Geolocation data can provide a wealth of evidence to various government agencies. Law enforcement agencies use location data to help place suspects near a crime scene in a given time frame. However, the use of location is not limited to criminal or civil investigations. Emergency response services use geolocation to locate persons, taxi and delivery services use location to improve service. There are many more examples where location evidence is vital. Recently, governments have started using (or are considering using) geolocation data to help identify and isolate infected citizens. Where does the location evidence come from and how one can extract it?
Sources of Geolocation Evidence
Location data can come from a variety of sources. These sources can be broken into the following parts:
- The mobile device itself. The data is stored on and extracted from the physical device.
- The cloud. The location evidence is uploaded to or synchronized with one or more cloud services (e.g. Google Account for Android smartphones).
- Third-party cloud services. Many mobile apps such as fitness and training apps, some games and online storage services (e.g. OneDrive, Dropbox) may store geolocation data either as location points or in the pictures metadata.
- Call Detail Record (CDR). The data is collected by, stored and disclosed to relevant authorities by mobile service providers regardless of the type of the user’s mobile device (smartphone, feature phone or embedded, e.g. LTE smartwatch).
Extracting the location data from the mobile device is tempting, especially considering the number of exploits and acquisition methods available even for the latest iPhone models and versions of iOS. However, analyzing an Android smartphone for location data may be counterproductive as Google stores a much longer and more comprehensive version of the data in the cloud, tied to the user’s Google Account.
Interestingly, location evidence is not limited to simple location points. Locations can be extracted from a variety of sources on the smartphone and in the cloud. Pictures and messages with image attachments contain EXIF data, which in turn stores the location where the image has been snapped.
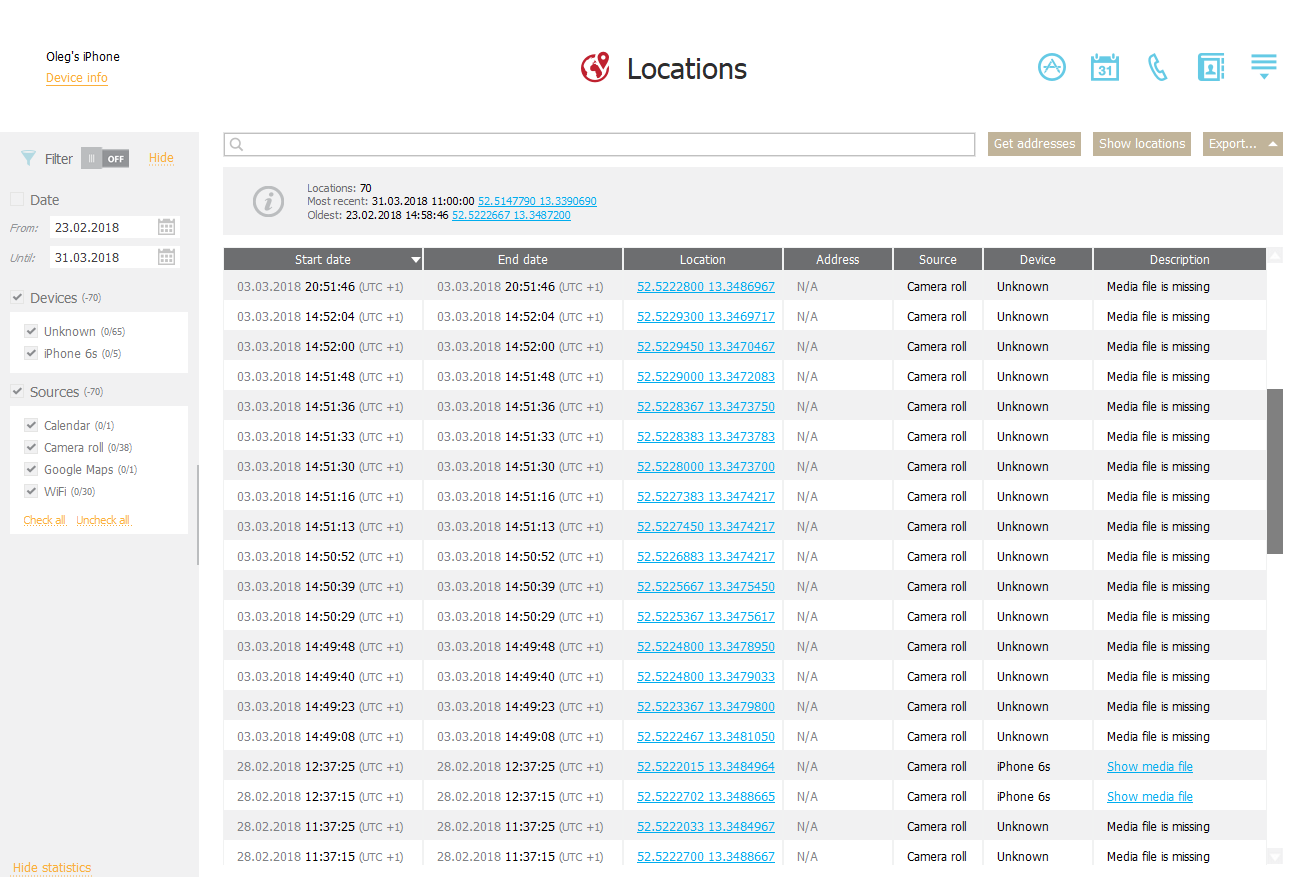
Installed applications with location access (e.g. health apps and sports trackers) may contain locations (which, in turn, may be synced to the respective cloud services).
