iOS is a locked down mobile operating system that does not allow its apps to directly access files in the file system. Unlike every other major mobile OS, iOS does not have a “shared” area in the file system to allow apps keep and share files with other apps. Yet, individual iOS apps are allowed to let the user access their files by using the file sharing mechanism.
While uploading or downloading shared files from an Android or Windows 10 smartphone occurs over a standard MTP connection established over a standard USB cable, you’ll need several hundred megabytes worth of proprietary Apple software (and a proprietary Lightning cable) to transfer files between iOS apps and the computer. But do you really?
While there’s nothing we can do about a Lightning cable, we can at least get rid of iTunes middleware for extracting files exposed by iOS apps. We’ll show you how this works with iOS Forensic Toolkit 3.0.
iOS File Sharing
If you are not familiar with iOS and its file sharing mechanism, please refer to this article first:
The file sharing mechanism was developed by Apple to allow users transfer files between their computer and apps in their iOS devices. As an example, users can upload a bunch of e-books or PDF documents into Adobe Reader, or transfer documents into the Microsoft Office app. Another popular use for file sharing is by media players allowing to upload videos in formats that are not natively supported by iOS to avoid iTunes transcoding them. Many video players allow uploading subtitles and custom fonts, a feature that is also available from certain third-party book readers.
The file sharing mechanism is sometimes enabled by app developers by an accident. For example, we could not think of a legitimate reason for the MiniKeePass password manager to expose its password database via the file sharing mechanism – yet it does.
