In today’s usage scenarios, messaging are not entirely about the text. Users exchange pictures and short videos, voice recordings and their current locations. These types of data are an important part of conversation histories; they can be just as valuable evidence as the text content of the chat.
Apple ecosystem offers a built-in messenger, allowing users to exchange iMessages between Apple devices. This built-in messenger is extremely popular among Apple users. Back in 2016, Apple’s Senior VP announced that more than 200,000 iMessages are sent every second.
All current versions of iOS are offering seamless iCloud synchronization for many categories of data. Starting with iOS 11.4, Apple devices can synchronize messages via iCloud. iMessages and text messages can be now stored in the user’s iCloud account and synchronized across all of the user’s devices sharing the same Apple ID. This synchronization works in a similar manner to call logs, iCloud Photo Library or iCloud contacts sync (albeit with somewhat longer delays). However, Apple will not provide neither the messages themselves nor their attachments when fulfilling LE requests or GDPR pullouts. Why is this happening, how to extract messages from iCloud accounts and what kind of evidence we can find in attachments? Read along to find out.
Messages in the Cloud: Security and Encryption
Due to point-to-point encryption, iMessages are securely protected while in transit. What about the cloud? Apple states that the data stored in the user’s iCloud account is securely encrypted. Apple also stores the encryption keys, which makes it possible for the company to fulfil law enforcement requests and GDPR data pullouts by handing over the information. This, however, does not apply to iCloud Messages and any attached content. Apple uses additional AES256 encryption to protect synced messages. The encryption key is re-encrypted with the user’s device passcode (iOS devices) or system password (macOS devices); if several devices with different passcodes/passwords are enrolled, the encryption key can be decrypted with either one. In addition, messages will only sync for accounts with Two-Factor Authentication.
Evidence in iMessage Attachments
iMessage is the de-facto instant messenger of choice for many iPhone users. Business Insider states that “Apple iMessage use outstrips Facebook Messenger and Snapchat among US youths”. “US Teens engage with iMessage more than any other social platform”, claims Guiseppe Stutto from Hacker Noon. “iMessage IS a social platform for teens. It’s currently the center of their immediate, social universe”, he continues. “They still spend hours on apps such as Instagram, Snapchat, Tumblr, or whatever else, but they constantly come back to their iMessage chats, whether it be 1v1 or group chats”.
As avid iPhone users, we make our own contributions to anecdotal evidence. Parsing our CEO’s iCloud account returned as many as 170,000 messages with more than 7 gigabytes worth of attachments. This is the kind of evidence to die for. While iMessages per se don’t include location information (except when users share their location), attachments are usually photos snapped with the iPhone’s camera just moments before the iMessage is sent. This contributes greatly to location history thanks to EXIF tags accompanying each picture.
Message Sync and Cloud Backups
Back in 2011, iCloud backups were among the first services introduced with Apple’s new cloud platform. Since then, many things have changed. Cloud backups are created daily at best, and for many users they may not be created at all due to Apple’s restrictive free tier of only 5 GB of iCloud space. The growth of Apple ecosystem means high probability of the user owning more than one Apple device. As a result, Apple continues moving things out of iCloud backups and into the shared bucked of synchronizable data.
Once, for example, the user enables iCloud Photo Library, all of their photos are automatically uploaded to iCloud and synchronized across all of the user’s devices registered on the same Apple ID. According to Apple, “When you turn on iCloud Photos, your photos and videos automatically upload to iCloud. They’re not duplicated in your iCloud backup, so you should keep backup copies of your library.”
It is similar for messages. According to https://support.apple.com/en-us/HT208532 and https://support.apple.com/en-ca/HT207428, once the user enables Messages in iCloud, neither messages nor attachments are stored in their iCloud backups: “When you use Messages in iCloud […], your content is automatically stored in iCloud. That means they’re not included in your iCloud Backup.”
Not Available When Serving LE and GDPR Requests
Messages are not included with information obtained via LE or GDPR requests. The additional encryption is the reason; according to Apple, the company does not have access to the user’s messages because of this encryption. Apple states: “your messages are encrypted on your device and can’t be accessed by anyone without your device passcode”. As already mentioned, once the user enables Messages in iCloud, neither the messages nor attachments will be stored in iCloud backups. As a result, messages can only be extracted from the cloud using third-party forensic software. The user’s Apple ID login, password, 2FA code, and device passcode (screen lock passcode) are required to extract and decrypt messages.
Downloading Messages and Attached Content from Apple iCloud
In order to extract messages and attachments from iCloud, you will need Elcomsoft Phone Breaker 8.40 or newer. If you are using a Windows PC, you must have iCloud for Windows installed. Mac users must have macOS 10.11 or newer. Use the following steps to access messages.
Pre-requisites:
- Elcomsoft Phone Breaker or newer
- iCloud for Windows or newer
- Apple ID and password
- Access to the second authentication factor (SIM card, iPhone or iPad device registered on the same Apple account). Note: thanks to GS authentication, you will only have to provide the one-time code once. The computer then becomes trusted, and 2FA codes will not be asked during subsequent acquisitions.
- Passcode (iPhone/iPad) or system password (Mac) of at least one device enrolled to iMessage sync
Steps to extract messages from iCloud:
- Launch Elcomsoft Phone Breaker and select Apple > Download from iCloud > Synced Data
- Specify the user’s Apple ID and password.
- Provide one-time code to pass Two-Factor Authentication.
- Select data to obtain from iCloud. Make sure the “Messages” box is selected.
