This publication is somewhat unusual. ElcomSoft does not need an introduction as a forensic vendor. We routinely publish information on how to break into the phone, gain access to information and extract as much evidence as theoretically possible using hacks (jailbreaks) or little known but legitimate workarounds. We teach and train forensic experts on how to extract and decrypt information, how to download information from iCloud with or without the password, how to bypass two-factor authentication and how their iPhone falls your complete victim if you know its passcode.
This time around we’ll be playing devil’s advocate. We’ll tell you how to defend your data and your Apple account if they have your iPhone and know your passcode.
iOS Devices Are Secure
We praised the iOS security model on multiple occasions. Speaking of the current pack of iOS versions (including iOS 11.4 release, 11.4.1 public beta and 12.0 first developer beta), we have full-disk encryption with decryption keys derived from the user’s passcode and protected by Secure Enclave. Thanks to the iOS keychain, we enjoy the additional layer of protection for our passwords and other sensitive information. If you protected your iPhone with a 6-digit passcode (which you really should, and which is the default since at least iOS 10), most of your information is securely encrypted until you first unlock your iPhone after it completes the boot sequence. Even if they take the memory chip off, they won’t get anything meaningful due to the encryption.
Starting with iOS 11.4.1 beta, Apple went an extra mile in an attempt to protect your iPhone against attackers trying to brute force your passcode. The newly implemented USB Restricted Mode disables the USB port on your iPhone one hour after you last unlocked the device (fingerprint, Face ID or passcode) or one hour after you disconnected it from a trusted USB accessory. Even if someone gets your iPhone, they’ll have to start brute forcing your passcode within one hour – or they won’t be able to start it at all.
iOS Backups Are Even More Secure
iOS has an exemplary backup system. Local backups made with iTunes can be protected with a password. The encryption of iTunes backups (in iOS 10.2 and up) is so strong that even the most powerful computer equipped with a high-end GPU accelerator can only try about 100 passwords per second. With this kind of security, breaking a reasonably strong 7-character password (that’s not made of dictionary words) would take a thousand years to break. Should you have reasons to believe that your data is of special interest to the third parties, you could use well more than the 7 characters to make up your password to choke even a network of 10,000 units.
But All of That Doesn’t Really Matter
The iOS devices are really secure, and iTunes backups are even more secure, so everything is good, right? Not really. All of that security doesn’t really matter if they know your passcode.
If they get to know your passcode (and you might just tell them if they ask nicely), they can do all of the following:
- Disable Find my iPhone and remove Activation Lock
- Enable two-factor authentication if it was not enabled (good luck passing that on your other devices)
- Change your Apple ID and iCloud password and, with that password, pull your iCloud backups, extract all your passwords (iCloud Keychain) and your synchronized data (such as your Safari browsing history) not just from your device but from all devices registered on your Apple ID account
- Yes, that includes all of your photos – including those taken with other devices, if you’re using iCloud Photo Library (if not, just the locally stored photos and videos)
- Lock or erase your other devices on the same Apple ID (yes, just like that)
- Reset your iTunes backup password, pair your phone with their computer and pull a local backup
- Extract all your saved passwords (from the local or iCloud keychain, or both)
Some of that is only possible in iOS 11. So if you hesitated to update your phone and are still on iOS 10 or earlier, you must be good? Surprise: using your passcode, they can easily update your phone (if it’s a 5s or newer) to iOS 11, and then do anything and everything listed above.
Don’t believe us? Try it yourself (hopefully, on your own device)! All the steps, with pictures, are clearly described in the following article: iOS 11 Horror Story: the Rise and Fall of iOS Security
From Multi-Layer Protection to Just the Passcode
iOS 11 was a turning point for Apple. The company brutally switched from the balanced, multi-layer security mechanism to a new scheme with a single guarded point of entry. The passcode is currently all that stands between your data and whoever possesses your iPhone.
With a bounty that high, it is only logical to expect everyone, including the law enforcement and forensic vendors, to try and break the passcode.
Cellebrite and GrayShift independently offered solutions aimed at the law enforcement. Their solutions try brute-forcing iOS devices passcodes. If your phone was unlocked at least once after its last reboot, they can crack your passcode amazingly fast. GrayShift are claiming under 30 minutes for a 4-digit passcode or about 2 days for a 6-digit one (with limitations). If they get your iPhone in a powered-off state, they’ll struggle with being able to only try one passcode every 10 minutes, meaning it would take them some 70 days to break a 4-digit passcode.
