After testing waters for more than a year, Google has finally pulled the plug and began blocking access to Google Play services on uncertified devices. Why Google took this step, who is affected, and what it means for the end users? Let’s try to find out.
Google Play Services Certification
In March 2017, Google rolled out a Google Play Services update that had a very minor addition. At the very bottom of its settings page, the Services would now display device certification status.
This is how it looks on an uncertified device:
What is this all about?
In order to use Google Play Services (the most prominent of which is the Google Play Store), smartphone manufacturers must sign a MADA agreement with Google. This agreement places certain restrictions on OEMs; for example, the agreement explicitly prohibits participants from “forking” Android, or manufacturing Android-based devices that are not Google certified. This, for example, is the reason why Amazon does not manufacture a single Google-certified device, as Amazon Fire OS is a classic Android fork. In addition, the terms of agreement disallow manufacturers pre-installing non-Google application stores (such as Amazon App Store or Yandex.Store), and require prominent placement of Google search bar and certain Google apps.
OEMS who signed the agreement must certify their Android devices with a Google-approved lab. Such certification, among other things, ensures compatibility and compliance with Android Compatibility Definition Document. Among other things, the Document defines a lot of security-related functions such as enforcing full-disk encryption on devices released with Android 6.0 and newer, or ensuring that the fingerprint scanner and other forms of biometric identification are disabled immediately after the boot until the device is unlocked with a passcode (or pattern) at least once.
Finally, the lab certifies that the device ROM does not include malware, which was a huge problem a few years back (and could be still a problem with many Chinese manufacturers).
Apparently, not all Android OEMs would choose the straightforward patth. Many smaller manufacturers, particularly those in China (e.g. Bluboo, Meizu, Xiaomi), would opt to ignore Google certification and release non-compliant devices with Google services. While most such devices were only available to the Western consumer through Chinese online outlets, some phones (such as the global versions of Meizu Pro 6 and Pro 6 Plus) were officially brought to Europe and sold through local retail and online stores including Amazon.
