VeraCrypt is a de-facto successor to TrueCrypt, one of the most popular cryptographic tools for full-disk encryption of internal and external storage devices. Compared to TrueCrypt, which it effectively replaced, VeraCrypt employs a newer and more secure format for encrypted containers, and significantly expands the number of supported encryption algorithms and hash functions. Learn how to break VeraCrypt containers with distributed password attacks.
VeraCrypt Encryption
Full-disk encryption tools rely on symmetric cryptography to encrypt data, and employ one-way transformations (hash functions) to protect the binary data encryption key with the user’s password. When attacking an encrypted container, the expert must either know the exact combination of the cipher and hash function, or try all of their possible combinations. If the expert makes the wrong choice of a hash function or cipher, the data will not be decrypted even if the correct password is known.
During the times TrueCrypt ruled the world of third-party full-disk encryption tools, users were presented with the choice of three individual encryption algorithms (AES, Serpent, and Twofish). In addition, five combinations of cascaded algorithms (AES-Twofish, AES-Twofish-Serpent, Serpent-AES, Serpent-Twofish-AES and Twofish-Serpent) were available, making the total of eight possible combinations. Passwords could be protected with one of the three supported hash functions (RIPEMD-160, SHA-512, or Whirlpool).
VeraCrypt offers the choice of some fifteen combinations of individual encryption algorithms and their cascaded combinations. Five different hash functions are supported, making it 15×5=75 possible combinations of symmetric ciphers and one-way hash functions to try. If you don’t know exactly which cipher and which hash function has been used to encrypt the container, you’ll have to try all of the 75 combinations during the attack.
VeraCrypt symmetric encryption algorithms
While Microsoft BitLocker and Apple FileVault 2 rely exclusively on AES encryption, it is common for third-party crypto containers to support more than one cipher. VeraCrypt in particular offers the choice of a number of symmetric encryption algorithms including AES, Serpent, Twofish, Camellia, and Kuznyechik. Additionally, ten different combinations of cascaded algorithms are available: AES–Twofish, AES–Twofish–Serpent, Camellia–Kuznyechik, Camellia–Serpent, Kuznyechik–AES, Kuznyechik–Serpent–Camellia, Kuznyechik–Twofish, Serpent–AES, Serpent–Twofish–AES, and Twofish–Serpent. Stacked encryption options are often considered the “safe side” of the matter.
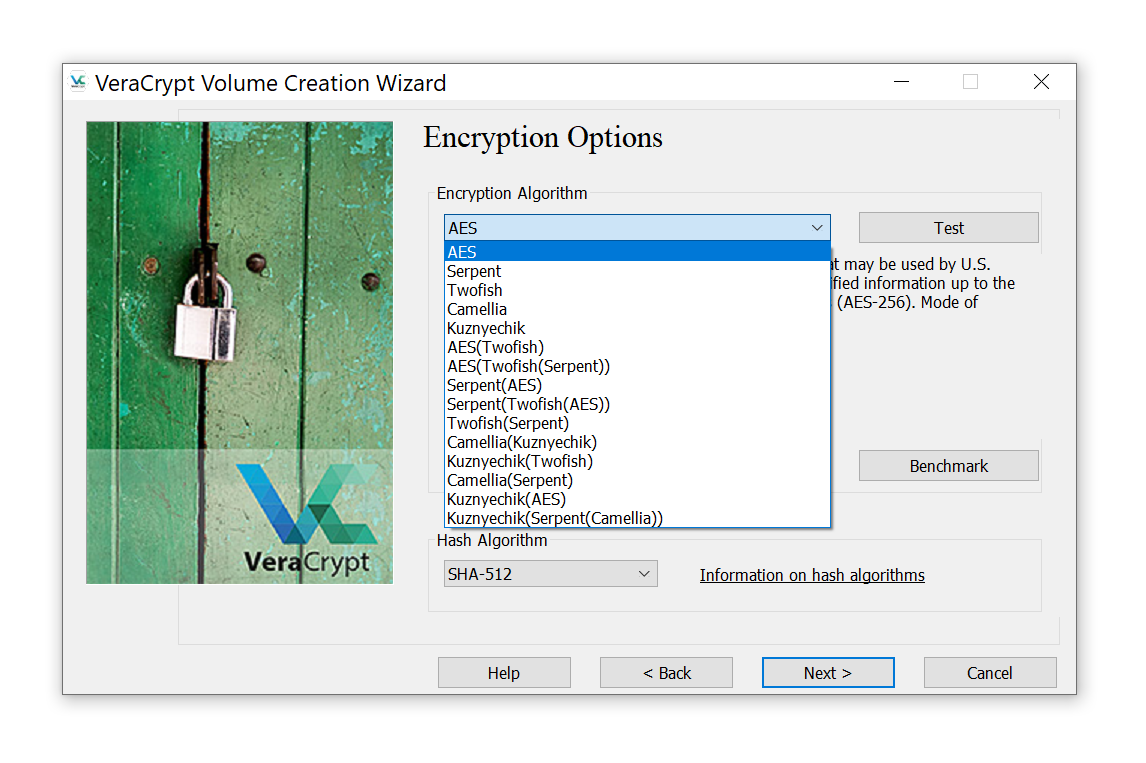
In reality, neither the alternative ciphers nor stacked encryption offer tangible benefits over AES-256 encryption other than “not being the default”. If a container is encrypted with a cipher different from the default AES encryption, you’ll have to guess the correct encryption algorithm in addition to finding the password. Elcomsoft Distributed Password Recovery allows specifying the encryption algorithm(s) when setting up an attack.