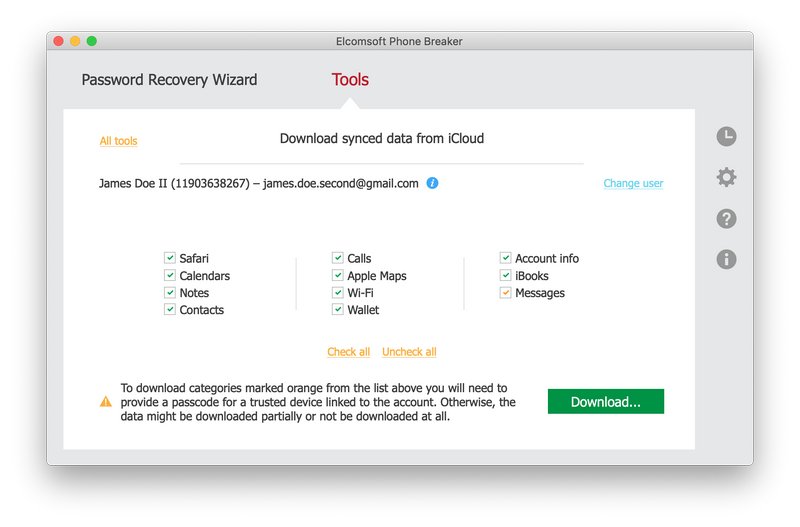
- Elcomsoft Phone Breaker will sign in to the user’s Apple account. Select a trusted devices to which you know the passcode or system password, and type in the passcode/password.

- Messages will download. After the messages are downloaded, click Finish. Alternatively, you may clock “Open in EPV” to automatically open downloaded data in Elcomsoft Phone Viewer. Yet another alternative is using the “Explore files” link to verify files that have been downloaded.
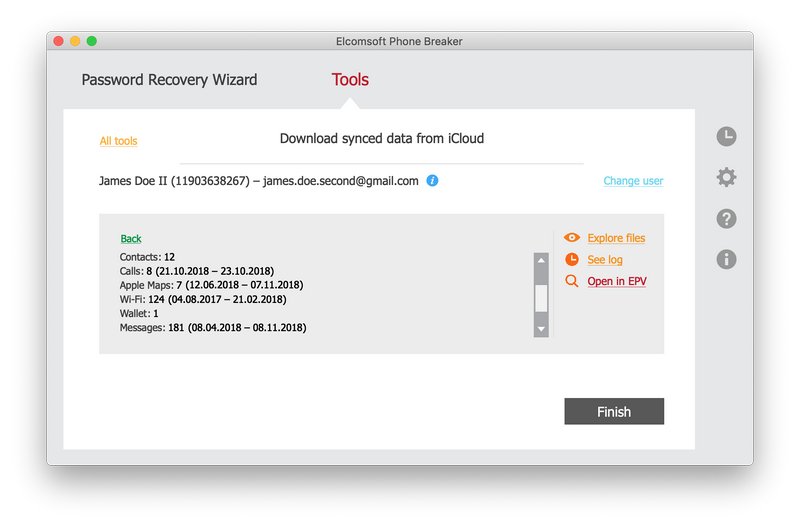
- You can now use Elcomsoft Phone Viewer to analyze downloaded messages.
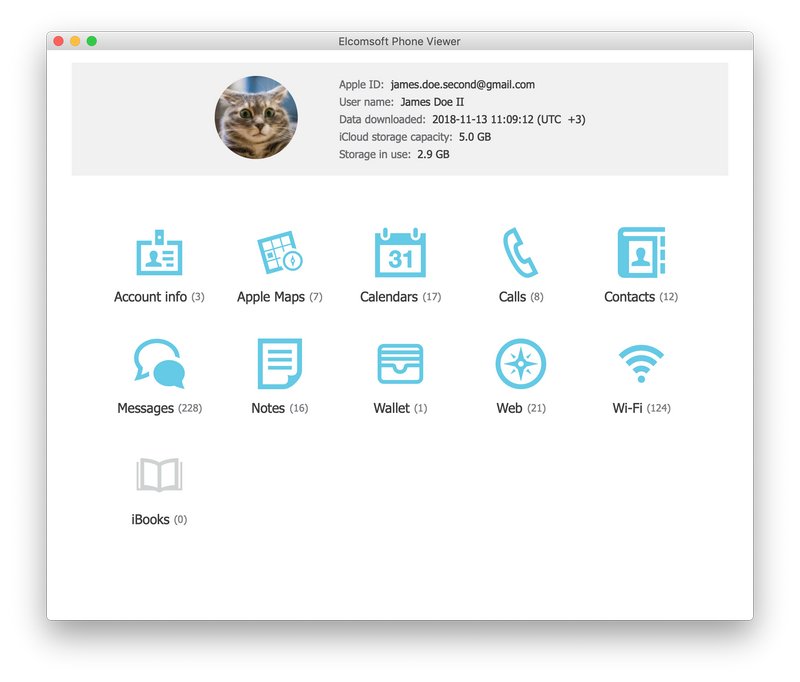 Click “Messages” to open the list of messages and attachments.
Click “Messages” to open the list of messages and attachments. This gallery displays thumbnail previews of extracted media file. Click Enlarge next to the preview to access the original or click Save to save as a file. You can apply a number of filters to show messages sent or received within a certain time range, or to only show messages with certain types of attachments (e.g. only messages with attached photos).
This gallery displays thumbnail previews of extracted media file. Click Enlarge next to the preview to access the original or click Save to save as a file. You can apply a number of filters to show messages sent or received within a certain time range, or to only show messages with certain types of attachments (e.g. only messages with attached photos).







