We have published multiple articles on iPhone backup passwords already, covering the different aspects of the backup protection. In this publication, we have collected the most important information about the things you can do under different circumstances, some software recommendations, and some other practical tips and tricks, in a brief and simple form.
The possible scenarios
There are two typical scenarios when you may be affected by iTunes backup passwords.
If you are a forensic expert, you may encounter the situation when the suspect’s iPhone is unlocked (the passcode is not set or is known), but the backup password is enabled, and your favorite forensic tool (whatever it is) prompts you for that password, offers you to crack it (do not do that just yet, until you’ve read the whole article), or warns that only a limited amount of data will be extracted.
If you are an iPhone user, you may need to transfer the data from one iPhone to another, e.g. when upgrading your device. And if you have set the password a long time ago and have successfully forgotten it, then you will not be able to restore from the backup. Your other option would be the cloud backup, but this option is not the best due to multiple reasons that are outside the scope of this article.
We recommend that you start reading from the About encrypted backups on your iPhone, iPad, or iPod touch article, and we can also recommend The Most Unusual Things about iPhone Backups with some deep inside information, but if you need a more practical manual, here we go.
Extract it
Nothing could be better than the original password, right? The good news are that if you are a Mac user (or working as an expert, have access not just to the iPhone but also to the Mac), there is a very good chance that backup password is stored in the macOS keychain. All you need is the password to that Mac, that’s it. Windows? No way, sorry.
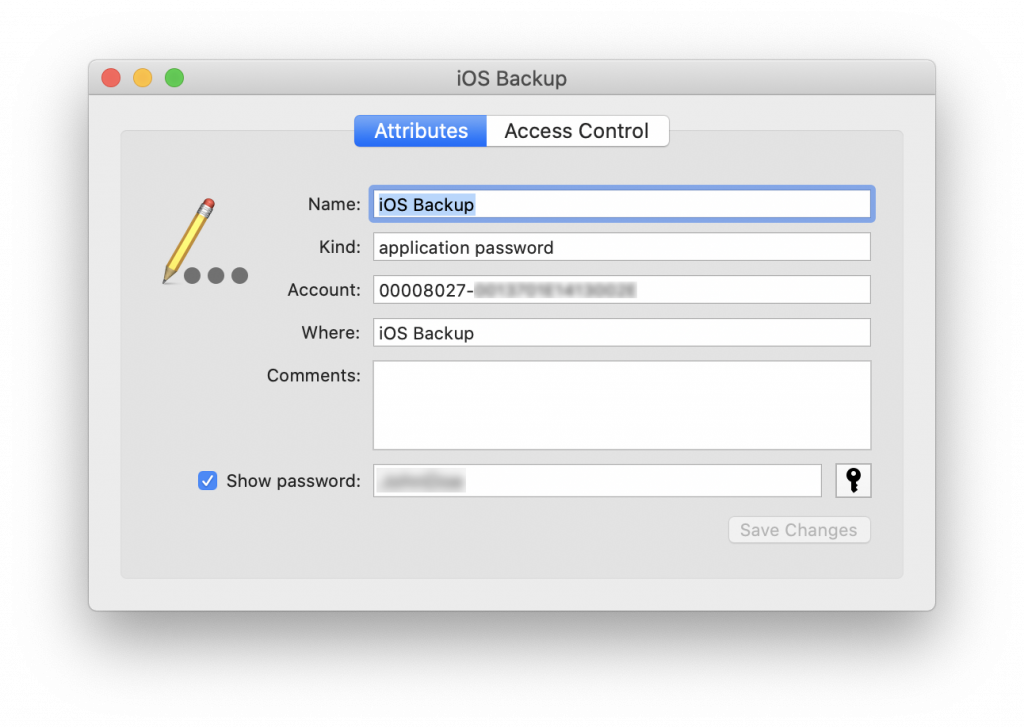
Software required: Keychain Acccess (free; built-in macOS utility)
Break it
Password cracking is one the topics where we have a very good experience with, and sometimes the backup password can be broken. This was relatively simple to do in iOS 9 and below; in iOS 10.2 and above, however, the cracking is effective only if the password is very short or very simple, or if you know (remember) a part of the password or its pattern, or have a very good wordlist. Otherwise, it may take years to crack the password, even on a supercomputer.
