iMessage is undoubtedly one of the most popular instant messaging platforms for an obvious reason: it’s built in to iOS and ships with every iPhone by default. iMessage does not require complex setup, so the number of iMessage users is closely matching the number of iPhone users. Apple sells about 200 million iPhones every year, and the total number of iPhones sold is more than a billion. Unless you absolutely must chat with someone outside of Apple’s ecosystem (like those poor Android folks), you won’t need Skype, WhatsApp or Telegram. It’s also comforting to know that iMessage works everywhere around the world while most other messengers are oppressed in one or more countries.
But what about iMessage security? Is it safe to use if you’re concerned about your privacy? Is there a reason why countries such as China, Iran or Russia block other messengers but keep iMessage going? Is it safe from hackers? What about Law Enforcement? And what about Apple itself? It must have access to your messages to target the ads, right? Is it OK to send those private snapshots or share your location via iMessage?
There is no simple answer, but we’ll do our best to shed some light on that.
What Apple Says
Let’s start with Apple’s Approach to Privacy:
We use end-to-end encryption to protect your iMessage and FaceTime conversations across all your devices. With watchOS and iOS, your messages are encrypted on your device so that they can’t be accessed without your passcode. We designed iMessage and FaceTime so that there’s no way for us to decrypt your data when it’s in transit between devices. You can choose to automatically delete your messages from your device after 30 days or a year or to keep them on your device forever.
At this point, not very clear. Let’s proceed with iCloud Security Overview:
iCloud secures your information by encrypting it when it’s in transit, storing it in iCloud in an encrypted format, and using secure tokens for authentication. For certain sensitive information, Apple uses end-to-end encryption. This means that only you can access your information, and only on devices where you’re signed into iCloud. No one else, not even Apple, can access end-to-end encrypted information.
End-to-end encryption provides the highest level of data security. Your data is protected with a key derived from information unique to your device, combined with your device passcode, which only you know. No one else can access or read this data.
Messages in iCloud also uses end-to-end encryption. If you have iCloud Backup turned on, your backup includes a copy of the key protecting your Messages. This ensures you can recover your Messages if you lose access to iCloud Keychain and your trusted devices. When you turn off iCloud Backup, a new key is generated on your device to protect future messages and isn’t stored by Apple.
If you’re somehow not convinced, have a look at iOS Security Guide:
When a user turns on iMessage on a device, the device generates two pairs of keys for use with the service: an RSA 1280-bit key for encryption and an ECDSA 256-bit key on the NIST P-256 curve for signing. The private keys for both key pairs are saved in the device’s Keychain and the public keys are sent to Apple identity service (IDS), where they are associated with the user’s phone number or email address, along with the device’s APNs address.
Messages in iCloud also uses CloudKit end-to-end encryption with a CloudKit Service Key protected by iCloud Keychain syncing. If the user has enabled iCloud Backup, the CloudKit Service Key used for the Messages in iCloud container is backed up to iCloud to allow the user to recover their messages even if they have lost access to iCloud Keychain and their trusted devices. This iCloud Service Key is rolled whenever the user turns off iCloud Backup.
iMessage Security and Privacy in General
Before we talk about the cloud, let us first check out messages that are not synced with iCloud.
To our knowledge, there are no known vulnerabilities in the iMessage protocol that would allow decrypting intercepted messages (and sniffing traffic between the iPhone and Apple servers is not easy at all). The only way to access messages would be obtaining them from the device itself by creating a local backup through iTunes. The thing is, you’ll have to have the device itself, and you must know its passcode (to establish pairing with the computer). If the backup is password protected, you’ll have one more problem (although not a serious one if the phone is running iOS 11 or 12 where you can simply reset that pesky password).
A couple of old yet good articles on iMessage security:
What about iCloud backups? While the messages are there if the backup exists, you’ll need the user’s Apple ID, password, and one-time code to pass two-factor authentication (or you can use an authentication token). While iCloud backups are encrypted, the encryption keys are stored along with the data (technically on a different server, but still accessible to anyone with proper credentials). If you managed to access an iCloud backup, decrypting messages isn’t all that difficult.
As you can see, iMessage security without iCloud sync is somewhat lacking.
However, if the user enables iCloud Messages, no messages will be ever included in the next (and all subsequent) iCloud backup. With extra AES 256 encryption, this is quite an improvement:
Message Sync
Back to iCloud backups. If you use cloud backups, they are created on a daily basis if your device is turned on, locked, and connected to a power source; please also note that it only works on Wi-Fi. Just go to Settings | [your name] | iCloud | iCloud Backup to turn the feature on or off; you can also back up manually there (connection to power source is not required for manual backup).
