We were attending the DFRWS EU forum in beautiful Florence, and held a workshop on iOS forensics. During the workshop, an attendee tweeted a photo of the first slide of our workshop, and the first response was from… one of our competitors. He said “Looking forward to the “Accessing a locked device” slide”. You can follow our conversation on Twitter, it is worth reading.
No, we cannot break the iPhone passcode. Still, sometimes we can get the data out of a locked device. The most important point is: we never keep our methods secret. We always provide full disclosure about what we do, how our software works, what the limitations are, and what exactly you can expect if you use this and that tool. Speaking of Apple iCloud, we even reveal technical information about Apple’s network and authentication protocols, data storage formats and encryption. If we cannot do something, we steer our customers to other companies (including competitors) who could help. Such companies include Oxygen Forensics (the provider of one of the best mobile forensic products) and Passware (the developer of excellent password cracking tools and our direct competitor).
Let’s start with “Logical acquisition”. We posted about it more than once, but it never hurts to go over it again. By “Logical acquisition”, vendors usually mean nothing more than making an iTunes-style backup of the phone, full stop.
Then, there is that “advanced logical” advertised by some forensic companies. There’s that “method 2” acquisition technique and things with similarly cryptic names. What is that all about?
I am not the one to tell you how other software works (not because I don’t know, but because I don’t feel it would be ethical), but I’ll share information on how we do it with our software: the methods we use, the limitations, and the expected outcome.
Logical acquisition with Elcomsoft iOS Forensic Toolkit (EIFT)
If you are familiar with iOS Forensic Toolkit (EIFT), you should know that its main advantage was (and still is) physical acquisition. Physical is only possible for devices with a known passcode (or no passcode at all). It is limited to iOS versions that can be jailbroken (currently up to iOS 11.1.2). There are significant benefits to physical acquisition despite the risks involved due to jailbreaking, but those are outside the scope of this article.
The following logical acquisition options are available in EIFT:
- I (Info)
- B (Backup)
- M (Media)
- S (Shared)
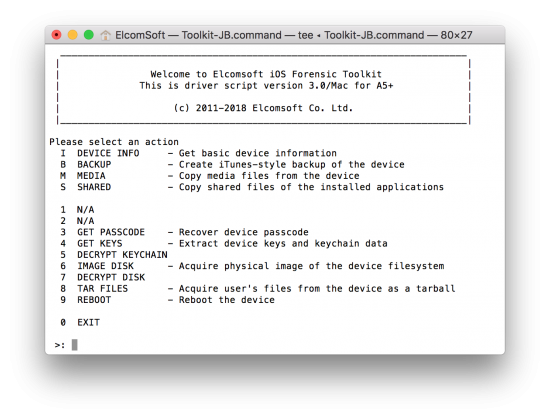
Let’s go though all of them.
Info
This logical acquisition option returns detailed information about the device including device name, exact model designation, iOS version and build number, total/free space, serial number, as well as the list of applications installed. Device information is acquired through the lockdownd service, and application information through installation_proxy. More at What can be extracted from locked iPhones with new iOS Forensic Toolkit, The iPhone is Locked-Down: Dealing with Cold Boot Situations and Obtaining Detailed Information about iOS Installed Apps.
Backup
This is what everyone calls “Logical acquisition”. Backups are created by the device itself the mobilebackup2 service, and saved into a set of files on the computer. That’s it. You send the command that looks like “give me the backup!”, and enjoy your coffee while the backup is being created.
Media
In addition to the backup (which may or may not be encrypted), one can also obtain media files (photos and videos) using yet another mechanism. These files are acquired via the afc (Apple File Conduit) service. This is the service most widely used by various third-party systems, services, applications and even hardware such as most home and car entertainment systems. You can quickly access all the music, photos, videos and books, along with some extra data like the records on how they have been edited, regardless of backup encryption settings. You can read more on that in How to Extract Media Files from iOS Devices.
Shared
By using yet another mechanism, you can access files shared by iOS apps. In iOS, many applications can store some of their files outside of the sandbox (now, that would be hard to get access to). Instead, they opt to share the files to allow access from other programs and the host computer. This includes many office packages, media players, some passwords managers (!) etc. Acquisition is performed via the house_arrest service. More information at Get iOS Shared Files without a Jailbreak.
To pair or not to pair?
In order to use all these features, the device should be paired with the computer (the only exception is the (I)nfo option, which can extract basic device info even without pairing).
There are two ways of doing that:
- Establish a new trusted relationship manually
- Provide an existing pairing record
Up to and including iOS 6, trusted relationship was established automatically and silently once the unlocked device was connected to the computer. That was scary, and presented a real security threat. You could be thinking you were connecting your phone to a charger, but it could have been a malicious computer behind the USB port.