This is far from being bullet-proof. For Apple, the situation was unacceptable, yet the company seemed to be unable to completely shut the exploit (whatever it is) both forensic firms are using. Did they think of bringing back the missing security layers? Not at all; they just kept trying to bulletproof the only protection measure still standing. They came up with the idea of shutting off the data port after a period of idling to ensure that no passcode cracking solution would work.
Passcode Protection Gets Stronger Protection
The idea behind USB Restricted Mode was pretty ingenious. The feature, apparently targeting forensic passcode cracking tools, disables any and all USB data communications from occurring over the Lightning port of your device one hour after the device has been last unlocked or connected to a trusted accessory. Once the user toggles the “USB Accessories” switch into the “Off” position (which, by the way, is how it’s configured out of the box), the iPhone will start prompting you to “Unlock iPhone to allow USB accessories to connect when it has been more than an hour since your iPhone was locked”.
This behavior is different in iOS 11.0 through 11.4, iOS 11.4.1 and iOS 12.
iOS 11.0 – 11.4 implement a toned-down version of USB Restricted Mode. In these versions of iOS, one would have to unlock the iPhone with Touch ID/Face ID/passcode after 24 hours since the phone was last unlocked. After 48 hours, the phone would have to be unlocked with a passcode only. In these versions of iOS, the USB port would still allow transmitting some data, at very least communicating that the phone must be unlocked in order to enable full data communications. While this implementation of USB restrictions can effectively prevent logical acquisition using existing pairing records (lockdown files), it did exactly nothing to stop solutions such as GrayKey from breaking your passcode. Notably, the “proper” USB Restricted Mode, the one that would completely shut down all data communications between the iOS device and the computer, was still missing in iOS 11.4.
iOS 11.4.1 includes a fully featured but undocumented implementation of USB Restricted Mode. This version of iOS comes with the new “USB Accessories” switch. By default, the iPhone will require you to “Unlock iPhone to allow USB accessories to connect when it has been more than an hour since your iPhone was locked”. (Notably, it is the “off” position of the switch that enables USB Restricted Mode, which is the default value).
iOS 12 beta also includes this switch; this time, the feature is properly documented in the Release Notes. However, we discovered that the implementation of this feature is slightly different between iOS 11.4.1 and iOS 12 beta. There are enough differences to say that iOS 12 is somewhat less protected compared to iOS 11.4.1, but since we only have the first developer beta of iOS 12, it’s too early to comment. The final implementation may change radically.
So what happens if someone gets your iPhone and tries to break in? Without proper equipment (such as GrayKey), they’ll be doing it manually. If they do, Secure Enclave will enforce a 80ms delay between attempts, somewhat limiting the speed of recovery.
In addition, iOS will introduce an increasing delay after each unsuccessful attempt. After 10 unsuccessful attempts your phone will be either blocked or erased (if you specified the corresponding option in the iPhone settings). Once again, this behavior is controlled by the system (iOS) and not by the hardware (Secure Enclave).
We tried several devices running iOS 11.4.1 beta and 12.0 beta, and noticed some differences.
iOS 11.4.1 will progressively increase the delay between unsuccessful attempts.
- 5 attempts: 1 minute
- 6 attempts: 5 minutes
- 7 attempts: 15 minutes
- 8 attempts: 15 minutes
- 9 attempts: 1 hour
- 10 attempts: 1 hour
- 11 attempts: Erase data or “iPhone is disabled”
iOS 12:
- 5 attempts: 1 minute
- 6 attempts: 5 minutes
- 7 attempts: 15 minutes
- 8 attempts: 15 minutes
- 9 attempts: 1 hour
- 10 attempts: 1 hour
- Erase data or “iPhone is disabled”
We then repeated the test with two devices, one running iOS 10 and one running iOS 12 beta 1. We’ve got the following results:
- 10:11 no delay (first attempt with incorrect passcode)
- 10:13 no delay
- 10:16 no delay
- 10:18 no delay
- 10:20 1 minute
- 10:24 5 minutes
- 10:31 15 minutes
- 10:49 15 minutes
- 11:07 1 hour
- 12:20 – iOS 10 device was unlocked with the correct passcode (couldn’t afford losing the jailbreak); iOS 12 still 1 hour
- 13:30 – iOS 12 device was finally disabled. Powered off and on again; the computer does not see the phone (the USB port is disabled)
As you can see, you’ll face a one hour delay before the last one or two attempts, after which the iPhone will become disabled.
