Since iOS 5, Apple allows users to back up their phones and tablets automatically into their iCloud account. Initially, iCloud backups were similar in content to local (iTunes) backups without the password. However, the introduction of iCloud sync has changed the rules of the game. With more types of data synchronized through iCloud as opposed to being backed up, the content of iCloud backups gets slimmed down as synchronized information is excluded from cloud backups (but still present in local backups).
Two-factor authentication (or lack thereof) affects what can and what cannot be synchronized. Whether or not the device is enrolled to iCloud Keychain affects the ability to sync iCloud Messages, Health, and other information featuring Apple’s end-to-end encryption. Sounds confusing? You are not alone. Even experienced forensic experts can get confused with what is stored where and what they need to do to access it. Let’s shed some light on the types of data that might be available in iCloud backups and how they are affected by the optional data sync.
iCloud Sync
All current versions of iOS are offering seamless iCloud synchronization for many categories of data. Synchronizable data includes:
- Safari: browsing history, open tabs, bookmarks
- Contacts, notes, calendars
- Photos (iCloud Photo Library)
- Call history
- Wi-Fi access points and passwords
- Apple Wallet
- Account information
- iCloud Mail
- Books (iBooks), including PDF documents and third-party books added by the user
- Stocks, Weather
- Shortcuts
- iMovie, Clips
- Pages, Numbers, Keynote documents (part of iCloud Drive)
The following categories are synced with end-to-end encryption:
- Apple Maps (searches, routes, frequent locations) (end-to-end encrypted)
- iCloud Keychain (end-to-end encrypted)
- Messages (SMS, iMessages, attachments) (end-to-end encrypted)
- Apple Health (end-to-end encrypted)
- Screen Time (end-to-end encrypted)
- Home data (end-to-end encrypted)
- Voice memos (end-to-end encrypted)
Speaking of messages, they can be synced with iCloud since iOS 11.4. iMessages and text messages can be stored in the user’s iCloud account and synchronized across all of the user’s devices sharing the same Apple ID. This synchronization works in a similar manner to call logs, iCloud Photo Library or iCloud contacts sync (albeit with somewhat longer delays). However, Apple will not provide neither the messages themselves nor their attachments when fulfilling LE requests or GDPR pullouts. Why is this happening, how to extract messages from iCloud accounts and what kind of evidence we can find in attachments? More on that in a moment.
Apple mentions a slightly different set of synchronized data types that are protected with end-to-end encryption. According to Apple, these include:
