We have just released an update to iOS Forensic Toolkit. This is not just a small update. EIFT 4.0 is a milestone, marking the departure from supporting a large number of obsolete devices to focusing on current iOS devices (the iPhone 5s and newer) with and without a jailbreak. Featuring straightforward acquisition workflow, iOS Forensic Toolkit can extract more information from supported devices than ever before.
Feature wise, we are adding iOS keychain extraction via a newly discovered Secure Enclave bypass. With this new release, you’ll be able to extract and decrypt all keychain records (even those secured with the highest protection class, ThisDeviceOnly) from 64-bit iOS devices. The small print? You’ll need a compatible jailbreak. No jailbreak? We have you covered with logical acquisition and another brand new feature: the ability to extract crash logs.
Secure Enclave Bypass Helps Decrypt the Keychain
The iOS keychain is an Apple’s solution to securely keep passwords, encryption keys, authentication tokens, certificates, payment data and app-specific credentials. Many keychain items can be recovered by analyzing a password-protected local backup. However, records protected with ThisDeviceOnly attribute can be only decrypted on the device itself.
These (and all other) records are securely encrypted. In iPhone 5s and all newer models, access to the encryption key is additionally protected with Secure Enclave. Until today, no third-party forensic solution existed to extract and decrypt keychain items from 64-bit iOS devices equipped with Secure Enclave. Jailbreak or not, bypassing Secure Enclave protection was considered impossible.
After years of research, we have found a way to access and decrypt protected keychain items, successfully bypassing Secure Enclave on jailbroken devices. We can now decrypt the entire content of the keychain including records marked ThisDeviceOnly.
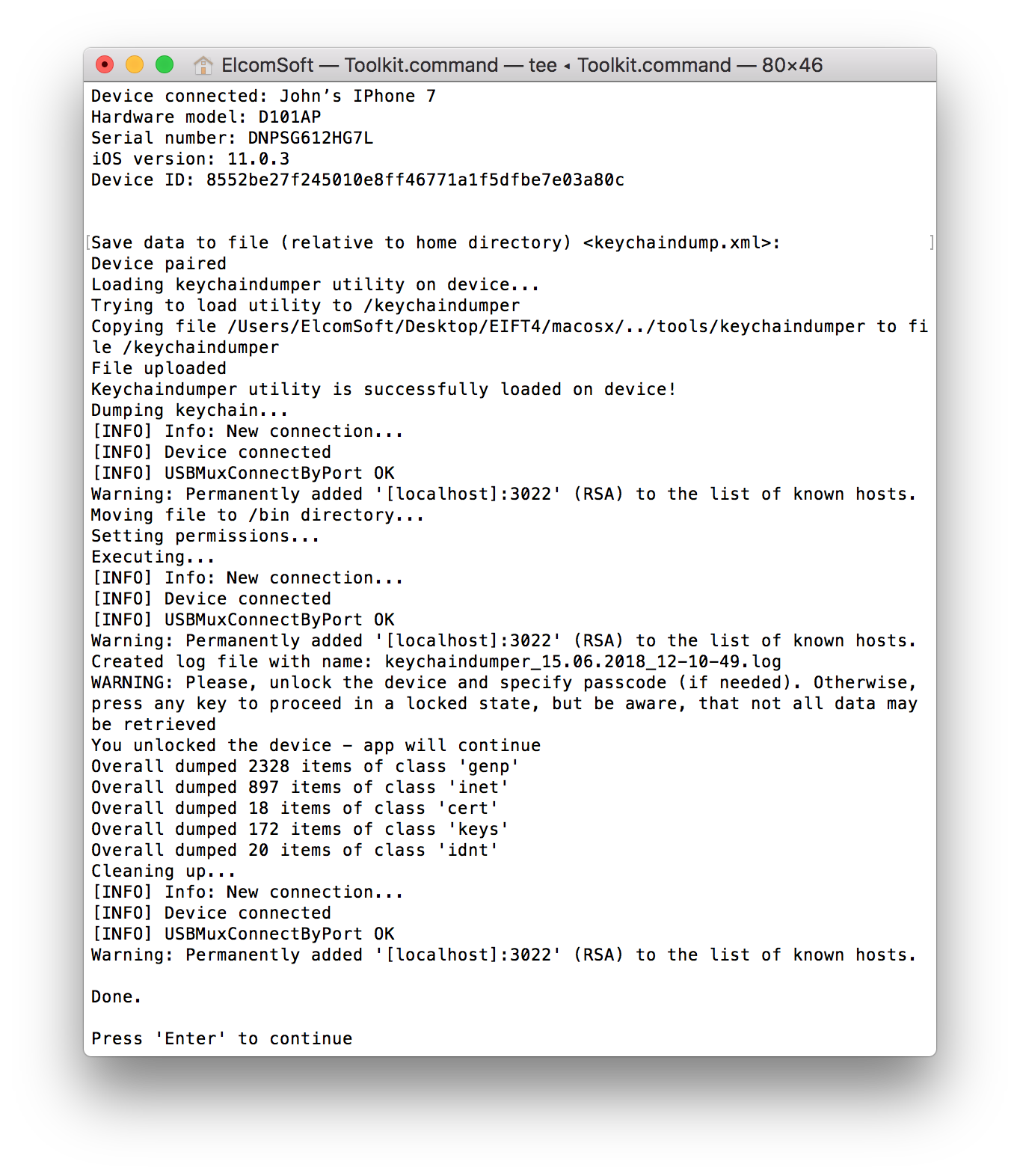
You can view the keychain by using Elcomsoft Phone Breaker.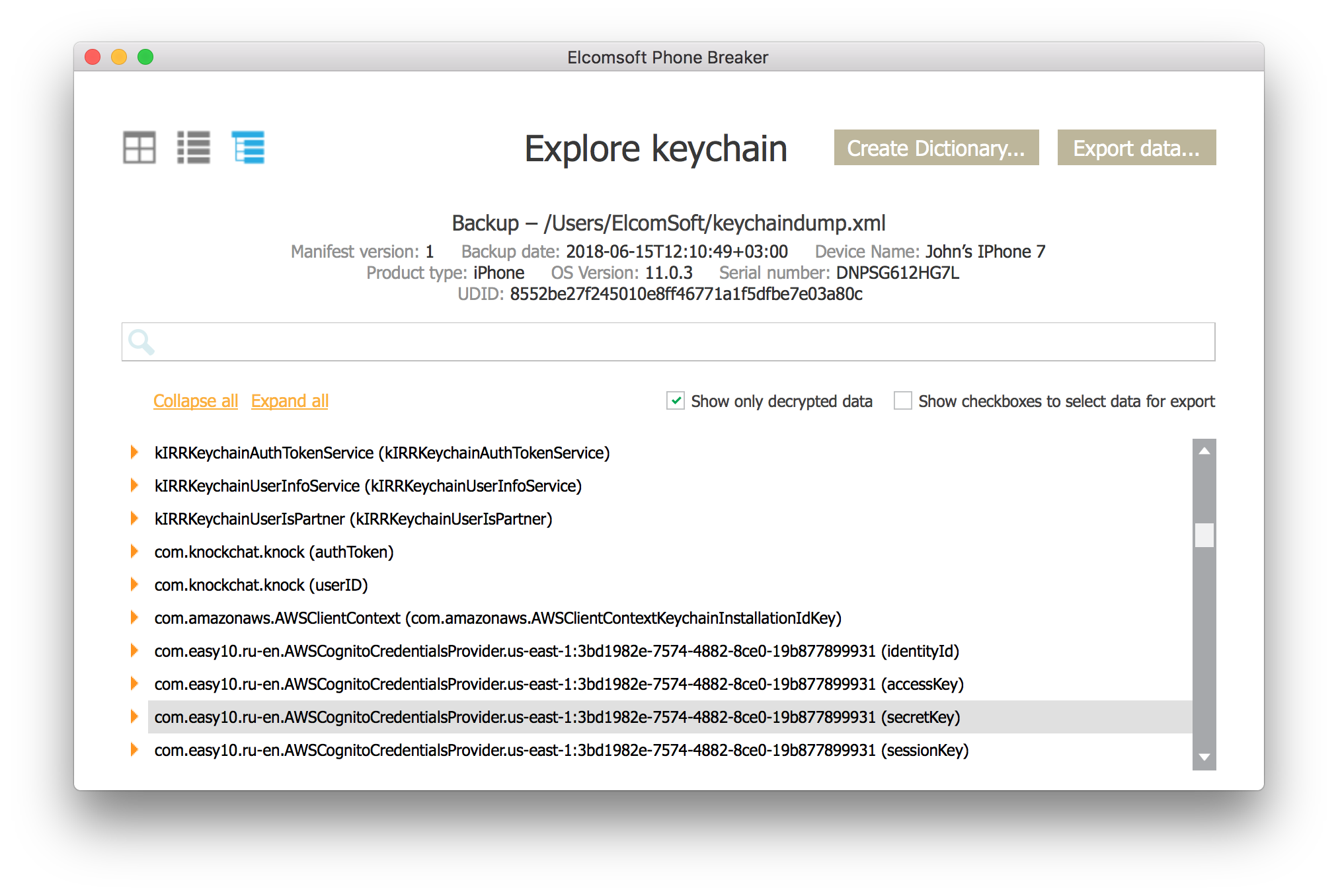
Until recently, we always recommended our customers to remove the passcode from device settings before acquisition; otherwise a lot of data would remain inaccessible. Some time ago we discovered that our acquisition process allows accessing encrypted information without removing the passcode by simply keeping the device unlocked during the entire acquisition process. While it might be possible to manually disable automatic screen lock by switching the Auto-Lock setting to Never, managed devices often lack this feature, automatically locking after a certain number of minutes.
We were able to bypass such restrictions even on managed devices via jailbreak. In order to decrypt some keychain records, the device must remain unlocked with display on during the entire acquisition process. We built a feature that disables automatic screen lock to make sure that even records with the strongest security attributes are successfully extracted and decrypted. This allows you performing physical acquisition without removing the passcode, which returns more information compared to devices with passcodes removed from the Settings.
Crash Logs… What Crash Logs?
Crash logs are little known, but can be an important part of the evidence that is not included to local backups. If you are an expert, you can check out the list of installed and uninstalled apps to figure if any apps that are not on the device have been used in the past. If you see an entry in the crash log that belongs to an app no longer installed, you can assume it was used some time in the past – at least up to the date and time specified in the crash log entry.
iOS Forensic Toolkit 4.0 can extract crash logs from iOS devices with or without a jailbreak. You’ll need a paired device or a valid lockdown file. 
Focus on Current Hardware
Remember the days of iPhone 3G? Released back in 2008, this iPhone is all but unusable by today’s standards. Yet, we kept supporting this and other devices long after they became obsolete. Bootrom exploits, partition dumps and file system dumps were just a few methods we had to include and show in the menus, making the extraction process complicated even to seasoned forensic experts.