Meizu smartphones sold in Europe employ what Meizu thought to be a smart trick. Out of the box, the device does not have Google Play services installed, so it does not violate anyone’s intellectual property. After initial setup (which obviously does not allow restoring backups from Google Drive), the user can voluntarily open the Meizu App Store and download the so-called “Google Installer”.
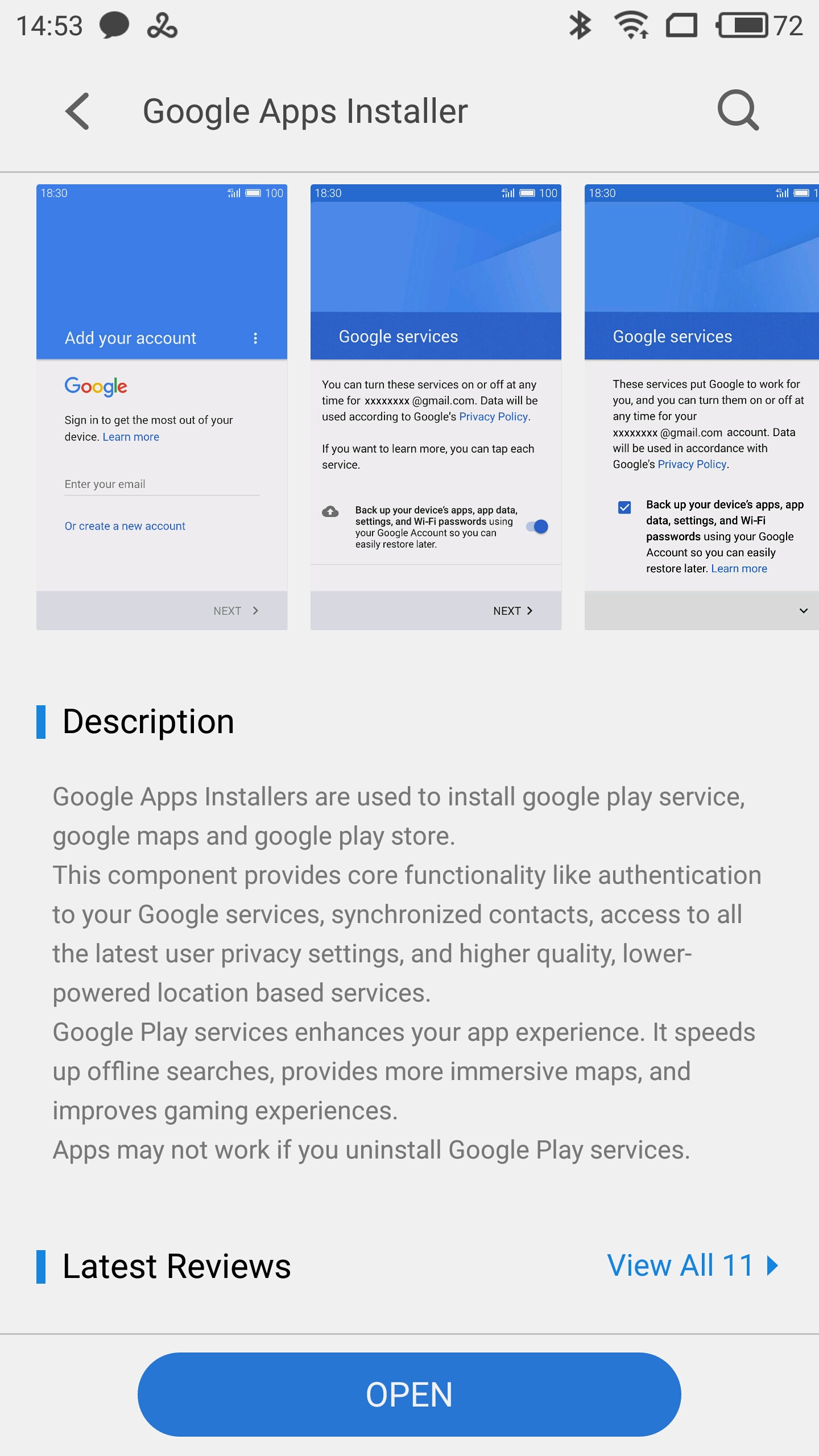
Once downloaded, the app obtains and installs Google services including Google Framework, Google Play Services, Calendar Sync and Google Play Store. The app is not made by Meizu; it is the user’s responsibility to obtain and to use the app to gain access to Google services.

Other than that, Meizu smartphones are a compatibility disaster. They don’t have encryption at all (let alone forced encryption), and they completely ignore Google’s security requirements (in particular, enabling the fingerprint reader immediately after boot). There would be no way such a device would pass Google certification.
Meizu was not alone. Some OEMs would release their smartphones with “unofficial” (extracted from other ROMs) Google services, often pre-installing malware alongside. Apparently, Google was never happy about it. The company set a goal to make things right.
The first step Google made in March 2017 added Google certification status to the bottom of the settings list. At the same time, Google started contacting vendors to inform them that Google will start enforcing certification in near future. Vendors were given an option to sign the MADA agreement, in which case their existing non-certified devices would be grandfathered. Vendors who did not sign the agreement, or who did not certify their devices, would be risking to have Google Play services blocked from their devices.
In Google now blocks GApps on uncertified devices, but lets custom ROM users be whitelisted, Mishaal Rahman from XDA Developers reported that Google has started entirely locking out newly built uncertified firmware from accessing Google services.
