The Screen Time passcode is an optional feature of iOS 12 and 13 that can be used to secure the Content & Privacy Restrictions. Once the password is set, iOS will prompt for the Screen Time passcode if an expert attempts to reset the device backup password (iTunes backup password) in addition to the screen lock passcode. As a result, experts will require two passcodes in order to reset the backup password: the device screen lock passcode and the Screen Time passcode. Since the 4-digit Screen Time passcode is separate to the device lock passcode (the one that is used when locking and unlocking the device), it becomes an extra security layer effectively blocking logical acquisition attempts.
Since users don’t have to enter Screen Time passcodes as often as they are required to enter their screen lock passcode, it is easy to genuinely forget that password. Apple does not offer an official routine for resetting or recovering Screen Time passcodes other than resetting the device to factory settings and setting it up as a new device (as opposed to restoring it from the backup). For this reason, the official route is inacceptable during the course of device acquisition.
Unofficially, users can recover their Screen Time passcode by making a fresh local backup of the device and inspecting its content with a third-party tool. In iOS 12, the Screen Time passcode can be only recovered from password-protected backups; in iOS 13, the passcode cannot be obtained even from the local backup. If local backups are protected with a password not known to the expert, the situation becomes a deadlock: one cannot reset an unknown backup password without a Screen Time passcode, and one cannot access the Screen Time passcode without decrypting the backup.
Elcomsoft Phone Breaker 9.20 offers an effective solution to the deadlock by obtaining Screen Time passcodes from the user’s iCloud account. The tool supports all versions of iOS 12 and 13.
Why Forensic Experts May Need the Screen Time Passcode
Even if no further restrictions are configured on the user’s device, the sole presence of the Screen Time passcode on the device means that certain features remain inaccessible. The most needed feature locked by the Screen Time passcode is the ability to reset unknown passwords protecting local (iTunes) backups.
iTunes backups are a major source of data during the course of logical extraction. If the backup is protected with a password, its entire content gets encrypted. Attacks on the password are extremely slow (around 100 passwords per second when using a GPU-assisted attack). While iOS 11, 12 and 13 do allow resetting the backup password from the device settings, one needs to enter the device screen lock password in order to do the reset. If the user has a Screen Time passcode, you will need to enter that passcode in addition to the screen lock passcode. Knowing the Screen Time passcode, you can remove this additional layer of protection and proceed to resetting the local backup password.
Screen Time iCloud Sync
Since iOS 12, Screen Time information can be synchronized to iCloud if the user activates the Share across devices feature. In addition to Screen Time passcodes, the system will synchronize comprehensive usage statistics of all devices enrolled in “Share across devices” and connected to the same iCloud account. If one or more child accounts are configured for the family, each child can have their own Screen Time password, which typically is different from their parents’ passwords.
By extracting and analyzing Screen Time information, experts can extract Screen Time passwords, thus gaining the ability to remove Screen Time protection and/or to reset the password protecting local (iTunes) backups. This in turn makes logical acquisition easily possible. Since iOS 13, the Screen Time password is not extractable from local backups, even if they are encrypted with a known password. For this reason, cloud extraction is the only way of obtaining Screen Time passwords from devices running iOS 13.
Screen Time information in iCloud is securely encrypted. Apple used the same protection mechanisms as it did for protecting the iCloud Keychain. The data is encrypted with an encryption key that can be decrypted by entering a screen lock passcode of the enrolled device. This means that, in order to access Screen Time data, you will need all of the following: the user’s Apple ID credentials (login, password and 2FA code) and their screen lock password.
Extracting the Screen Time Password with Elcomsoft Phone Breaker
In order to extract the Screen Time password from iCloud, you will need Elcomsoft Phone Breaker 9.20 or newer. At the time of this writing, Elcomsoft Phone Breaker is the only tool on the market that can obtain Screen Time passwords from the cloud (as opposed to extracting them from local backups).