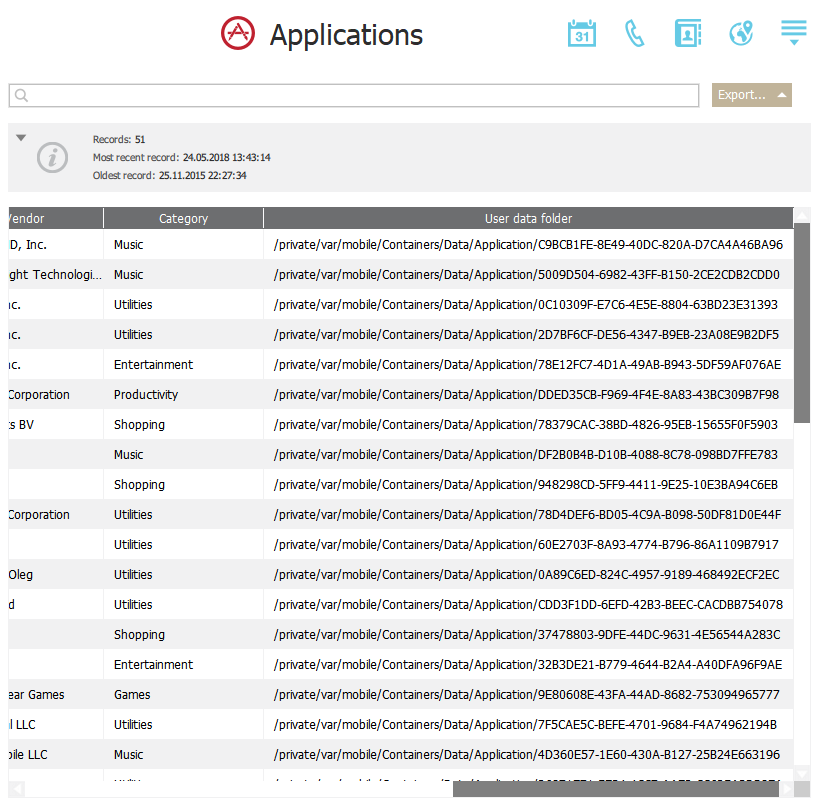
A lot of location points might be available in health apps such as Google Fit or Strava. Even calendar events may contain location data! All of these (and several more) sources represent what we call the “aggregated location evidence”. Starting with Elcomsoft Phone Viewer 3.70 released way back in 2018, we support aggregated locations.
Speaking of locations, EPV 3.70 can extract location data from a wide range of sources. For iOS devices, the supported sources of location data include:
- Significant locations (what are those?)
- Locations cache (3G/LTE/Wi-Fi connections)
- Apple Maps
- Google Maps
- EXIF in media files, including the ID of the device that was used to capture the image
- Calendar events, including the link to the event
- The UBER app
Many of these sources are exclusive to the file system acquisition of a physical device. However, some data is available via cloud acquisition as well. Let us see what one can expect to obtain from the three cloud providers: Apple (iCloud), Google, and Microsoft.
Apple
Unlike Google, Apple does not maintain the history of its user’s location. Correspondingly, the hopes of obtaining years worth of location history from iCloud are unfounded. However, there are several sources that may still deliver some location data. These include:
Health > Workouts
In Apple ecosystem, this is the only type of cloud data containing multiple precise timestamped location points. The data comes from the user’s Apple Watch. Once the Apple Watch detects the beginning of a workout, the device starts logging workout data such as heart rate and location. The location points come from the GPS sensor built into all recent Apple Watch models.
The Workouts data belongs to the Health category, which in turn is using end-to-end encryption. In order to access end-to-end encrypted data with Elcomsoft Phone Breaker, you will need the user’s Apple ID and password, one-time two-factor authentication code, and the user’s screen lock password or system password to one of the devices registered on that Apple ID account.
You can analyze the data with Elcomsoft Phone Viewer.
