Tired of reading on lockdown/pairing records? Sorry, we can’t stop. Pairing records are the key to access the content of a locked iPhone. We have recently made a number of findings allowing us to extract even more information from locked devices through the use of lockdown records. It’s not a breakthrough discovery and will never make front page news, but having more possibilities is always great.
Physical acquisition rules if it can be done. Physical works like a charm for ancient devices (up to and including the iPhone 4). For old models such as the iPhone 4s, 5 and 5c, full physical acquisition can still be performed, but only if the device is already unlocked and a jailbreak can be installed. All reasonably recent models (starting with the iPhone 5s and all the way up to the iPhone 7 – but no 8, 8 Plus or the X) can be acquired as well, but for those devices all you’re getting is a copy of the file system with no partition imaging and no keychain. At this time, no company in the world can perform the full physical acquisition (which would include decrypting the disk image and the keychain) for iPhone 5s and newer.
The only way to unlock the iPhone (5s and newer) is hardware-driven. For iOS 7 and earlier, as well as for some early 8.x releases, the process was relatively easy. With iOS 9 through 11, however, it is a headache. There is still a possibility to enter the device into the special mode when the number of passcode attempts is not limited and one can brute-force the passcode, albeit at a very low rate of up to several minutes per passcode.
The worst about this method is its very low reliability. You can use a cheap Chinese device for trying passcodes at your own risk, or pay a lot of money to somebody else who will do about the same for you. Those guys do have more experience, and the risk is lower, but there still is no warranty of any kind, and you won’t get your money back if they fail.
There are other possibilities as well. We strongly recommend you to try the alternative method described below before taking the risk of “bricking” the device or paying big money for nothing.
The First Look
First, let’s get the UDID of the device. That can be easily done with iOS Forensic Toolkit. Just plug in the device and use the “(I)nfo” command. It works regardless of the iPhone lock status, and only requires the device connected with a cable. In the resulting “ideviceinfo.xml” file, you get the model number, phone name (which can sometimes help identify the owner), UDID, iOS version and some other data.
Second, if you have access to any computer that iPhone has been ever connected to, look there first:
Windows:
C:\Users\$USERNAME$\AppData\roaming\Apple Computer\Lockdown
Mac:
/private/var/db/lockdown/
Note: you may be unable to access that folder on macOS unless you have proper permissions set; that can be done with ‘sudo chmod’.
Look for the file {UDID}.plist. This is a so-called “lockdown record”. Is it there? If it is, you pulled the lucky ticket! Copy that file into EIFT folder, run “(I)nfo” again, and provide that file to the program when prompted.
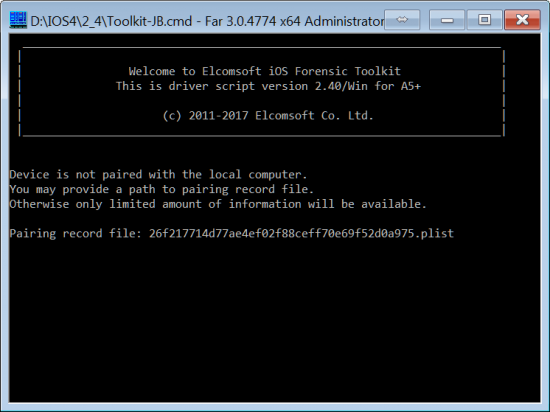
Now things become more interesting.
To Reboot Or Not To Reboot?
It is very important to know what happens with the iPhone after you turn it off or reboot. There are multiple services running in iOS that are listening for commands over USB, but most of them will only start once you unlock the device for the first time after rebooting. The most useful for us is the backup service, the only one needed for logical acquisition. What we actually need is:
- Backup service running
- A lockdown record
What is the lockdown record for? It’s required to establish communication with the locked device. That’s what iTunes does when you connect the iPhone to the computer. If you do it for the first time, you need to establish a trust relationship by confirming that you trust that PC or Mac. Once you do, syncing and creating backups will be done automatically from now on, without the need to unlock the device with Touch ID or passcode.
If you power off or reboot the device and do not unlock it afterwards (with a passcode), iTunes will fail to connect. You will still be able to access some very basic info, but forget about backups. The backup service is not running yet.
Still, there is something in between (basic info and backup) that you can get with a pairing record even if the iPhone is locked after a cold boot. We had a write-up on that recently:
https://blog.elcomsoft.com/2017/10/can-you-unlock-that-iphone/
Now you can see that in action in EIFT. Again, all that works even if iPhone was not unlocked after last reboot. We already described (at the link above) what we can get this way so I will not repeat.
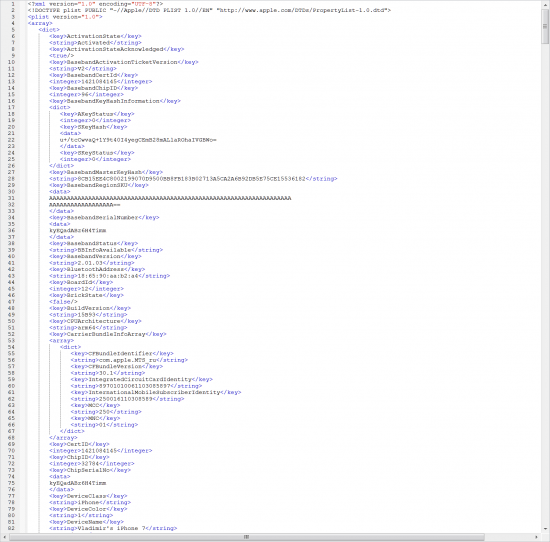
Can We Get Some More?