But what about data syncing? Many users won’t enable iCloud backup for various reasons. One of them is space: you only get 5 GB as a free tier, and that’s definitely not enough for backups. However, syncing is enabled by default, and it is very, very convenient.
Most data is synced in almost real time. That includes contacts, call logs, notes, Safari browsing history etc, but not messages. Yes, we tried hard, with various devices (from iPhone 5S to iPhone Xs Max, as well as the iPad and several different Macs). Our devices were running various versions of iOS ranging from iOS 11.4 (the first version of iOS that supports messages in iCloud) to iOS 12.1.1 (available as a beta at the time of this writing), connected via Wi-Fi and LTE. Only Apple knows when and how messages are synced with the cloud. Sometimes messages (both iMessage and SMS) are uploaded into iCloud (and so synced to other devices connected to the account) in 5 to 10 minutes, but the other day it takes several hours to sync. For one of our test accounts, the messages are still not in the cloud after 4 days.
Looks like the implementation is still buggy, despite the fact that it was released in almost a year after the first announce.
Message Attachments
“Attachment” is actually not a good term, but we are still going to use it for the lack of a better one. Speaking of messages, this means any non-text content: images, videos, voice messages, notes, contacts, locations, documents etc. iMessage makes it easy to share virtually anything (with or without text comment).
If you have your messages synced with iCloud, then all attachments are being synced, too. Yes, everything you send or receive is also being uploaded to iCloud – and there is no way to prevent that except by disabling message syncing (or just disabling iCloud completely, though I’d say it’s a bad idea).
As noted above, messages are not included in iCloud backups if Message sync is on. What about attachments? It’s the same. Attachments are only available on the device itself and in some secure container in the cloud (used for syncing only).
There is one more important thing about message attachments you definitely need to know.
