According to surveys, the average English-speaking consumer maintains around 27 online accounts. Memorizing 27 unique, cryptographically secure passwords is nearly impossible for a person one could reasonably call “average”. As a result, the average person tends to reuse passwords, which means that a single password (or its simple variations) can be used to protect multiple online accounts and services. The same passwords are very likely to be chosen to protect access to offline resources such as encrypted archives and documents. In fact, several independent researches published between 2012 and 2016 suggest that between 59 and 61 per cent of consumers reuse passwords.
Considering how consistent the numbers are between multiple researches carried out over the course of four years, we can safely assume that around 60% of consumers reuse their passwords. How can this data help us break passwords, and how did we arrive to the value of 70% in the title? Read along to find out!
Password Reuse: Gathering the Low Hanging Fruit
According to the online survey, which surveyed more than 2,000 English-speaking adults in 2016, the average person has 27 discrete online logins. “What the study does not say, however, is how many actual passwords each participant has for his or her 27 logins. One thing is for sure: It’s a lower number”, says Joseph Bernstein, BuzzFeed News Reporter [ Source ]
So how many discrete passwords does the average person have? Or actually, how many passwords do YOU have? You can easily find out by using our new tool. Well, actually, it’s an old tool that we recently updated with one important function: the ability to extract all passwords cached by Internet browsers and mail clients on the user’s computer, filter the list by removing duplicates and saving it into a custom dictionary file – ready to be used for brute-forcing passwords to your other (much better protected) data.
So let us see how many passwords you have! For that you’ll need a full version of Elcomsoft Internet Password Recovery 3.0 (or newer). Launch the product and push the “Export Passwords” button on the toolbar (highlighted).
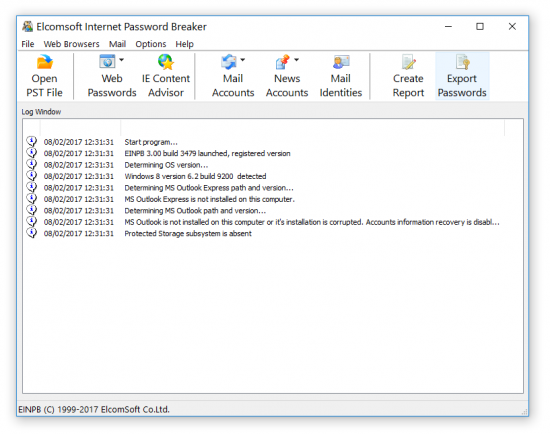
Once you push the button, you’ll be prompted for a file name to save your password list. Enter the name and wait a few seconds. Elcomsoft Internet Password Breaker will automatically scan your computer for available passwords including password storage systems in Chrome, Internet Explorer, Edge, Outlook, Windows Mail and about a dozen other browsers and email clients.
Once the list is saved, open it with any viewer or editor that supports Unicode (yes, we support international passwords). How many discrete passwords can you count? (I have 83, by the way).
That was easy. Too easy perhaps. But sure enough your important files (archives, documents, encrypted volumes and so on) are not encrypted with any of those passwords, are they? Well, this is not the case for the average person. According to several studies, 59 to 61 per cent of consumers repurpose their passwords to protect different types of data. This means we can try using the passwords we’ve just discovered to unlock other stuff – like password-protected Office 2013 documents, encrypted RAR5 archives or BitLocker volumes.
Brute Force Your Way into Secure Encryption Using the Password List
If you are given a task of unlocking a bunch of password-protected documents, you’re assigned a tough job. Even if you use one of the best password recovery tools running on top hardware, you’re still looking at about 7,000 passwords per second when breaking an Office 2013 document on a PC with a single NVIDIA GTX 1080 board. With this kind of a speed, brute-force is no longer an optimal strategy.
Dictionary attacks are a better strategy (and the only one that actually works for resources protected with very low recovery speeds), but using the general dictionary of English language may be too much for speedy attacks and too little to actually break the password.
A quality custom dictionary is absolutely necessary when attacking files protected with strong encryption. Can you imagine a higher quality dictionary than one containing the user’s other passwords?
Assuming that your passwords were saved into a file named “password-list.txt” here’s how you configure the pipeline.
- Use “password-list.txt” as a custom dictionary; no mutations.
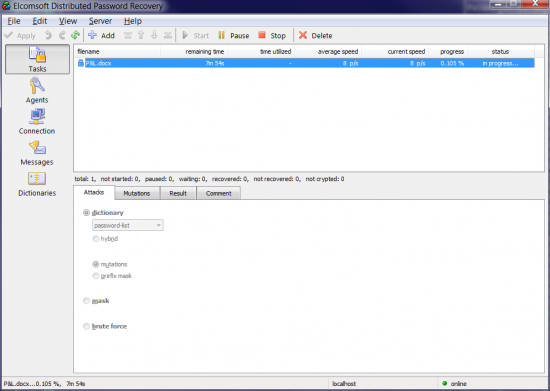
- Using the same dictionary, enable a single mutation that appends 0 to 4 digits to the end of the password.
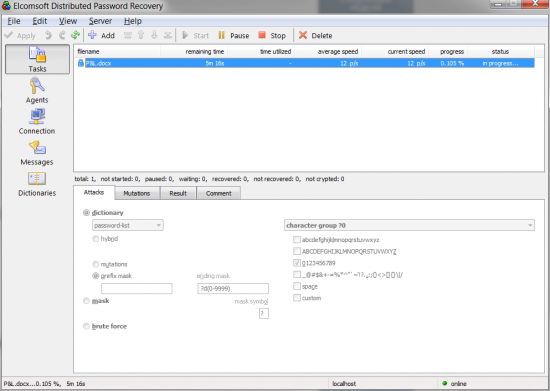
- Using the same dictionary, configure the following mutations (Case/Digit/Year) as shown on the screen shot:
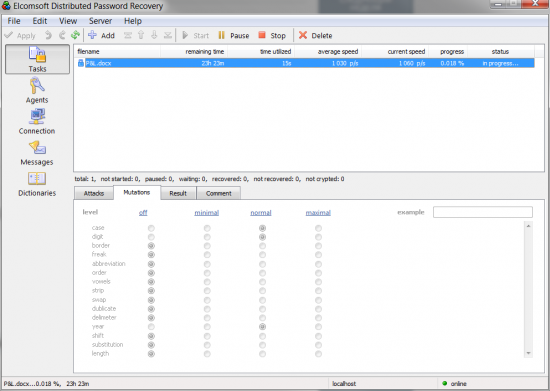
Using the first attack only takes a moment, and can solve up to 60 per cent of cases. The second attack is slower, but it still takes just a couple minutes (assuming that the custom dictionary consists of 100 or less unique passwords). The final attack may take a lot longer; you can customize it so that it tries a reasonable number of combinations. However, considering the tiny size of the custom dictionary we’re using, you still have great chances of this attack finishing in reasonable time. Statistically, the two attacks can solve up to 70 per cent of cases, albeit the last one can take longer than just a few minutes.
What if none of those passwords worked? If this is the case, you can set up a similar attack pipeline using the Top 10,000 Passwords list referenced in our previous publication.
Conclusion
Building a high-quality custom dictionary that contains all of the user’s cached passwords is now possible with a single click. Just a few minutes of work may help you solve 60 to 70 per cent of cases much faster than you could imagine. We recommend using the following tools:
– Elcomsoft Internet Password Breaker (for extracting passwords and building a custom dictionary)
– Elcomsoft Distributed Password Recovery (for brute-forcing passwords to a variety of formats on one or several computers)
– Elcomsoft Advanced Office Password Recovery (for breaking passwords to office documents)