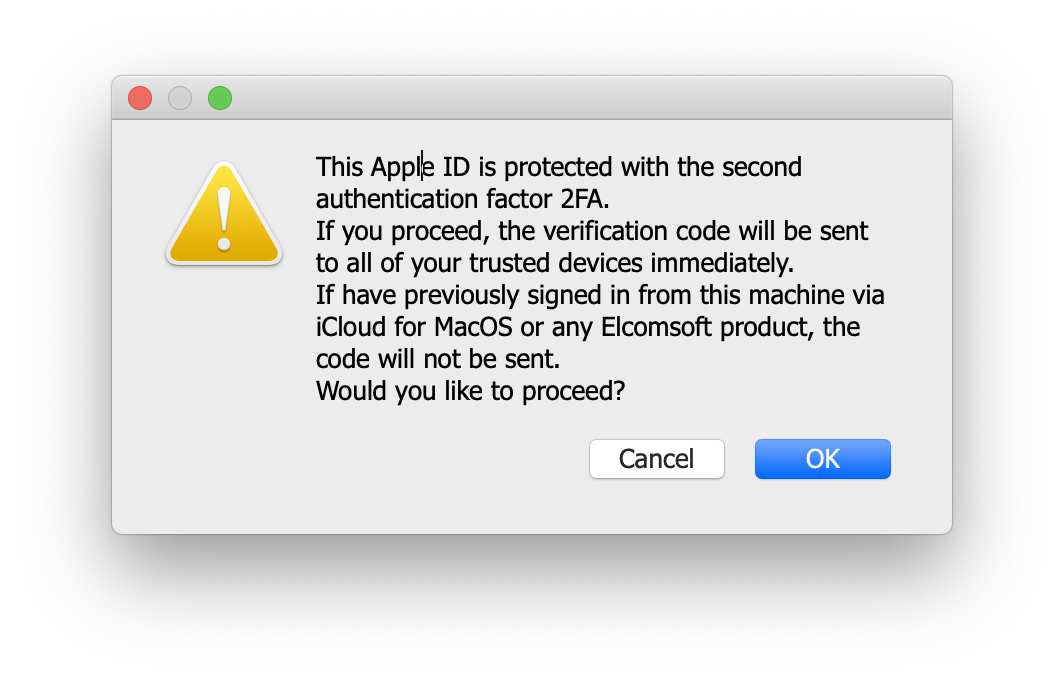
In order to have Screen Time passcodes synchronized with the user’s account, the “Share across devices” setting must be already enabled on the device. If it’s not, the Screen Time passcode remains local and cannot be extracted from the cloud. The “Share across devices” feature requires 2FA, so passing two-factor authentication will be mandatory.
Important: if the Screen Time password is configured and is unknown, but the “Share across devices” setting is not already enabled on the device, the Screen Time password will not sync to iCloud. If you attempt to enable “Share across devices” yourself, you will be prompted for the Screen Time password, which is a deadlock. As a result, you will be only able to extract Screen Time passcodes from iCloud if the “Share across devices” setting is already enabled.
- Launch Elcomsoft Phone Breaker
- Select “Synced data”
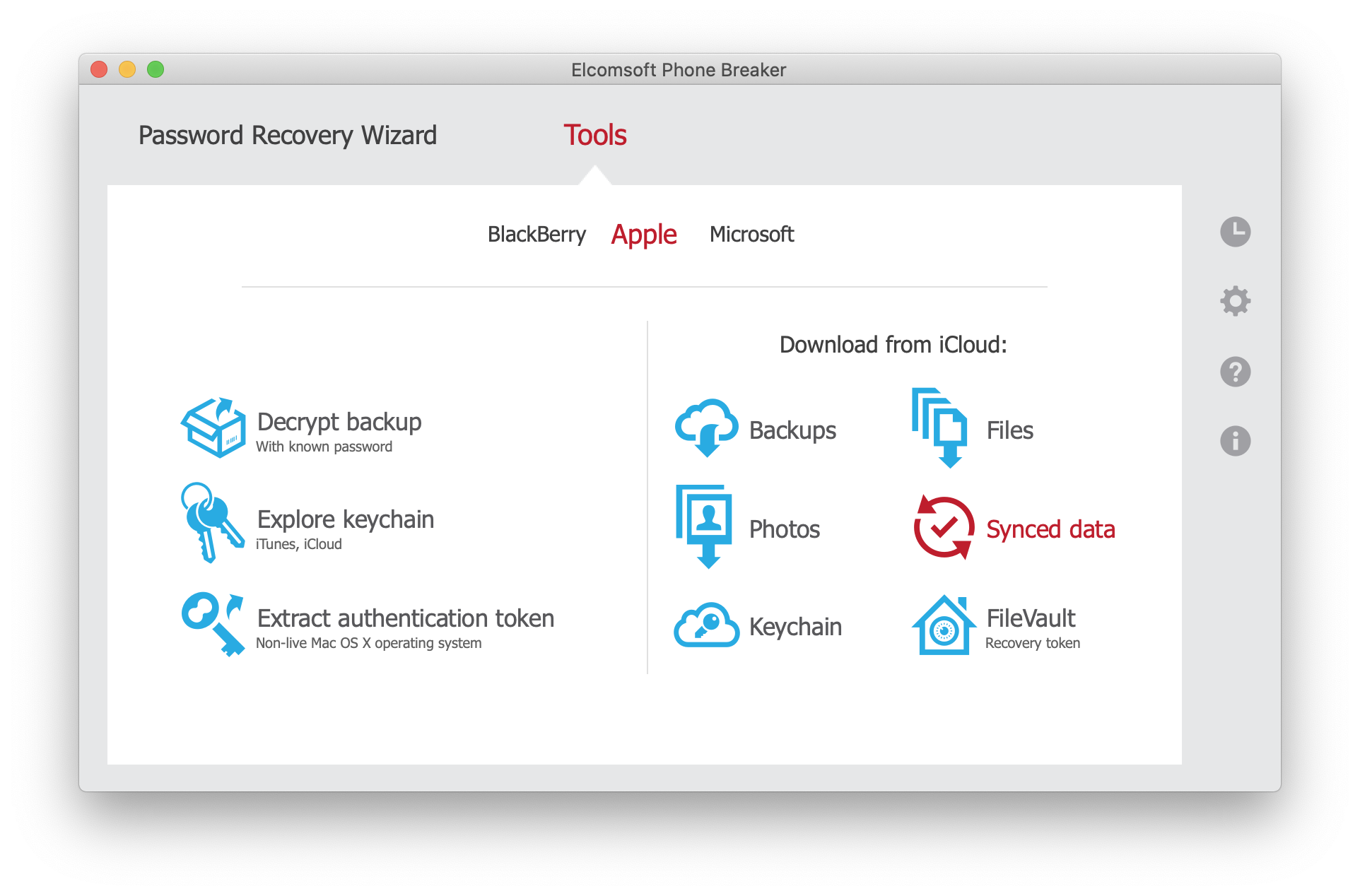
- Sign in to the user’s Apple account (login/password/2FA only)
- On the screen that follows, select the “Screen Time” check box

- Phone Breaker will display the list of enrolled devices. You will be prompted for device screen lock passcode. Select a device from the list and enter its passcode (or system password if it’s a Mac) to continue
- Download the data
- Launch Elcomsoft Phone Viewer and open the data you have just downloaded

- The Screen Time passcode will be displayed on the main screen of Elcomsoft Phone Viewer
Additional information is available in Elcomsoft Phone Viewer if you open the “Screen Time” tab.

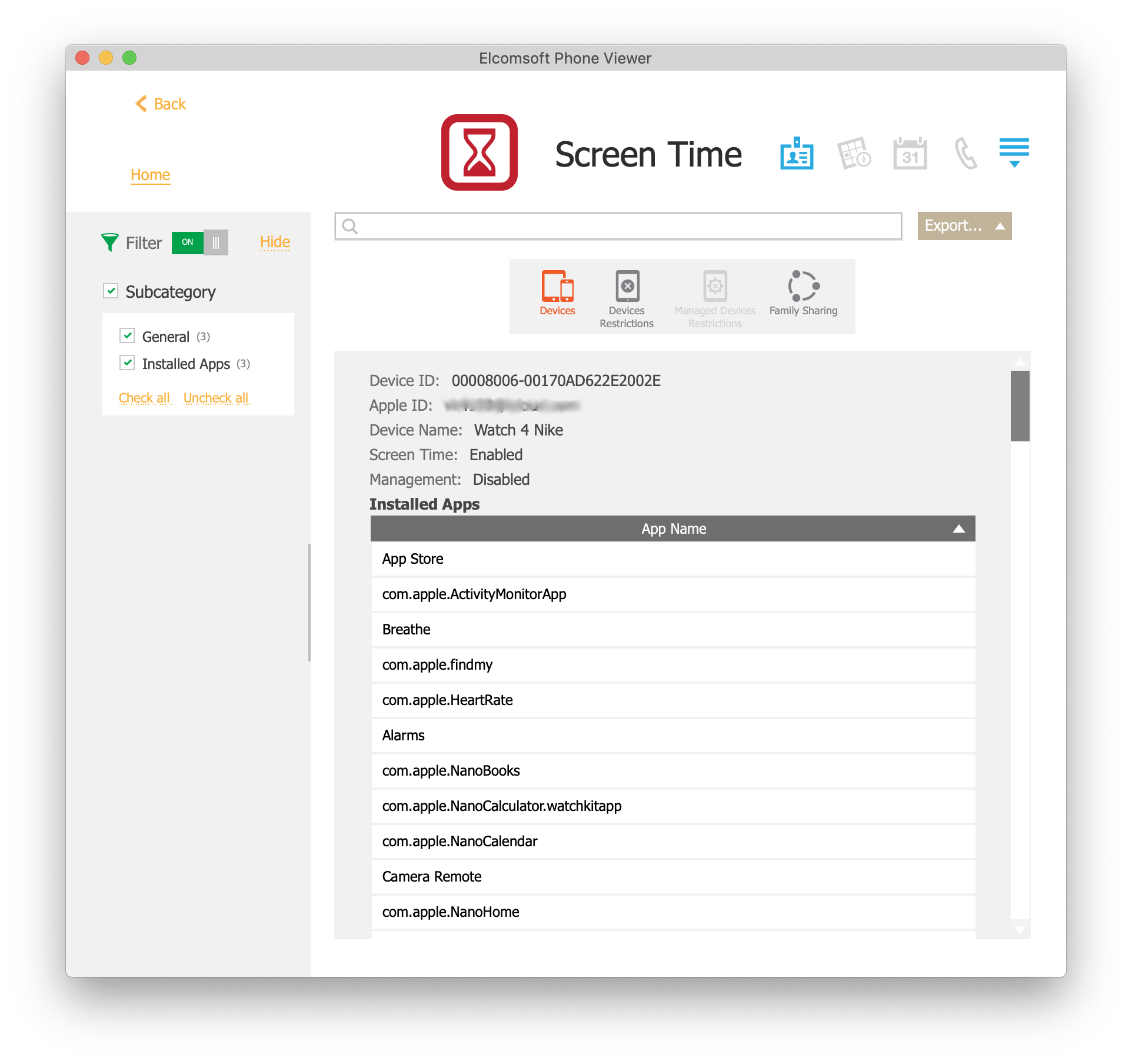
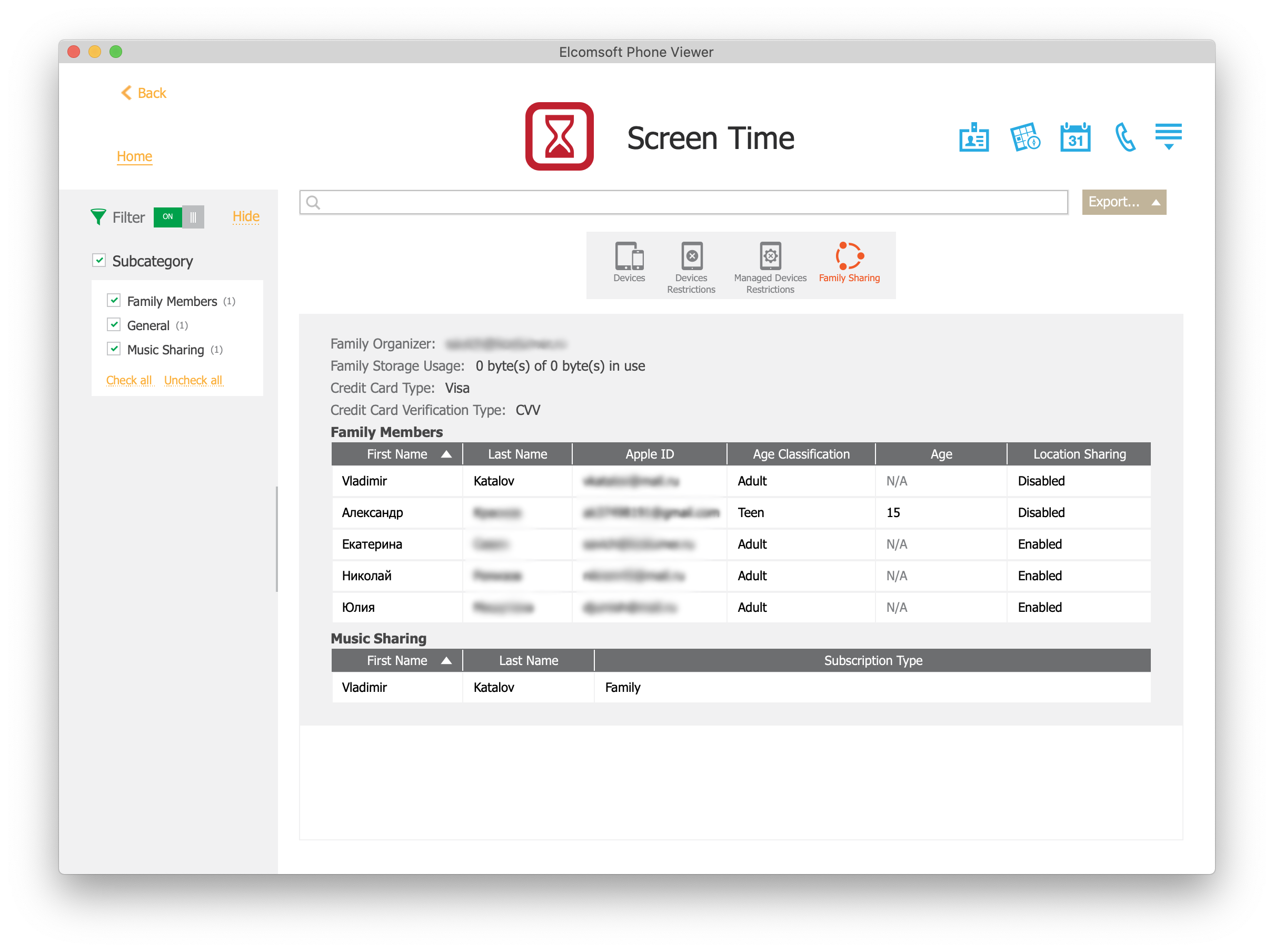
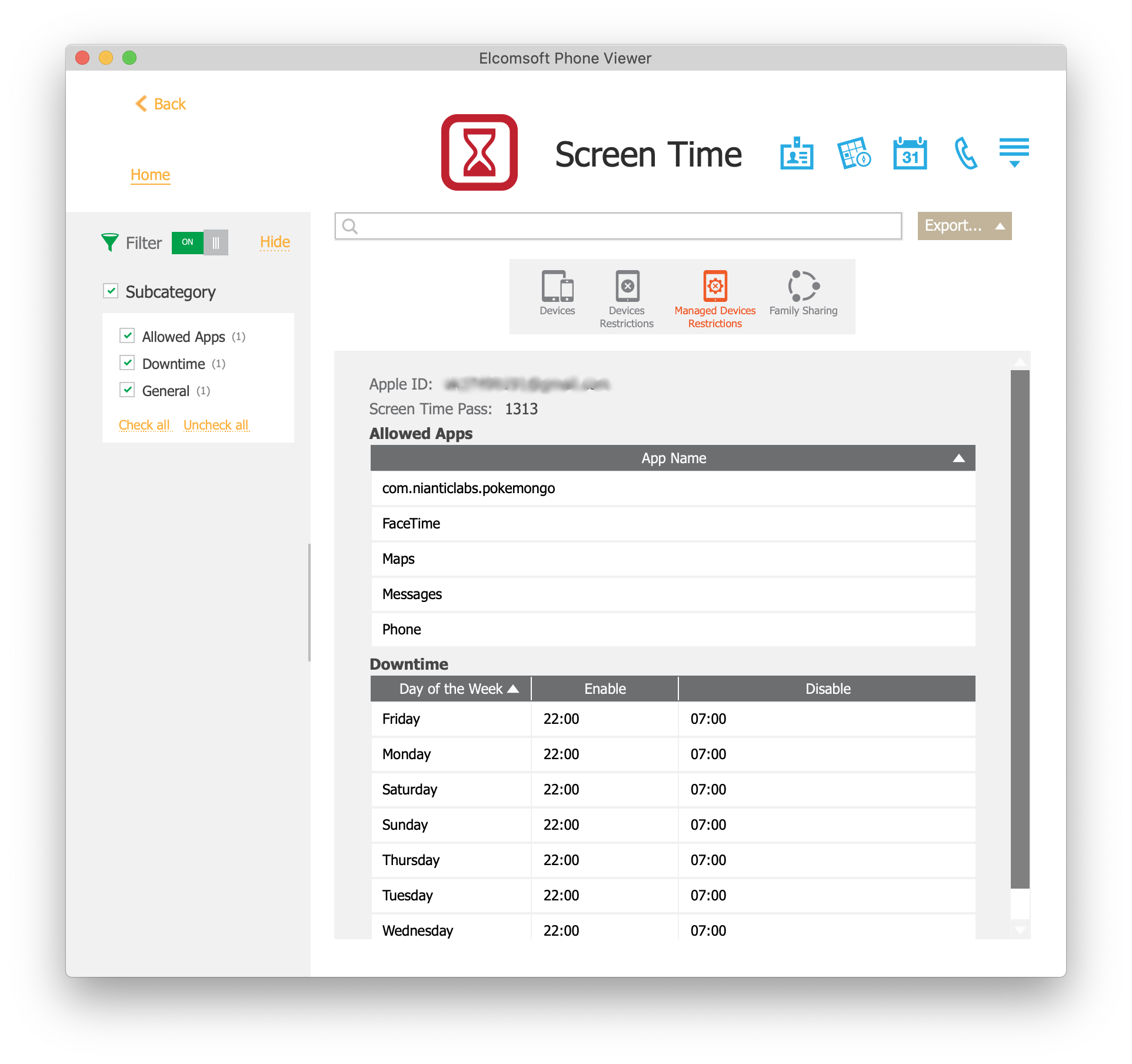

The following Screen Time data is extracted: the Screen Time password (both parents’ and children’s, if any child accounts are present); information about all devices sharing Screen Time data through iCloud, including the list of installed applications on these devices (including Mac computers and Apple Watch). In addition, the tool extracts information about configured restrictions. You can view all of that data in Elcomsoft Phone Viewer.
The Next Step
If the purpose of obtaining the Screen Time passcode was resetting the local backup password, you can now open the Settings app and tap Reset All Settings. You will be consecutively prompted for the device screen lock passcode and Screen Time passcode. After resetting the local backup password, make sure to specify your own password (via iTunes or by using Elcomsoft iOS Forensic Toolkit that automatically sets the password of “123”). If using iOS 13, you will need to confirm the change by entering the device screen lock password (on the device) when prompted. You must specify a known local backup password to decrypt the Keychain and Health data. In iOS 13, you will only have access to Safari browsing history and some other data (such as calllogs) in local backups that are password-protected.
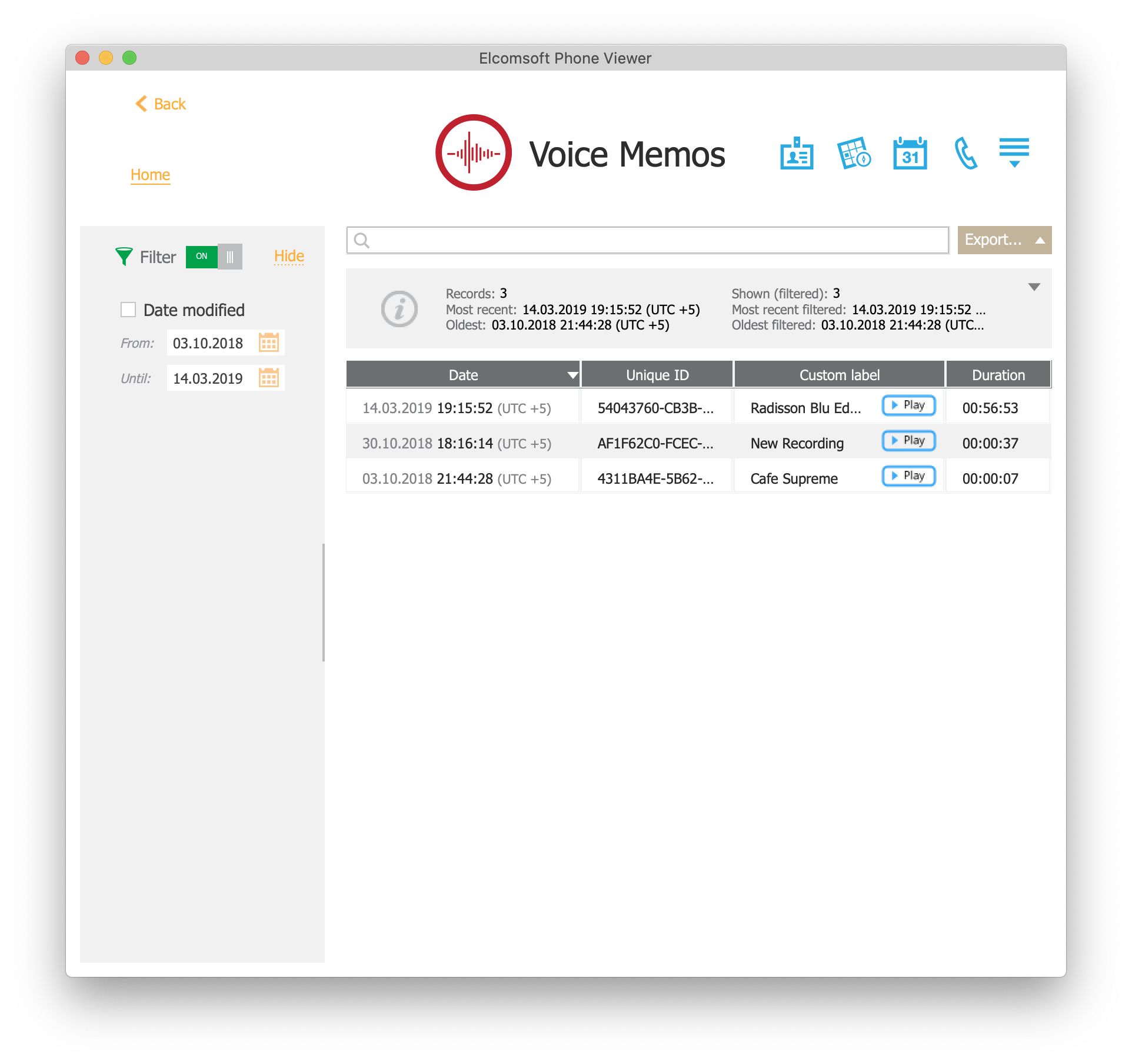
Extracting Voice Memos from iCloud
Voice Memos is a native app made by Apple and available in the App Store. The app makes it possible to record audio clips using the iPhone’s built-in microphone. In iOS 12, Voice Memos became a fully-featured audio recording and editing app. Voice Memos is frequently used to record lectures and presentations, interviews and auditions. iOS 12 and 13 as well as macOS 10.15 Catalina can synchronize the recorded audio clips to iCloud.
Elcomsoft Phone Breaker can download Voice Memos clips from iCloud synced data. This is how to do that.
- Launch Elcomsoft Phone Breaker
- Select “Synchronized data”
- Sign in to the user’s Apple account (login/password/2FA or token)
- On the screen that follows, select the “Voice Memos” check box
- Download the data
You can now analyze Voice Memos with Elcomsoft Phone Viewer.