It is very interesting to note that Apple has these numbers wrong in their official documentation.
In https://support.apple.com/en-gb/ht204306, Apple states:
“If you enter the wrong passcode on an iOS device six times in a row, you’ll be locked out and a message will say that your device is disabled.”
We have not been able to confirm the number of failed attempts being “six times in a row”. In our tests, the delay occurs after entering the wrong passcode 5 times in a row, after which we experience a progressively increasing delay. Why Apple put the wrong number in the official documentation is beyond us.
Now, what exactly happens once the iPhone is “disabled” (assuming you didn’t enable the “Erase after 10 unsuccessful attempts” option)? In iOS 11.4.1, if at least one hour has passed since the last successful unlock, the iPhone will disable all data communications over its Lightning port (USB Restricted Mode). Even if the phone displays a message instructing you to connect it to iTunes to unblock, doing so will result in exactly nothing. With data port disabled, you’ll see zero communications between the phone and iTunes. The same happens in iOS 12.
What if you genuinely forget your own passcode and are caught hands down with a blocked iPhone? Before iOS 11.4.1, you could connect it to iTunes to perform a factory reset, and then set it up, possibly restoring from the backup; Activation Lock would require entering your iCloud credentials to activate the device.
In iOS 11.4.1 and iOS 12 beta, this is no longer an option. If you connect the blocked iPhone to iTunes, there will be still zero data communicated over the USB port. You must boot your iPhone into Recovery mode, and only then will iTunes “see” the iPhone. We tried “updating” the iPhone without erasing data; the update (to the same version of iOS 11.4.1) was successful, but the phone remained in the blocked state. We had to do the “restore” operation, losing all data, to regain control over the device. On the one hand, this is a major inconvenience; on the other hand, this is exactly the type of behavior we wanted to see for preventing forensic unlocks with GrayKey and similar software (another question is, if it really does prevent such unlocks). Another way to reset your iPhone at this point would be switching it into DFU mode, connecting to iTunes and re-flashing firmware.
iOS Restrictions Give an Extra Protection Layer
There is very little you can do about forensic unlocks aside of relying on Apple’s USB Restricted Mode and using a stronger passcode (6 digits an absolute minimum, alphanumerical passwords not based on dictionary words recommended). However, you can add an extra protection layer to block at least the most trivial acquisition attempts based on resetting your iTunes backup password.
Using Restrictions to Block Backup Password Reset
First and foremost, once you enable Restrictions and choose a 4-digit PIN, no one will be able to reset your backup password via the “Reset All Settings” process. Using the “Reset All Settings” command, they will be first prompted for your passcode. If they provide the correct passcode, on the next step they’ll have to enter your Restrictions password (the 4-digit PIN). Considering that it is much, much easier to record your passcode than it is to obtain your rarely used Restrictions password, you can consider your backup password to be reasonably safe against resets.