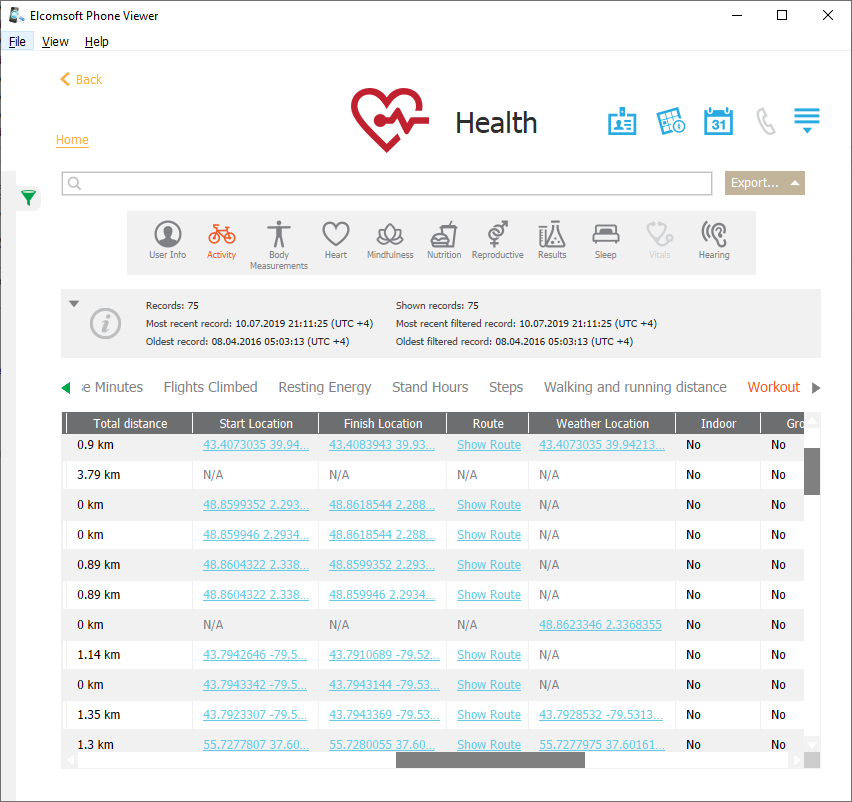
Find My data
Find My can reliably pinpoint the location of the user’s Apple devices. It is essential that using the Find My service does not require access to the second authentication factor even if two-factor authentication is enabled for the user’s Apple account.
iCloud Backups
Some location data can be extracted from iCloud backups made by iPhone devices. The largest number of location points is usually obtained from the photos available in iCloud backups. However, if the user enables iCloud Photos, the photos will be synchronized to iCloud and excluded from iCloud backups.
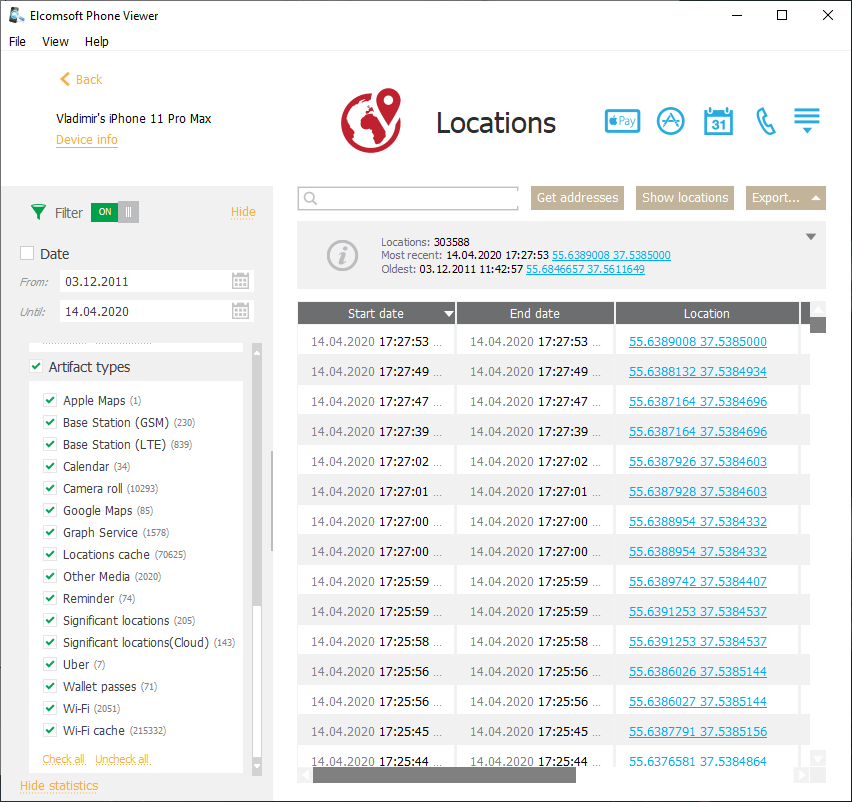
iCloud Photos
If the user enables iCloud photo library, the pictures taken on any of the user’s devices will be synchronized with the cloud. By downloading the pictures with Elcomsoft Phone Breaker and extracting GPS tags from EXIF metadata (or simply using Elcomsoft Phone Viewer > Aggregated Locations) helps build a rather detailed timeline of the user’s location history.
iCloud Messages
General iMessages per se do not carry geotags, the picture attachments may include EXIF tagged with location. In addition, there is a special kind of iMessages called “Location”. Naturally, these messages contain precise location geotags.
Apple Maps
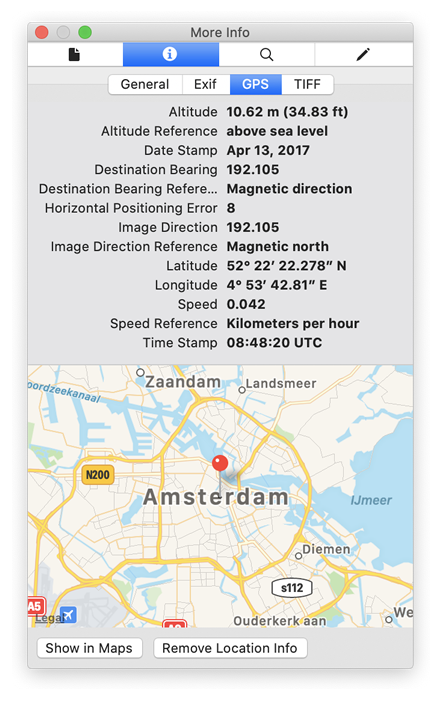
Surprisingly, the Apple Maps app contain a limited amount of location data. As little as it does, Apple protects Apple Maps data with end-to-end encryption (iOS 13). This level of protection is similar to other protected categories such as iCloud Keychain, iCloud Messages, Health and Screen Time. While we can still obtain that data from the cloud, the procedure relies on the process for extracting other end-to-end encrypted data, which means you have to use the password/passcode of one of the user’s devices.
