The iPhone is one of the most popular smartphone devices. Thanks to its huge popularity, the iPhone gets a lot of attention from the forensic community. Multiple acquisition methods exist, allowing forensic users to obtain more or less information with more or less efforts. Some of these acquisition methods are based on undocumented exploits and public jailbreaks, while some other methods utilize published APIs to access information. In this article, we’ll compare the types and amounts of data one can extract from the same 256-GB iPhone 11 Pro Max using three different acquisition methods: advanced logical, full file system and iCloud extraction.
Overview
We have tested and compared the available acquisition methods for extracting the iPhone 11 Pro Max running iOS 13.3. The device is connected to an iCloud account along with a huge bunch of other devices including the MacBook Pro, one Mac Mini, one iMac, four other iPhones (the 6s, 7, X, Xr), one iPad Pro 3rd gen, one Apple Watch, a couple of Apple TVs and a single HomePod; that’s not even counting devices from other family members. As a result, we expected a lot of the data to synchronize across devices via iCloud.
Please note that the situation is constantly changing. In every other version of iOS and macOS, Apple change the way the data is stored and protected; there are continuous changes to iCloud, too. See macOS, iOS and iCloud updates: forensic consequences for some recent examples.
Logical acquisition
Logical acquisition is the fastest, simplest, and most compatible acquisition method that works for all iOS devices running all iOS versions. All you need is the iOS (iPadOS, WatchOS, tvOS) device itself, plus the Lightning cable (for Apple Watch, also the iBUS adapter).
With logical acquisition, you can obtain:
- Extended device information
- Device backup (iTunes style); may be password-protected
- Media files (plus some system databases that may contain info on deleted files)
- Crash and diagnostic logs
- Shared application data
iTunes backups take a major part in logical acquisition. You can make a backup with iTunes (or in the Finder on the latest macOS Catalina), see How to back up your iPhone, iPad, and iPod touch for details; just make sure that you disabled device syncing with the computer. Most forensic software titles also support this method, though on Windows, they usually require iTunes to be installed anyway (because of the device drivers).
Detailed information on device backups is available in our The Most Unusual Things about iPhone Backups article. The major problem with backups is password protection. If a password is set, it is almost impossible to break it; you may be able to reset the password if you have the device and know its screen lock passcode, but this operation has serious consequences, see The Worst Mistakes in iOS Forensics for details. At the same time, password-protected backups contain significantly more information than unprotected ones (the password must be known, obviously), including the keychain.
There is more to logical acquisition than just backups, and that part is frequently overlooked. Regardless of the backup protection, you can always obtain all media files from the device along with the metadata (which often contains information on deleted files) and thumbnails.
Last but not least, you can always acquire crash and diagnostic logs (that may help to build the device usage timeline), as well as the files shared by some applications.
The good thing about logical acquisition is that it’s sometimes available even for screen-locked devices. The trick works if you have physical access to a ‘trusted’ computer, just before the USB restricted mode is activated on the device. No, you will not be able to break the passcode, but all the data mentioned above will be available.
In our test, we have extracted a backup with 112K files (138 GB total); and 47K media files (incl. metadata), 101 GB total; plus 271 shared files (109 MB).