- Apple Card transactions (requires iOS 12.4 or later)
- Home data
- Health data (requires iOS 12 or later)
- iCloud Keychain (includes all of your saved accounts and passwords)
- Maps Favorites, Collections and search history (requires iOS 13 or later)
- Memoji (requires iOS 12.1 or later)
- Payment information
- QuickType Keyboard learned vocabulary (requires iOS 11 or later)
- Safari History and iCloud Tabs (requires iOS 13 or later)
- Screen Time
- Siri information
- Wi-Fi passwords
- W1 and H1 Bluetooth keys (requires iOS 13 or later)
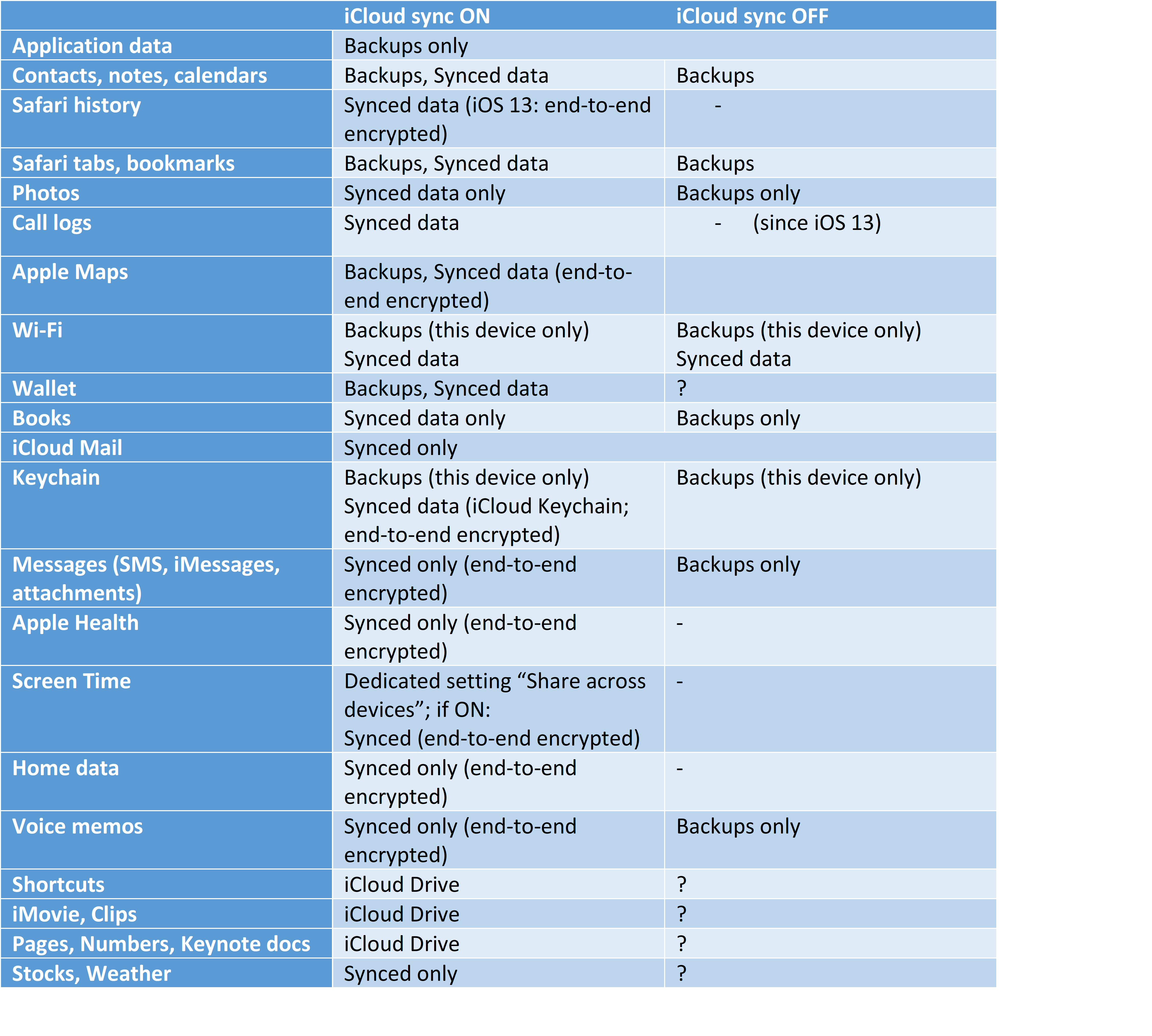
iCloud Backups
iCloud backups are created automatically on a daily basis if the device is connected to a known Wi-Fi network and left on a charger with its screen locked. The device must be unlocked at least once after first boot or restart.
iCloud backups are similar in content to local (iTunes) backups without a password. However, they will not include certain types of data, and will exclude many types of information if iCloud sync is enabled.
We built the following cheat sheet to show what types of data are included in iCloud backups with and without iCloud sync enabled for a particular data category. Note: the table reflects the current state of affairs (iOS 13.5.1); please refer to iOS 13 (Beta) Forensics for information on what has changed in iOS 13 since previous iOS releases.
Some information is protected with what Apple calls “end-to-end encryption”. What exactly does end-to-end encryption mean? Let us look at how Apple protects data in iCloud.
iCloud Security
There are several layers of security protecting your iCloud account. The content of iCloud backups is split into small chunks that are stored at Amazon, Microsoft, AT&T and even Google servers. However, neither company has access to the content of iCloud backups. Here is what other security experts have to say about this matter.
“Data stored on Google may include contacts, calendars, photos, videos, documents and more, but Apple is keen to stress that Google has no means of accessing that data”, writes Ben Lovejoy from 9to5mac.
“Each file is broken into chunks and encrypted by iCloud using AES-128 and a key derived from each chunk’s contents that utilizes SHA-256. The keys and the file’s metadata are stored by Apple in the user’s iCloud account. The encrypted chunks of the file are stored, without any user-identifying information, using third-party storage services, such as S3 and Google Cloud Platform.”
“All Google would see is meaningless encrypted data, with no way to tie even that to any particular individual. Apple doesn’t go into specifics about its use of third-party servers, so it’s possible that the same user data is spread across more than one platform”, he continues.