You can view location data with Elcomsoft Phone Viewer.
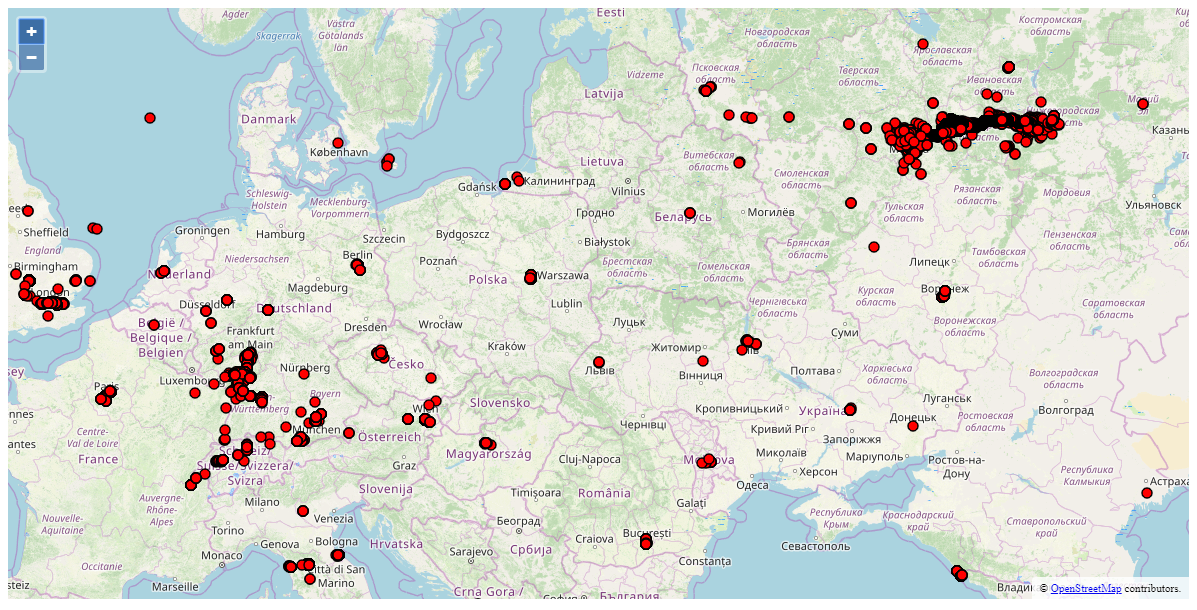
Google
Google stores many years worth of location data in the users’ Google accounts. Location data can be obtained from the following sources:
Google location history, routes and places (more on that later). This is a major source of geolocation data.
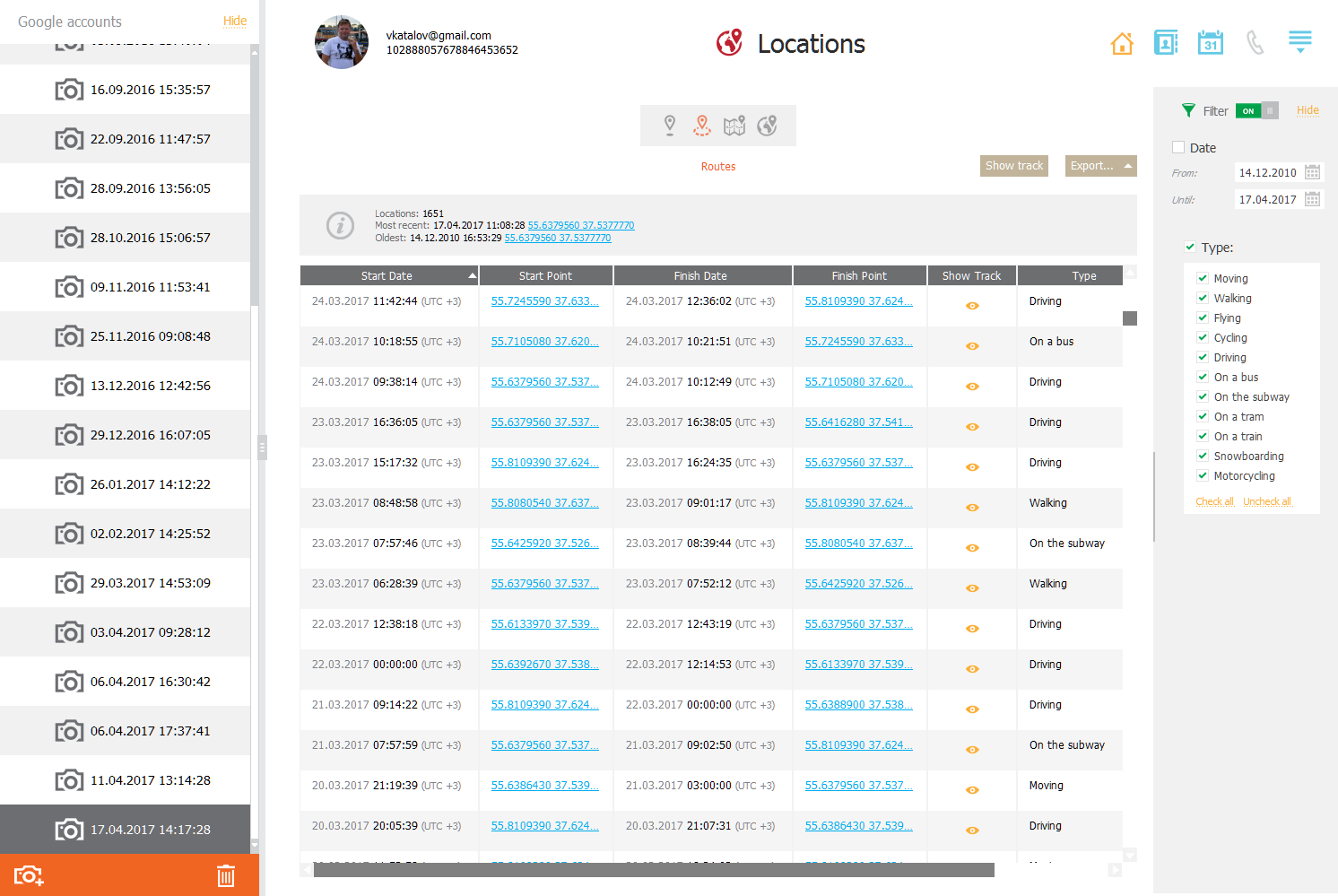
What’s “routes and places”, and how does that relate to “location history”?
Location history is simply raw geolocation data Google collects from various sources (e.g. GPS sensor, mobile networks, Wi-Fi BSSID and so on). Effectively, Google location