How to Reset or Recover Windows SYSKEY Passwords
December 7th, 2018 by Oleg Afonin
Category: «General»
Some 22 years ago, Microsoft made an attempt to make Windows more secure by adding an extra layer of protection. The SAM Lock Tool, commonly known as SYSKEY (the name of its executable file), was used to encrypt the content of the Windows Security Account Manager (SAM) database. The encryption was using a 128-bit RC4 encryption key.
The user had an option to specify a password that would protect authentication credentials of Windows accounts stored in the SAM database. If SYSKEY password was set, Windows would ask for this password during startup before displaying the login and password prompt.
While SYSKEY was not using the strongest encryption, attacking (brute-forcing or resetting) the user’s Windows login and password would not be possible without first decrypting the SAM database. As a result, a SYSKEY password would require the attacker to brute-force or reset SYSKEY protection prior to accessing the system’s Windows accounts. More importantly, an unknown SYSKEY password would prevent the user’s system from fully booting. This fact was widely exploited by ransomware and commonly abused by “tech support” scammers who locked victims out of their own computers via fake “tech support” calls.
Due to SAM database encryption, reinstalling or repairing Windows would not solve the issue unless the user had access to a recent backup or a System Restore Point. For this reason, Microsoft removed the ability to set SYSKEY passwords in Windows 10 (release 1709) and Windows Server 2016 (release 1709), steering users towards the much more secure BitLocker encryption instead. However, older systems are still susceptible to SYSKEY ransomware attacks.
Since SYSKEY protection is fairly old by hi-tech standards, it is no longer secure (it never been in the first place). Victims of SYSKEY ransomware or “tech support” scammers can now restore their systems by recovering or resetting SYSKEY password. Elcomsoft System Recovery has the ability to discover or reset SYSKEY passwords in order to restore the system’s normal boot operation. This is also the first time ever we’re publishing screen shots of the Elcomsoft System Recovery user interface.
Removing SYSKEY Password
SYSKEY encryption is a relatively little known feature that was actively exploited by “tech support” scammers and ransomware. Once a SYSTEM password is activated, the entire SAM registry hive is encrypted. This makes it difficult to restore Windows to working condition, especially if the scammer has also removed all System Restore points. Victims of this scam will see the following message when they attempt to start their computer:
“This computer is configured to require a password in order to start up.”
Elcomsoft System Recovery can attempt to automatically reset SYSKEY protection. A straightforward removal of SYSKEY password bears the risk of breaking the Windows boot process. For this reason, Elcomsoft System Recovery performs a number of safety checks to determine whether resetting a SYSKEY password of the particular system may cause issues.
Note: instructions below assume that you already created a bootable media containing Elcomsoft System Recovery 5.40 or newer.
In order to remove an unknown SYSKEY password, do the following.
- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- In Elcomsoft System Recovery, specify the disk or partition where Windows is installed, then click Next.
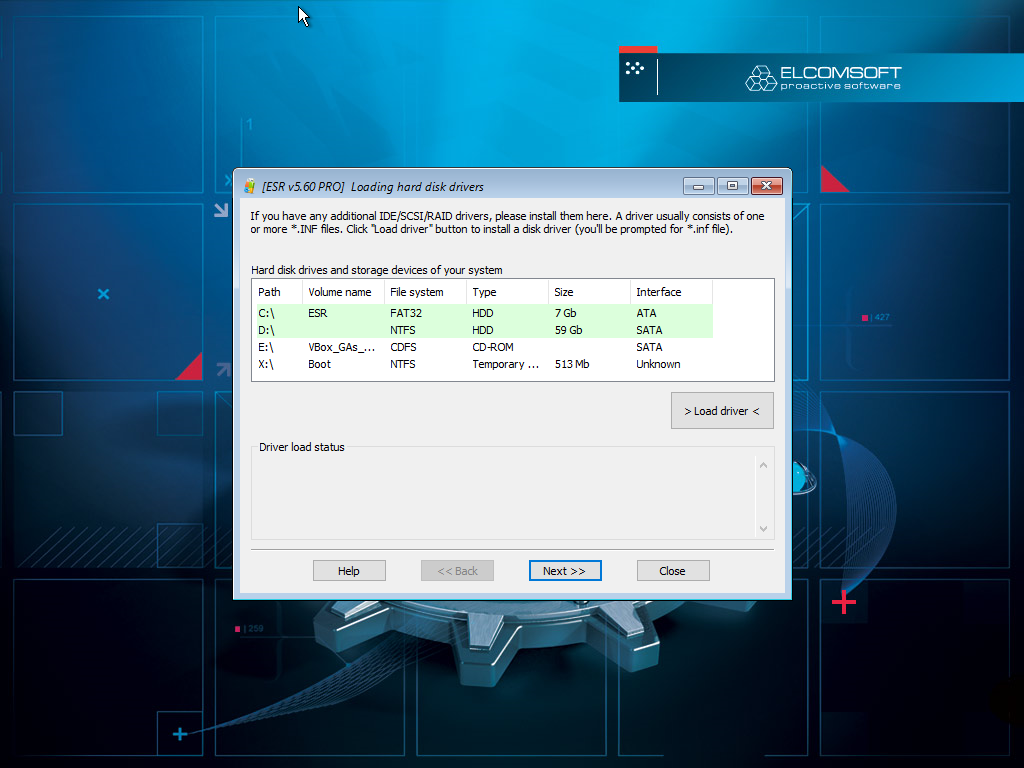
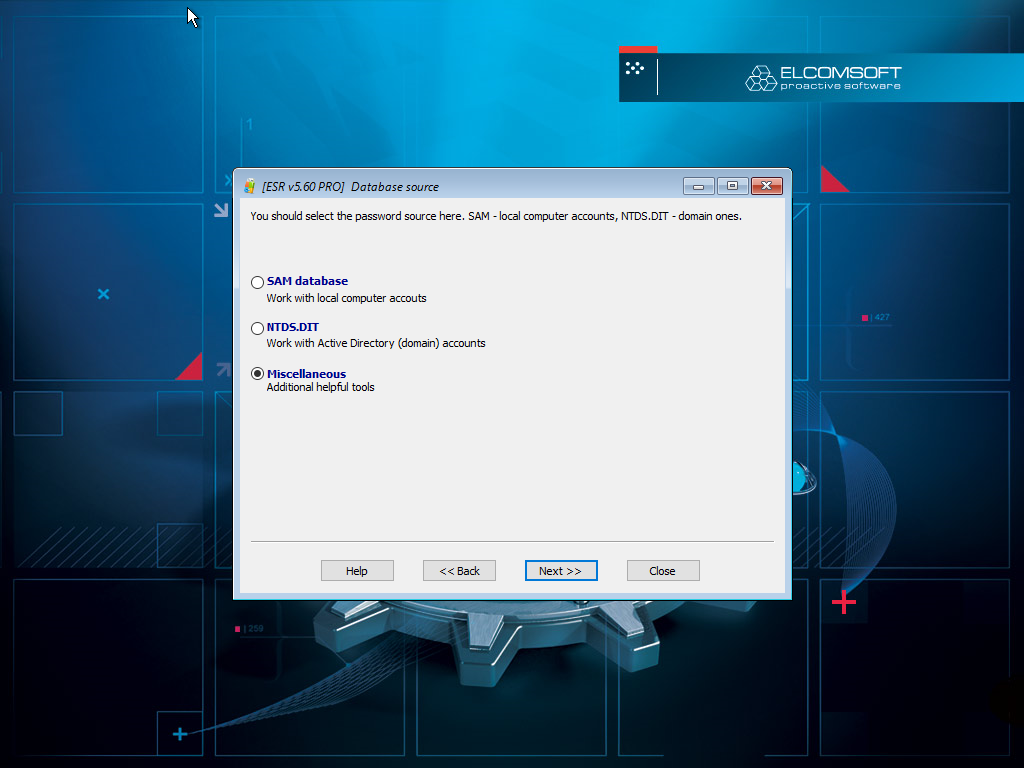
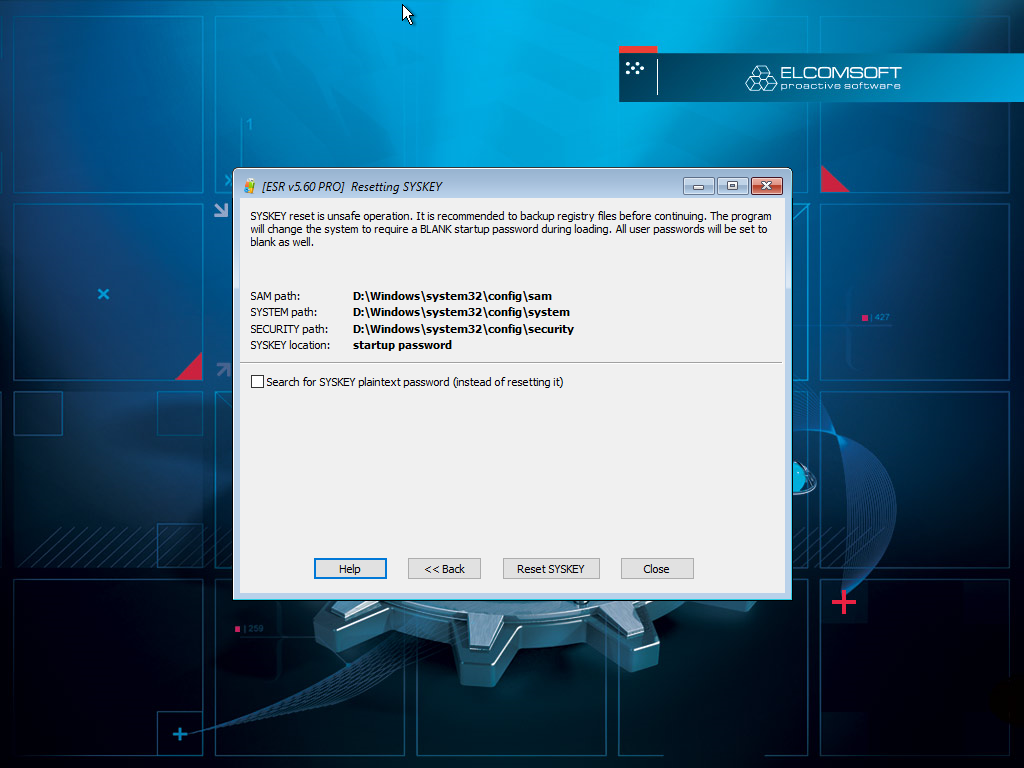
- The ability to remove SYSKEY passwords is located under Miscellaneous.
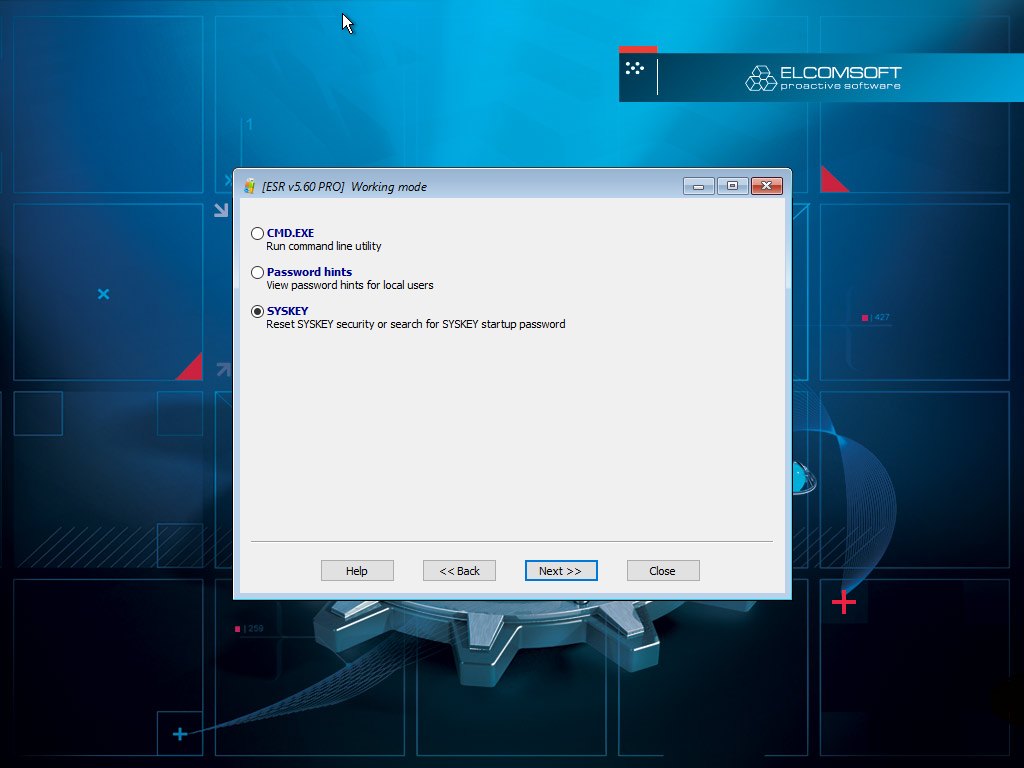
- Choose SYSKEY.
- Select whether ESR should automatically search for the SAM database or specify its location.