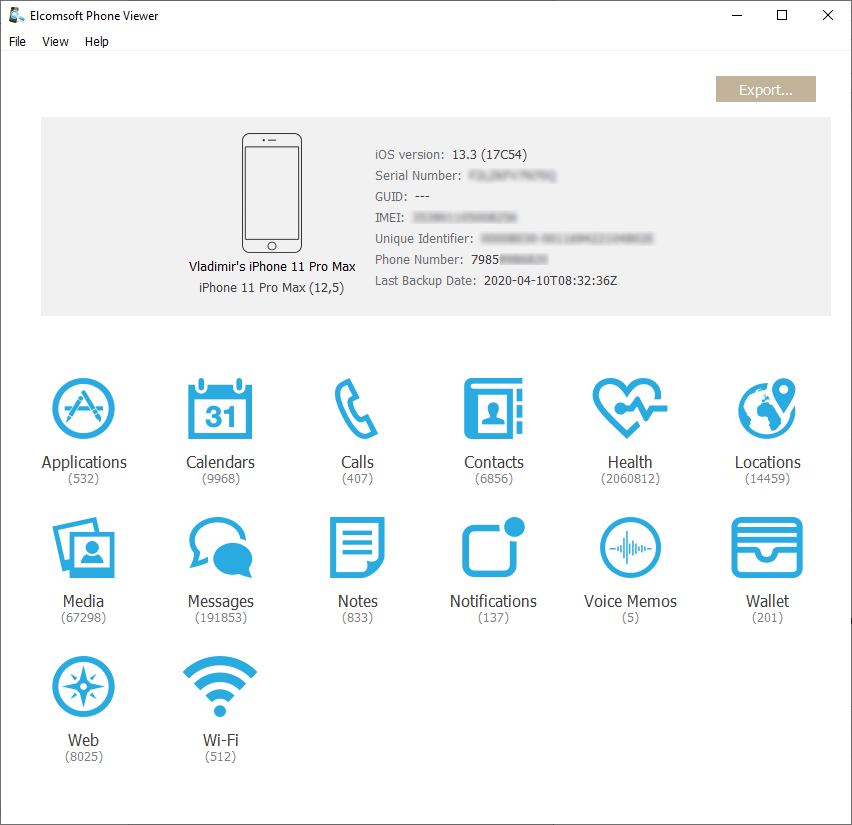
Full logical acquisition (including media files, logs and shared files) is possible in some forensic packages such as Elcomsoft iOS Forensic Toolkit.
Pros
- Very simple to use
- Completely safe if you use forensic software
- Still safe with iTunes (if you don’t forget to disable the sync)
- Compatible with all iOS versions
- May work with locked devices (if pairing record exists)
- Can get device logs and shared app data
- Media files (with EXIF) available even if backup password is set
Cons
- Limited amount of data is available
- Backup encryption may be an issue
- Keychain can be obtained only from protected backups with known password
- You still need that screen lock passcode to pair the phone to the PC (unless using existing lockdown files)
Full file system acquisition
Even a password-protected backup contains significantly less information than actually exists on the device. The device stores enormous amounts of data: system databases (with detailed location data), third-party application data even from secure messengers, SQLite write-ahead logs (WAL) that may contain deleted data, temporary files, WebKit data, AplePay transactions, notifications from all applications, and a lot of other critical evidence.

Extracting the full file system can be relatively difficult. The first problem is the problem of choice. With several different ways to access the file system (classic and rootless jailbreaks, the checkm8 exploit, and agent-based extraction) laid out into a three-dimensional compatibility matrix, it’s a tough choice when it comes to selecting the right method. At this time, we can extract the file system from all of the devices running iOS 13.3 and older (see Full file system and keychain extraction: now with iOS 13 and iPhone 11 support); for older ones (up to iPhone X) it is possible even for the latest iOS 13.4.1, including partial extraction for devices locked with an unknown passcode (see BFU Extraction: Forensic Analysis of Locked and Disabled iPhones).

But it worth it, really. For the same device mentioned above, we got 211 GB of data in about the same time (the speed is about 2.5 GB/min, or 150 GB an hour).
That method, theoretically, can be used by installing a jailbreak to the device. However, jailbreaking is far from being forensically sound with too many changes, most of which are not documented. You will also need a tool such as iOS Forensic Toolkit to decrypt the keychain.
