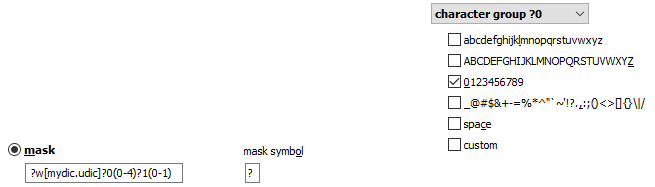Password managers or password reuse? This is the question faced by most consumers. Reusing a password or its minor variations for different accounts has never been a good idea, yet in today’s world of online everything the rate of password reuse reaches astonishing values. Using a password manager helps reduce password reuse, supposedly offering increased security. In this article, we’ll perform forensic analysis of some of the most common password managers.
Reusing Passwords is a Bad Idea
Major hacks and security breaches happen all the time. Occurring quickly one after another, there is little doubt the hackers are using databases of previously harvested passwords in order to try exploiting a variety of online resources. Password reuse is a major contributor to these hacks. After harvesting a single password database, hackers are quick to try stolen account credentials on other resources. Implemented via a botnet, these attacks may not trigger a security warning even if the account is compromised.
Old researches suggest the password reuse rate among user accounts on different services was at least 31 percent just a few years back. Today, the number of online accounts used by an average consumer had grown significantly, which led to severe increase of reused passwords. Recent reports suggest that some 59% of consumers reuse password across a number of different online services. This number can be significantly higher if we count the use of similar passwords.
What do these numbers mean in practice? For every 20 online accounts, an average consumer employs only 7 different passwords. Of these 7 passwords, only 3 are unique. The “different” passwords looks obviously similar. One of the most common behavioral patterns we observed was appending the number of digits and special characters required by a given Web site or resource to the end of the password. As a result, the list of “different” passwords may include simple variations such as password1, password123, Password1$, and so on. These patterns may be easy to detect and exploit during an investigation.
Password Reuse and Computer Forensics
While password reuse is bad for security, allowing hackers quickly attacking a number of services, it can be a blessing for computer forensics. By obtaining the list of passwords, experts may be able to determine a common pattern. This pattern, in turn, enables them building a so-called mask-based attack. Mask-based attacks reduce the number of passwords to try by allowing to specify something that all or most of the user’s password have in common.
As an example, Elcomsoft Distributed Password Recovery that we have updated a few days ago had significantly improved one of the most popular masks. Before we get to that, let us see what some of these passwords have in common:
password
Password$
password1
Password12
Password5678
Password123$
As you can see, all of these passwords are based on a single key word “password” that may or may not start with a capital “P”. The key word may or may not be followed by a number containing up to 4 digits, that may or may not be followed by a special character. This is a very realistic scenario; the user tries using as simple a password as they can get away with. However, if a security policy enforces the use of a certain number of capital letters, numbers and special characters, the user simply adds them to the end of the password.
In EDPR 4.20, you can use a simple mask like this:
?0assword?1(0-4)?2(0-1)
character group ?0: Pp
character group ?1: digits
character group ?2: special symbols
Now, what do the following passwords have in common?
andy1980
apple1$
mary1968
hopeful1
wardrobe
monitor$
All of these passwords are based on a single dictionary word that start with a small letter, that may or may not be followed by a number containing up to 4 digits, that may or may not be followed by a special character. If you were using an older version of Distributed Password Recovery, you’d have to build a very complex hybrid attack to account for all of these password variations. EDPR 4.20 makes it as simple as this:
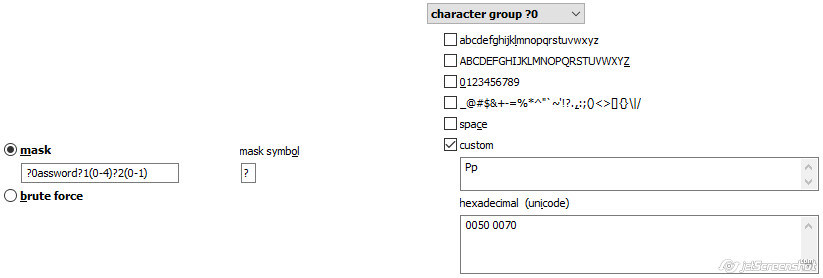
?w[mydic.udic]?0(0-4)?1(0-1)
character group ?0: digits
character group ?1: special symbols
Now, what if the user had a slightly more complex set of passwords like this:
Andy1980
Apple1$
mary1968
hopeful1
wardrobe
monitor$
These passwords are similar to the previous case in being based on a single dictionary word that may or may not be followed by a number containing up to 4 digits, that may or may not be followed by a special character. However, this time around the dictionary word may or may not start with a capital. Do we have a mask for that? Learn by taking a 3-day training course on breaking passwords!
Password Managers
1Password, Dashlane, KeePass and LastPass are the four most popular password managers. Password managers store, manage and (optionally) sync user passwords as well as other sensitive data. Password managers were explicitly designed to mitigate the issue of password reuse, offering the ability to generate, store and use passwords that are truly unique and non-reusable.
A typical password manager keeps all passwords in a database. The database is secured (encrypted) with a master password, and stored either locally or in the cloud. Password managers support both desktop and mobile devices, employing strong encryption to secure access to the password databases.
