Cloud acquisition is one of the most common ways to obtain valuable evidence. When it comes to Google, the Google Account analysis may return significantly more data compared to the extraction of a physical Android device. However, there is one feature that is often overlooked: the ability to extract data stored in the user’s Google Account without the login and password. Let’s talk about Google authentication tokens and what they bring for the mobile forensics.
Authentication Tokens
The general concept behind authentication tokens is very simple. Instead of the login and password, your Web browser or app would send a small set of binary data instead of your login and password. Once the token has been obtained, the user can access the required resources for a period of time without the need to re-enter their login and password every time. In other words, instead of having to use the login and password every time for accessing the different Google services, the user authenticates once, obtains an authentication token, and uses that token for further authentication through other Google services. An authentication token obtained in Google Chrome is automatically used to sign the user into their Google services such as the online address book, calendars and so on. Notably, the token cannot be used to access some services such as the online password storage.
Tokens are not passwords. They are not password hashes either. Instead, tokens are random (or pseudo-random) sequences of characters or binary data. The token is generated by Google servers after the user first passes authentication. While the token works as a password replacement, it cannot be used to attack or recover the password: the data is just a random identification string, which is not a hash function of the password itself. The use of authentication tokens makes the system not only more convenient (no need to re-authenticate for the user) but in a way more secure since the password is not saved anywhere.
When it comes to Google, we can use two types of tokens: the one used in the Google Chrome browser to access Google services in general, and the specific type of token used to access files stored in Google Drive. The second type of tokens is only used by the Google Backup & Sync (formerly Google Drive) app if one is installed on the computer.
Google also stores authentication tokens on mobile devices (both iOS and Android). While one may be able to extract and use these tokens, they are generally more difficult to extract compared to the tokens stored on the user’s personal computer.
The Google Drive token
This authentication token is created by the Google Drive (Google Backup & Sync) app on Windows and macOS computers. The token is stored encrypted. In Windows systems, the token is protected with DPAPI, while in macOS the app utilizes the system keychain to encrypt the token.
The Google Drive token can be extracted and decrypted with Elcomsoft Cloud Explorer. The Google Drive tokens are limited; they can be only used to access files in the user’s Google Drive plan.
In order to extract the Google Drive token, you’ll need the original Windows or Mac computer that was used to log into Google Drive with the Google Backup & Sync app installed. You will also need Elcomsoft Cloud Explorer to extract and decrypt the token. Of course, just any random PC won’t do the trick. You’ll need a computer which has the Google Backup & Sync app installed, and the user must’ve been logged in to Google Drive on that PC at the time the computer is seized. If the user logged out of their Google Drive, the authentication tokens are then deleted (or just invalidated).
The Chrome token
This token is created when the user signs in to their instance of the Chrome browser. This token is valid to authenticate the user with a number of Google services. In Windows systems, the Chrome token is protected with a combination of DPAPI and Gcm256 (old versions of Chrome relied on DPAPI protection exclusively), while in macOS the app utilizes the system keychain to encrypt the token.
In order to extract the Chrome token, you will also need the user’s original Windows or Mac computer with the Chrome browser installed. The user must be signed in to that browser at the time of extraction.
You will need Elcomsoft Cloud Explorer to extract the token. If the user signs out of their Google Account in Chrome, the authentication tokens are then deleted.