When analysing an iOS device, you won’t be able to tell which apps have shared files, and which don’t. Settings | General | iPhone storage lists a bunch of apps with data, but it does not make a difference between shared files and sandboxed app data. You’ll need a computer to access those files.
Normally, accessing shared files would require using Apple iTunes. This is how it looks:
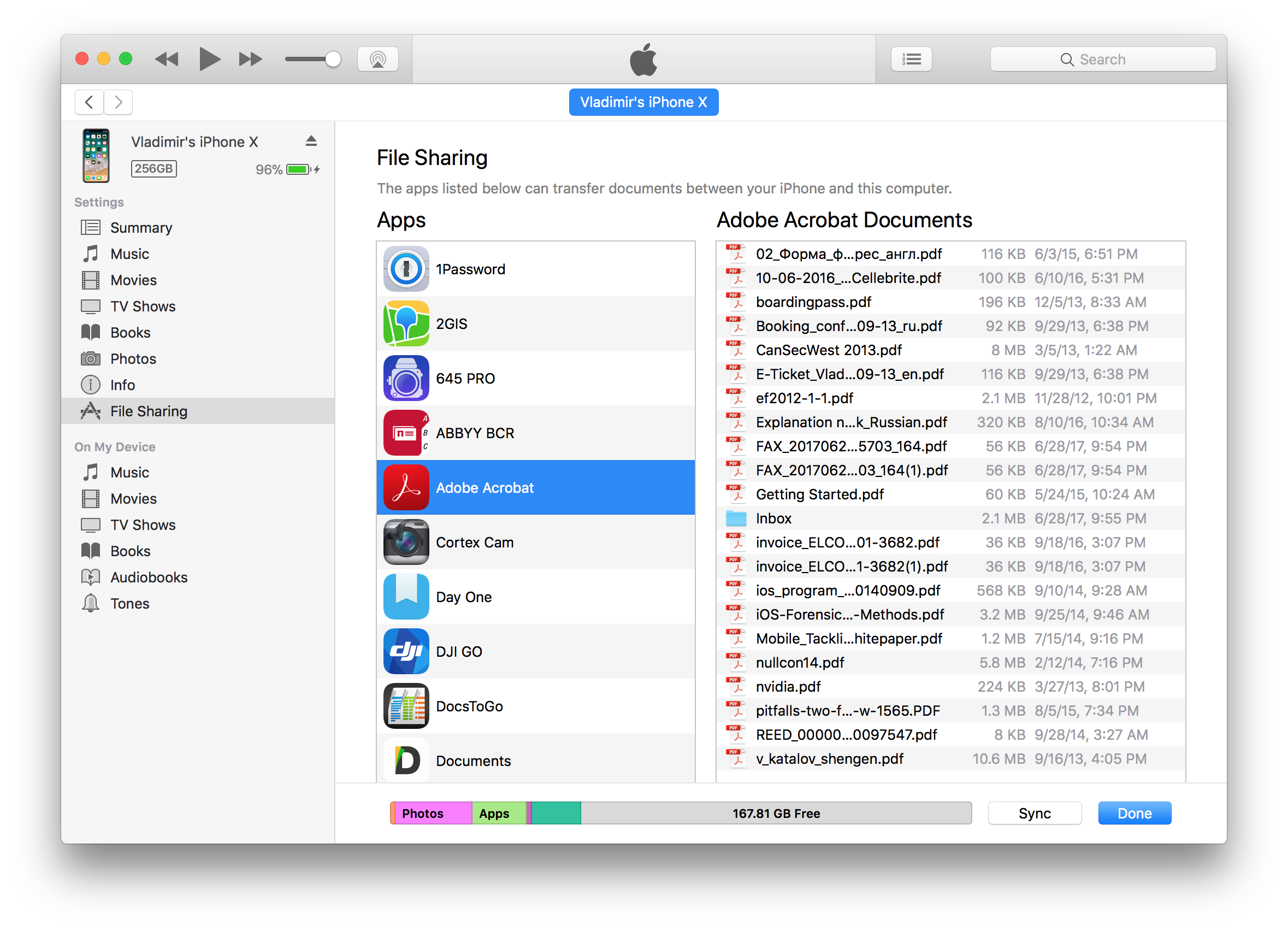
That said, using iTunes during an investigation is the worst idea ever. iTunes is not forensically sound, and it’s never been. iTunes is a huge tool that attempts to automatically synchronize the user’s iPhone with their computer – something that an expert would want to avoid. Besides, the backup may be password-protected, which further complicates the extraction.
For this reason, we built shared files extraction into our iOS acquisition tool, iOS Forensic Toolkit 3.0.
iOS 8.2 and Earlier: Extracts Sandboxed App Data
Interestingly, the extraction mechanism described below can access sandboxed app data (and not just shared files) if the device is running iOS 8.3 or earlier, being a good alternative to logical acquisition (especially considering that a backup might be protected with a password). Newer versions of iOS have disabled access to anything but shared files.
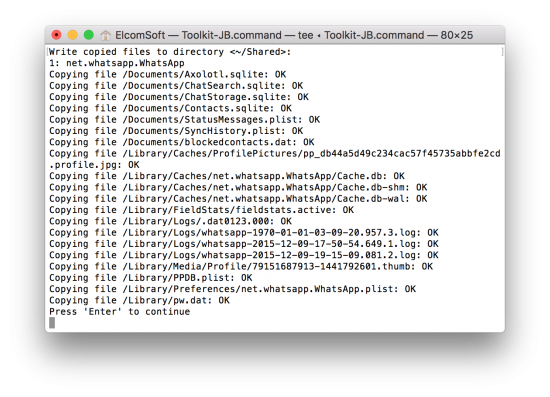
Extracting Shared Files with iOS Forensic Toolkit
If the iPhone you are about to extract is already unlocked and (in the case it runs iOS 11) you know its passcode, do the following steps.
- Launch iOS Forensic Toolkit by invoking the “Toolkit-JB” command.
- Connect the iPhone to the computer using the Lightning cable. If you are able to unlock the iPhone, pair the device by confirming the “Trust this computer?” prompt and (in the case of iOS 11) entering device passcode. If you cannot perform the pairing, you will need to provide path to a lockdown file later on.
- From the main window, enter the “S” (Shared) command.