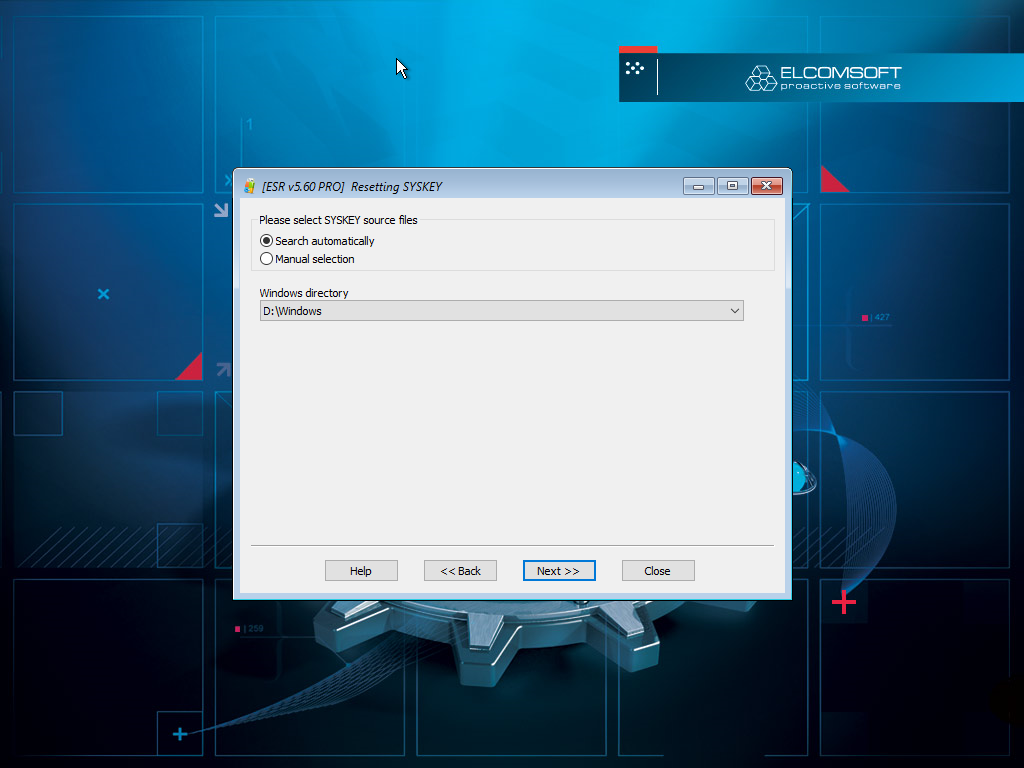
- The tool will perform the necessary safety checks and warn you if a potential issue is detected. To just reset the password, leave the “Search…” option blank. Click “Reset SYSKEY” to finish.
- Finally, reboot your computer. Windows should start normally.
If a potential issue is discovered, you will see the following warning:
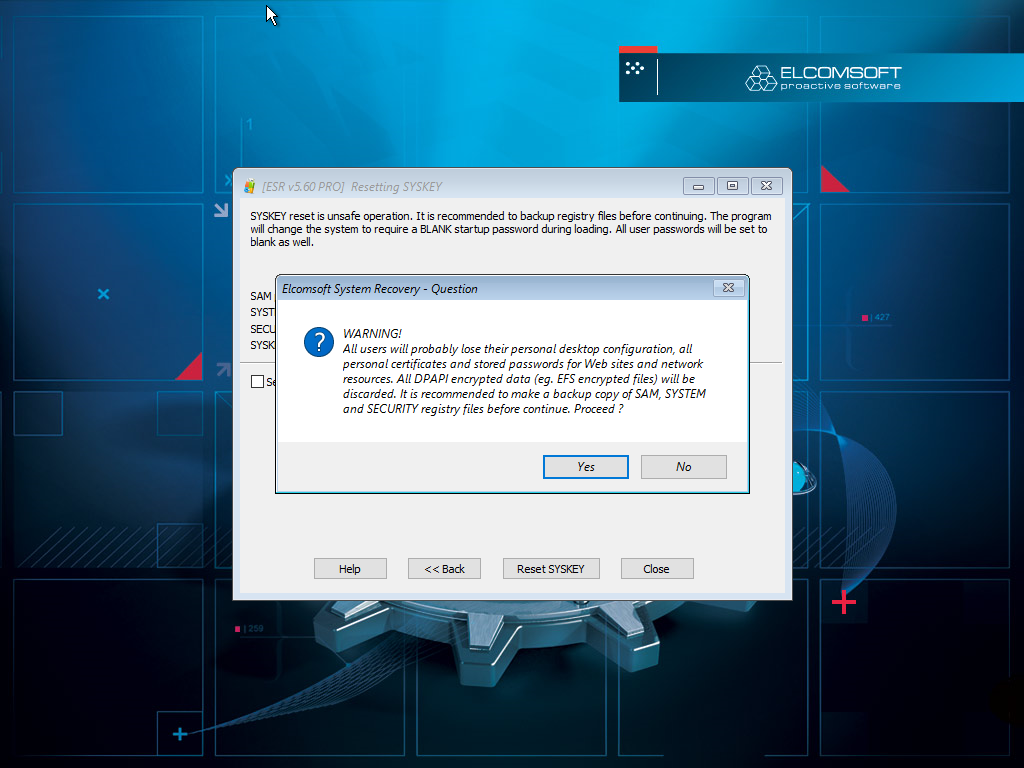
If you proceed, you will lose access to DPAPI encrypted data (EFS-encrypted files and folders). In addition, we recommend that you make backup copies of SAM, SYSTEM and SECURITY registry hives (this must be done manually).
Discovering SYSKEY Password
Resetting the SYSKEY password may or may not work depending on configuration of the particular system. Recovering the SYSKEY password is a significantly safer operation that does not have the potential negative impact of simply resetting the password. Elcomsoft System Recovery can automatically check your computer to look up for cached SYSKEY passwords throughout the system. The tool will analyze various registry keys, temporary files and databases to look up for a cached copy of SYSKEY password. If this is successful, SYSKEY protection can be removed instantly and risk-free.
In order to look up for SYSKEY password, do the following:
- Boot your computer to bootable storage media with Elcomsoft System Recovery. Depending on your computer’s motherboard manufacturer, you may need to press Del, F8, F11, F12 or another key to invoke a special menu to temporarily override boot order or to enter UEFI/BIOS setup.
- Follow steps 2 through 6 in Elcomsoft System Recovery. However, this time make sure the “Search for SYSKEY plain text password” option is selected.

- You will have the choice between a fast or thorough scan. Tap Recover SYSKEY to continue. The tool will attempt to locate the SYSKEY password on your computer.
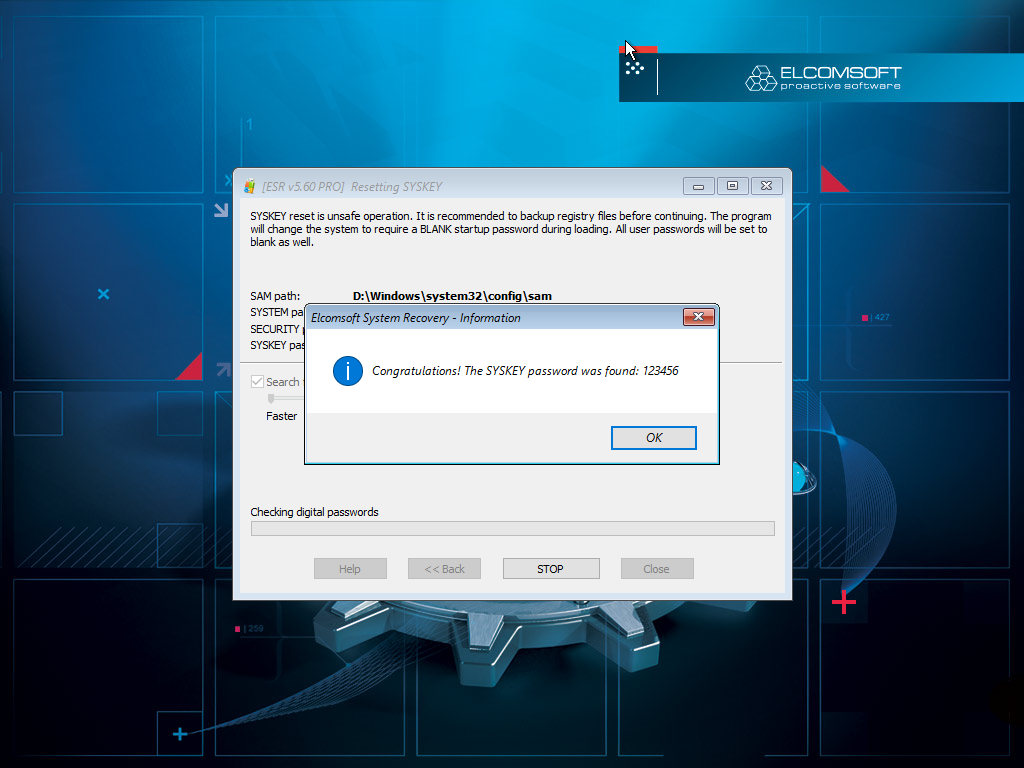
- Take a note of the discovered SYSKEY password and reboot your computer. Enter the discovered SYSKEY password when prompted.