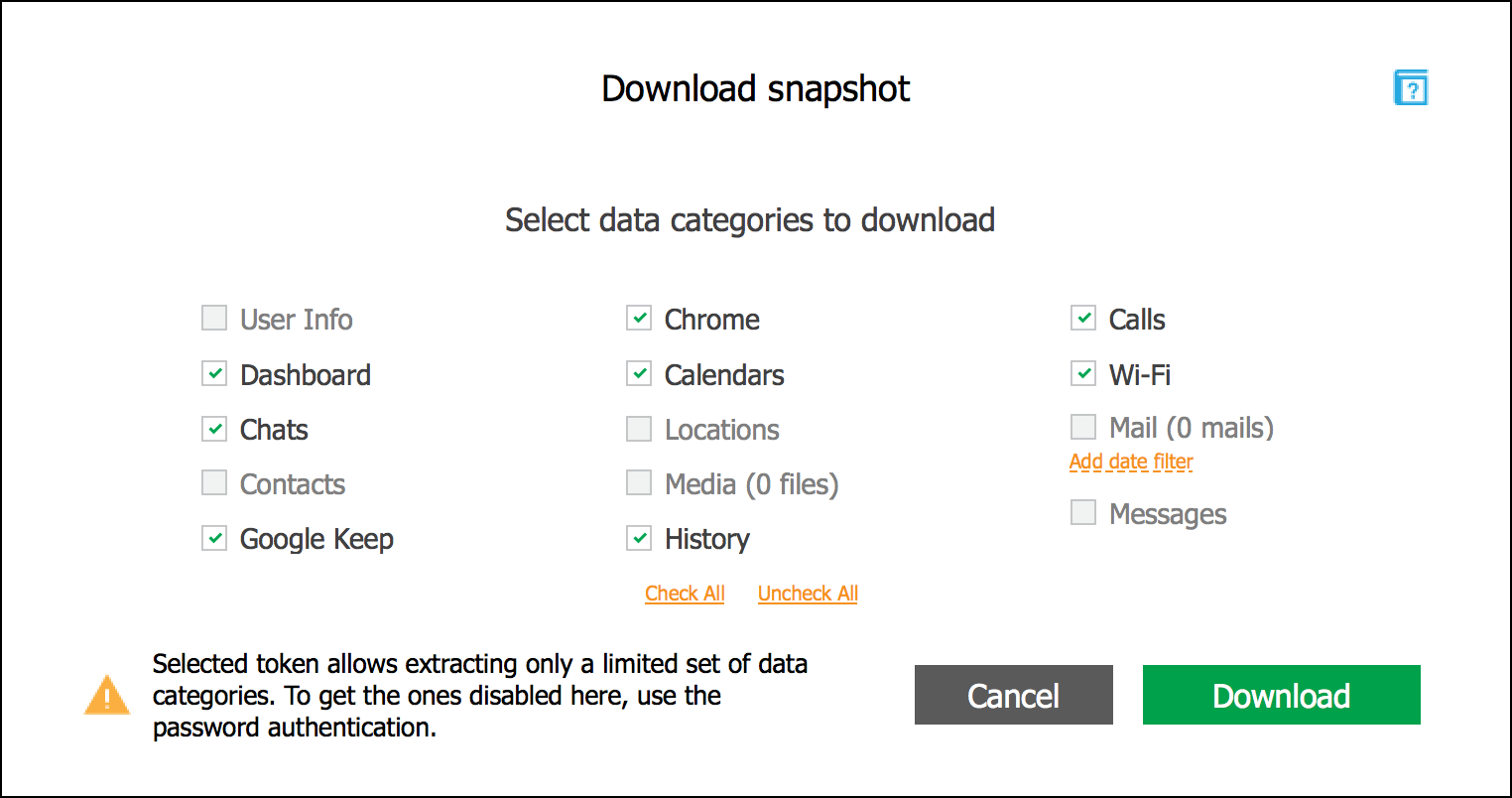
The Chrome token provides access to more data categories compared to the limited Drive token. The accessible categories include Chrome history and other data (e.g. the list of open tabs and bookmarks), the list of Wi-Fi networks, call logs, calendars, Google Dashboard data, as well as Google Keep notes. The full list of data categories accessible with Chrome authentication tokens is shown here:
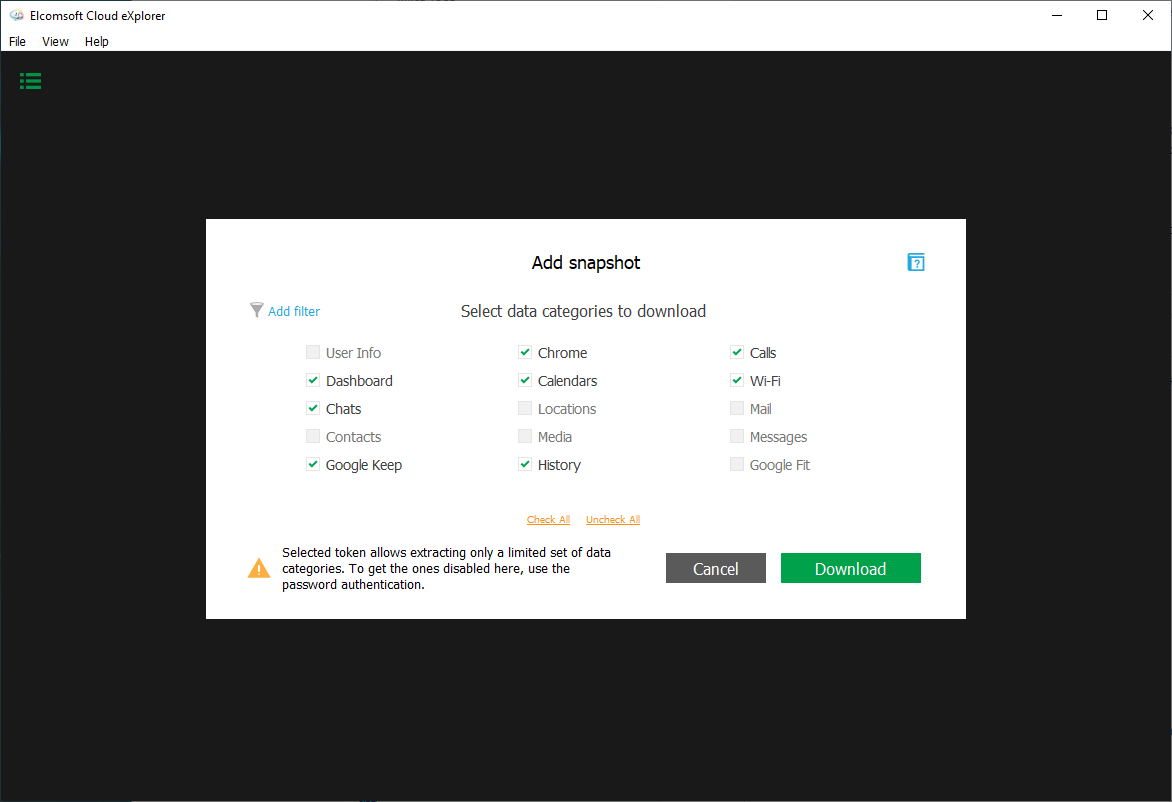
Extracting the tokens
We researched where Chrome and Google Drive tokens are stored on Mac and PC computers, and discovered a way to use them for passwordless authentication into Google services with Elcomsoft Cloud Explorer. Passwordless authentication is available if Google Chrome is installed on the user’s computer, and if the user has signed in to any Google service via the browser.
This is where Google stores the authentication tokens on the user’s computer.
For Google Chrome tokens:
Chrome Windows:
%appdata%\Local\Google\User Data\<Profile_name>\Web Data
Chrome macOS:
~/Library/Application Support/Google/Chrome/<profile_name>/Web Data
For Google Drive tokens:
Windows (in the Registry):
HKEY_CURRENT_USER\SOFTWARE\Google\Drive\
The key name starts with "OAuthToken_"
macOS (in the Keychain):
in the login keychain
Elcomsoft Cloud Explorer comes with a tool named Google Token Extractor (GTEX). This command-line tool automatically searches the user’s computer (Windows or Mac) for authentication tokens saved by the Google Chrome browser or the Google Drive app. Once the authentication token is located, GTEX saves it into the current (Windows) or the user’s default directory (Mac). Tokens for all logged-on accounts will be extracted, decrypted and saved.