Pros
- Partial acquisition is available for locked/disabled devices
- Full set of data acquired
- Backup password protection is ignored
- MDM protection is not an issue
- Complete keychain is available
Cons
- iOS version should be vulnerable
- Requires iOS developer account
iCloud acquisition
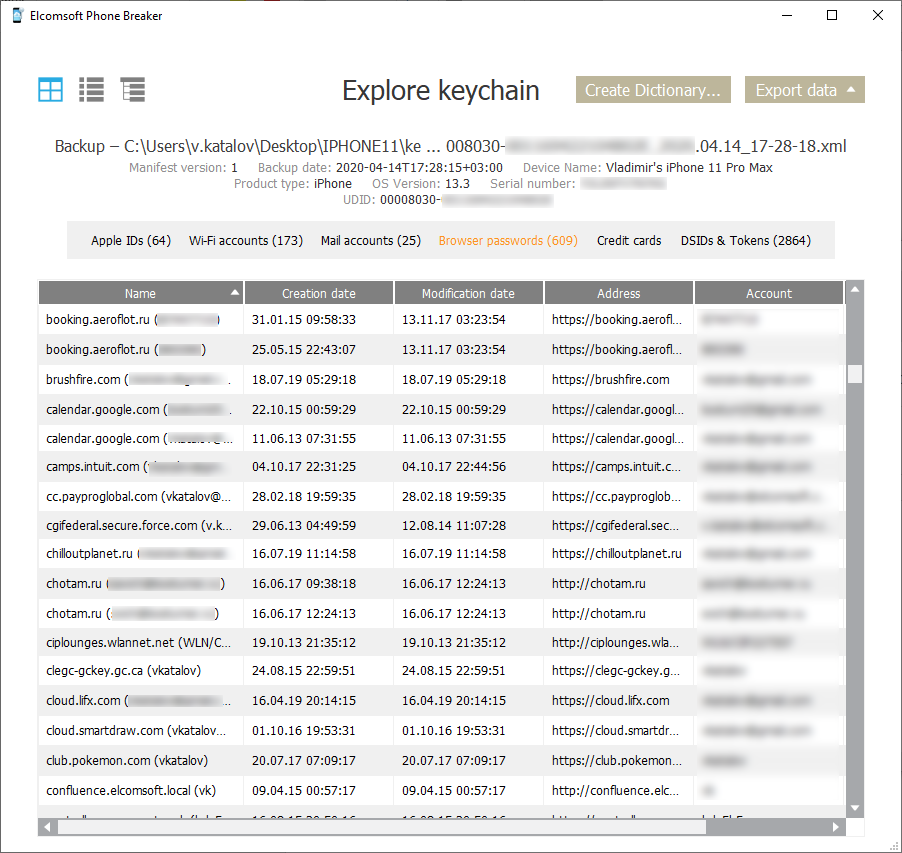
That’s actually the hidden gem. Initially, iCloud acquisition was all about the backups. Today, the role of iCloud backups had diminished significantly; the iCloud backups are even more limited than local iTunes backups with no password set. Most iPhones and iPads also sync a lot of data with the cloud. Just about everything can be sunced from contacts to photos and messages, as well as the keychain. Also, the iCloud keychain, contrary