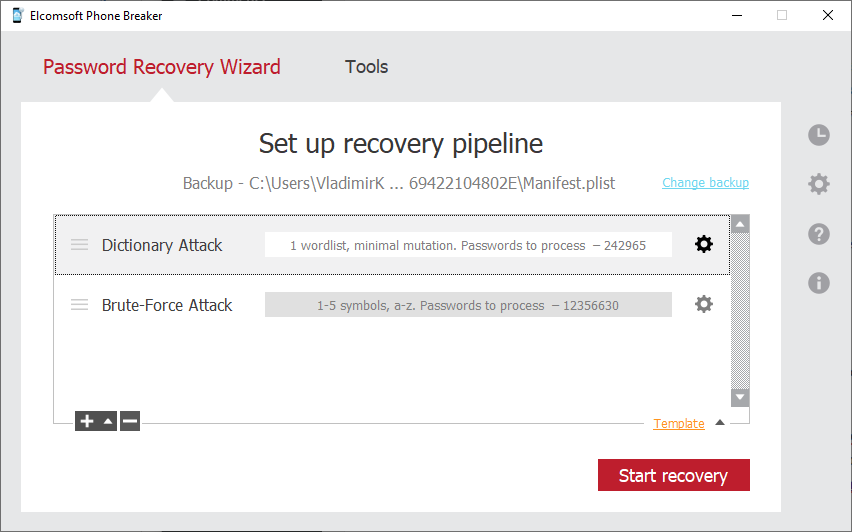
Software required: hashcat (free) or Elcomsoft Phone Breaker
Reset it
iOS 11 introduced the ability to simply reset backup password. This option is still available in iOS 13 and the current betas of iOS 14, so it’s likely it is there to stay. The steps are quite simple (as described in Apple’s HT205220 mentioned above):
- On the iPhone, go to [Settings] | [General] | [Reset]
- Press [Reset All Settings];
- Follow the steps (you will be prompted for device passcode)
Some settings will be reset, and the backup password will be removed. You can now connect the device to the computer and create a new unencrypted backup, or (recommended) set a new password without entering the old one.
The devil is in the details. The main problem is that the device passcode is also removed, and that may be fatal, especially if you are working not with your own data but investigating an incident as a forensic expert. More information in iOS 11 Horror Story: the Rise and Fall of iOS Security and Protecting Your Data and Apple Account If They Know Your iPhone Passcode. In short, do not do it until it remains the only option and you are out of other solutions.
Software required: none
Ignore it
Yes, sometimes you do not actually need to recover, reset or break the backup password, as surprising as it may sound.
First, if you only need to get access to the media files (photos and videos) from the iPhone, then the backup password does not really matter. You can extract the pictures and videos whether the password is set or not. We often receive requests from home users (and even from friends) looking for help to extract just the family photos; quite often the photos (with geolocation data) are also all that is needed for forensic experts, especially when they are very short in time and will not bother with password reset or recovery.
Second, for selected iPhone models and iOS versions (currently, up to iOS 13.5 on iPhone Xr/Xs/11, and for all iOS versions on older models), you can get significantly more data than included in backups, and no backup password is required for that. The data is extracted as a file system image (not in the standard backup format), and it cannot be used to restore another device . But who cares if the data is all you are after? As the Russian proverb says, “do you need a license or a ride?”
Last but not least, sometimes (basically, at the same conditions as above, while there are some notable nuances) you can also extract the original backup password from the device itself (from its keychain), in addition to the file system image. It’s hard to say whether it adds some value to file system extraction (as it is more complete than a backup), but sometimes you can use this password to extract the data from an older backup that may contain some deleted files.
Software required: Elcomsoft iOS Forensic Toolkit
Conclusion
As you can see, several options exist, and it is very rare when none of them are available. However, you should carefully review the possibilities, understand their consequences, and weigh the risks to select the safest and most effective method for your particular case.




