In this how-to guide, we’ll cover the steps required to access the list of saved wireless networks along with their passwords.
Step 1: Make a password-protected backup
In order to extract the list of Wi-Fi networks from an iOS device, you must first create a password-protected local backup of the iOS device (iPhone, iPad or iPod Touch). While we recommend using Elcomsoft iOS Forensic Toolkit for making the backup (use the “B – Backup” option in the main menu), Apple iTunes can be also used to make the backup. Make sure to configure a backup password if one is not enabled; otherwise you will be unable to access Wi-Fi passwords.
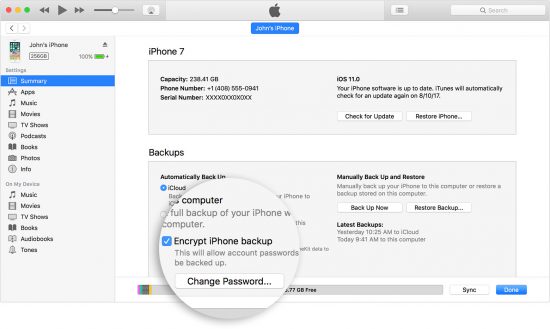
Important: if you are performing a forensic extraction, we highly recommend using iOS Forensic Toolkit in order to make the backup. Unlike iTunes, iOS Forensic Toolkit does not attempt to “sync” the iOS device being acquired with the computer you connect it to, ensuring that no changes are made to device data. More information on how to use iOS Forensic Toolkit for logical acquisition: iOS Logical Acquisition: The Last Hope For Passcode-Locked Devices?
Note: if you are using iOS Forensic Toolkit to produce a backup, the tool will automatically set a temporary backup password. The password will be “123”; you will need to use this password when opening the backup with Elcomsoft Phone Viewer.
If the device is locked with an unknown passcode, follow this guide: Acquisition of a Locked iPhone with a Lockdown Record
Step 2: Recover backup password
This step is only required if the backup is protected with an unknown password. If you know the password (or specified one during the first step), skip this step and go directly to Step 3.
To recover the password, do the following:
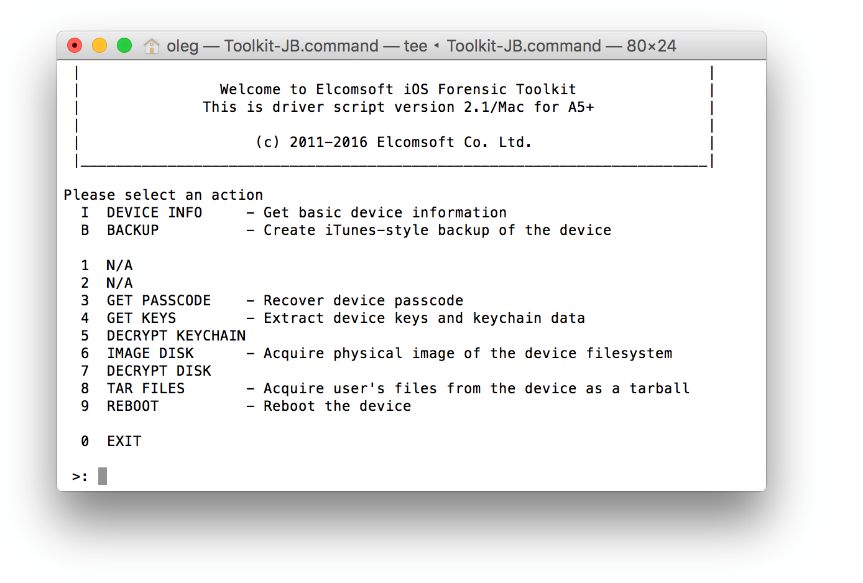
1. Open Elcomsoft Phone Breaker
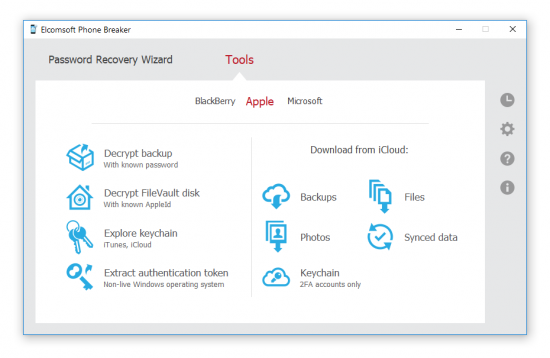
2. Password recovery wizard | Choose source | iOS device backup
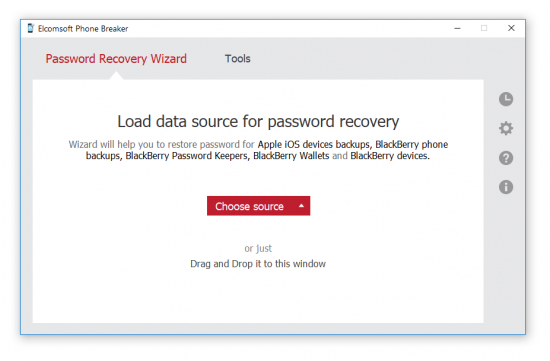
3. The list of available backups will be displayed. At this point, you may select an existing backup from the current PC.