to Apple’s doc, may contain not just passwords but also authentication tokens. There is also iCloud Drive with many files and documents, usually including Documents and Desktop folders from Mac computers. And all that is collected not just from a single iPhone but from all devices connected to the account.
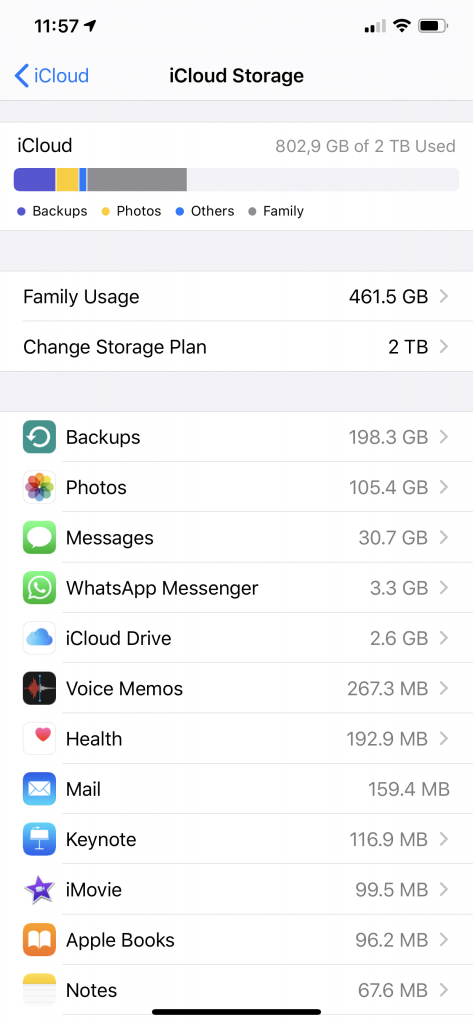
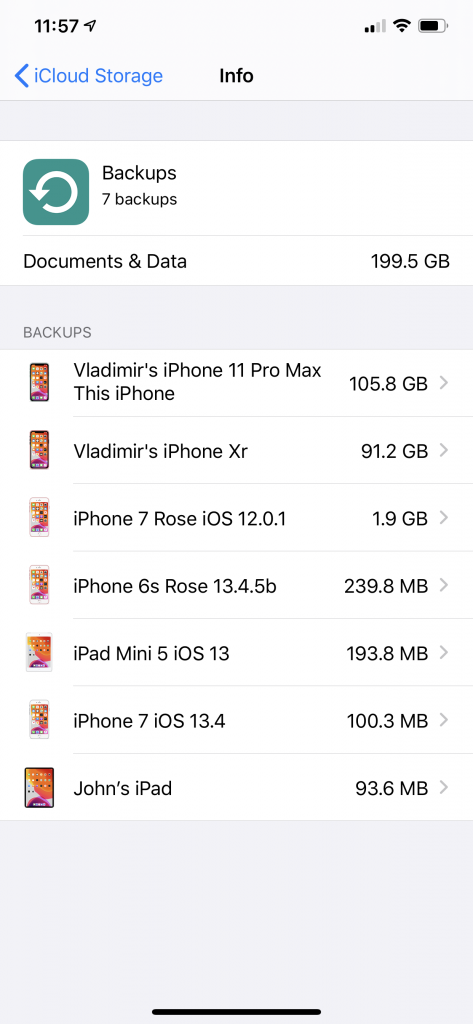
During the test extraction with Elcomsoft Phone Breaker we have extracted 39 GB of synced data, plus 101 GB of iPcloud Photos; that’s not counting the backups. Amazing.
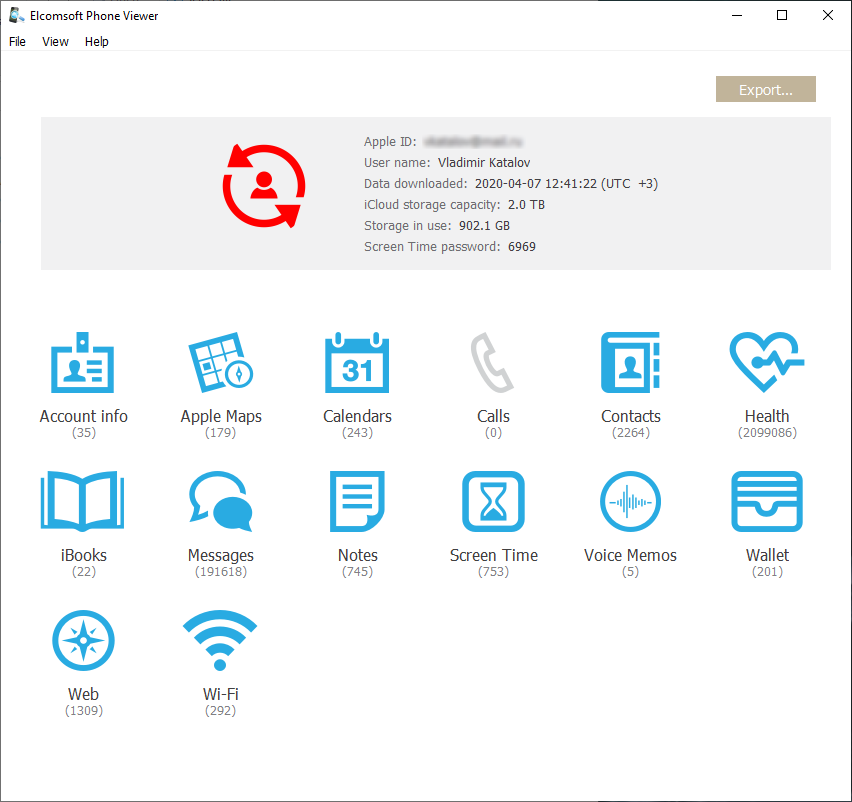
Also, there is a lot of files on the iCloud Drive. This includes documents, third-party application data and backups from some messengers, password managers and more.