Apple addressed that vulnerability in iOS 7 with the now-familiar “Trust this computer?” prompt.
Fast forward to iOS 11, you now have to unlock the device you are about to connect and provide the correct passcode. You cannot use Touch ID or Face ID to establish a new trusted relationship (see New Security Measures in iOS 11 and Their Forensic Implications for more information).
What happens when you make a trusted relationship? A pair of cryptographic keys is created. One key is kept on the device, and the second, matching key is stored on the computer. Using the keys, the computer can communicate with the iOS device even if it is locked. This ability to communicate is unconditional for iOS 7 and older. In iOS 8 and up, you can only do it after the device has been unlocked at least once, simply because most data on the device is encrypted with a cryptographic key calculated by combining data from a hardware key and the user’s passcode. In addition, most of the services mentioned above are not yet running before the device is unlocked.
If, however, you have physical access to the computer (PC or Mac) with established trust relationship for the particular device, you can then obtain a lockdown record from that computer and transfer it to your own computer to make it a trusted one. This is essential for understanding trusted relationships: the lockdown record is not tied to a particular computer; it’s simply a file that can be copied around and used on a different Mac or PC!
Starting with iOS 7, pairing (lockdown) records do expire. The exact expiration time is not known. What we do know is that it was at least 6 months for older versions of iOS, reduced to about 10-14 days in iOS 11. Since iOS 11.3, Apple officially documents the lifespan of lockdown records, which is now 7 days only according to the latest Release Notes (see iOS 11.3 Adds Expiry Date to Lockdown (Pairing) Records). While this puts an obstacle to logical acquisition via lockdown records, it also means that you’ll have to re-pair your own device every week when connecting it to your computer or a wired entertainment system (e.g. your car, home audio system using a Lightning port etc.) This is yet another trade-off between convenience and security, and one bad news for forensics.
Going back to the days of iOS 7, some of these mechanisms worked a bit “wider” than intended or described, allowing us to access more data. It also used to work over Wi-Fi. iOS 8 was a major security overhaul, while iOS 9 further improved security. Still, you can access pretty much everything once you have a valid, non-expired lockdown record – even for locked devices. This is NOT a vulnerability, but a well-documented way the iOS is designed to work.
iOS system services, a.k.a. “backdoors”
We didn’t discover America by telling about all those services. They were researched in detail by the forensic expert Jonathan Zdziarsky several years ago, and you can easily find his presentations on this topic, such as Identifying Back Doors, Attack Points, and Surveillance Mechanisms in iOS Devices. In fact, most forensic products make use of one or more of those services/protocols. Everything beyond backups is usually called “advanced” or given a cryptic “numbered” name instead of properly describing how they work and what the limitations are. Instead, they often go for things such as “We were able to extract 2,387 images with method 1 and 4,933 images with method 2 from our test iPhone 6S running iOS 10.0”.
All the functions mentioned above (among many others) are implemented in the open-source libmobiledevice library. It is not free of bugs. While iTunes is not actually needed to use the lib, you still have to have it installed in order to get the Apple Mobile Device driver (it is technically possible, though not very easy, to install just the driver).
You should also know that on iOS 8+ devices, all those services (except lockdownd) only start after the device is first unlocked. Consequently, if the device has not been unlocked after a reboot, you will be able to get only device information (even with a lockdown record).
What are the benefits?
You may wonder why one may ever need to use software such as ours to acquire a backup (and other data) if that can be easily done through iTunes? In fact there are several reasons.
First, using forensic software is, well, forensically sound, at least compared to acquisition through iTunes. Once you connect the device to the computer, it may start syncing immediately (though syncing may be disabled in advance; still, we are not sure whether iTunes makes any changes to the device contents once connected, probably yes).
Second, our software can use lockdown records, so it has the ability to acquire locked devices. As we already mentioned, some limitations apply. Of course, you need to have a lockdown record itself obtained from a PC or Mac. Next, the lockdown record must be valid (non-expired). And finally, the iPhone must be unlocked at least once after the last reboot; otherwise the logical acquisition is limited to just accessing advanced device information (which is still a lot better than nothing).
Third, you may encounter a situation when a backup is locked with a password. iOS 11 now allows resetting the iTunes backup password (see iOS 11 Makes Logical Acquisition Trivial, Allows Resetting iTunes Backup Password), but if you are working with a device running an older version of iOS and the backup password is strong, then acquiring Media and Shared files is about all that could be done. This is still much better than nothing, especially since media files may contain location meta data in their EXIF tags.