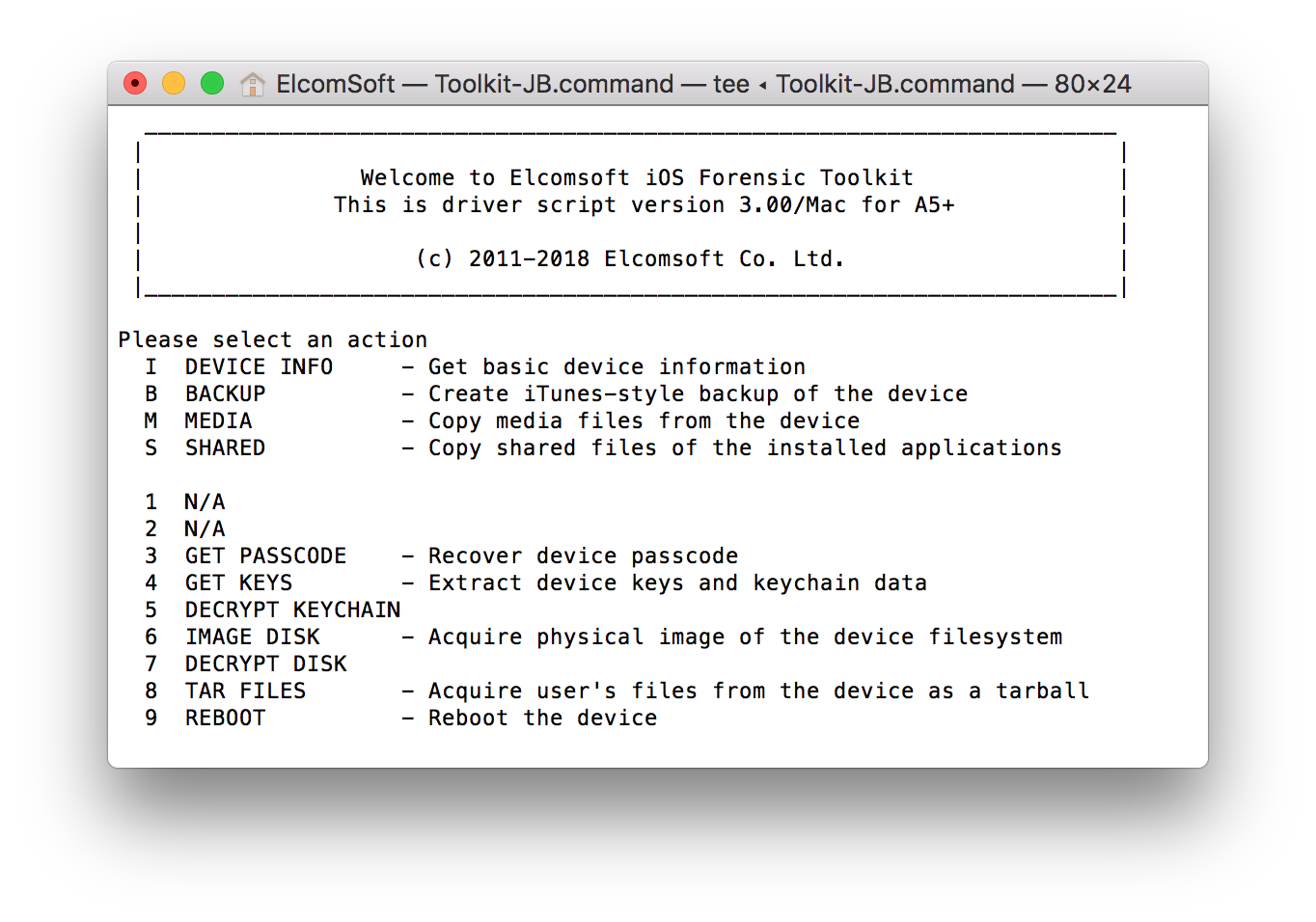
- If you were able to establish trust between the iPhone and the computer on Step 2, you will be prompted for path to save the shared files to. If not, you will be prompted to provide path to a lockdown file. Tip: the easiest way to do it is by dragging and dropping the lockdown file onto the iOS Forensic Toolkit window when prompted.