More information:
Pros
- Compatible with all iOS versions
- The device itself is not needed
- Data from all the devices connected to the account is accessible
- iCloud keychain can be obtained
- Files in iCloud Drive
- Real-time data is available
- Older device backups might be accessible
Cons
- iCloud credentials (including the second factor) are required
- Acquisition with tokens may be possible, but very limited
- Password/passcode of one of the trusted devices is required to access end-to-end encrypted data
- Device(s) may not use iCloud at all, so sometimes no or almost no data is available
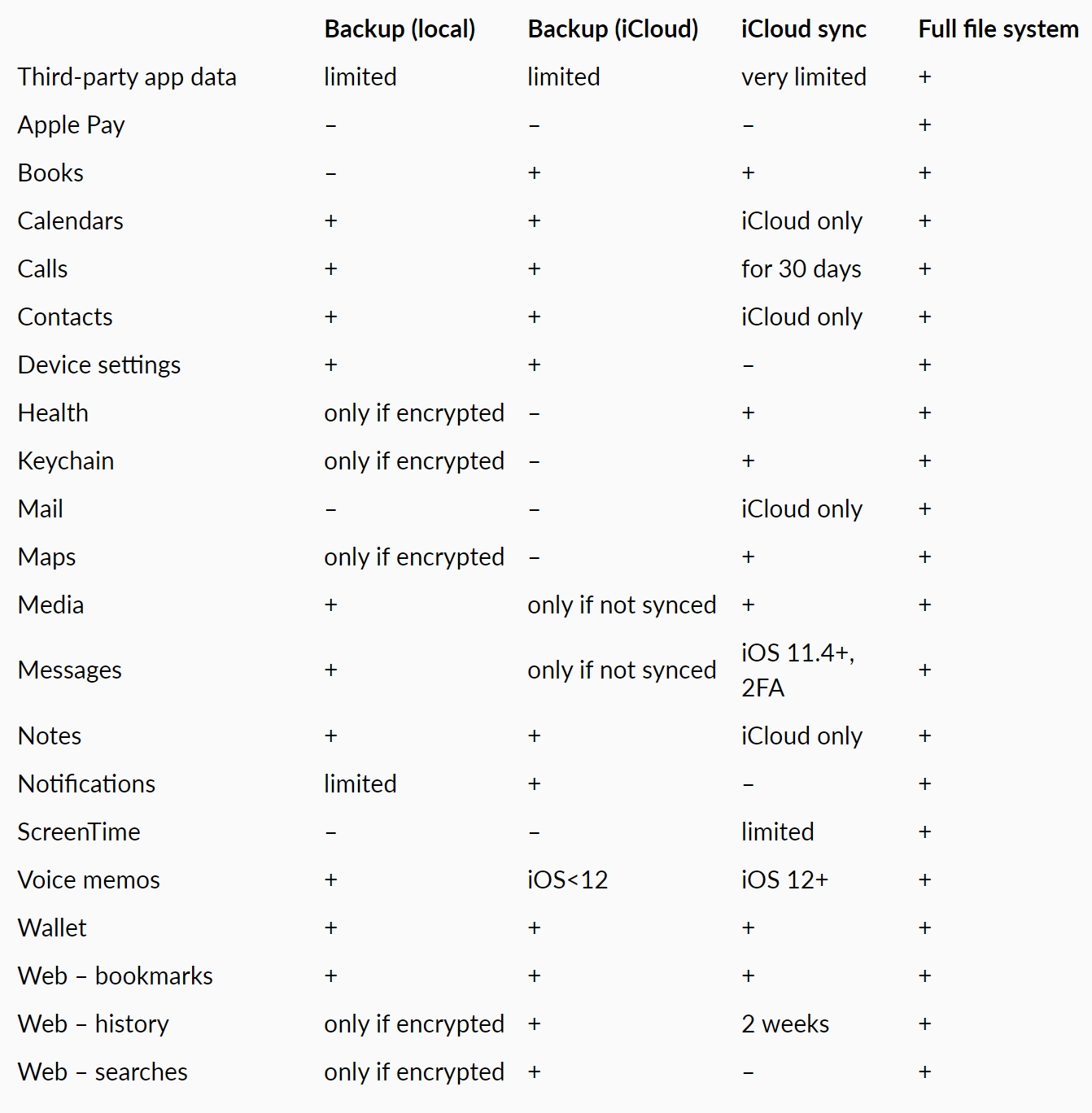
Comparison table
Below is a compact comparison table of what you can expect to obtain with each acquisition method:
Conclusion
In this article, we’ve briefly overviewed and compared the different iOS extraction methods. Armed with this information, you might be able to extract more data from the device than you’ve initially considered available.













