The new build of iOS Forensic Toolkit is out. This time around, most of the changes are “internal” and do not add much functionality, but there is a lot going on behind the scenes. In this article, we will describe in details what is new and important, and how it’s going to affect you. We’ll share some tips on how to use the software in the most effective way, making sure that you extract all the data from iOS devices in the most forensically sound possible.
The problem(s)
In order to acquire the data from iOS (watchOS, tvOS, or iPadOS) device, you need to talk to it over the USB connection. While Wi-Fi acquisition is also possible in some cases, the good old cable is always better. We use several different protocols and services running on the device, and there is quite a lot of stuff between our tool and the low-level Apple driver (there is simply no other way to talk to the iPhone).
First, the driver. Have you seen the problem listed in If your computer doesn’t recognize your iPhone, iPad, or iPod? There is more: in the standalone version of iTunes for Windows there was an additional component called “Apple Mobile Device Driver”, in fact even two of them (32-bit & 64-bit). The Microsoft Store edition of iTunes does not have one, though the drivers of course are there. Long story short, we always relied on the component listed above, and the Toolkit may fail to operate if it does not find one. Most other forensic packages for iOS acquisition work the same way; without these components, they recognize the device, but can not get any data from it.
Second, there are some other components between the Toolkit and the drivers. Just to give you an idea, have a look at CheckRa1n article: third-party components, iproxy stuff, plus a lot of things that are not listed there (such as itunnel_mux).
Last but not least, the type of the connection. We always recommended to not only put the device into Airplane mode, but also disable network connections (Wi-Fi and even Ethernet) on the computer you run the Toolkit on. I sometimes forget to do that myself, receiving unexpected result. I even had a good one once the Toolkit accidently connected to my Apple TV that in the same Wi-Fi network and got some data from it; at the time, I did not even know that Apple TV acquisition is possible; read Apple TV and Apple Watch Forensics 01: Acquisition to see what it ended up with.
What has been changed and how it affects you
The new communication channel drops legacy dependencies and becomes significantly faster and more robust. Now it does not matter whether you have the legacy or Microsoft Store edition of iTunes installed (still, we recommend you to read Apple iTunes: Standalone vs. Microsoft Store Edition, as there are some other important differences, affecting other products), as well as the status of the network connection. In fact there is much more – for example, after the reconnection of the device while Toolkit is running.
Note that the changes affect logical acquisition and jailbreak-based TAR extraction only; file system imaging via the extraction agent is unaffected as it was already using the new communication mechanism.