Once Google Token Extractor extracts the token, the file is named according to the following format:
<user_name><Google ID><token_type><date><time>.xml
Example:
Google Chrome:
john.smith_test.account@gmail.com_GoogleChrome_05.05.2020_15-05-16_UTC.xml
Google Drive:
john.smith_test.account@gmail.com_GoogleDrive_05.05.2020_15-05-16_UTC.xml
Inside, the token may look like this.
Google Chrome (Windows):
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?>
<ExtractedToken>
<GTEXVersion>1</GTEXVersion>
<Platform>Windows</Platform>
<GoogleID>test.account@gmail.com</GoogleID>
<Token>1/ukM2X_qTUU-viA-8Yn6LqzLjcGQ-nmHjsh254RYAOF4</Token>
<TokenType>GoogleChrome</TokenType>
<ClientID>77185425430.apps.googleusercontent.com</ClientID>
<ClientSecret>OTJg....</ClientSecret>
<ExtractedAt>03.04.2018 09:12:35</ExtractedAt>
</ExtractedToken>
Google Drive (МаcOS)
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?>
<ExtractedToken>
<GTEXVersion>1</GTEXVersion>
<Platform>macOS</Platform>
<GoogleID>other.test.account@gmail.com</GoogleID>
<Token>1/ukM2X_qTUU-viA-8Yn6LqzLjcGQ-nmHjsh254RYAOF4</Token>
<TokenType>GoogleDrive</TokenType>
<ClientID>645529619299.apps.googleusercontent.com</ClientID>
<ClientSecret>nu6p....</ClientSecret>
<ExtractedAt>27.02.2018 16:46:55</ExtractedAt>
</ExtractedToken>
Once the token is extracted, it can be used with Elcomsoft Cloud Explorer to access information stored in the user’s Google Account without the need to re-enter the password or perform the secondary authentication step.