history contains timestamped geolocation coordinates providing no information about the places’ street addresses or business names. To find out which place the user has actually visited, you have to manually pin those coordinates to a map and analyze the data.
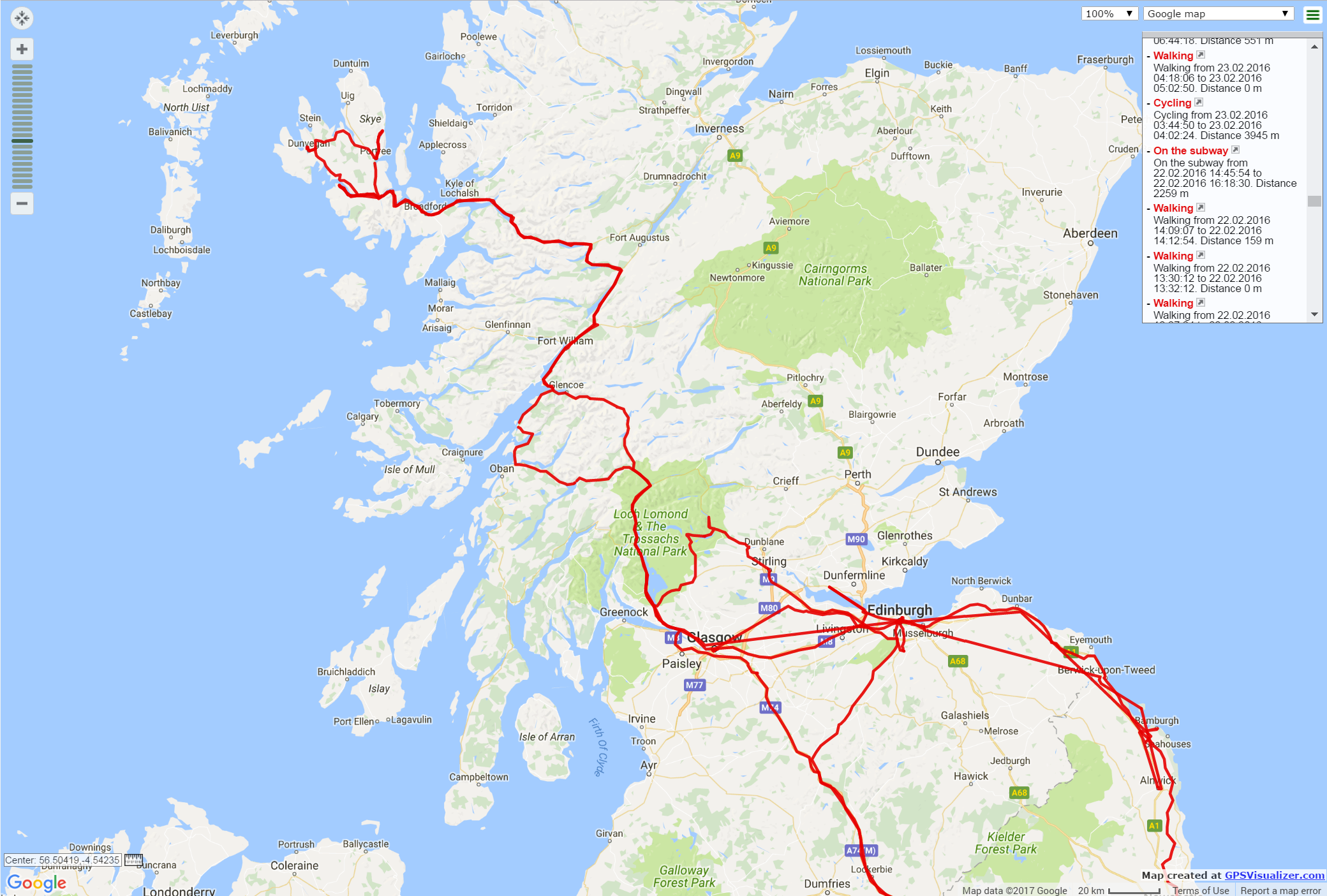
Routes and places is Google’s take on that analysis. Google uses artificial intelligence based on crowdsourced data to match geolocation data to points of interest (POI) on the map. As a result, Google can make an educated guess on which POI the user visited, how much time they spent and what type of activity they engaged into.