Anything else? Yes. We sometimes experienced problems with (I)nfo, (L)ogs and (S)hared commands on certain combinations of device/iOS. It worked perfectly one day but did not give an expected result on some other computer the day after (no data or limited data). It was related to the same channel/protocol problems; now fixed. Also, we have improved iOS 13.4.1 support, and added support for iOS 13.4.5 (beta 4 is now available, and the Toolkit has been fully tested with it, though we have yet to check whether there is any new data in 13.4.5 related to new Exposure Notification API for COVID-19 tracking).
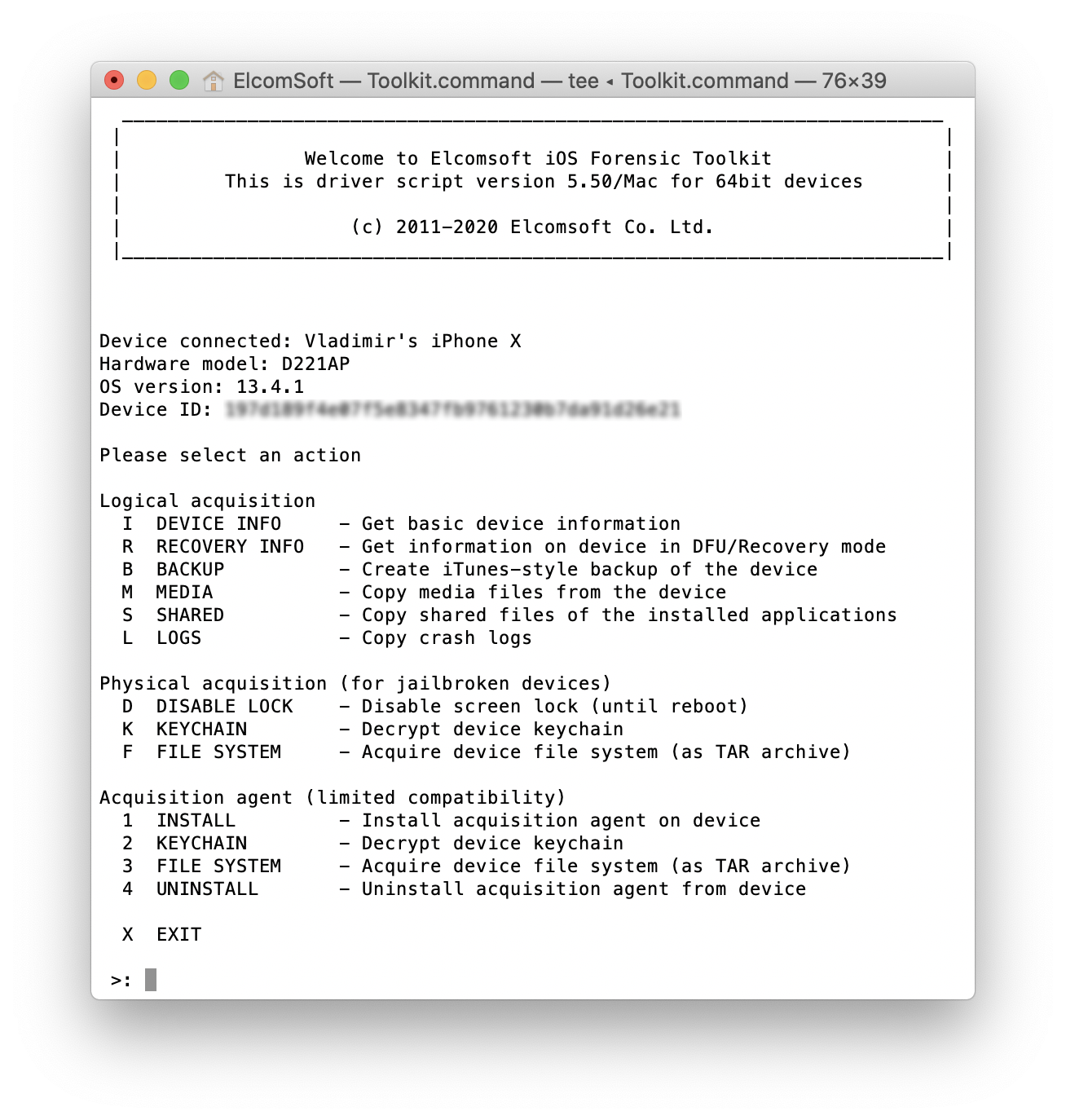
Windows or macOS?
The short answer is “both”, but we still strongly recommend using macOS systems for data acquisition (for analysis, you have more options on Windows). The macOS version always was (and will be) more reliable and convenient than the Windows one, mostly because of the higher quality USB drivers, but also due to some notable differences in the system kernel.
If you are using macOS 10.15 Catalina, follow the tips listed in Installing and using iOS Forensic Toolkit on macOS 10.15 Catalina article; in brief:
- Process the DMG image of iOS Forensic Toolkit using xattr command.
- Establish trust relationship with the device in Finder (there is no immediate prompt when you connect the device).
- If you need to access lockdown files, disable SIP first (requires reboot), then give yourself access to this folder with sudo chmod command.
If you still prefer Windows (we still support Windows 8/8.1 and Windows 7 along with Windows 10), make sure you read iOS Acquisition on Windows: Tips&Tricks. There is just one additional yet important note. When you create an iTunes-style backup with the Toolkit, please be patient. After selecting the output folder and receiving the notification on the backup password, but before the process of creating a backup actually starts, there is a pause of up to 2 minutes. It looks like nothing is happening while you wait – this is normal. Finally, if something goes wrong with the Windows version, the first thing to try is just reboot the system and run the process again. It really helps in 90% cases. Again, that’s why we always recommend to use macOS but not Windows!
Compatibility info
Here is the most actual information:
- (Advanced) logical acquisition: all devices, all versions
- Full file system and keychain extraction of jailbroken devices: all device/iOS combinations where a jailbreak is available (currently up to iOS 13.4.5 beta for checkra1n-compatible devices, up to 13.3 incl. for iPhone Xs/Xr/11/11 Pro)
- Agent-based extraction: most devices running iOS 11.0 to 13.3 (except the iPhone 5s and 6 running some specific iOS versions)
The lockdown files timeframe is limited to 30 days for iOS 11-13, according to Apple Platform Security (use the following page if direct link to PDF will accidently stop working). These files are extremely useful for advanced logical acquisition of locked devices, unless the USB restricted mode is activated (see Activating data connections securely chapter in the same document, and our USB Restricted Mode in iOS 13: Apple vs. GrayKey, Round Two article for less technical explanation and the description of all the consequences).
The future? Looks like we will be able to add agent-based extraction for iOS 13.3.1, 13.4 and 13.4.1 soon, as well as some legacy iOS versions (iOS 7 to iOS 10), at least the file system, but probably not the keychain. Just note that in order to use this feature, you need a Developer Account with Apple, though there is a chance that we will soon allow to sign our agent using just the usual disposable Apple ID.