Using the tokens
The Google Drive token extracted from Google Backup & Sync can only be used to extract files from the user’s Google Drive account.
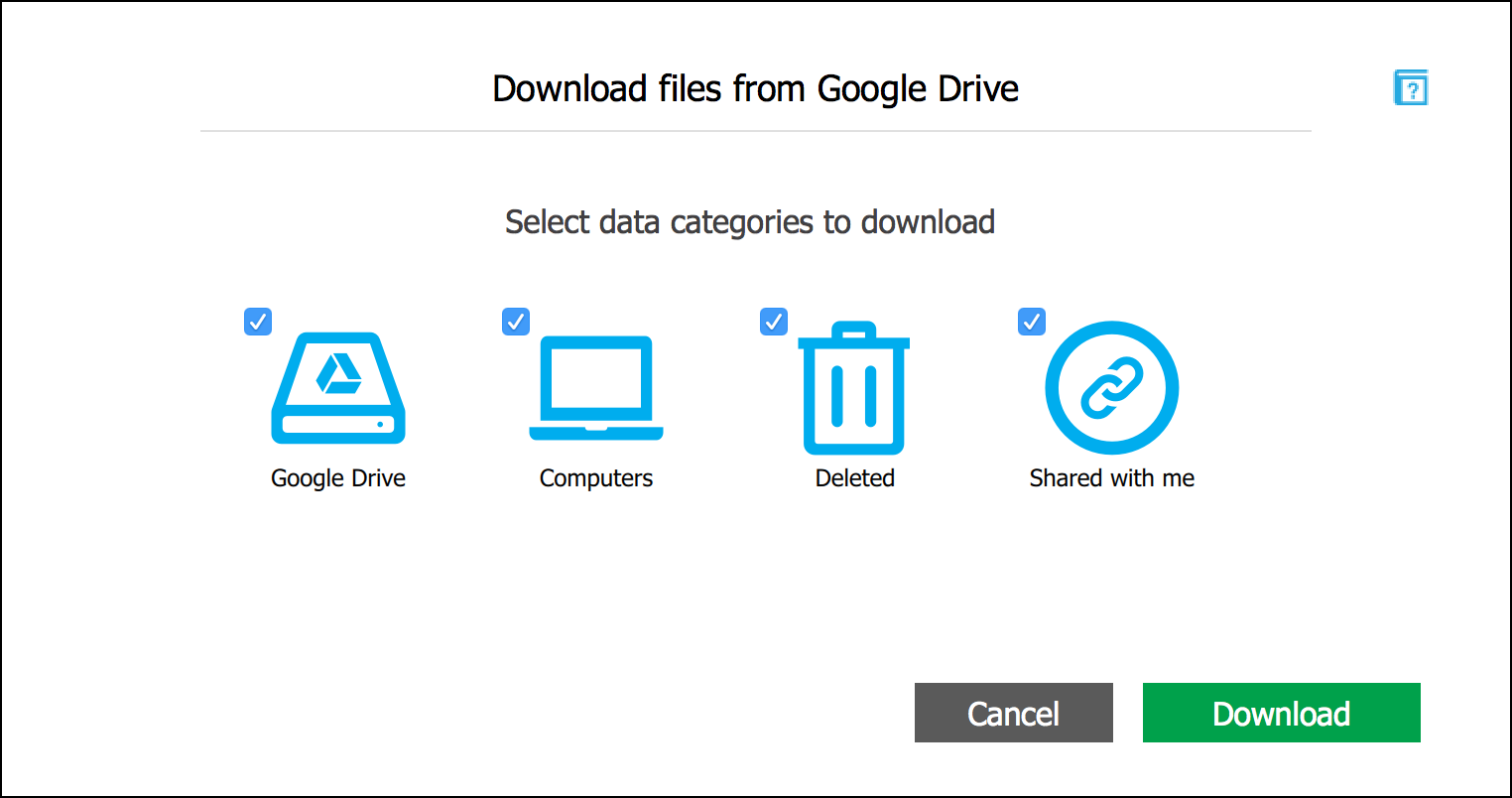
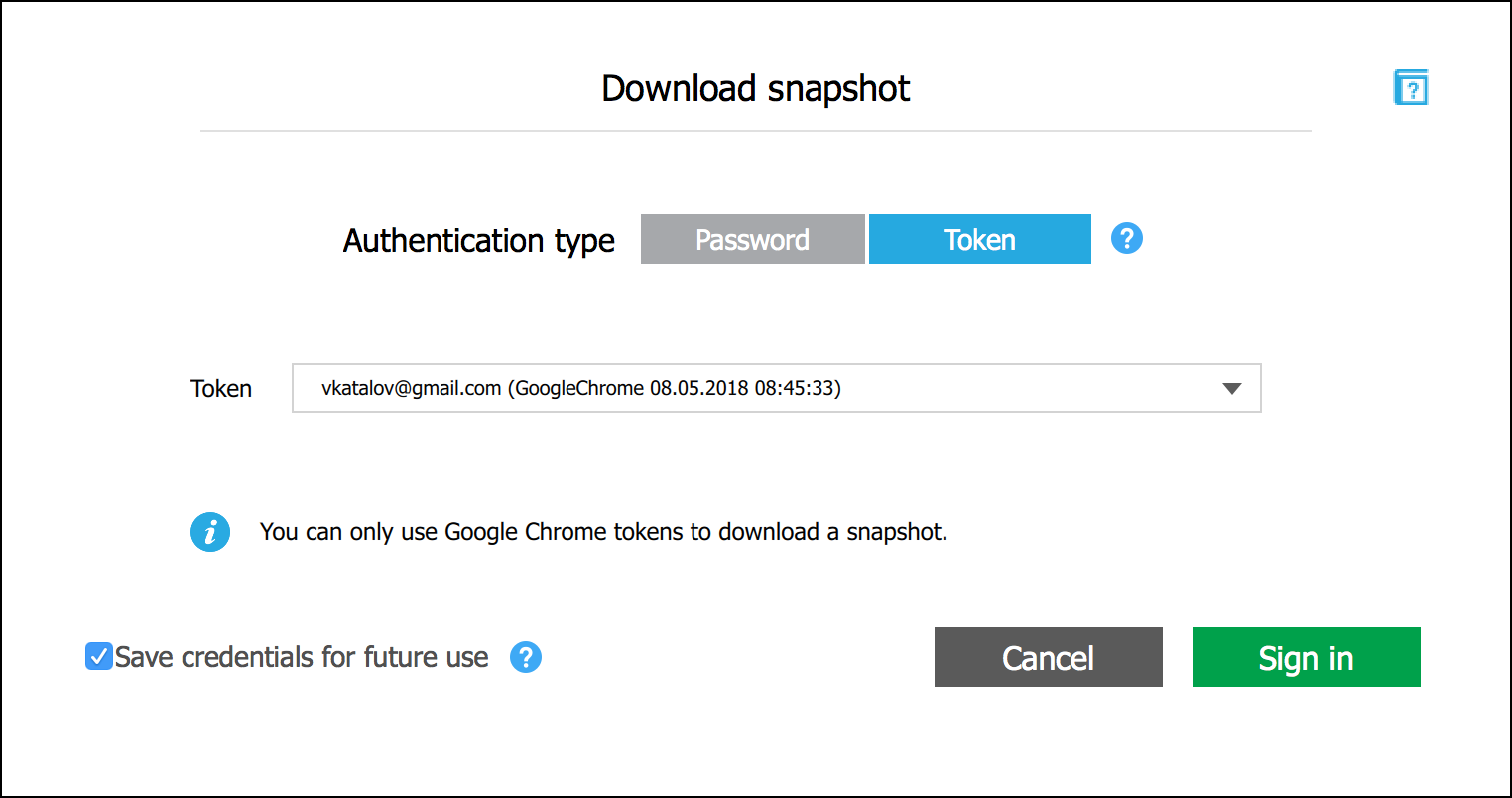
The Chrome token, however, can be used to access many additional data categories. To sign in with a token, create a new snapshot in Elcomsoft Cloud Explorer and choose to authenticate with a token.
You will be presented with a list of available data categories (the ones that are grayed out may contain some data, but it is simply not available by the token, but only with login and password).