In this release, we shift our focus to Apple’s current hardware (iPhone 5s and newer devices), leaving legacy iPhones behind in order to streamline acquisition workflow. While the UI is still console-based, the commands are now laid out in sequential order, enabling straightforward acquisition and streamlined workflow. You just have to try it! Here is how the new user interface looks:
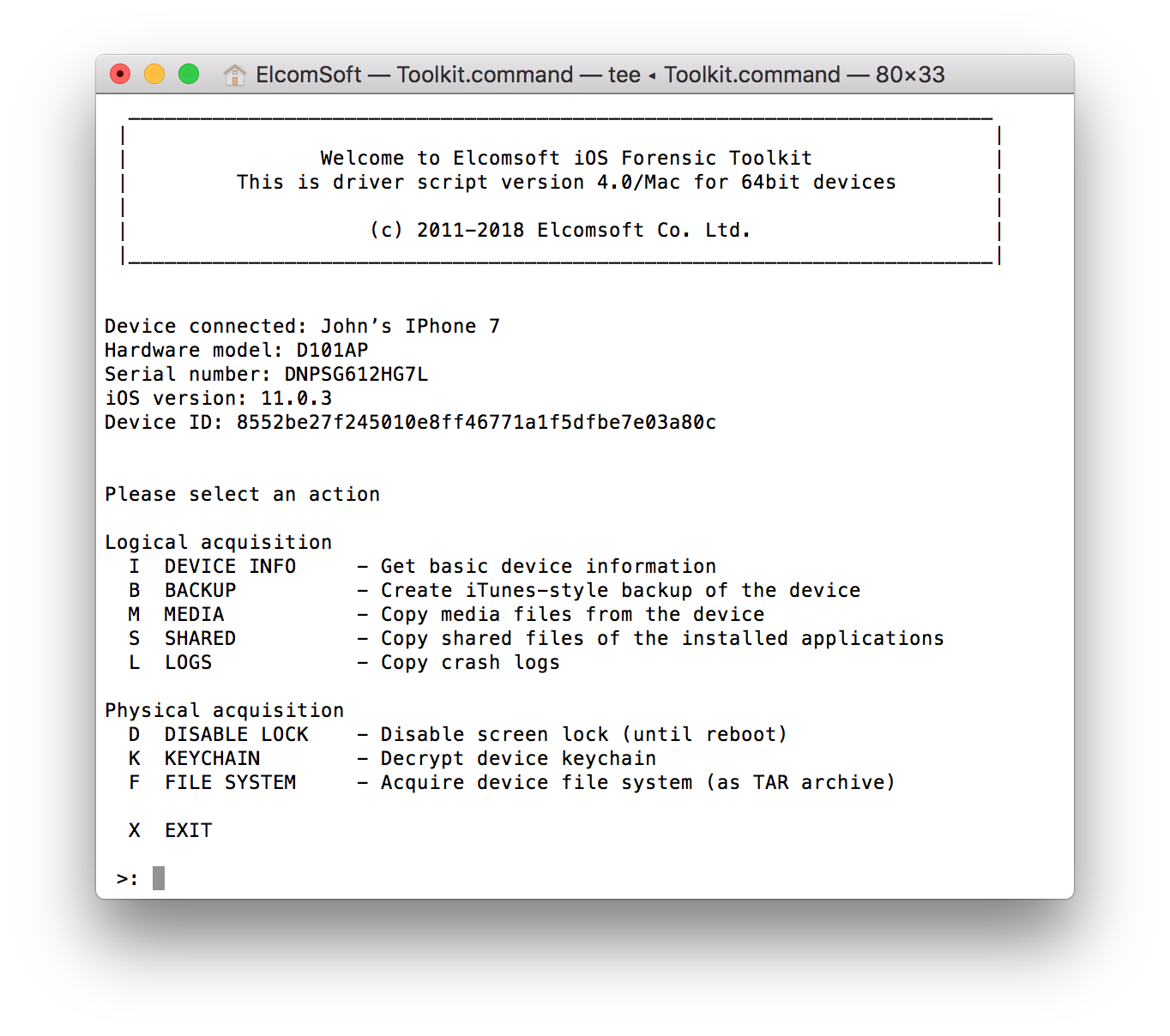
We’ve grouped logical acquisition and physical acquisition commands to make it clear what you can expect of devices with and without a jailbreak.
Still have a bunch of older devices to process? We’ve got you covered! Once you are on the latest release, just drop us an email to request a copy of the legacy Toolkit.