As a result, routes and places allow experts analyzing the users’ activities during their daily routine the way Google sees them, complete with the type of transport, stopovers and POI visited. Places and routes and places significantly improve readability of location data, providing experts a concise list of places instead of numerical geolocation coordinates.
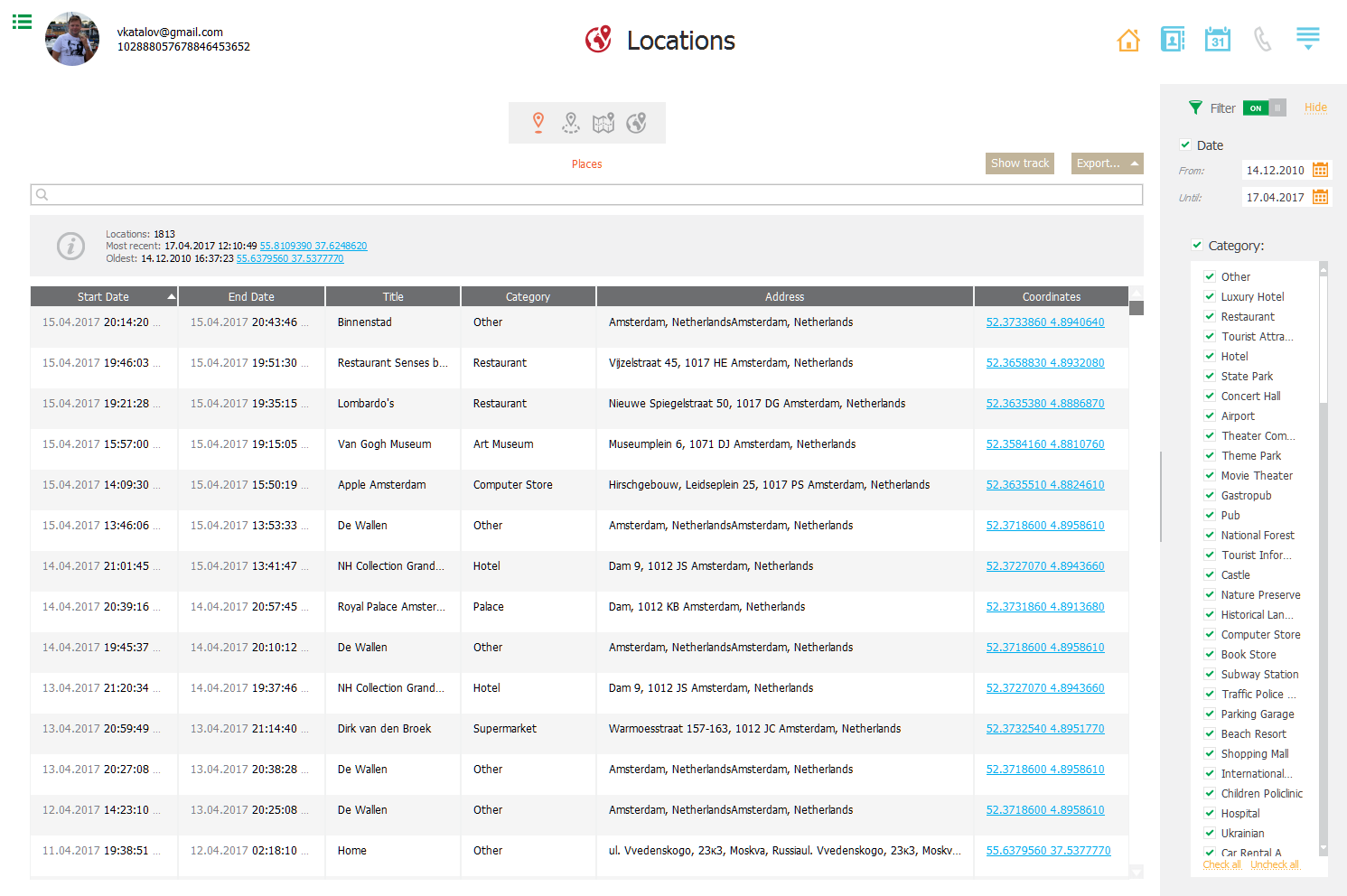
Extracting, viewing and analyzing Google location history, Google Fit data, routes and places is easily possible with Elcomsoft Cloud Explorer.