Oh, one more thing. If a backup password is not set, EIFT automatically sets it to “123”. That way you will gain access to more data compared to an unencrypted backup, including the keychain and Health data. Of course you can set the password manually through iTunes, but that is often overlooked.
Physical? What physical?
The term physical acquisition is probably harder to define than logical. Originally, physical acquisition meant obtaining bit-precise copy of the device storage, without modification (at all) of the original device contents. Speaking of iOS devices, it is only possible for legacy hardware (up to iPhone 4), thanks to vulnerabilities in bootrom code. We introduced full physical acquisition soon after iOS 4 release (the first iOS version with full disk encryption; it was trivial for iOS 1-3, no 3rd party software was required).
Now it may mean virtually everything, but usually means obtaining the full copy of device file system (including the data not available with logical acquisition). And yes, we use term ‘physical’ too 🙂 In our software, physical acquisition now (for newer iPhones) means creating the TAR archive of all files from the device, but it is available only when/if you can install the jailbreak first, so that process is NOT forensically sound, and you should should know that, and afford all the risks involved. However, that way you can obtain far more information than with logical acquisition — including application data, location history, downloaded emails etc. In many cases, it worth it (but always start with logical, anyway).
A word on mobile forensic market
Back to what we started this article from.
It is a hot topic now. No, I’m not speaking of the challenges we experience (believe me, we have a new challenge every second day), but about the competition.
We love competition, and competition is something we cannot live without – and it is definitely good for everyone, especially to consumers.
Not every vendor plays fair though. I mentioned two good vendors, Oxygen Forensics and Passware, who provide excellent products and who we love to cooperate with. I can say no single bad word about them, and will be happy to recommend them to our customers. If there is something our software does not do, we’ll simply recommend a customer to try their software.
The thing is, no single software package covers 100% of one’s forensic needs. If you hear something like “Our software does it all, and you will not need anything else”, I would recommend staying far away from that company.
That’s not the only red flag. A “very unique method” should also make you worry if no technical details are disclosed. In most cases, these methods are based on researches made by someone else without a proper credit or even a reference. While it’s fine to use such researches, calling it “new” and “unique”, and making no reference is unfair. This is especially common in Android forensics. Do you know what “Advanced ADB” acquisition for Android” is? Search for “Dirty Cow” (or CVE-2016-5195). Curious how Samsung S7 is cracked? Through engineering firmware leaked from Samsung breaching into TEE (I’m not kidding, blame Samsung engineers for weak implementation).
I also remember the case when one company said “[PRODUCT] is also the only cloud forensics tool to support two-factor authorization on Google and iCloud services”. Of course they were not the only, and not even the first on the market. I noted it in our corporate Twitter; they never replied, but now their advertising materials say “[PRODUCT] is the only solution that leverages cloud, computer, and smartphone artifacts to examine cloud data. This unique capability allows examiners to extract cloud evidence [..] and pull more evidence from cloud sources than any solution. It also supports two-factor authorization on Google and iCloud services”. Still not completely true (about the only and unique), but slightly better.
There are often some truly amazing things exclusively available as a service. Pack your device and send to the vendor (who might be located in another part of the world). Privacy and security? You decide.
There are usually no universal access methods even for a single smartphone vendor, be it Apple, Samsung, Motorola or whatever. The limitations are often not mentioned, and you might be really surprised that a method that worked for “model 600” did not in fact work with the “model 600A”, or even the “model 600” running a newer firmware.
What else? The number of supported devices is often inflated by counting the number of “profiles” and not actual devices, such as counting iPhone 6s models MKQY2LL/A, MKR12LL/A, MKQX2LL/A and MKR22LL/A as different devices while in reality the color is the only difference. Since different vendors put different meaning to the “profile”, they are virtually impossible to compare – and you almost never know the number of unique models they support. For example, A1633 and A1688 could be considered different devices as they support different LTE bands.
Forensic hardware? Don’t let the marketing people cheat you. A “device” for smartphone acquisition is usually a tablet with software built-in. It cannot work any better than the software, and usually its only purpose is to protect the software from reverse-engineering. The only exceptions are devices for JTAG and passcode cracking, but those are frequently available from AliExpess and other Chinese outlets at a fraction of the price.
We believe the amount of information the company reveals about their software and their methods is one of the most important indicators. The more transparent the company is about its products, the better. You might be told the reason for keeping it secret is keeping the vendor (Apple, Samsung or whatever) unaware of the exact vulnerability they are exploiting (might be an easy fix otherwise). While this is partially true, it’s not the whole truth. One of the reasons is not letting competitors “steal” the vulnerability. Another reason is marketing. Attracting customers at whatever price could be more important than retaining them with quality service. After all, who cares if a feature does not work in a particular case if the money has been already paid?