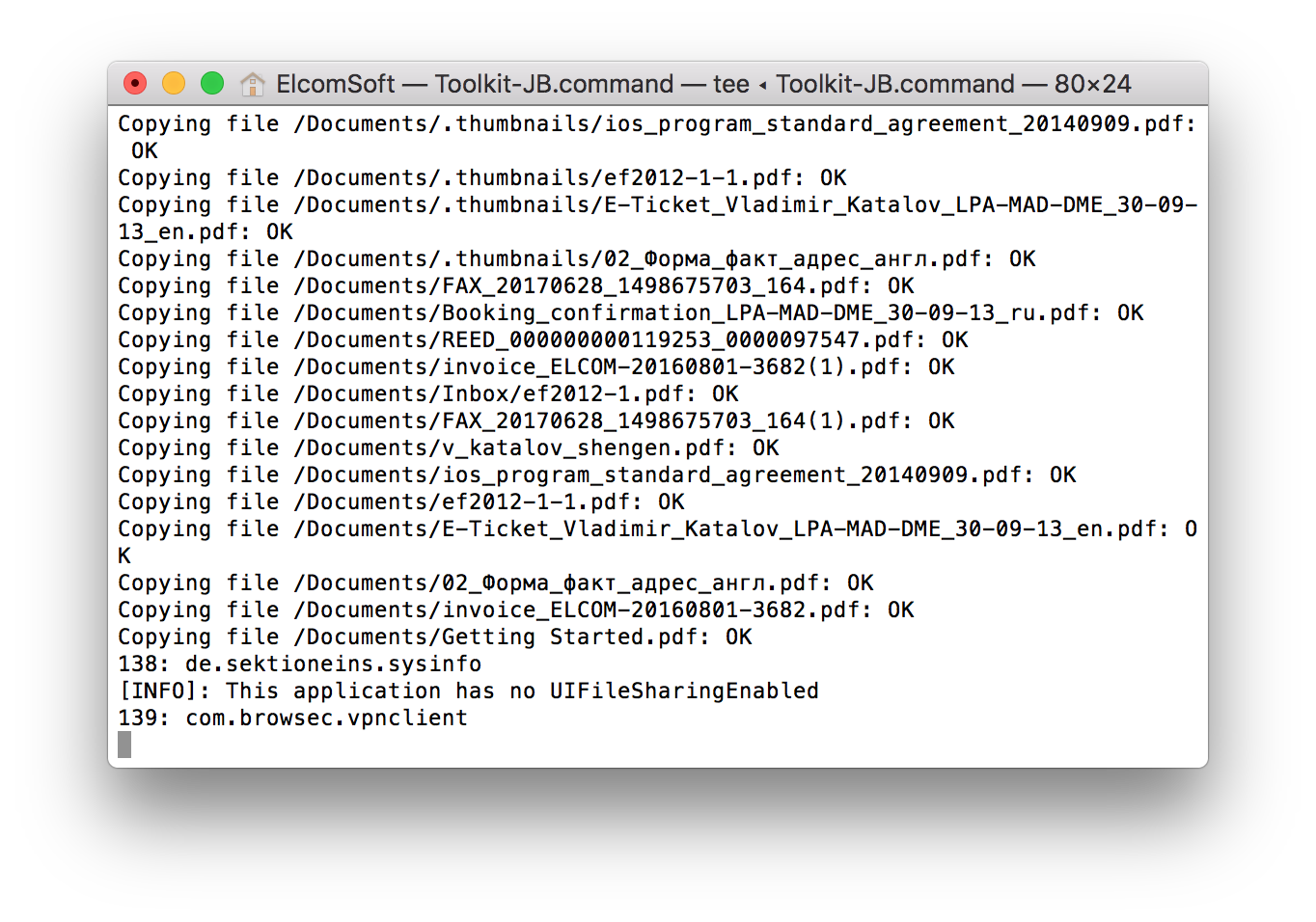
- iOS Forensic Toolkit will begin extracting the shared files.