Always extract the keychain if possible! It is actually a gold mine, often allowing iCloud acquisition (use Elcomsoft Phone Breaker for that; available for moth Windows and macOS).
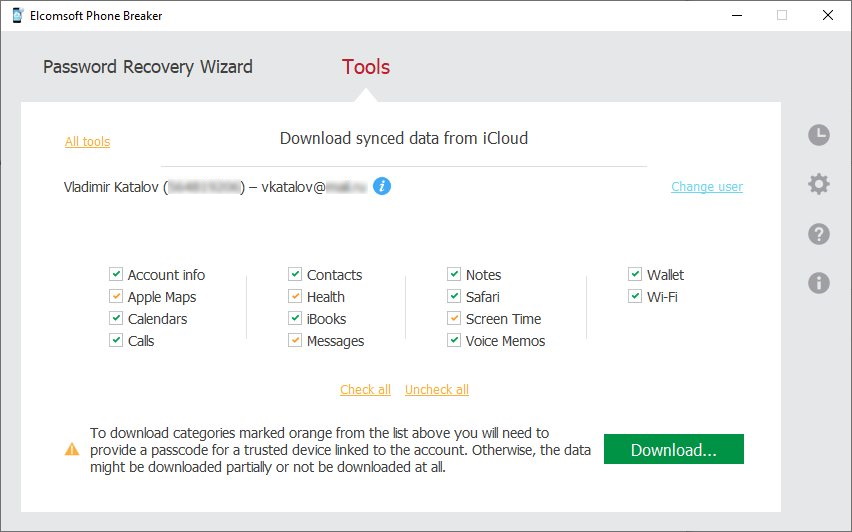
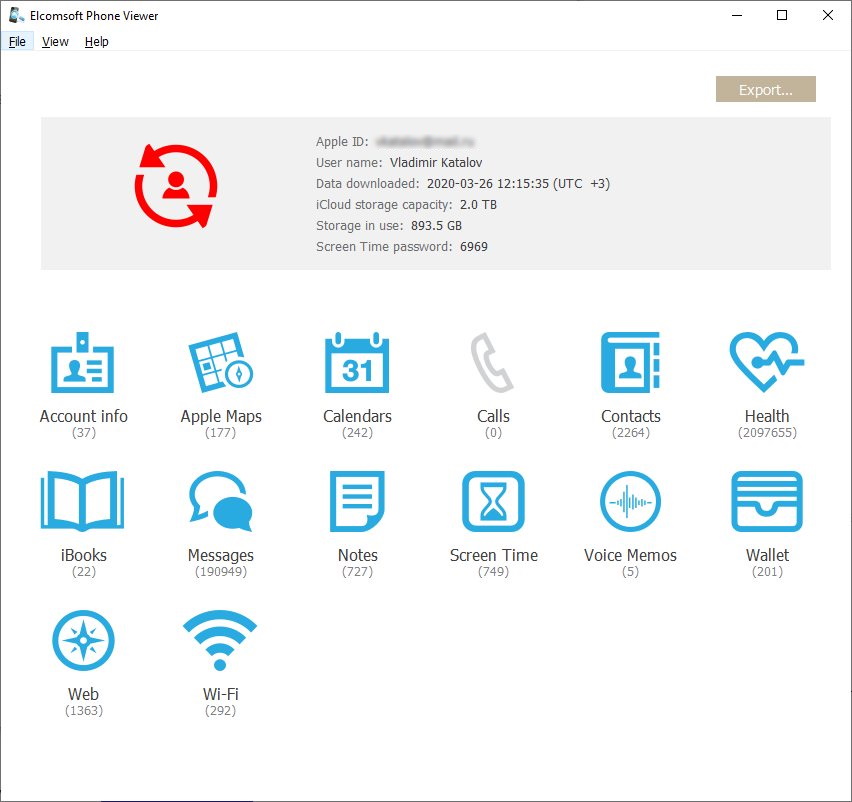
Then you will also need Elcomsoft Phone Viewer, the lightweight multi-platform forensic application to browse and analyze the data. The tool supports iTunes and iCloud backups, as well as full file system images and synced iCloud data:
Conclusion
iOS acquisition looks much simpler than Android acquisition, but that’s only at a first glance. Do not trust tools that do not provide the full, detailed explanation of how all of their features work, and hide everything under “method 1” and “method 2”, with a note like “if first method does not work, try the other one”. You need to understand how everything works, what data you can get, and (probably the most important!) what the consequences are.
EIFT, Elcomsoft iOS Forensic Toolkit, Elcomsoft Phone Breaker, Elcomsoft Phone Viewer, EPB, EPV, full file system, iTunes, logical acquisition, macOS 10.15, macOS Catalina