Google Fit
Unlike Apple Health, Google Fit estimates physical activity data based on the periodic polling of the built-in step counter and location tracking. Location points are then stored in the user’s Google Account under the Google Fit category (separate from the main location history).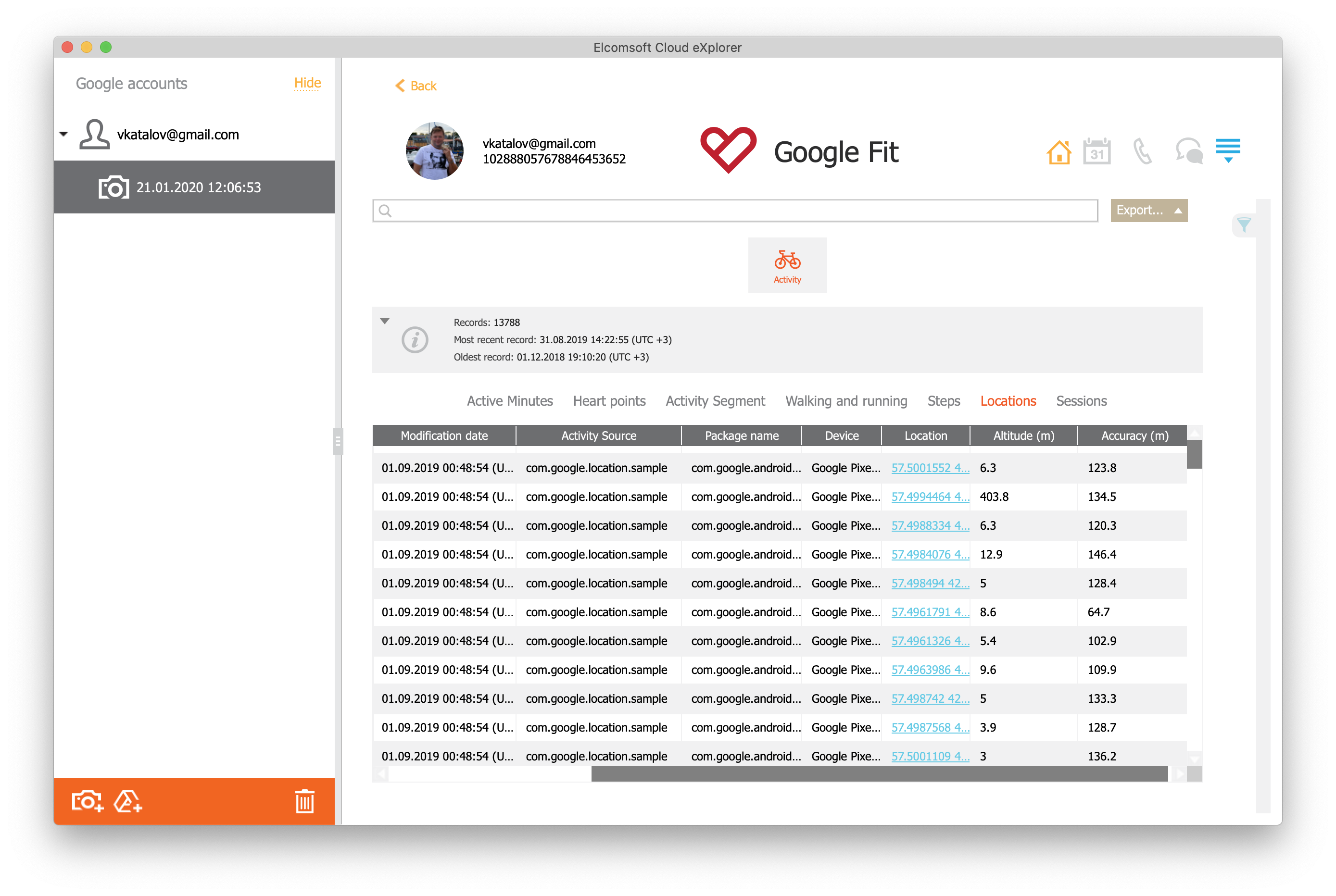
Google Photos
Currently, Google does not offer accessing geolocation tags if you’re using Google Photos API. As a result, forensic analysis of the user’s Google Photos may not return location data. However, retrieving Google Photos via a legal request will yield images with full EXIF metadata including geolocation tags.
Microsoft
Microsoft synchronizes location data with the user’s Microsoft Account. This data can be viewed in the Privacy Dashboard (instructions: View your data on the privacy dashboard) or obtained with Elcomsoft Phone Breaker (Fetching Call Logs, Browsing History and Location Data from Microsoft Accounts). The data can be downloaded by using the “Download your data” link, which returns location points in JSON format. The data is collected by Microsoft from various sources including Cortana, Microsoft Edge (desktop and mobile apps), Bing searches (if signed in to the user’s Microsoft Account).
Microsoft – Apple and Google
One additional source of location data that is rarely mentioned is OneDrive. Office 365 subscribers receive 1TB of cloud storage with their subscription. Apple users receive only 5GB of iCloud storage for free, which limits the number of photos and videos they can store in the cloud without a subscription charge. As a result, savvy iPhone users store their pictures in OneDrive using the corresponding iOS app.
Google offers free unlimited photo storage in Google Photos. However, the free tier dramatically reduces the size and quality of the pictures, making the service less than desirable for those concerned with the quality of their photos. In addition, Google Photos apparently strips location data from EXIF tags. For this reason, a number of Android users also save their photos to OneDrive instead of (or in addition to) Google Photos.