As a result of this security policy, Apple is the sole party to have access to encryption keys. These keys, however, are readily available to anyone who knows the user’s Apple ID and password and uses Elcomsoft Phone Breaker or similar forensic tool.
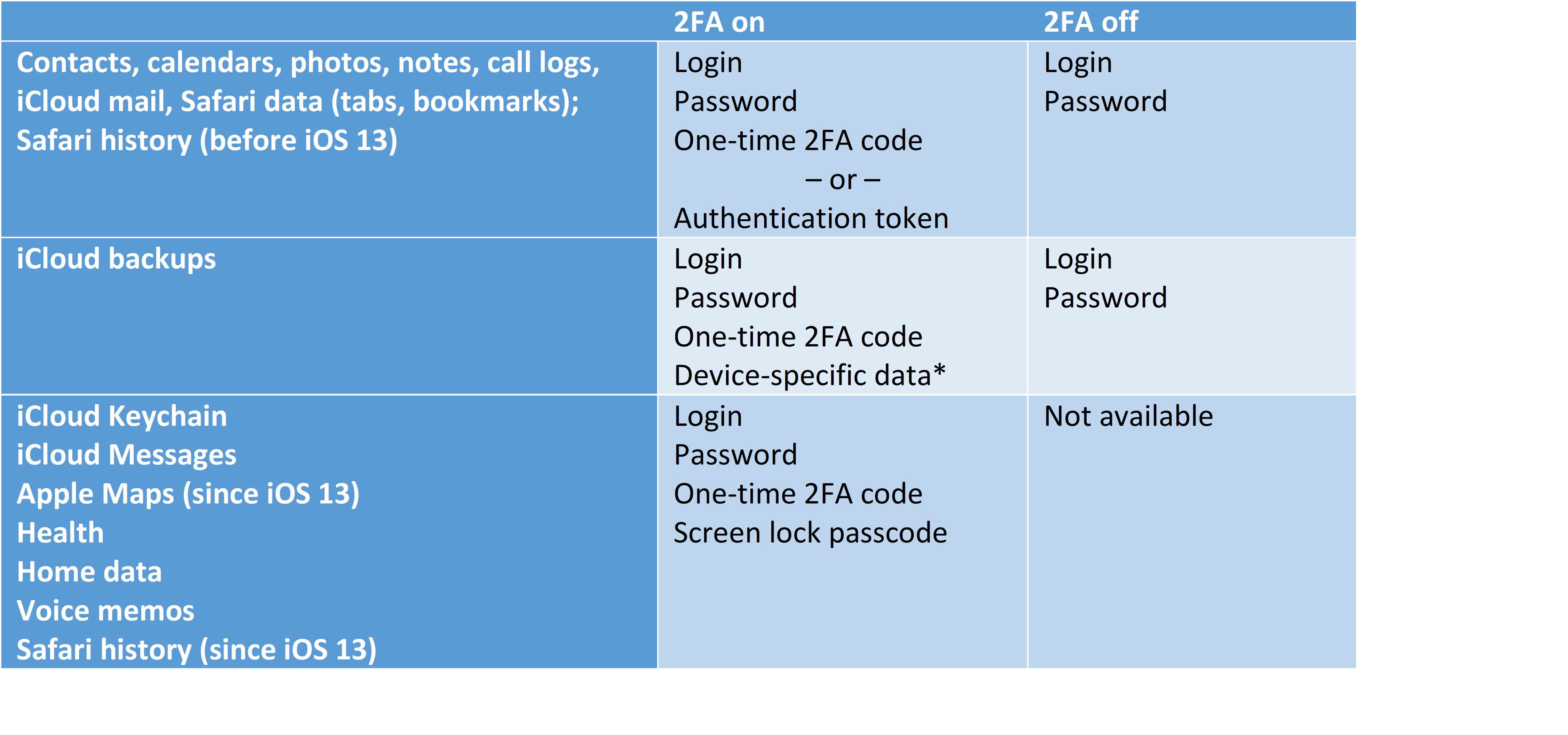
To make unauthorized third-party access more difficult, Apple introduced Two-Step Verification that was replaced by Two-Factor Authentication later on. Two-Factor Authentication requires the use of a one-time code that could be pushed to a connected and trusted Apple device, generated on one of the trusted devices in offline mode, or sent as a text message (SMS) to a trusted phone number (read why it’s insecure in Apple Two-Factor Authentication: SMS vs. Trusted Devices). If one has access to such a trusted device or SIM card, passing 2FA is not very difficult.