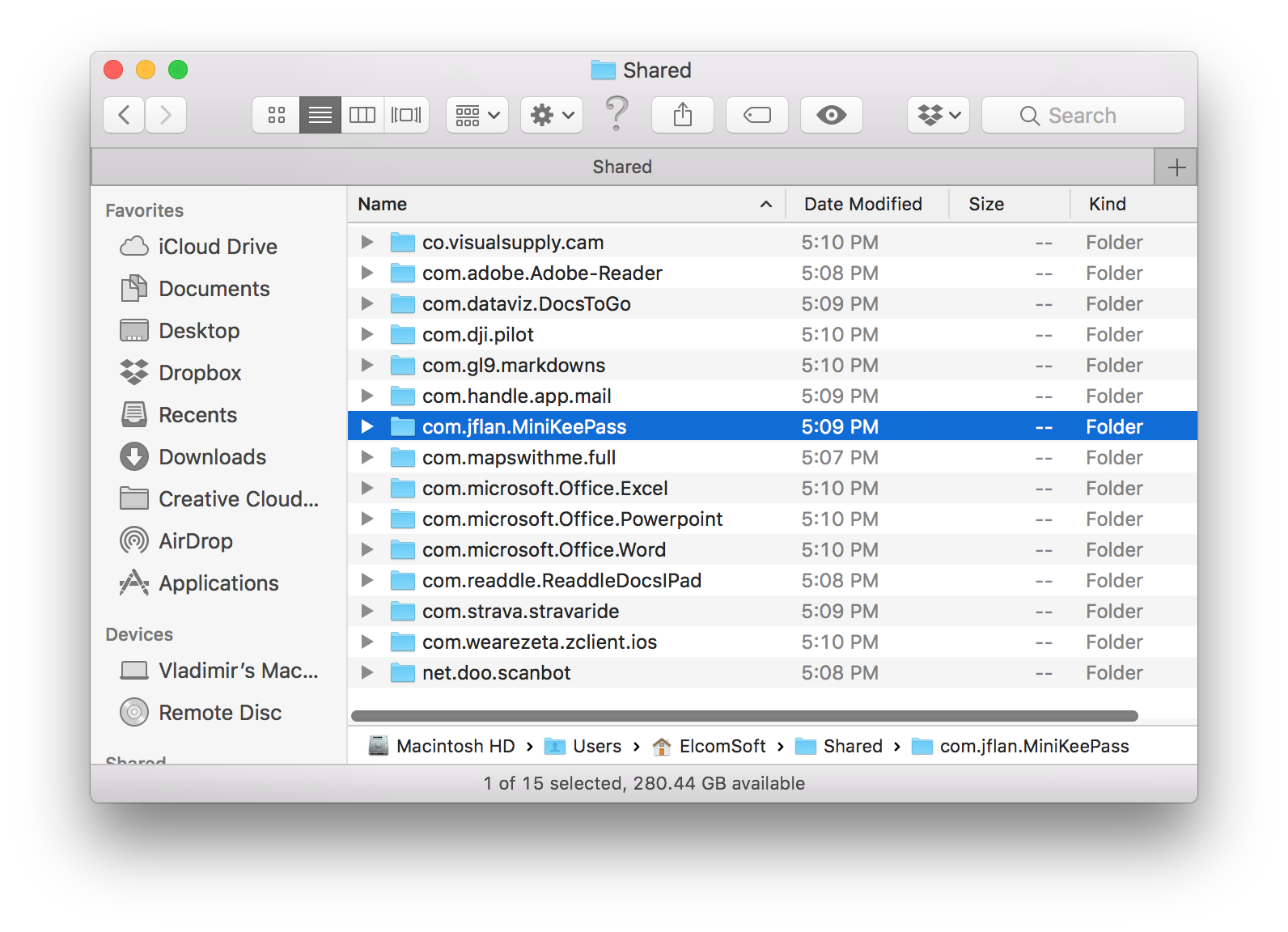
- Once the copying is complete, you’ll be able to review the files. By default, the “Shared” folder will be created in the user’s home folder.
Conclusion
The new extraction method in iOS Forensic Toolkit 3.0 offers a quick and convenient way to extract shared files from both unlocked and locked iPhone and iPad devices without resorting to local backups and without using the iTunes app.









