It’s been a long while since we made an update to one of our most technically advanced tools, Elcomsoft Forensic Disk Decryptor (EFDD). With this tool, one could extract data from an encrypted disk volume (FileVault 2, PGP, BitLocker or TrueCrypt) by utilizing the binary encryption key contained in the computer’s RAM. We could find and extract that key by analyzing the memory dump or hibernation files.
What Elcomsoft Forensic Disk Decryptor did not do until now was pretty much everything else. It couldn’t use plain text passwords to mount or decrypt encrypted volumes, and it didn’t support escrow (recovery) keys. It didn’t come with a memory imaging tool of its own, making its users rely on third-party solutions.
With today’s release, Elcomsoft Forensic Disk Decryptor gets back on its feets, including everything that was missing in earlier versions. Plain text passwords and recovery keys, a Microsoft-signed kernel-level RAM imaging tool, the highly anticipated portable version and support for the industry-standard EnCase .E01 and encrypted DMG images are now available. But that’s not everything! We completely revamped the way you use the tool by automatically identifying all available encrypted volumes, and providing detailed information about the encryption method used for each volume.
The First Step
You begin with launching Elcomsoft Forensic Disk Decryptor 2.0 and opening a physical disk or disk image (did I mention we now support EnCase .E01 and encrypted DMG volumes?)
Once you open the disk (or disk image), EFDD scans the disk (or image) and identifies all encrypted volumes available on that disk. These volumes along with their corresponding encryption settings are then displayed in the main window.
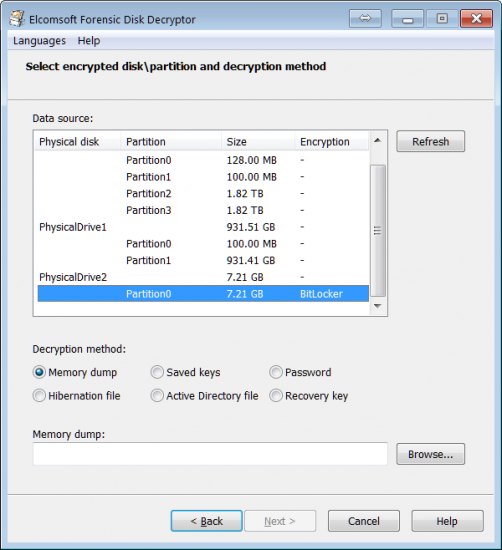
Ways to Decrypt
In previous versions, the toolkit was limited to mounting or decrypting volumes with binary cryptographic keys extracted from the computer’s memory image or hibernation file. The ability to use plain-text passwords or escrow keys for accessing data stored in the encrypted containers was sorely missing.
That has changed in EFDD 2.0. In this release, we’re added new ways to mount or decrypt encrypted volumes. You can still use the binary cryptographic key, but if you know the original container’s password, you can just type in that password to either mount the volume or perform its full decryption for offline analysis.
Yet another way to access encrypted data is by using an escrow key, or recovery key, as they are sometimes called. Escrow keys offer a backup of a sort, providing a way for the rightful owner to decrypt data if they lose or forget their password.
For BitLocker volumes, the Recovery Key can be pulled from Active Directory or, for personal accounts, from the user’s Microsoft Account via this link: https://account.microsoft.com/devices/recoverykey
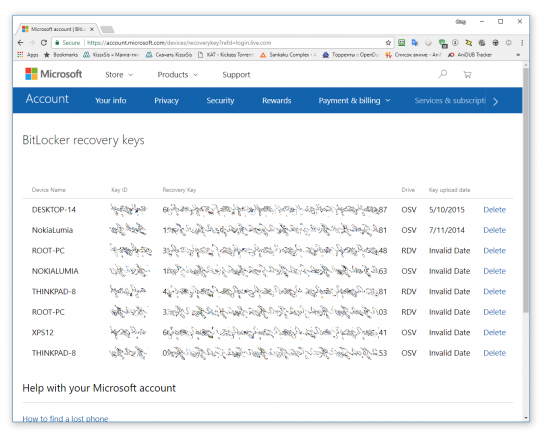
If you’re into breaking BitLocker volumes, we have a comprehensive write-up here and here. You can also learn what has changed in BitLocker in Windows 10 November Update.
For FileVault 2, you can extract the recovery key from Apple iCloud (you’ll need Elcomsoft Phone Breakerto do that).
New Kernel-Level RAM Imaging Tool
The original release of EFDD was made to scan the computer’s volatile memory image. In that image, the tool looks for cryptographic keys that are used for accessing data stored in encrypted containers. If it could find a cryptographic key, EFDD then decrypted the container with no lengthy attacks on the original plain-text password. It all sounds great, but where do you get the RAM image?