Some types of data have stronger protection. Users can only store passwords, encryption keys and other sensitive information such as Health and Messages in the cloud if they enable Two-Factor Authentication. These types of data are additionally encrypted (on top of the “normal” iCloud encryption) with a key that is re-encrypted with the user’s device passcode (or multiple passcodes if there are several devices with different passcodes). Since Apple does not know the user’s device passcode, it does not have access to the user’s passwords or messages. Apple refers to this protection scheme as “end-to-end encryption”.
Based on this information, we created a cheat card on what is required to access certain types of synchronized data.
 A word on device-specific data*: a special type of digital signature is required when accessing iCloud backups. If you restore an iCloud backup onto a genuine Apple device, this digital signature is seamlessly generated by the device itself. However, if you use third-party software such as Elcomsoft Phone Breaker to download iCloud backups, a workaround must be used to produce a digital signature that can be successfully validated by Apple servers. We’ve implemented such a workaround in Elcomsoft Phone Breaker.
A word on device-specific data*: a special type of digital signature is required when accessing iCloud backups. If you restore an iCloud backup onto a genuine Apple device, this digital signature is seamlessly generated by the device itself. However, if you use third-party software such as Elcomsoft Phone Breaker to download iCloud backups, a workaround must be used to produce a digital signature that can be successfully validated by Apple servers. We’ve implemented such a workaround in Elcomsoft Phone Breaker.
iCloud Keychain and other end-to-end encrypted categories
The keychain is one of the core and most secure components of macOS, iOS and its derivatives such as watchOS and tvOS. Its cloud version, the iCloud Keychain, is Apple’s best protected vault. End users are mostly familiar with a particular feature of the keychain: the ability to store all kinds of passwords. This includes passwords to Web sites (Safari and third-party Web browsers), mail accounts, social networks, instant messengers, bank accounts and just about everything else. Some records (such as Wi-Fi passwords) are “system-wide”, while other records can be only accessed by their respective apps. However, the role of the keychain is not limited to a password manager. In addition to storing the user’s passwords, the keychain also protects authentication tokens, credit card data and a lot more, including the encryption keys for other types of end-to-end encrypted data (such as Health, iCloud Messages, Screen Time password etc.) In other words, one must decrypt the iCloud Keychain before attempting to access any other data category protected with end-to-end encryption.
Since iCloud Keychain keeps the user’s most sensitive information, it’s protected in every way possible. By breaking in to the user’s iCloud Keychain, an intruder could immediately take control over the user’s online and social network accounts, profiles and identities, access their chats and conversations, and even obtain copies of personal identity numbers and credit card data. All that information is securely safeguarded.
Elcomsoft Phone Breaker extracts the iCloud Keychain and other data types employing end-to-end encryption by adding the tool into the trusted circle. This in turn requires entering a screen lock password (device passcode) or system password (macOS computers) of one of the user’s devices that are already enrolled. You will need all four of the following in order to access end-to-end encrypted data:
- Apple ID (the login)
- Apple ID password
- One-time two-factor authentication code (push, SMS or TOTP)
- Screen lock password or system password of an already enrolled device
More information
Please check out the following articles for more information:
Conclusion
Information in Apple iCloud is indeed encrypted. For many types of data such as iCloud Photos or Safari browsing history, Apple makes use of simple encryption with cryptographic keys stored alongside main data. iCloud Keychain, Messages, Health and Home data, Screen Time and some other types of information are protected with end-to-end encryption with an additional key. Accessing end-to-end encrypted data requires user’s screen lock passcode or system password (for Mac computers) of an already enrolled device. If multiple devices are registered on the same Apple account and enrolled in iCloud Keychain, one can use a passcode (or system password) from any of those devices to access that key.
Apple continues to shift information away from iCloud backups, opting to synchronize those types of data instead. Some types of data (e.g. contacts, calendars, notes) will remain in iCloud backups even if they sync to iCloud. If the user enables iCloud sync for certain other categories (e.g. Photos, Books, Messages), they will not be included in iCloud backups. Finally, Health information is never included in iCloud backups, while Keychain is backed up with “this device only” attribute.
There are complex dependencies between iCloud synchronization, version of iOS, and whether or not Two-Factor Authentication is enabled. We tried to review those dependencies, and sum them up in a table.