VeraCrypt hash functions
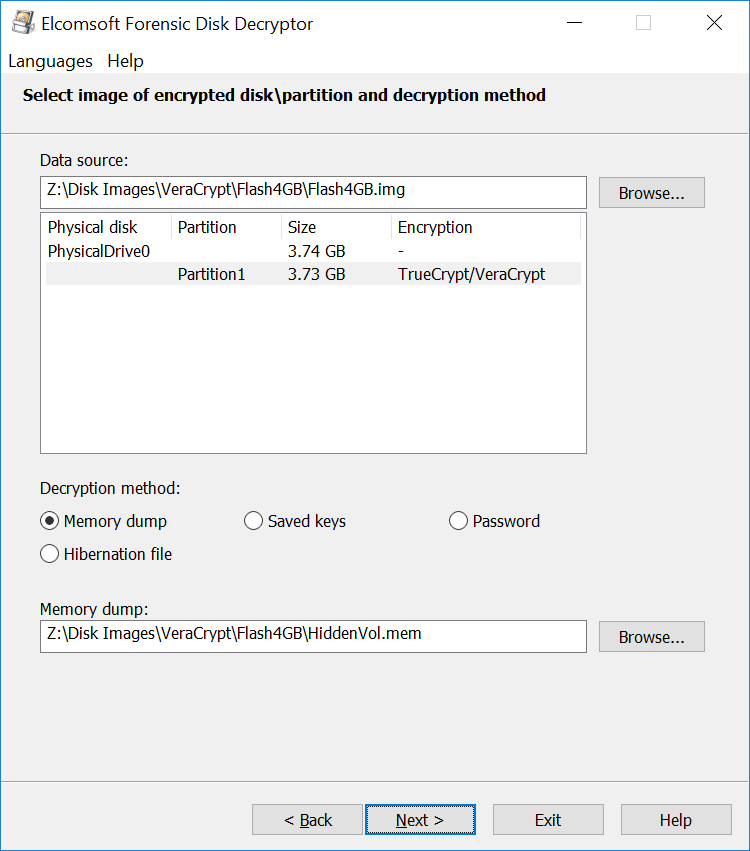
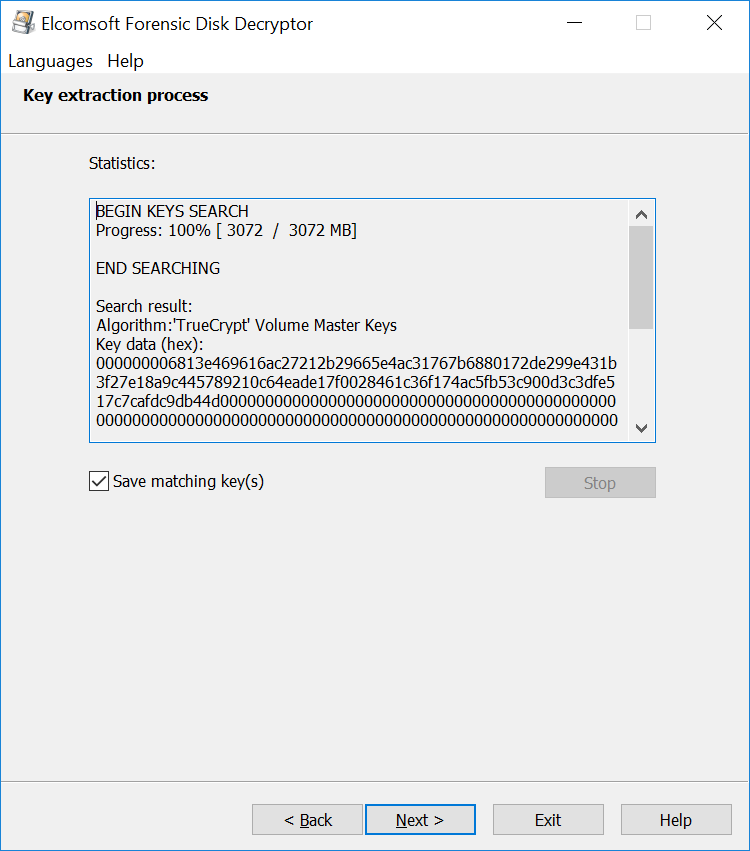
When VeraCrypt encrypts or decrypts the data, it is using a perfectly random, high-entropy encryption key to perform symmetric cryptographic operations. This key is called a Media Encryption Key (MEK) or Data Encryption Key (DEK). The MEK is exactly the key one may be able to extract from the computer’s RAM dumps, hibernation and page files. If you are able to extract the MEK, you can fast forward to decrypting the data without running attacks on the user’s password. More about extracting media encryption keys and instantly decrypting VeraCrypt containers in our blog:
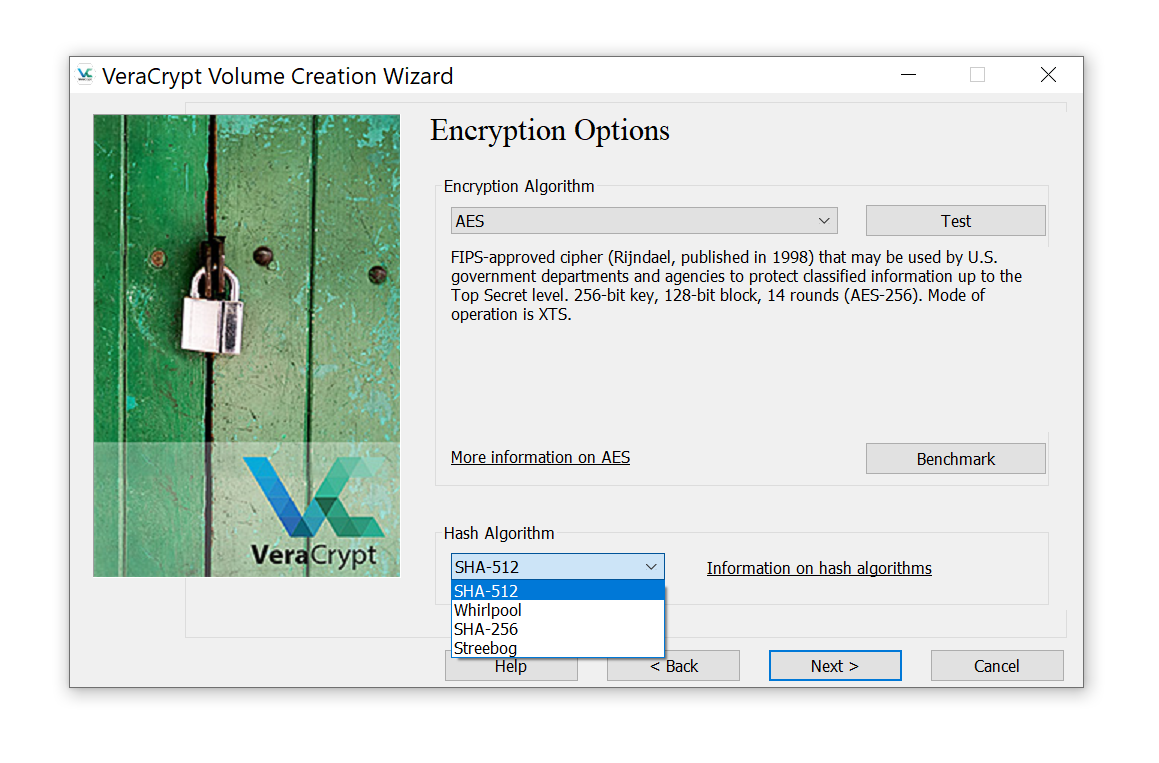
If the binary Media Encryption Key is not available, you’ll have to recover that key in order to decrypt the data. VeraCrypt stores the MEK alongside with the encrypted data. The Media Encryption Key is encrypted with a Key Encryption Key (KEK), which, in turn, is the result of multiple (hundreds of thousands) iterative one-way hashing operations performed on the user’s password. By default, VeraCrypt uses 500,000 rounds of hashing to ‘wrap’ the KEK. VeraCrypt supports four hash functions including SHA-512, Whirlpool, SHA-256 and Streebog.
