Even today, seizing and storing portable electronic devices is still troublesome. The possibility of remote wipe routinely makes police officers shut down smartphones being seized in an attempt to preserve evidence. While this strategy used to work just a few short years ago, this strategy is counter-productive today with full-disk encryption. In all versions of iOS since iOS 8, this encryption is based on the user’s passcode. Once the iPhone is powered off, the encryption key is lost, and the only way to decrypt the phone’s content is unlocking the device with the user’s original passcode. Or is it?
The Locked iPhone
The use of Faraday bags is still sporadic, and the risk of losing evidence through a remote wipe command is well-known. Even today, many smartphones are delivered to the lab in a powered-off state. Investigating an iPhone after it has been powered off is the most difficult and, unfortunately, the most common situation for a forensic professional. Once the iOS device is powered on after being shut down, or if it simply reboots, the data partition remains encrypted until the moment the user unlocks the device with their passcode. Since encryption keys are based on the passcode, most information remains encrypted until first unlock. Most of it, but not all.
We’ve figured out exactly which types of data remain accessible in iPhone devices after a reboot or immediately after the iPhone is powered on. Assuming that the phone is locked and the passcode is not known, what exactly is and what is not available depends on several factors.
- Whether the iPhone was unlocked (with a passcode) at least once after cold boot
- Whether you have a lockdown record
A lockdown record? We wrote about them before; if you need a refresher, please refer to these two articles:
In a word, a lockdown (pairing) record is a file stored on the computer that was used to sync with the iPhone in question. If you are able to retrieve a lockdown record from the user’s computer, you may be able to access significantly more information from the device – even if it was never unlocked since powered on.
What is and what isn’t available? The following matrix applies to devices running iOS 8 through iOS 11:
|
Basic device info |
Advanced device info |
App list |
iTunes-style backup |
| Device locked, no lockdown record |
Yes |
No |
No |
No |
| Device never unlocked after reboot, lockdown exists |
Yes |
Yes |
No |
No |
| Device unlocked after reboot, lockdown exists |
Yes |
Yes |
Yes |
Yes |
Basic device info consists of the following data (accessible with or without a lockdown record):
- Device model and name
- iOS version and build number
- Device ID
- MAC addresses of the phone’s Wi-Fi and Bluetooth adapters
Advanced device information (lockdown record required) includes:
- ICCI/IMEI/IMSI and phone number
- Whether or not an iTunes backup password is enabled
- Date and time of last iTunes and iCloud backups
- List of synced accounts including email address for Google accounts
- Various bits such as total and available disk space, time zone and language settings
Extras include (lockdown record required; device must be unlocked at least once after a reboot):
- App list (package name, version, path to data folder, some additional information)
- iTunes-style backup
Note: the app list is also available via full iTunes-style local backups. However, a local backup may come out encrypted with an unknown password, in which case the data will be encrypted unless the password is known.
Accessing Information with a Lockdown Record
In order to access basic and advanced information about the device, you would need to have all of the following:
- A valid lockdown record extracted from the user’s computer
- An iPhone or iPad device running iOS 8 through 11
- Elcomsoft iOS Forensic Toolkit 2.40 or newer
In order to extract device info:
- Connect the iPhone or iPad device to your computer.
- Launch iOS Forensic Toolkit 2.40 (or newer).
- Use the “I(nfo)” command
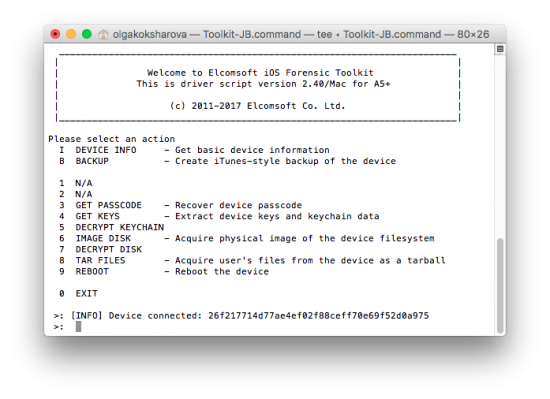
- Provide path to the pairing (lockdown) file when prompted.
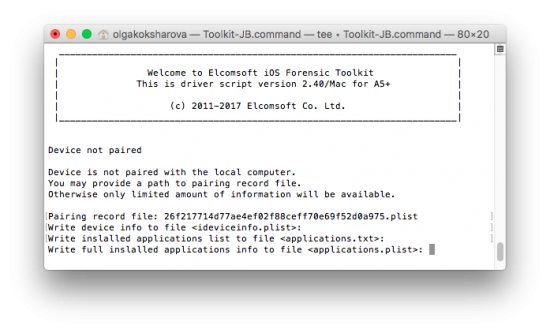
- Information about the iOS device will be extracted and saved into a file ideviceinfo.plist (XML).
If the iPhone was unlocked at least once after a reboot, iOS Forensic Toolkit will automatically extract additional information about the apps. A pair of files will be created (applications.txt and applications.xml/.plist). The first file contains a brief list of all applications installed on the device (including their version numbers); the second file includes additional details on every application.
- Mac OS X users: the plist file will be saved in your Home folder (Finder | Go | Home).
- Windows users: the xml file will be saved in the current folder.
Conclusion
Even if what you have is a locked down, powered off iPhone, you still have options. Basic device information is available via iOS Forensic Toolkit no matter what. If you have a valid lockdown record extracted from the user’s computer, you’ll be able to access significantly more information about the device – even when dealing with cold boot situations. Finally, if you are given an iPhone that was unlocked at least once after booting, you will be able to extract the app list and capture a full system backup.