In iOS, when you send a link to a web page or a particular file, iMessage generates a thumbnail preview. For most documents, it is just an application icon. For images, it’s a thumbnail. For videos, it’s usually the first frame. For Web sites, it’s a preview or one of the images from its HTML headers – or even video (yes, the whole one; again that depends on HTML tags). Moreover, the preview is saved as an attachment both on the device itself and also the cloud (if cloud syncing is enabled). And by the way, if you send or receive a link to an image in Dropbox, then the image itself is saved. If you share a location (using Apple Maps), then the actual part of the map (as an image) is saved, too. And for all links, favicon is also being saved (if exists).
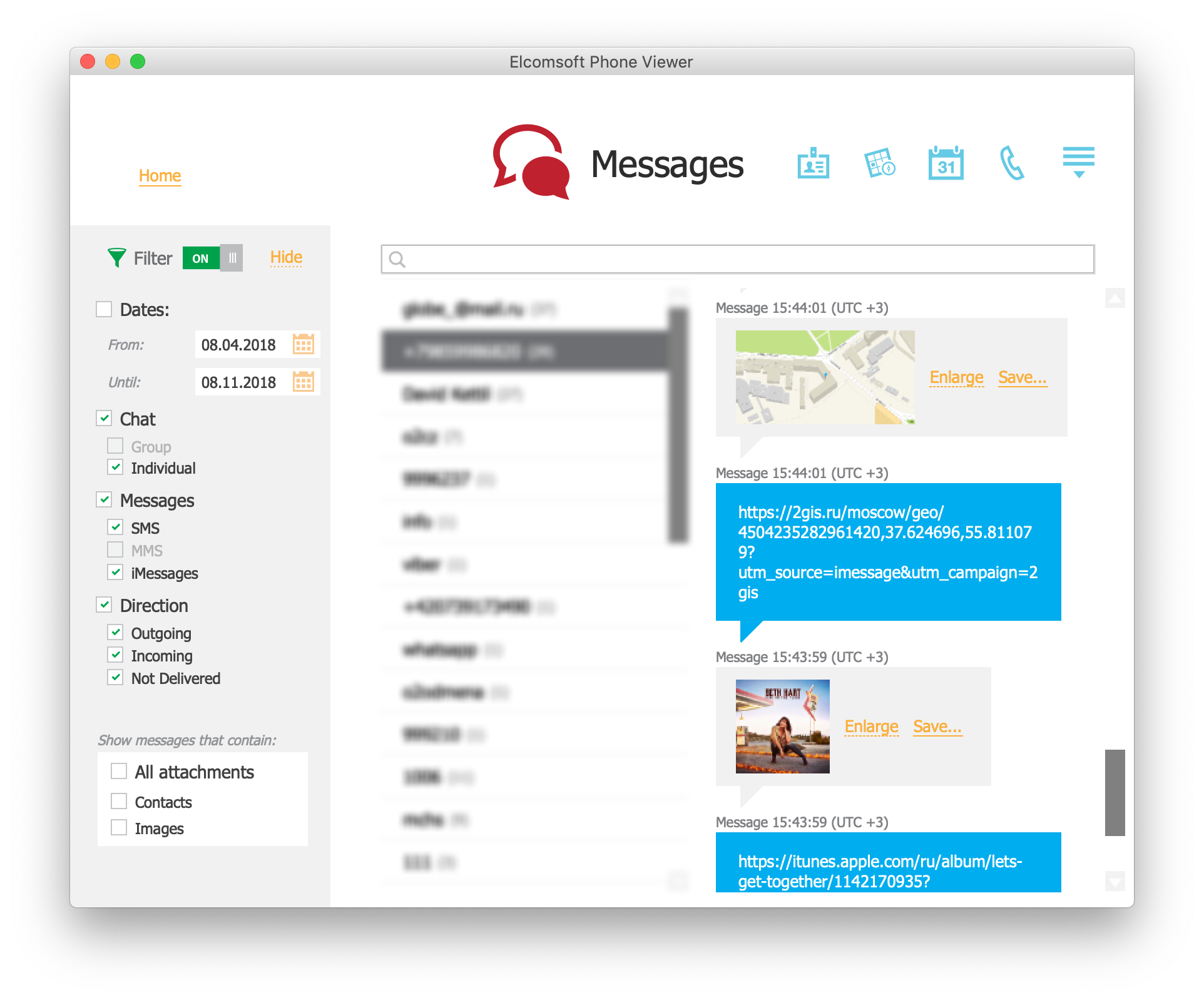
 It is worth trying with other content such as iMessage-enabled apps. Auto-generated attachments may have valuable content even if the link itself is no longer available at the time of investigation.
It is worth trying with other content such as iMessage-enabled apps. Auto-generated attachments may have valuable content even if the link itself is no longer available at the time of investigation.
Deleted Data
What happens when you delete a message (and have your messages synced with iCloud)? In one of our past discoveries, we have found that Apple does not always delete photos, web browsing history and notes.
I have got good news for you: messages (along with attachments) are properly deleted from iCloud. Apple has learned its lessons. There is still some “gap” after the message is deleted; it is still available in the cloud for some time, up to several days. Even if messages are marked for deletion, some devices connected to the account may be offline at the time when you press “delete”, and I think that could be the reason. Deleted data can be still recovered from local device backups as everything is stored in SQLite databases, but definitely not from iCloud; at least we could not do that.
So What’s the Deal?
Back to iMessage privacy and security.
Yes, messages in iCloud are encrypted, but not exactly end to end. Technically, they are encrypted using a key that is stored in iCloud Keychain. And yes, you can access messages including non-text content (attachments) such as images, videos, locations, contacts, notes and more if you manage to extract iCloud Keychain first. Accessing iCloud Keychain is not easy: you need not just the user’s credentials, but also the passcode of one of the trusted devices (the device itself is not needed, you just need the passcode).
What else do you need to get messages (along with attachments, i.e. non-text content)? Elcomsoft Phone Breaker (to download everything from iCloud) and Elcomsoft Phone Viewer (to browse the data). Read Messages in iCloud: How to Extract Full Content Including Media Files, Locations and Documents for more details.