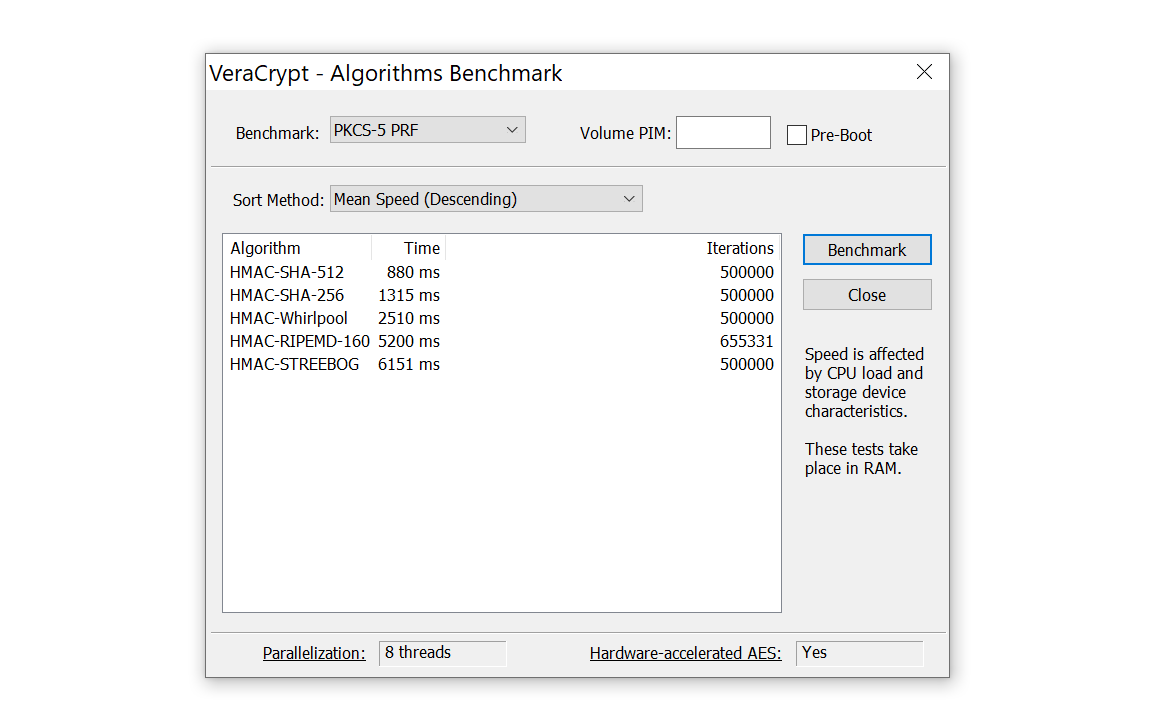
In other words, when the user types their password, VeraCrypt performs 500,000 rounds of hashing with one of the four supported hash functions to calculate the KEK. The number of rounds is set to a deliberately high value in order to slow down brute-force attacks. A single Intel i7-9700K CPU delivers the following performance:
When running an attack on the user’s password, calculating the correct Key Encryption Key would not be possible without knowing which hash function exactly was used to produce the key. VeraCrypt offers the choice of SHA-512 (default), Whirlpool, SHA-256 and Streebog hash functions.
Using Elcomsoft Distributed Password Recovery to break VeraCrypt passwords
While VeraCrypt does protect its encrypted containers against brute-forcing the password, we have significant advances in password recovery attacks compared to what we had some ten years back. Brute-forcing a password today becomes significantly faster due to the use of GPU acceleration, distributed and cloud computing. Up to 10,000 computers and on-demand cloud instances can be used to attack a single password with Elcomsoft Distributed Password Recovery.