What if the iPhone we have has been unlocked at least once? It does not matter that the device is still locked now and the passcode is not known. The only thing that matters is that someone has unlocked it at least once after a reboot. Basically, this means that the device is unlocked, sort of. The data partition is decrypted, and the relevant services are running. Use the “(B)ackup” option in EIFT and get a full iTunes-style backup for further analysis and discovery.
Another challenge: what if the backup is password-protected? You can try to recover the password (we have an app for that), but for iOS 10.2+ your chances are extremely low unless the password is very short or simple (or you have a very good dictionary – for example, containing passwords extracted from the user’s computer with Elcomsoft Internet Password Breaker). Ten million hash iterations to check a single password is something where even the best password-cracking company will give up.
However, you can still obtain some information with the “(I)nfo” option (again, only if the device was unlocked after reboot!). This includes the list of applications installed, along with the version numbers. Not much, but better that nothing. Two files are created: applications.txt (with a brief list for quick analysis) and applications.xml (or applications.plist on Mac) with extensive info on everything. It is yet to be carefully evaluated what we can get from there (no app data itself, but some other useful info exists).

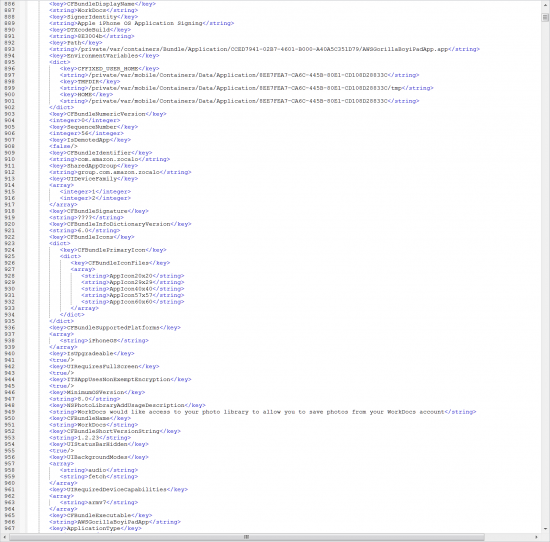
In fact, this is not something new. iOS is still extremely secure, and you already had a chance to do the same thing using various open-source tools if you have enough knowledge, experience and time. We just wanted to make it simpler to leave you more time to do the actual analysis.
One More Thing
Back to physical acquisition. As you know, it can be done for jailbroken devices only, and if you can install a jailbreak, it is the best way to go.
We continuously watch for new jailbreaks, and recently discovered a new one: Saigon for iOS 10.2.1. Not every device is supported, but iPhone SE, iPhone 6/Plus and iPhone 6S/Plus are. iPhone 5S is not on the list, as well as iPhone 7 and iPhone 7 Plus.
Installing this jailbreak is fairly easy. Download Cydia Impactor, sideload the provided .IPA file onto the device (you will have to sign it using any Apple ID during the process; we recommend to register a new one just for that), confirm (trust) new developr’s profile, run the Saigon app – and voila. After that, install OpenSSH, and you can use EIFT to pull location data, mail, Telegram conversations etc.
You know what was the hardest part for us? Finding a supported device still running 10.2.1. To be honest, we are a bit tired collecting different iOS devices and testing all the features of our software on all of them, but we have no choice.
Anyway; EIFT works just fine with that particular jailbreak, we did not even have to modify it, only update the documentation. Disclaimer: no warranties of any kind about jailbreak installation, sorry. In fact the process is very safe and should not brick the device even if something goes wrong; in worst case, jailbreak will just fail, but not affecting the data on the device.
So, what particlar device/iOS combinations do we support now? For logical acquisition and pairing records, there is 100% compatibility (at least starting with iOS 6); as for physical, that is in fact the question of jailbreak availability (while we support all jailbreaks that currently exist). Here is the list of models the jailbreak is NOT available for:
- iPhone 5/5C: 10.0+
- iPhone 5S, 6, 6 Plus: 8.4.1, 9.3.4-9.3.5, 10.3+
- iPhone 6S, 6S Plus, SE: 9.3.4-9.3.5, 10.3+
- iPhone 7, 7 Plus: 10.2+
- iPhone 8, 8 Plus, X
Should we expect a jailbreak for iOS 10.3 and iOS 11? We never know. Exploiting iOS vulnerabilities becomes harder and harder. Apple bug bounty program has been announced over a year ago, and one can get up US$ 200,000 for a critical iOS vulnerability. Jailbreaking usually requires exploiting more than one vulnerability, for different parts of the OS.
EIFT 2.40 is now available, grab it to use lockdown records effectively. In best case scenarios, if the iPhone is unlocked and a jailbreak can be installed, you can pull even more data.