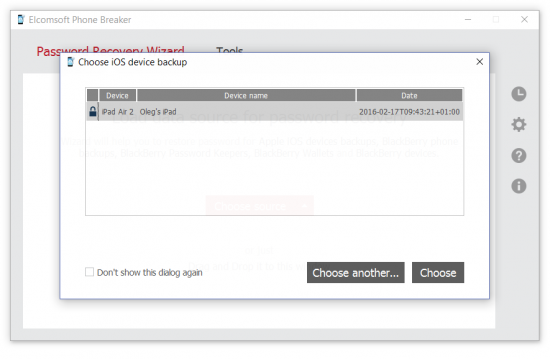
If you are processing the backup extracted on a different computer or created with iOS Forensic Toolkit, select “Choose another” and specify path to the manifest.plist
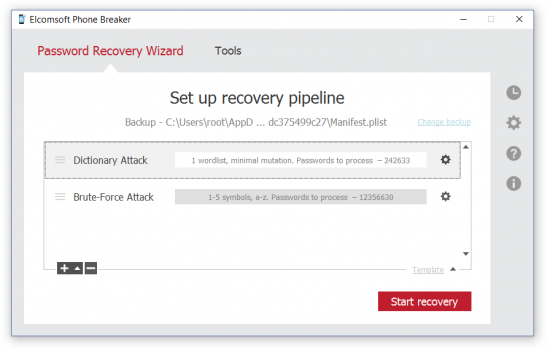
4. Default attack settings will be available. If you are content with default attack settings, you may begin the attack by clicking the “Start recovery” button.
5. Once the password is discovered, it will be displayed.
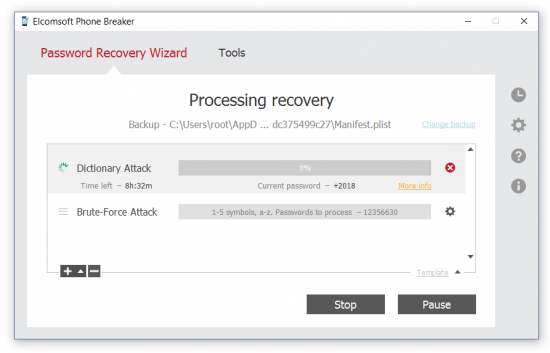
Once the password is recovered, you may optionally decrypt the backup in Elcomsoft Phone Breaker. Alternatively, you may open the backup in Elcomsoft Phone Viewer, in which case it will be decrypted automatically (although you will need to supply the backup password).
Step 3: Open the backup in Elcomsoft Phone Viewer
In order to access the list of Wi-Fi networks and view Wi-Fi passwords, you will need to use Elcomsoft Phone Viewer 3.50 or newer.
1. In Elcomsoft Phone Viewer, open the backup.
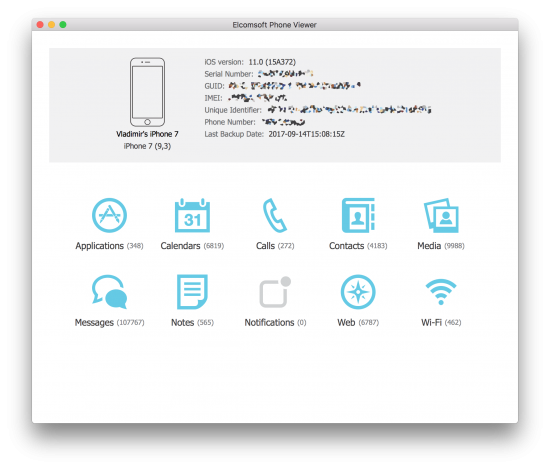
2. If the backup is encrypted, provide backup password in order to decrypt the backup.
3. Once the backup is opened, select “Wi-Fi”. The list of available Wi-Fi networks along with their passwords will be displayed.

Note: by default, Wi-Fi passwords are masked. To unmask Wi-Fi passwords, click on the “eye” icon next to the masked text in the “Wi-Fi Password” column.