Brute force attacks became not just faster, but much smarter as well. The user’s existing passwords are an excellent starting point. These passwords can be pulled from the user’s Google Account, macOS, iOS or iCloud keychain, Microsoft Account, or simply extracted from the user’s computer. The user’s existing passwords give a hint at what character groups are likely used:
Elcomsoft Distributed Password Recovery offers a number of options to automatically try the most common variations of your password (such as the Password1, password1967 or pa$$w0rd):
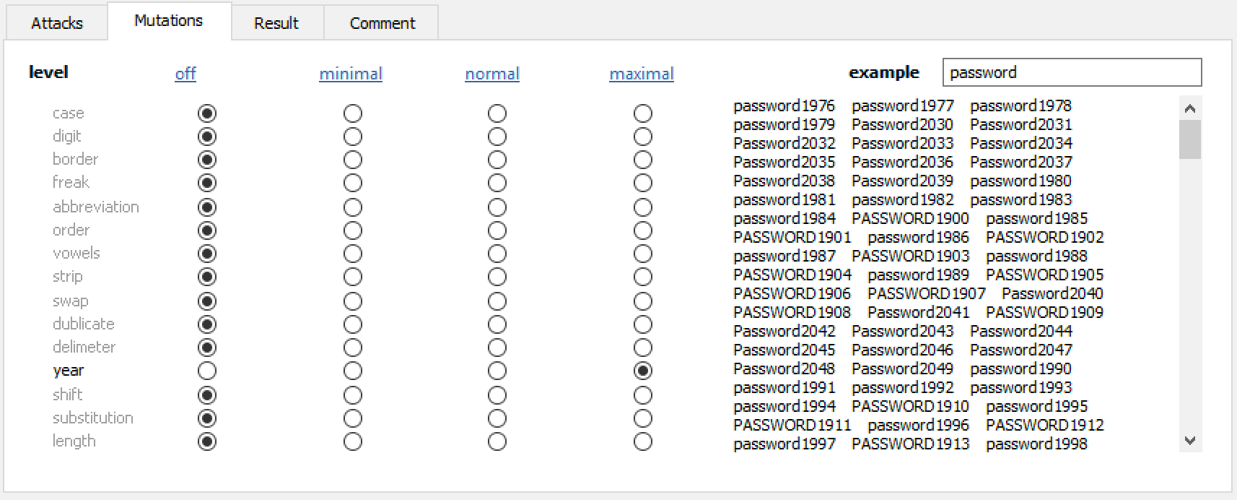
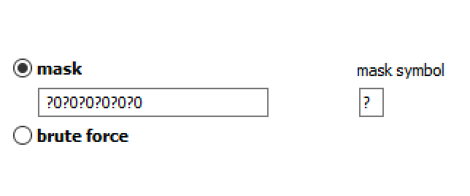
Masks can be used to try passwords matching established common patterns:
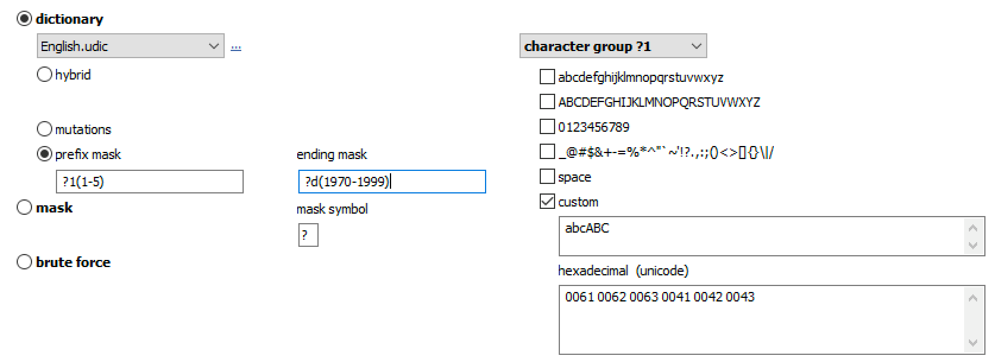
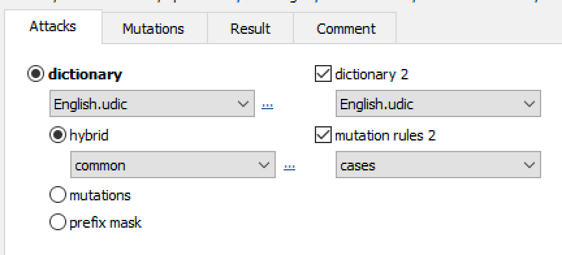
Advanced techniques allow composing passwords with up to two dictionaries and scriptable rules:
If a non-standard hash function was selected, the attack will be slowed down significantly even with GPU acceleration. A single video card (e.g. NVIDIA GTX 1080) can process about 170 passwords per second with VeraCrypt default settings (AES encryption, SHA-512):
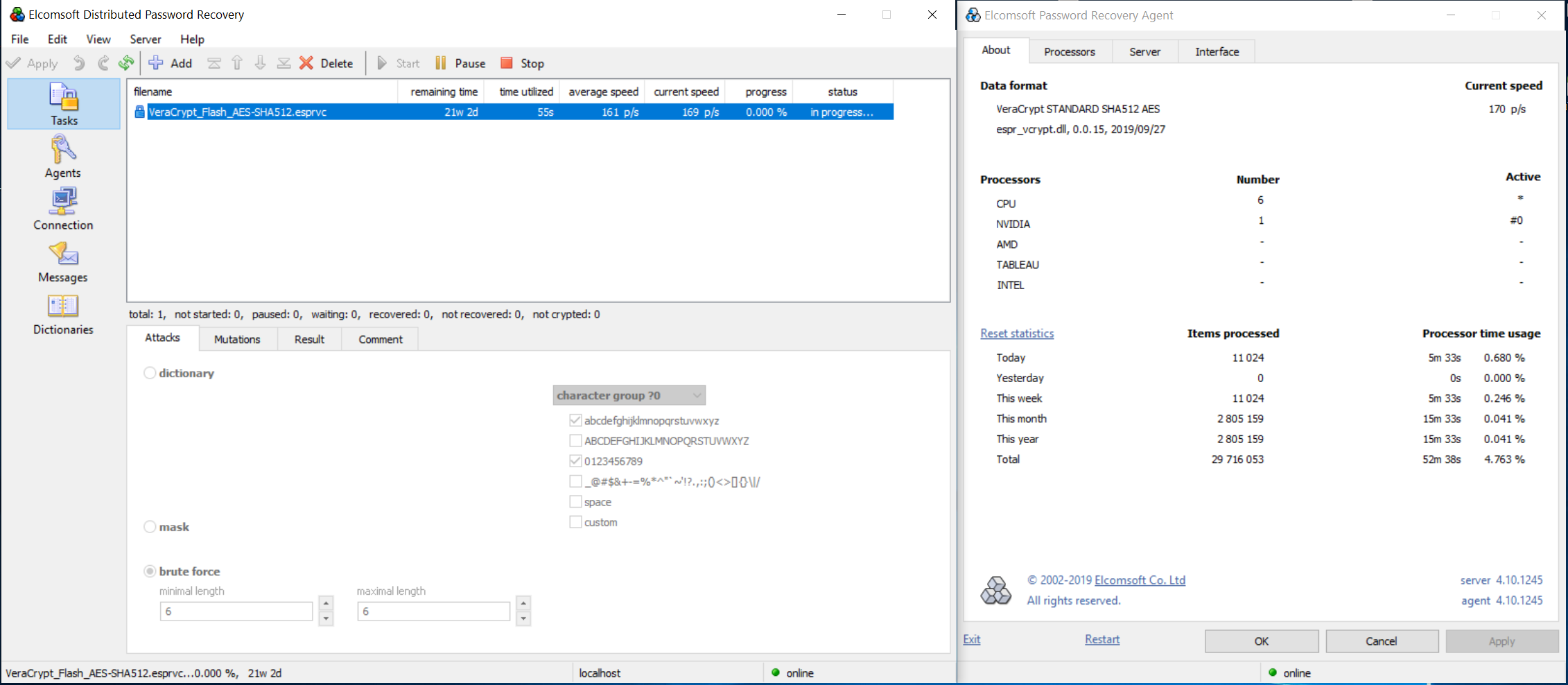
However, a non-standard combination of symmetric cipher and hash function (e.g. AES + Whirlpool, or Serpent + SHA-256) requires trying all possible combination of ciphers and hash functions. This will be significantly slower; about one password per second on the same computer equipped with a single video card:
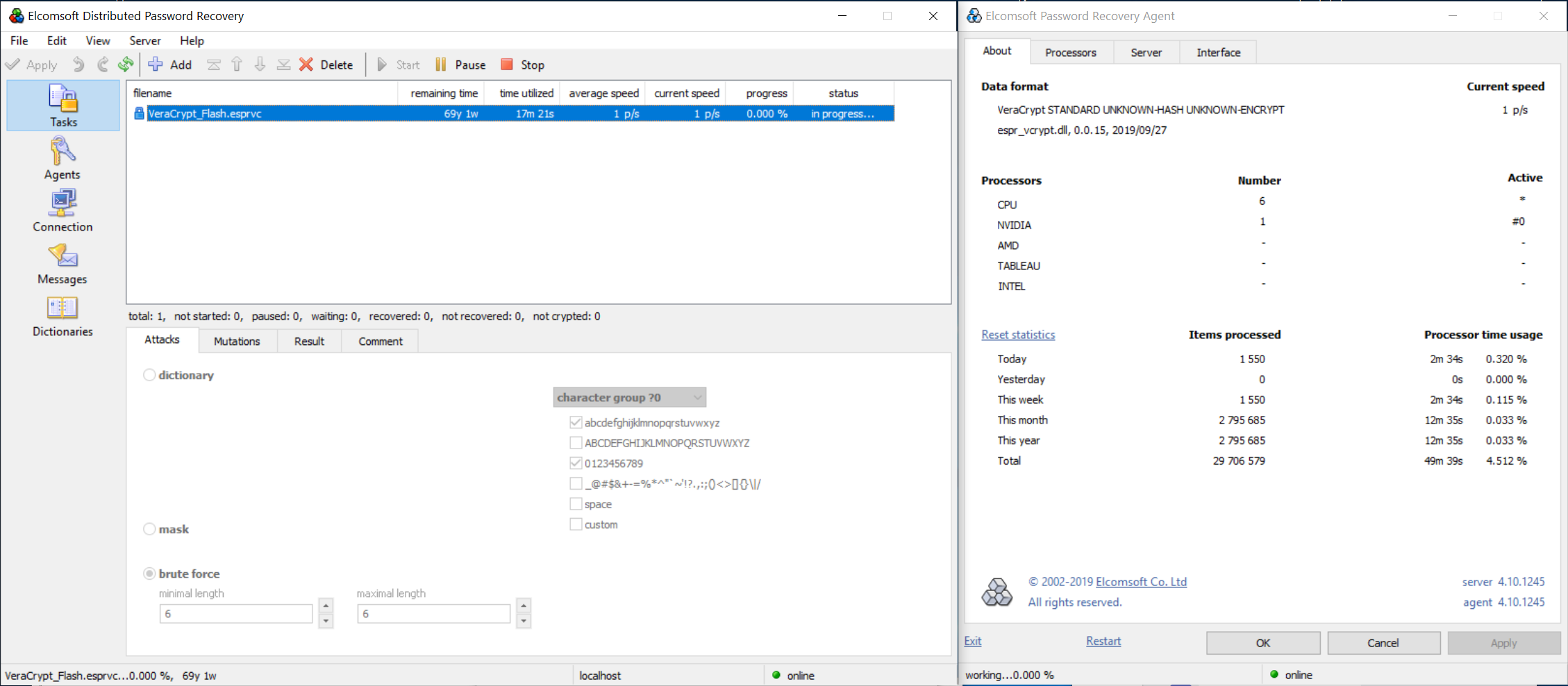
How fast, exactly?
VeraCrypt is well-prepared to withstand brute-force attacks. By default, some 500,000 rounds of user-selected hash function are performed to calculate the KEK (Key Encryption Key). Some hash functions are faster than others, and some are extremely slow. The choice of the hash function greatly affects the speed of the attack. However, there is one thing that affects the speed even more than the choice of a hash function: it’s whether you know exactly which combination of encryption and hashing was used.
Remember, VeraCrypt offers the choice of 15 encryption methods (single encryption algorithms and cascaded encryption) and 4 hash functions. If you don’t know exactly which combination of hash+encryption was used to protect the encrypted container, you will have several strategies:
- Try the default AES+SHA-512 attack
- Try guessing the right combination (it rarely works), or
- Try all possible combinations (slow but comprehensive)
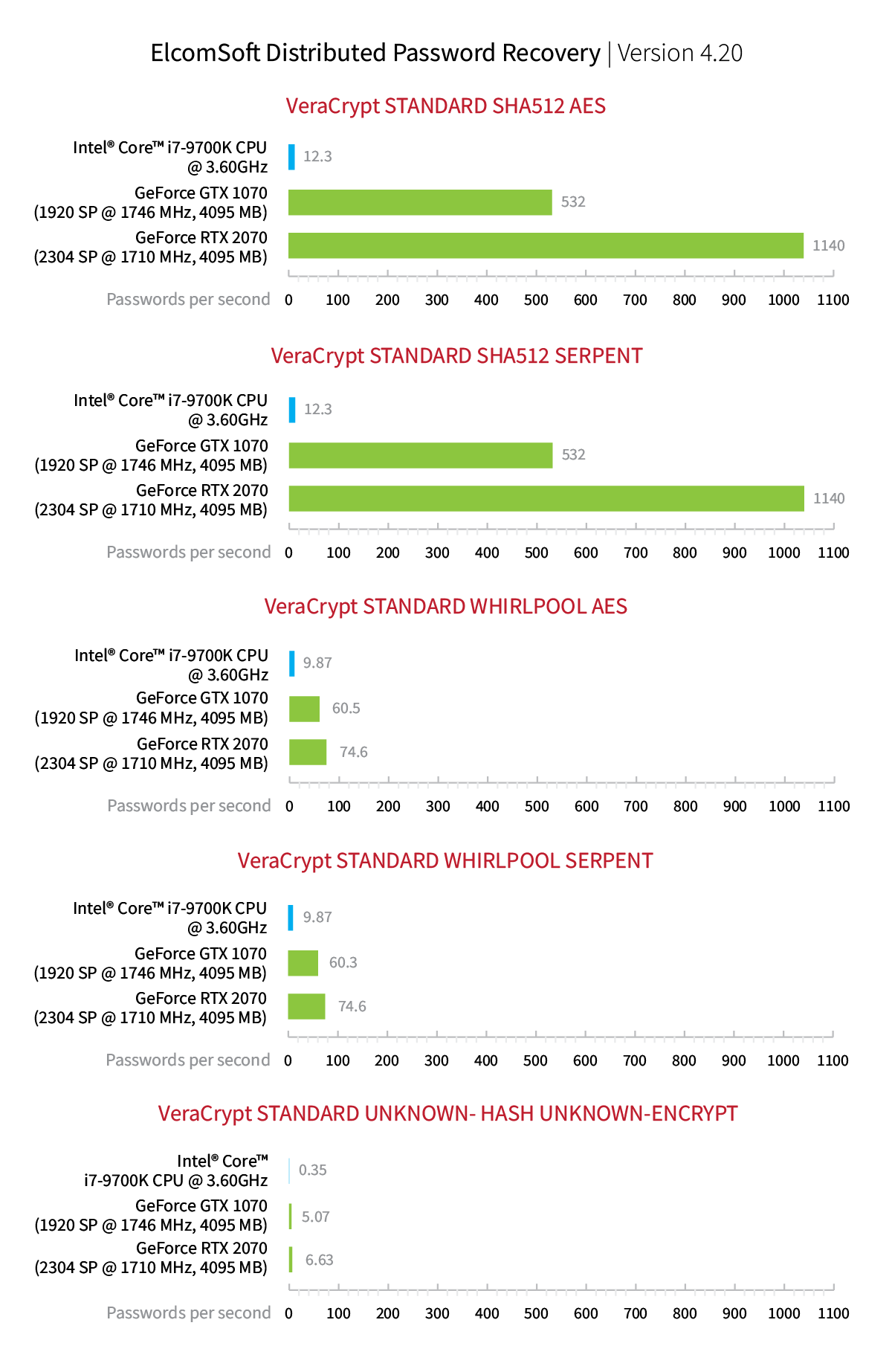
