, or if you simply lack any means to unlock the device. If this happens, you can still use the Device Information option in iOS Forensic Toolkit. At very least, you’ll be able to access information about the phone including such as the model name and number, as well as its serial number.
[sgmb id=”2″ customimageurl=”” ]