By analyzing EXIF data of the pictures stored in the user’s OneDrive, experts may be able to retrieve a number of additional timestamped location points.
Location Evidence Can Lie
Location data can lie. When analysing digital evidence, blindly trusting The Tool (or The Tools) is the worst mistake one could make. Speaking of location data, one of the most frequent mistakes is relying on EXIF data extracted from all images discovered in the device or in the user’s cloud account. Many of such images may originate from a different device belonging to a different user, received as attachments or saved from the Internet. The location cache, which is another source of location evidence, lists the approximate coordinates of the nearest base station, which may be in quite a distance from the user’s device. Geolocation of Wi-Fi access points is obtained from third-party services based on the access point’s BSSID identifier; this data should generally be questioned as hard evidence. Finally, Significant Locations are great, but are derived with a closed-source algorithm. However, Significant Locations are among the more reliable indicators of the user’s actual location, albeit without a time stamp.
Take, for example, the following screen shot of my Microsoft Account displaying my location history.
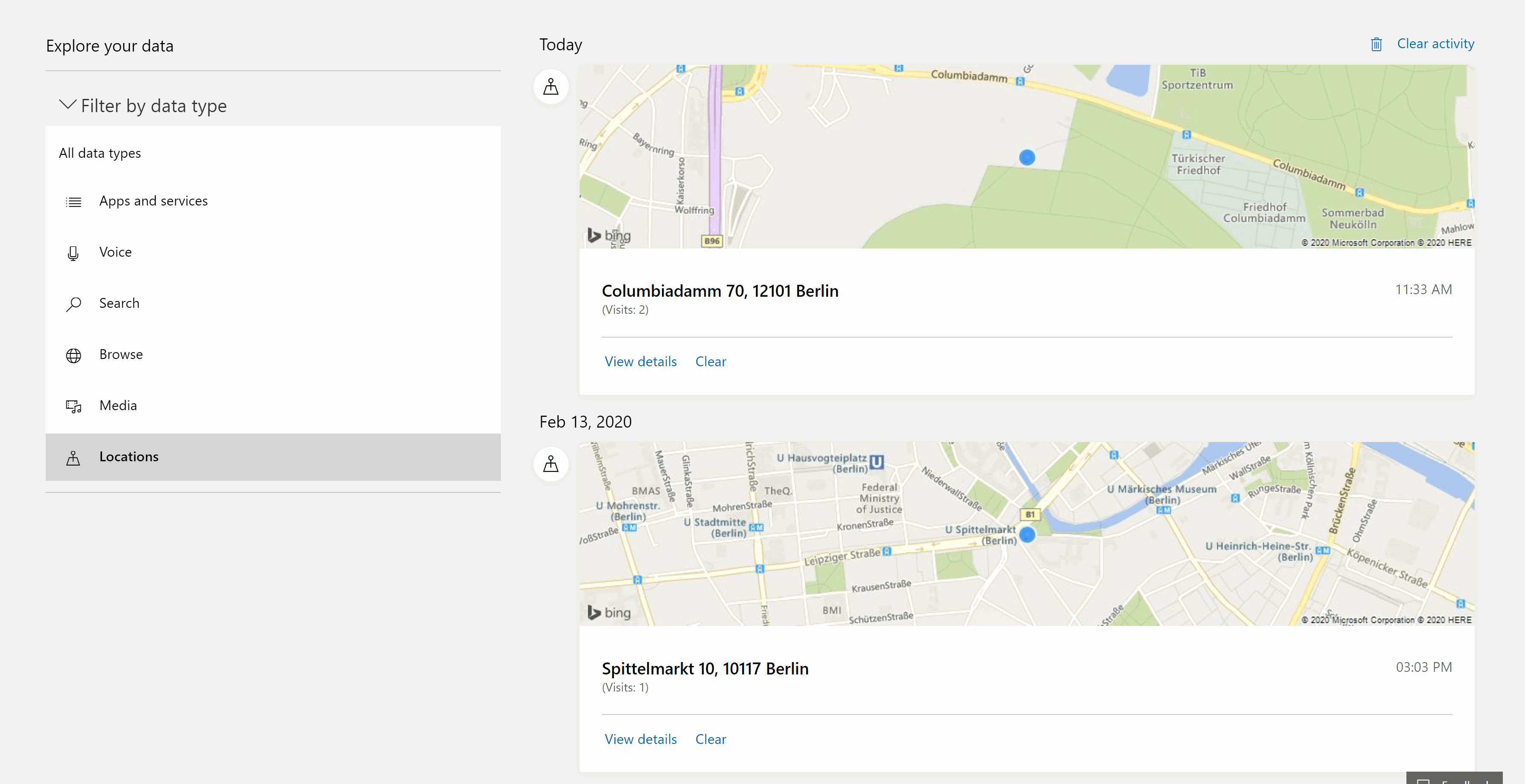
Both of these locations are a lie. The first point is supposed to represents the location of my desktop computer, which is grossly off by some 5 km. The second point is even more interesting, as it represents a device that I no longer own for almost half a year that still, by some miracle, reports its location to my account despite disabling “Find my phone” and erasing the phone.