With the majority of users taking the default route, it may be worth it to first try an attack with the default settings (AES encryption, SHA-512 hash). If that attack fails, it would make sense trying all possible combinations of encryption and hashing. Note, however, that trying all possible combinations is about 175 times slower compared to attacking a single combination of AES+SHA-512.
One thing that does not affect the speed of the attack is the user’s choice of encryption. Whether they choose to encrypt with AES, Serpent, Twofish or any other single algorithm, the speed of the attack will remain the same. Attacks on cascaded encryption with two algorithms (e.g. AES(Twofish)) work at half the speed, while cascading three algorithms slows them down to around 1/3 the speed.
Alternative attacks
Combining the use of multiple computers and cloud instances equipped with multiple GPU units may increase the recovery speeds significantly. Yet, even these higher speeds may not be enough when attacking containers protected with long, complex and non-reusable passwords. In such cases, alternative attacks may deliver better results.
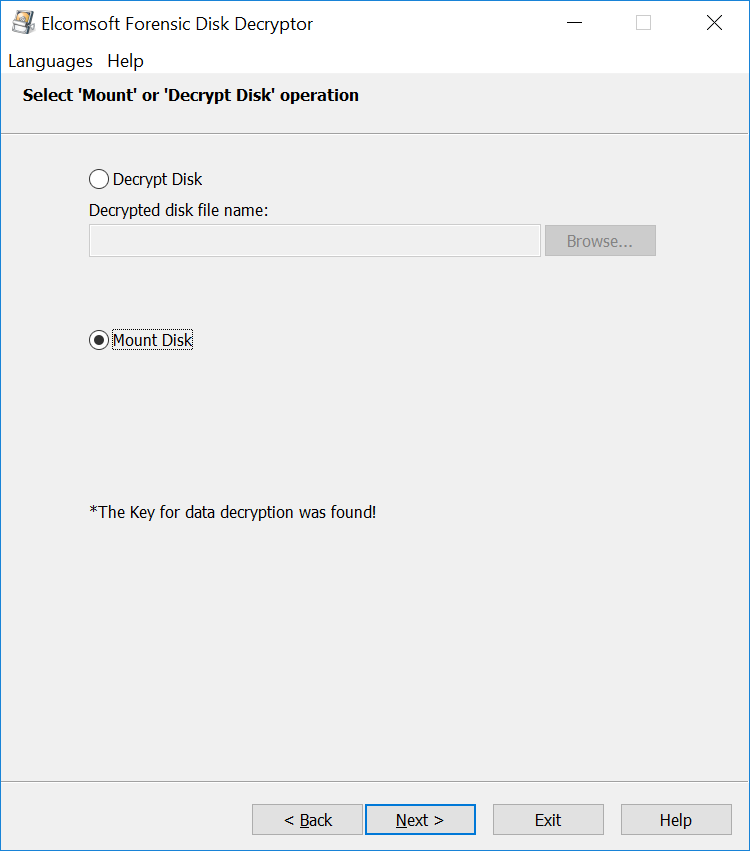
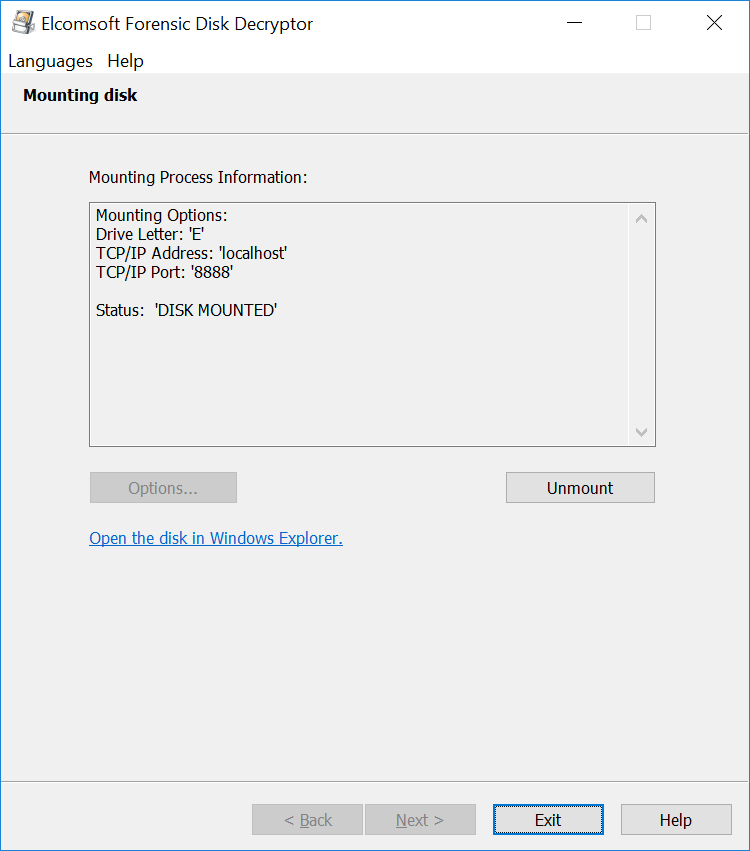
The most commonly used alternative targets the on-the-fly encryption key (OTFE), or Media Encryption Key. This is the binary, symmetrical key VeraCrypt uses to encrypt and decrypt data it writes to or reads from the encrypted volume. Gaining access to the OTFE key allows decrypting the data directly without knowing or needing the password.
