Home users and small offices are served by two major manufacturers of network attached storage devices (NAS): QNAP and Synology, with Western Digital being a distant third. All Qnap and Synology network attached storage models are advertised with support for hardware-accelerated AES encryption. Encrypted NAS devices can be a real roadblock on the way of forensic investigations. In this article, we’ll review the common encryption scenarios used in home and small office models of network attached storage devices made by Synology.
Encryption in Network Attached Storage Devices (NAS)
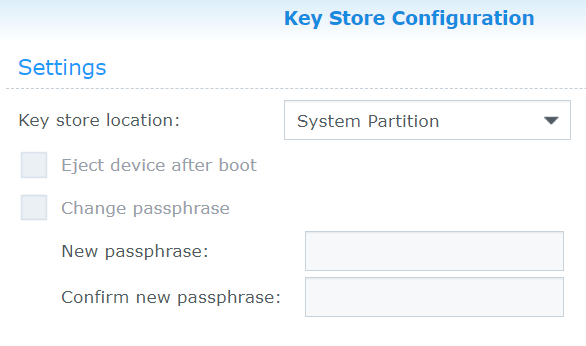
Along with other manufacturers of network attached storage for home users, Synology offers users the option to store encryption keys in the built-in key storage. This feature adds the convenience of automatically mounting volumes on reboot.
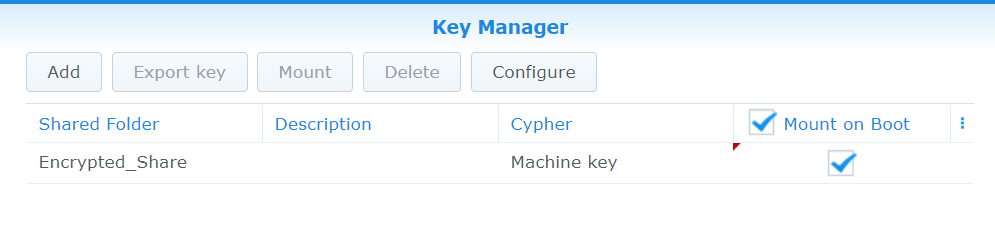
Note: when the key is stored on an internal hard drive, the wrapping passphrase cannot be changed. This is by design. Synology uses a single fixed, pre-programmed passphrase on all of its NAS units.
At the same time, his design presents a potential vulnerability. As long as the key and the disks are intact, the attacker may decrypted the data without brute-forcing the key. The intended usage scenario of built-in encryption with on-device keys is the safe disposal of disks independent of the encryption key. Manufacturers recommend backing up the encryption keys protected with a strong password.
Our approach to decrypting the data stored on NAS devices is based on the assumption that at least one of the following conditions is true:
- The user added the encryption key to on-device storage, optionally allowing shares to mount on boot, as shown in the picture:
- The user stored the encryption key on an external device, and that external device is also available, as shown in the picture:

- The user saved the encryption key, and that key is available. Note that Synology automatically saves the encryption key in a file on the user’s computer when the user creates the encrypted share. The name of the file will be <name_of_encrypted_share>.key:

- The encryption passphrase is known.
In order to decrypt the encrypted share, experience using Linux or forensic tools supporting eCryptFS folders is required.
Synology: File-Based Encryption
Synology uses folder-based encryption based on eCryptFS, an open-source stacked cryptographic file system. Detailed information on eCryptFS is available here. From the point of view of a regular consumer, Synology’s encryption implementation is very restrictive. The encryption passphrase cannot be changed without decrypting and re-encrypting all data. In addition, file names stored in encrypted folders cannot contain more than 143 Latin characters in their names.
“There is no way to change the passphrase on the fly as ecryptfs encrypts each file with that passphrase individually and all files need to be rewritten with the new passphrase.
So all you can do is create a new directory, mount it with the new passphrase and copy all the files over there.” (Grumbel)
Synology DSM relies on the built-in Key Manager to store encryption keys. Stored encryption keys allow users mounting their encrypted shares automatically once the Synology NAS boots up; otherwise, the passphrase must be entered on every boot.

In Synology devices, the encryption passphrase is wrapped (encrypted with a different passphrase). If we treat the encryption passphrase as a Media Encryption Key (MEK), the wrapping passphrase becomes the Key Encryption Key (KEK). One of the goals of file system encryption is preventing the attacker from removing the hard drive(s) and decrypting the data. In Windows systems with BitLocker device encryption, this is achieved by wrapping the encryption key with a unique sequence obtained from the hardware-bound TPM module.
Naturally, this was the expectation when we started researching the encryption in Synology devices. In reality, Synology does not appear to be using hardware-bound encryption. Instead, a single, pre-programmed wrapping passphrase (KEK) is used to encrypt the encryption passphrase (MEK). As a result, both the MEK and the KEK can be stored on the hard drive (if the user adds their key to the DSM Key Manager); both can be extracted from the cold device, the MEK unwrapped and used to decrypt the data.
Synology: Encryption Vulnerabilities
Vulnerability 1: The stored encryption key can be intercepted and the data accessed if the user had the encryption key stored in DSM Key Manager.
Vulnerability 2: All Synology NAS devices use a single, pre-set wrapping passphrase as opposed to the user’s logon password.
The following command reveals the user’s original encryption passphrase:
printf "%s" "\$1\$5YN01o9y" | ecryptfs-unwrap-passphrase keyfile.key -
Where “$1$5YN01o9y” is the fixed wrapping passphrase and “keyfile.key” is the wrapped encryption key. The passphrase can be used to mount the encrypted share:
mount -t ecryptfs -o key=passphrase,ecryptfs_cipher=aes,ecryptfs_key_bytes=32,ecryptfs_passthrough=no,ecryptfs_enable_filename_crypto=yes,passwd=$(printf "%s" "\$1\$5YN01o9y" | ecryptfs-unwrap-passphrase /path/to/keyfile.key -) /path/to/encrypted/folder /path/to/mountpoint
The /path/to/keyfile.key, /path/to/encrypted/folder and /path/to/mountpoint must be replaced with your actual encryption targets. Synology devices typically mount encrypted shares under the following path:
/Volume<N>/@<name_of_encrypted_share@
In our example, the path to the encrypted share is as follows:
/Volume1/@Encrypted_Share@
Additional information:
- How To Recover Synology encrypted folders in Linux (Robert Castle)
- How to decrypt ecryptfs file with private key instead of passphrase (slackexchange)
- Automatically mounting encrypted folders (in German) (synology-forum.de)
- Script: Decrypt encrypted folders via keyfile (.key) (in German) (synology-forum.de)
If the user opts to store the encryption key on an external USB device, DSM prompts changing the default wrapping passphrase.
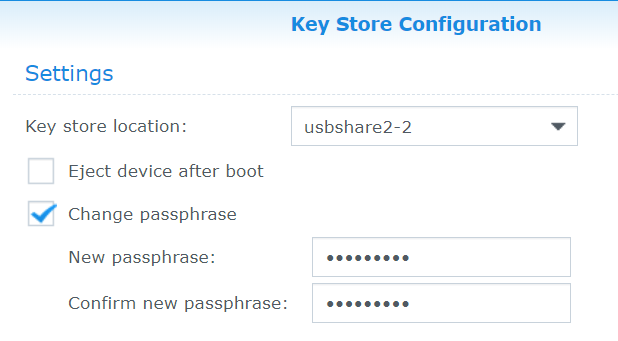
However, users can still use that key to make the encrypted volumes automatically mount on startup. To facilitate that, DSM caches the wrapping passphrase. This wrapping passphrase can be extracted from DSM and used to decrypt the MEK.
What if the user does not store the encryption passphrase in the DSM Key Manager? In this case, the encrypted shares must be unlocked by manually typing the encryption passphrase. As this is the case, users must memorize the passphrase; the passphrase cannot be changed without re-encrypting the entire content of the encrypted share. All this opens the door to attacks based on the human factor (1, 2, 3 and 4).
Future work
We have plans on determining the exact location of the keys stored in the DSM Key Manager, as well as the location of the wrapping passphrase that is used to encrypt the MEK. The next logical step would be writing a bunch of shell scripts to automate the recovery of encrypted volumes from “cold” devices or disk images.
Conclusion
In this article, you can find no out of the box “we have a tool for that” type of solutions. We demonstrated vulnerabilities in some of the most commonly used hardware-backed implementations of encryption used by major manufacturers of attached storage devices for consumers. As we demonstrated, relying on built-in encryption in network-attached devices manufactured by Synology may leave information vulnerable depending on whether or not the key is stored in the built-in Key Manager.