Notably, the entire password database is usually protected by a single master password. That single master password decrypts and opens all stored passwords.
Since most customers use their mobile devices to access accounts and open documents, password managers are also available on mobile platforms. Touch screens are no physical keyboard, and “motor learning” cannot be used to type complicated passwords; this results in simpler master passwords selected by users who frequently unlock their password vaults on mobile devices. Touch ID or Face ID do help avoid typing in the master password, but authentication with a master password is still required from time to time.
1Password is developed by AgileBits since 2006. This password manager supports Windows, macOS, iOS and Android platforms. The database can be stored locally, in Dropbox or in iCloud. The database is included with iTunes backups and iCloud backups.
LastPass was introduced by Marvasol Inc (acquired by LogMeIn) in 2008. LastPass also supports Windows, macOS, iOS and Android platforms. In addition, LastPass can be installed as a browser extension in many popular browsers. Passwords are synchronized through the LastPass server. In addition to desktop versions, the password database can be also acquired from browser extensions and Android devices.
Dashlane was developed by Dashlane in 2012; it also supports Windows, macOS, iOS and Android. Passwords are synchronized through Dashlane server. The password database can be only acquired from the computer or mobile device via file system extraction.
KeePass is an open-source application with native builds available for Windows only. There are numerous third-party ports for all major desktop and mobile platforms. KeePass offers no backup or synchronization options; the database can be acquired from the local PC or via file system extraction of a mobile device.
As I have already mentioned, password managers store passwords in local databases. These databases can be (and most probably are) encrypted with a single master password. Due to the sensitive nature of the information, the protection is typically very strong to sustain high-performance brute-force attacks. However, many password managers employ different protection settings for the different databases across their apps and plugins. A Windows desktop app would typically carry the strongest protection, while an Android app would use the weakest protection. Some password managers use adaptive protection strength that depends on the measured performance of the particular device.
Either way, using GPU-assisted attacks is a must when attacking password manager databases. The latest version of Elcomsoft Distributed Password Recovery can utilize GPU acceleration to speed up attacks on 1Password, Dashlane, KeePass and LastPass databases encrypted with a master password. The following benchmark demonstrate the performance of the attack on local databases extracted from the corresponding Windows desktop apps of 1Password, Dashlane, KeePass and LastPass:
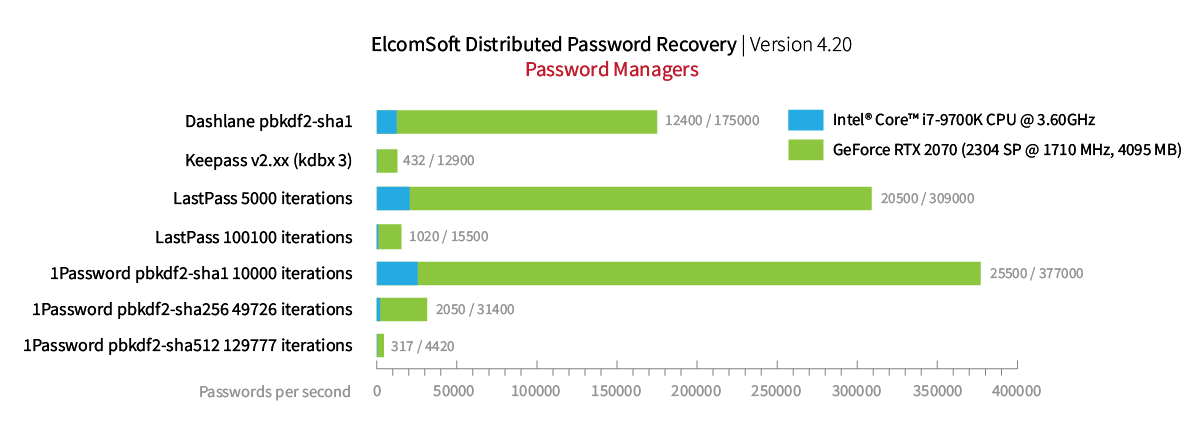
If you’re confused with benchmark values for the different password managers, this is because they are confusing. Password managers do employ different protection settings in different environments. For example, if we take 1Password, the recovery speed depends on the hashing algorithm (SHA-1, SHA-256, or SHA-512) and the number of iterations. The desktop Windows app supports SHA-512 with a seemingly random number of hash rounds, which is calculated individually based on the performance and some other characteristics of the particular computer; this is to ensure that the password database is opened without a delay. Correspondingly, the speed of the attack falls as the the number of iterations increases. For this reason, the benchmarks for 1Password may look very confusing.
A Word of Caution: a Unique Password Is Not Enough
Even if one used a unique, random password for every online account, this may not be enough to secure online presence. A compromised ‘generic’ email account such as Yahoo! Mail not only enables the attacker to access historic email messages stored in that account, but to request password reset for other accounts registered with that email address. Which accounts exactly? That would be easy to guess by analyzing the user’s email history. A compromised Google Account opens access to the user’s entire digital life from comprehensive location history to – you guessed it! – stored passwords. Compromised Apple and Microsoft accounts lead to similar consequences. As a result, we cannot stress enough the importance of two-factor authentication. We believe no Apple ID, Google Account, Facebook or Microsoft Account should be ever used without two-factor authentication.