There is more than one way to access OTFE keys. While the encrypted volume is mounted, the encryption key is available in all of the following locations:
- The computer’s volatile memory (RAM). VeraCrypt needs the OTFE key in order to read and write data stored in the encrypted volume, so the encryption key is always stored in the RAM.
- Page file(s). While the OTFE key may or may not land in the page file, scanning the page file(s) takes minutes or several hours of time (compared to days and weeks of brute-forcing the password).
- Hibernation file. Windows uses a hibernation file to dump parts of the computer’s RAM onto the hard disk when the computer sleeps (if Hybrid sleep is enabled, which it is by default); when the computer hibernates (which is disabled by default); and when the computer shuts down (when Fast startup is enabled, which is enabled by default). The hibernation file can be only scanned if the boot volume is not encrypted or can be unlocked.
This is how the extraction works with Elcomsoft Forensic Disk Decryptor:
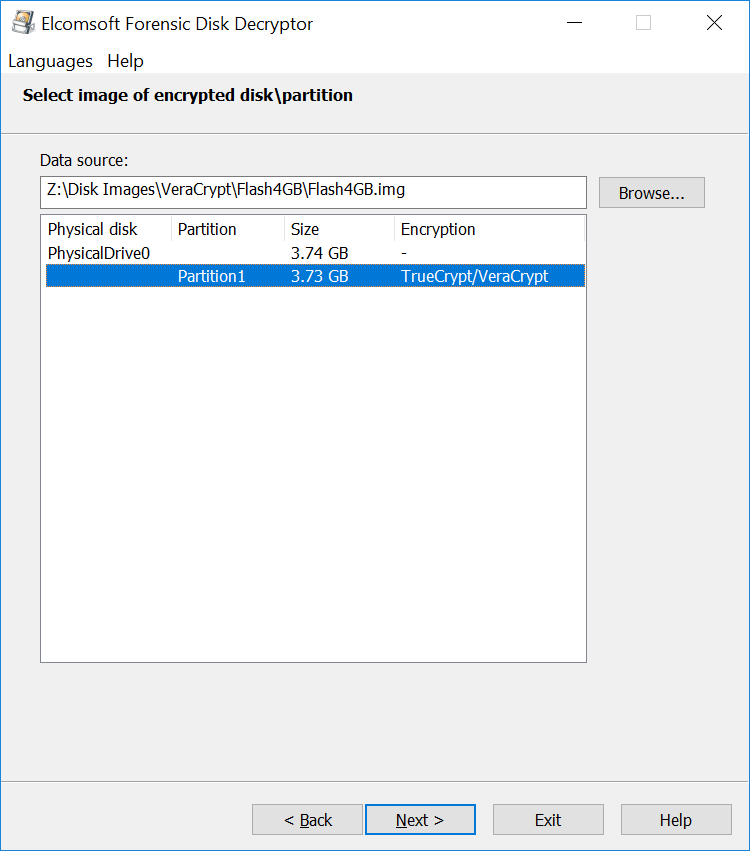
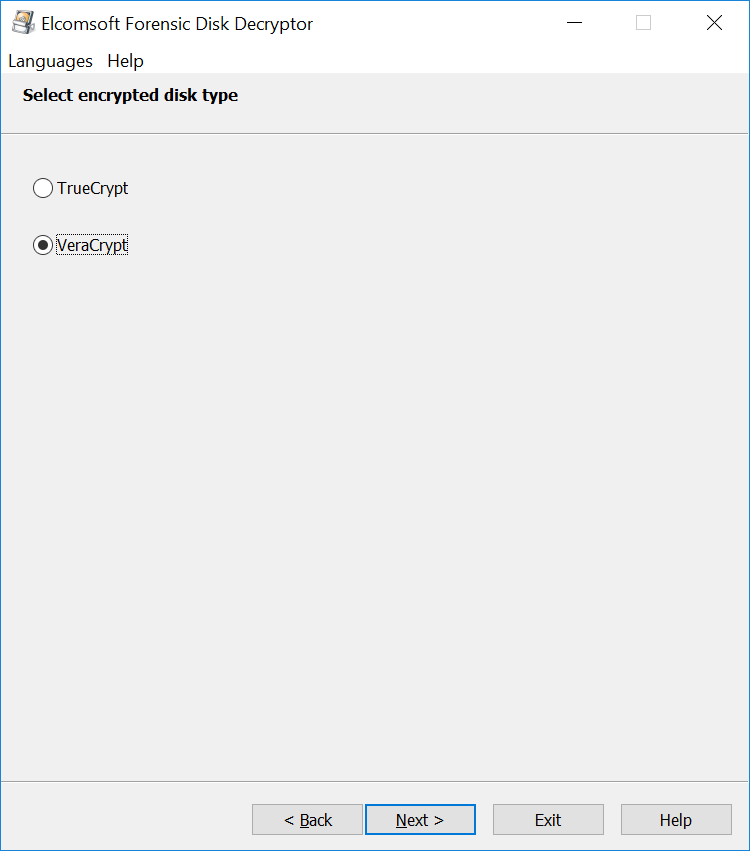
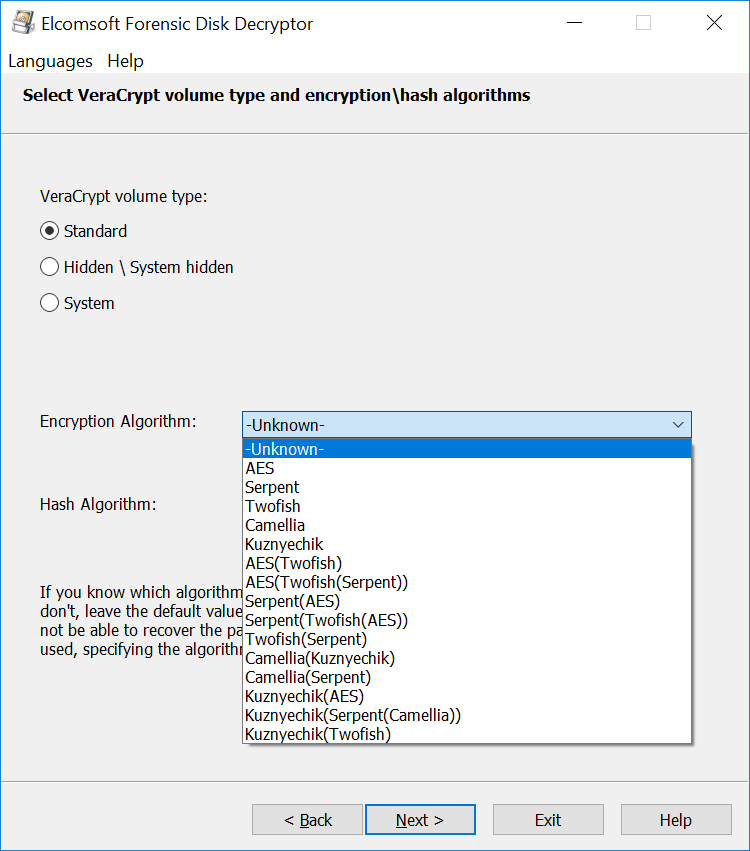
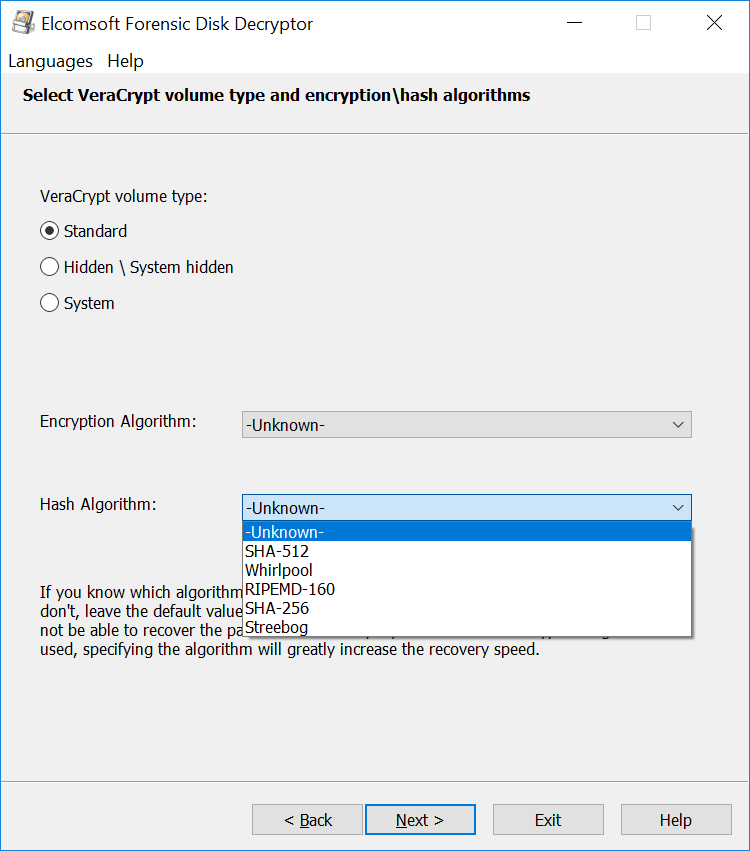
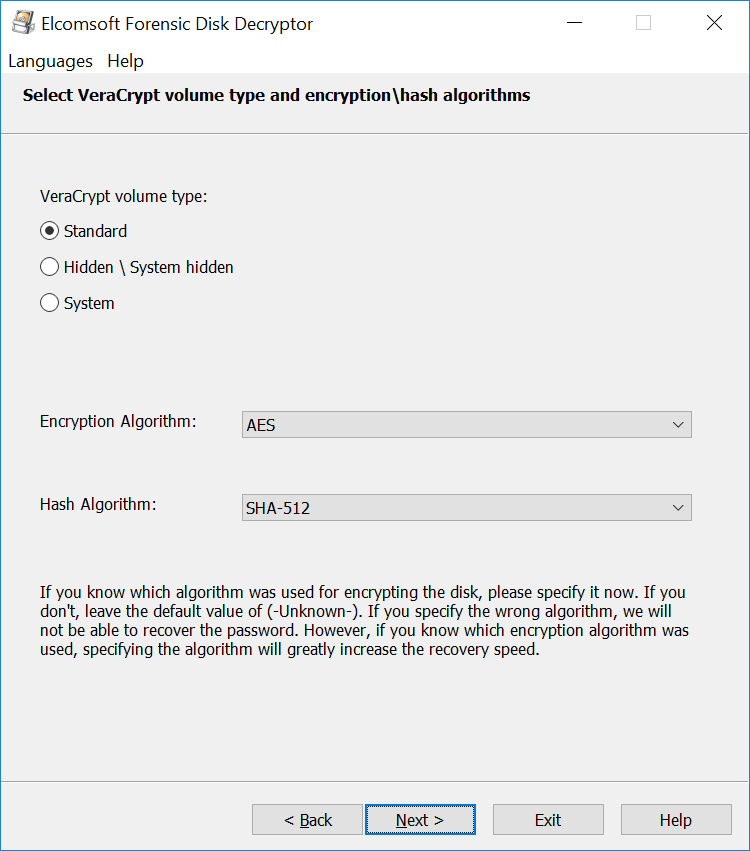
The time required to locate the OTFE keys depends largely on the amount of RAM installed in the user’s computer, and the speed of the expert’s PC. It also depends on the encryption settings. Selecting a non-standard combination of an encryption algorithm and hash function (e.g. AES+SHA-256 or AES+Whirlpool) will require trying all possible combinations instead of using the single default setting (AES+SHA-512), which takes extra time. In our experience, scanning a 16 GB memory dump can take 15 to 30 minutes with default settings and up to several hours with a non-standard combination of encryption and hash.