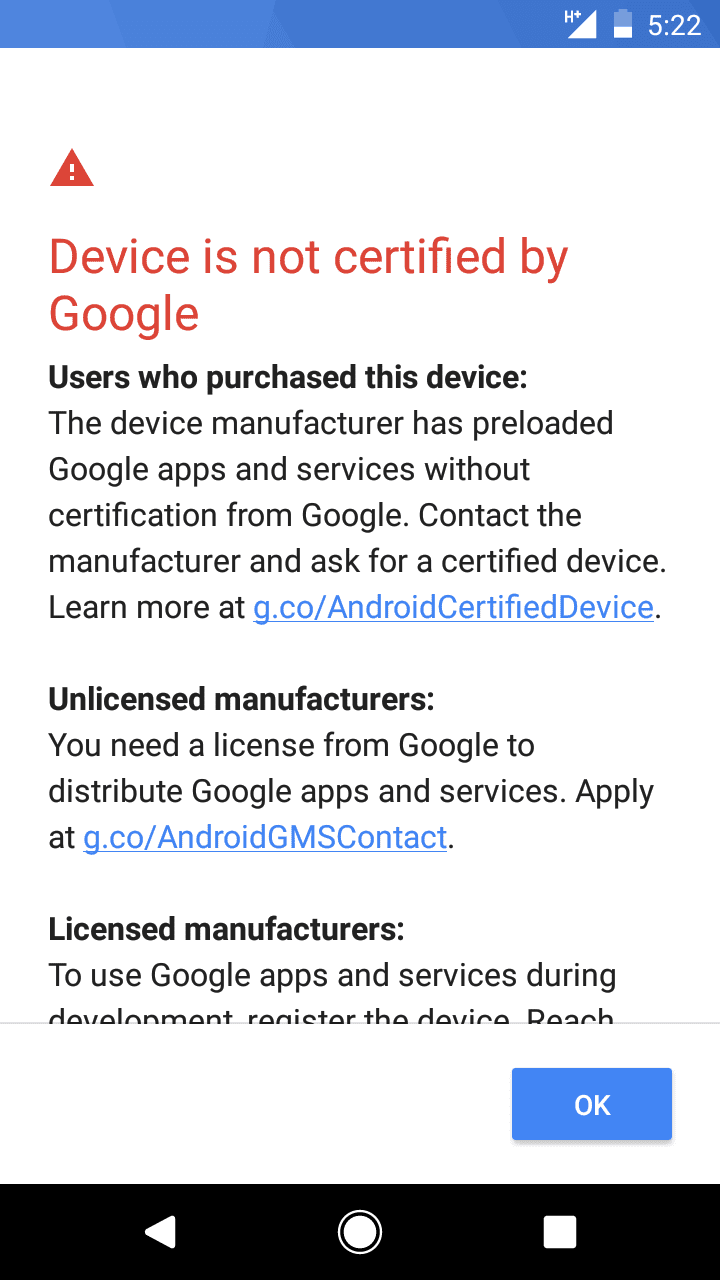
If the user is attempting to set up a new uncertified Android device, they may be disallowed from signing in to their Google Account. This only happens if the uncertified device is running a recently built firmware (according to Mishaal, the change went into effect March 16th and affects any software builds made after this date by checking ro.build.fingerprint for the build date).
If you are a regular consumer and have just purchased the device, you may turn to the vendor to request that they certify the device (or, better yet, simply return the device back to the store, as such post-factum certification is very unlikely to happen). Custom ROM users who deliberately installed non-certified software can whitelist individual devices by visiting g.co/AndroidDeviceRegistration (which currently redirects to https://www.google.com/android/uncertified/). The registration process is not the simplest one, but still allows users of custom ROMs to access Google services, so power users may opt to install Magisk instead, which fixes access to Google services without requiring device registration.
Device makers will have to contact Google to have the device certified by going through the proper certification channel.
The Meaning of It
Google services certification is not meant to block or limit the use of custom ROMs. We are yet to see what happens if a user installs a custom ROM on a device that was properly certified by the vendor (it could be that the device would be whitelisted by IMEI). Instead, Google is going after unscrupulous manufacturers who bypass the proper certification channels in order to slip their malware-ridden, highly insecure devices to unsuspecting consumers. Does it really work? It seems to be working as intended. We have recently heard that the newer Meizu Pro 7 smartphone has been properly certified.
Additional resources:






