In the world of mobile forensics, physical acquisition is still the way to go. Providing significantly more information compared to logical extraction, physical acquisition can return sandboxed app data (even for apps that disabled backups), downloaded mail, Web browser cache, chat histories, comprehensive location history, system logs and much more.
In order to extract all of that from an i-device, you’ll need the extraction tool (iOS Forensic Toolkit) and a working jailbreak. With Apple constantly tightening security of its mobile ecosystem, jailbreaking becomes increasingly more difficult. Without a bug hunter at Google’s Project Zero, who released the “tfp0” proof-of-concept iOS exploit, making a working iOS 11 jailbreak would take the community much longer, or would not be possible.
The vulnerability exploited in tfp0 was present in all versions of iOS 10 on all 32-bit and 64-bit devices. It was also present in early versions of iOS 11. The last vulnerable version was iOS 11.2.1. Based on the tfp0 exploit, various teams have released their own versions of jailbreaks.
Select Your Jailbreak
Several different jailbreaks are available for different combinations of hardware and versions of iOS. LiberIOS and Electra jailbreaks overlap, doing the same job for iOS 11 devices. It is up to you which jailbreak to choose; they both exploit the same vulnerabilities, and should work about the same with iOS Forensic Toolkit. We have successfully tested the following jailbreaks:
iOS 10:
iOS 11:
There is also g0blin jailbreak for iOS 10.3.x, limited to A7-A9 devices (so iPhone 5S, iPhone 6/Plus, iPhone 6S/Plus, iPhone SE, 6th-gen iPod and some iPads), but we have not tested our software with it (though it should work).
How to Extract Data from a Jailbroken iOS 11 Device
In order to extract data from an Apple device running iOS 10 or 11, you will need iOS Forensic Toolkit 3.0 (or newer), follow one of the two guides depending on whether or not you can pair the device to your computer.
Note: you will need to install a jailbreak prior to extraction. If you have not yet installed a jailbreak, please refer to Jailbreaking iOS 11.
If the iPhone you are about to extract is already unlocked and (in the case it runs iOS 11) you know its passcode, do the following steps.
- Launch iOS Forensic Toolkit by invoking the “Toolkit-JB” command.
- Connect the iPhone to the computer using the Lightning cable. If you are able to unlock the iPhone, pair the device by confirming the “Trust this computer?” prompt and (in the case of iOS 11) entering device passcode. If you cannot perform the pairing, skip to the second guide (“Locked iPhone”).
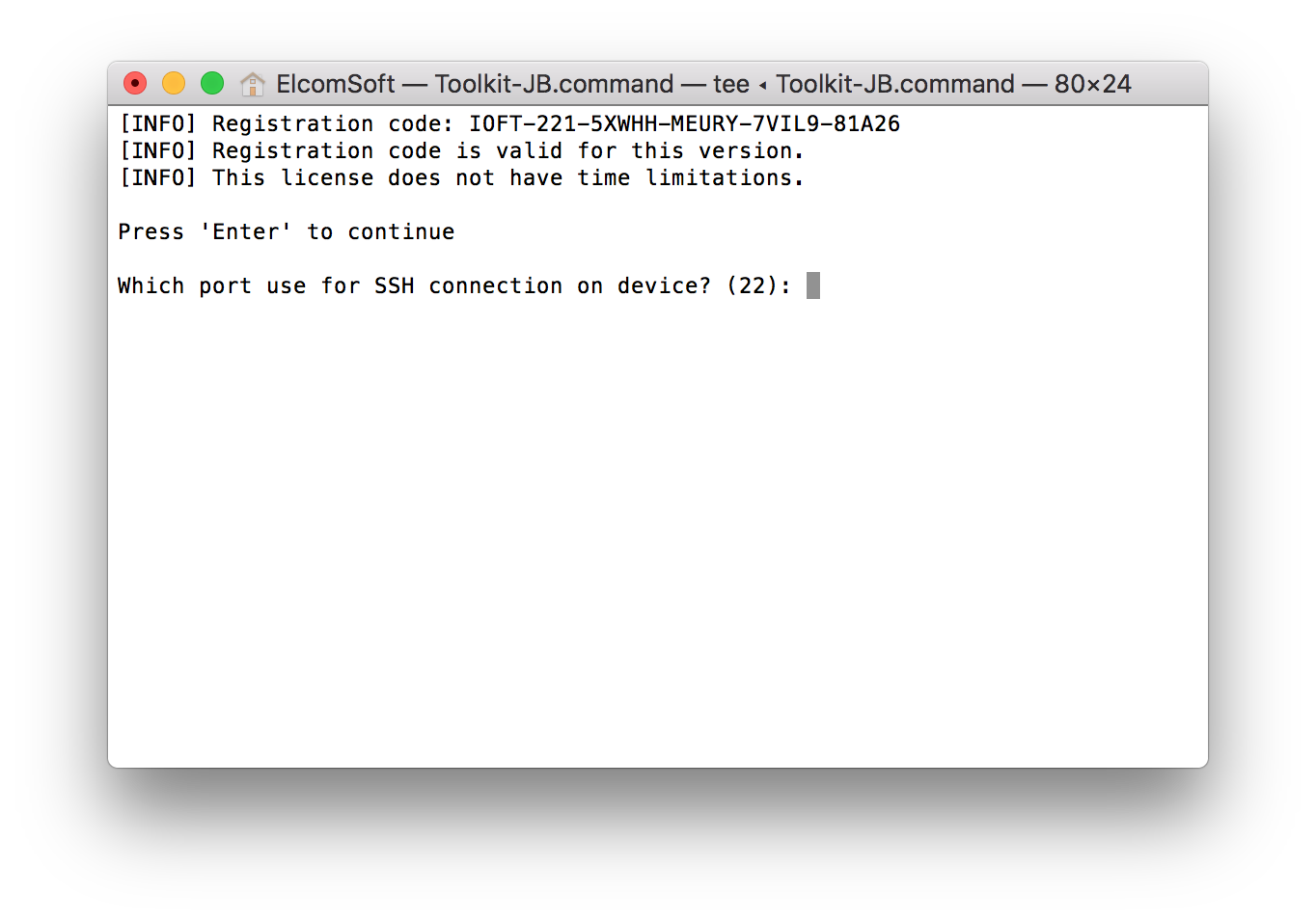
- You will be prompted to specify the SSH port number. By default, the port number 22 can be specified by simply pressing Enter. However, some jailbreaks require a different port number. For example, the Meridian jailbreak uses port number 2222.
- From the main window, enter the “8” (TAR FILES) command.
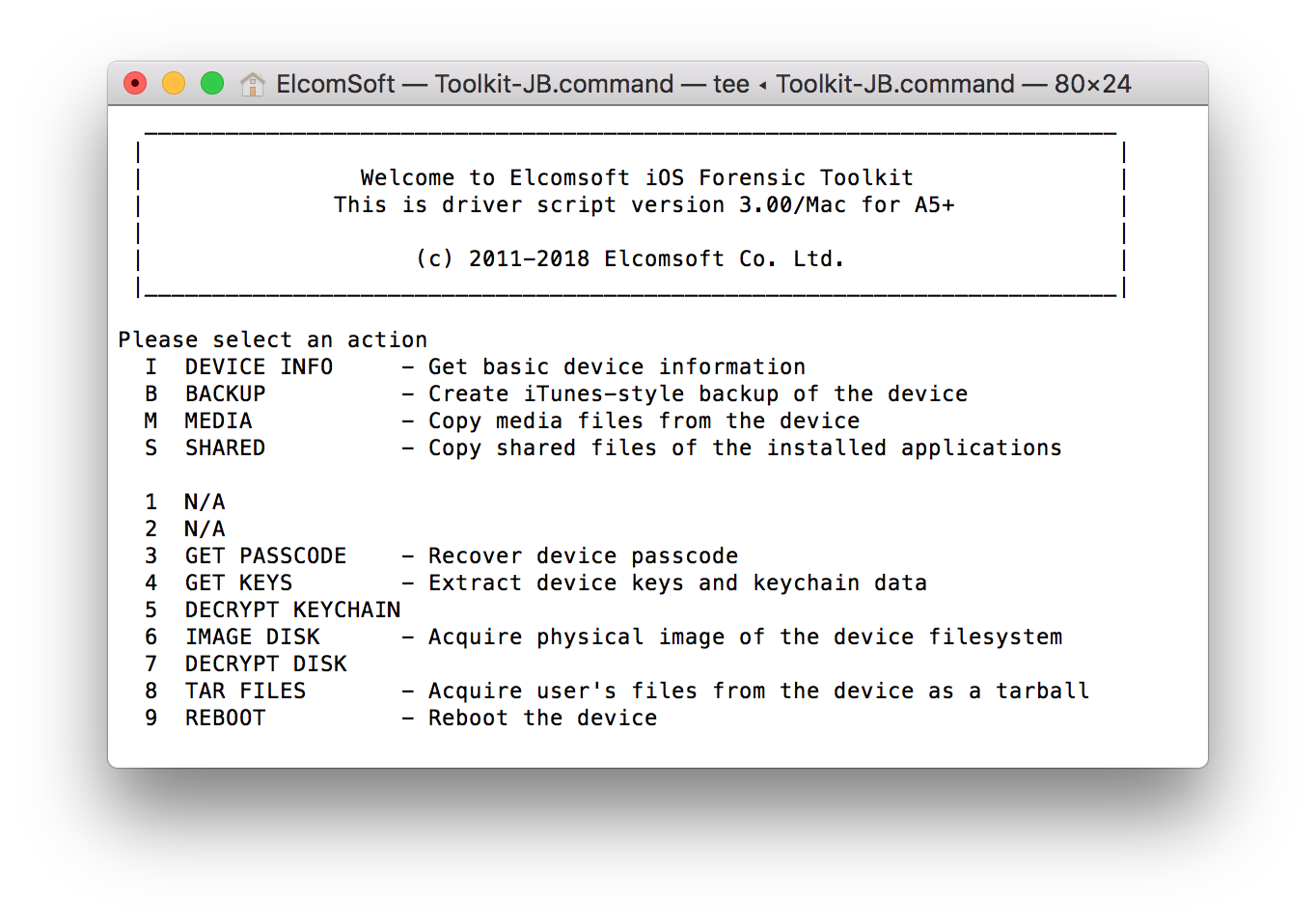
- If you were able to establish trust between the iPhone and the computer on Step 2, you will be prompted to enter the root password. By default, the root password is ‘alpine’. You may need to enter the password several times.

- Specify file name. The path is relative to the home directory.
- Wait while the file system is being extracted. This can be a lengthy process, but usually takes up to 10-15 minutes:
When the process is finished, disconnect the device and proceed to analyzing the data.
Jailbreaking iOS 11 and iOS 10
In order to jailbreak an Apple device running iOS 11 (or iOS 10), follow these instructions.
Steps to jailbreak:
- Back up data with iOS Forensic Toolkit (if backup password is empty, specify and record a temporary password)
- Obtain and install the jailbreak tool using the links above. This includes two files:
- The jailbreak IPA file
- Cydia Impactor available at http://www.cydiaimpactor.com/
- Cydia Impactor (developed by Saurik) is used to sign the IPA file so that the jailbreak tool can be executed on iOS devices. You will need to use valid Apple ID credentials for signing the IPA. We recommend using a newly created Apple ID for signing the certificate.
- Connect the iOS device to the computer, trust the computer on the iOS device and launch Cydia Impactor.
- Drag the jailbreak IPA onto Cydia Impactor app.
- Provide Apple ID and password when prompted. Click OK to allow Cydia Impactor to sign the IPA and upload it onto the iOS device.
- On the iOS device, open Settings > General > Device Management. You will see a developer profile under the “Apple ID” heading. Tap the profile to establish trust for this developer. (An Internet connection is required to verify the app developer’s certificate when establishing trust.)
- On the iOS device, find the jailbreak app and run it.
- In a few moments, the jailbreak will complete. The device may or may not reboot; this is normal. You may see a message about successfully jailbreaking the device. You may also see an error message, in which case we recommend repeating the procedure after rebooting the device.
- The jailbreaks already include a supported SSH daemon that can be used by iOS Forensic Toolkit. If no SSH connection can be established, install OpenSSH from the Cydia app on the device, or as described here.
Note: the jailbreaks are semi-tethered. They will expire after 7 days, after which the procedure must be repeated.