Before this release, Elcomsoft Forensic Disk Decryptor was relying on memory images captured by third-party tools. Our customers always came back to us, asking if we’re going to develop an imaging tool of our own. And so we did.
Elcomsoft Forensic Disk Decryptor 2.0 comes with a proper forensic-grade memory imaging tool that uses zero-level access to computer’s RAM in order to create the most complete memory image. Our RAM imaging tool includes a kernel mode driver that carries a Microsoft digital signature, making it fully compatible with existing 32-bit and 64-bit versions of Windows from Windows 7 and up to the latest Windows 10 Fall Creators Update.
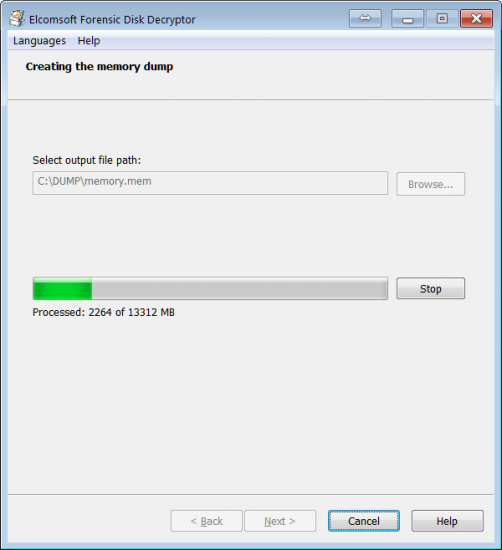
Why does a memory imaging tool need a kernel-level driver? The driver is required to access all areas of the computer’s memory including those that are actively protected with system or third-party anti-dumping and anti-debugging tools. Many memory acquisition tools run in the user mode, and are denied access to certain protected areas in the computer’s RAM. Unlike those tools, ElcomSoft’s solution comes with a kernel-level driver that works in the systems’ most privileged “zero” circle, having full and unrestricted access to all areas of the computer’s memory.
The driver is digitally signed by Microsoft. The Microsoft digital signature allows the tool to be installed (or launched) on computers running all versions of Microsoft Windows up to the latest version that enforce driver signing.
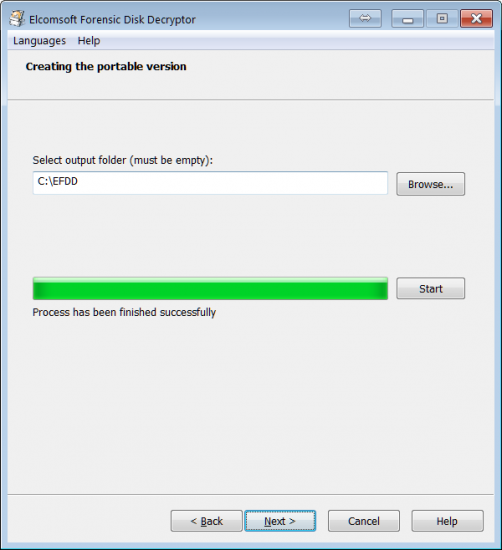
The Portable Version
Elcomsoft Forensic Disk Decryptor 2.0 now fully supports EnCase images in the industry-standard .EO1 format, as well as encrypted DMG images. However, the tool can be launched on live systems from a portable USB drive. In order to create a portable version, you’ll need to install Elcomsoft Forensic Disk Decryptor to your computer first, and register it with your license key. You will then be able to create a portable installation on a portable media (BYOFD, or Bring Your Own Flash Drive).
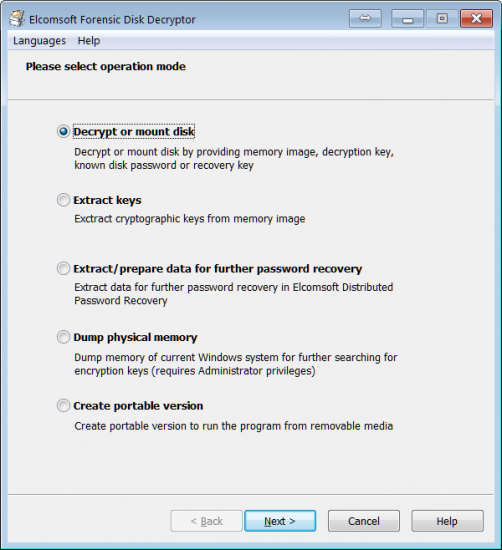
You can then use the newly created portable installation to capture other computers’ volatile memory and/or mount or decrypt encrypted volumes.
New Introductory Price and Updates
Did you buy a license for one of the previous versions of the tool during the past year? You might be eligible for a free update! For new customers, we have a special introductory price offer running through the end of February. Until February 28, 2018, you’ll be able to get 30% off the $599 price. Follow this link to place an order: https://www.elcomsoft.com/purchase/