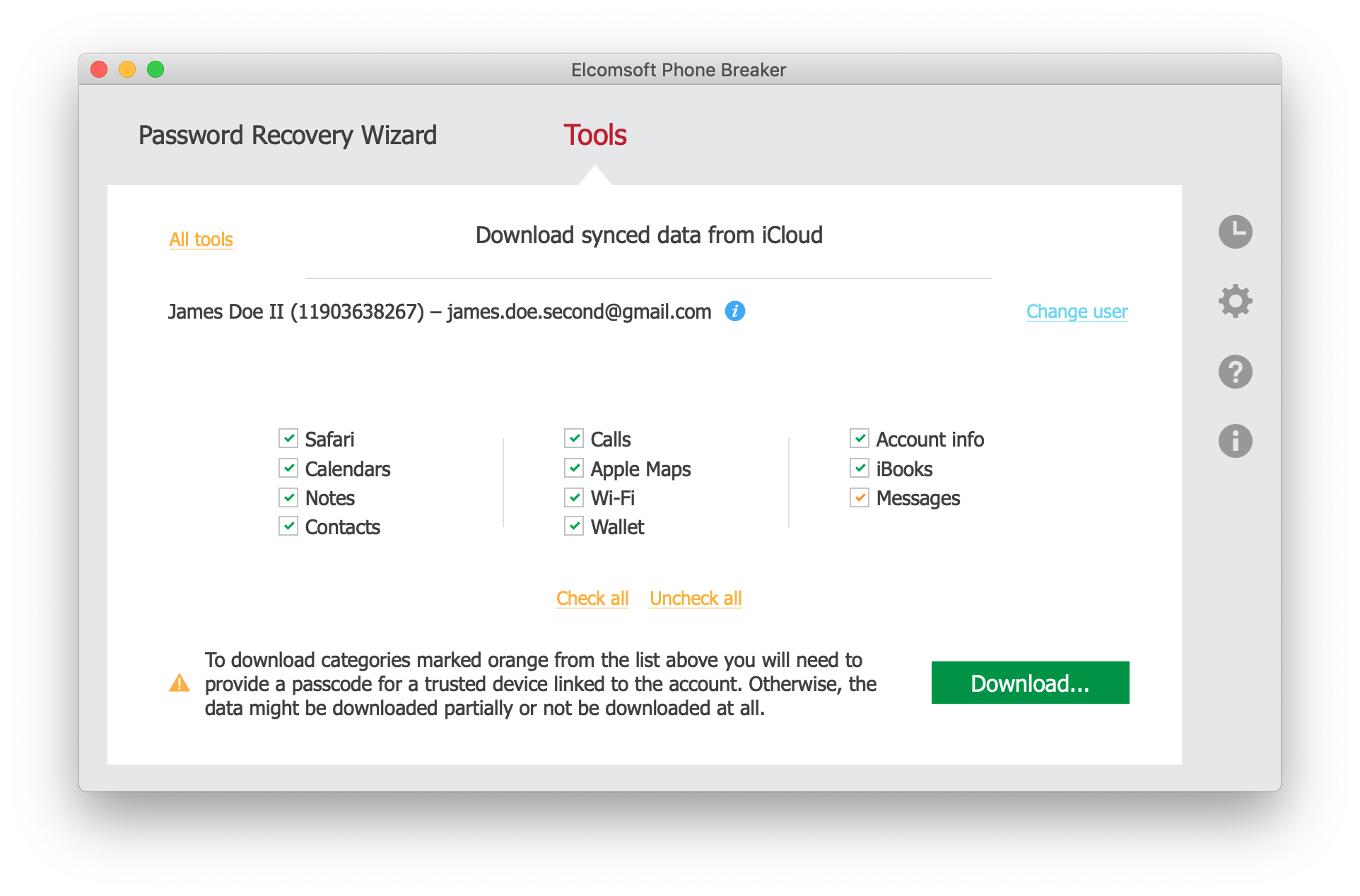 Still, how secure is iMessage? There is no definite answer. Messages and attachments have better protection and an addition level of encryption compared to other content. In order to decrypt them, one needs to acquire the keychain first, and this is troublesome.
Still, how secure is iMessage? There is no definite answer. Messages and attachments have better protection and an addition level of encryption compared to other content. In order to decrypt them, one needs to acquire the keychain first, and this is troublesome.
Can Apple read your messages? No, they really do not have access to your iCloud keychain and your messages, and this is the reason why they do not include them into the bunch of data available with “Get a copy of your data” at Apple ID Data and Privacy (thanks to GDPR). Law enforcement? They can send a request to Apple, or use our software. The first option is not going to work for messages, but using our software does; again, only if you have the user’s credentials and the passcode.
Are there alternatives? Of course! With Apple ID, password, second authentication factor and the passcode, one can connect a new device to the account, enable iCloud Keychain, wait until the device is completely synced, set iTunes backup password, create a local backup, and open the backup with some forensic software to analyze. See Cloud Forensics: Why, What and How to Extract Evidence (I doubt you will like the process).