Your Passwords Are Belong To Us: Your Entire Apple Account May Fall Victim
As we demonstrated, anyone who has physical access to your iPhone and knows your passcode can change your Apple ID/iCloud password, disable or erase your other devices, turn off Activation Lock (Find My iPhone), and download your photos, backups, passwords and synced items (such as iMessages) from iCloud. All that is based on their ability to view of change your iCloud password. Did you know that your Apple ID/iCloud password may be stored in the Keychain? Well, here is one (no worries, it’s not my real password):
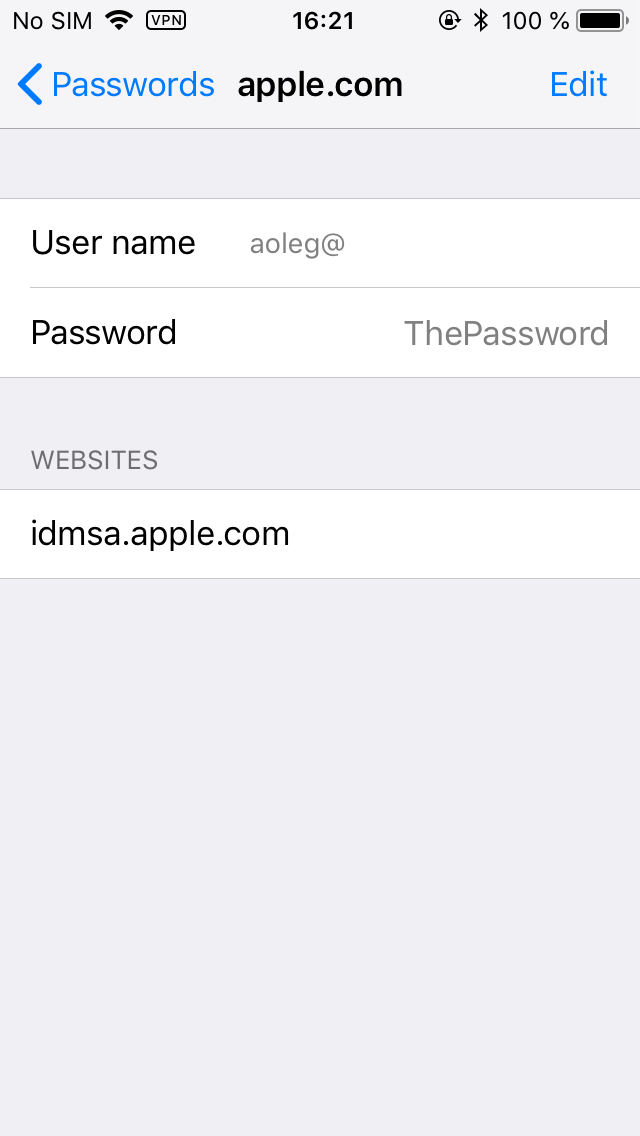
How did we get there? Settings > Accounts & Passwords > App & Website Passwords. Once you are there, tap App & Website Passwords. You will be prompted for Touch ID.
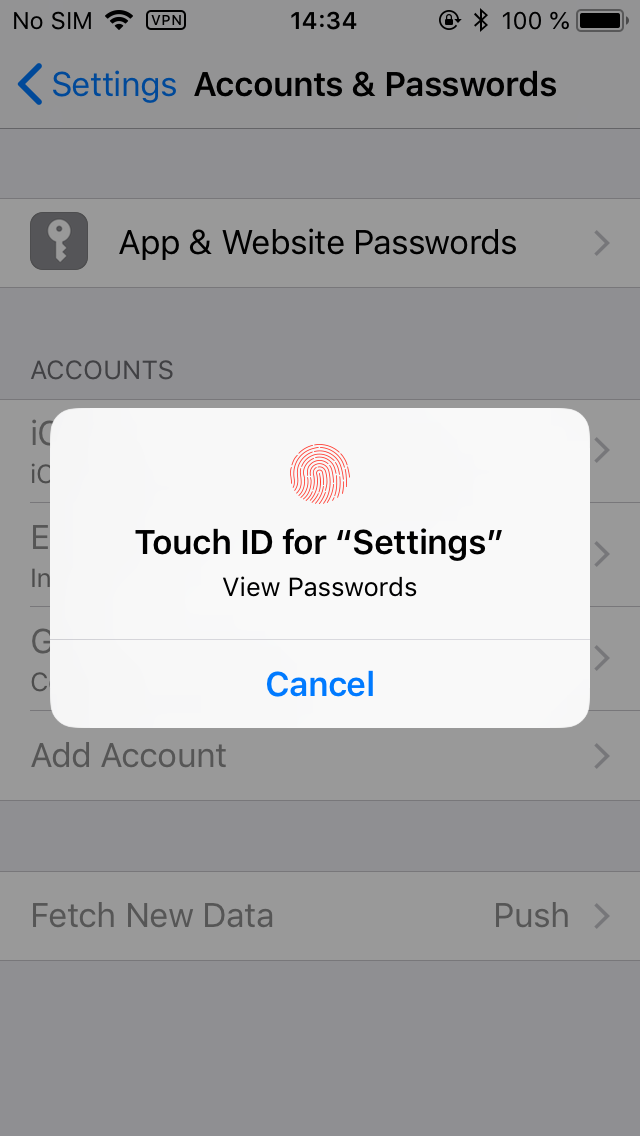
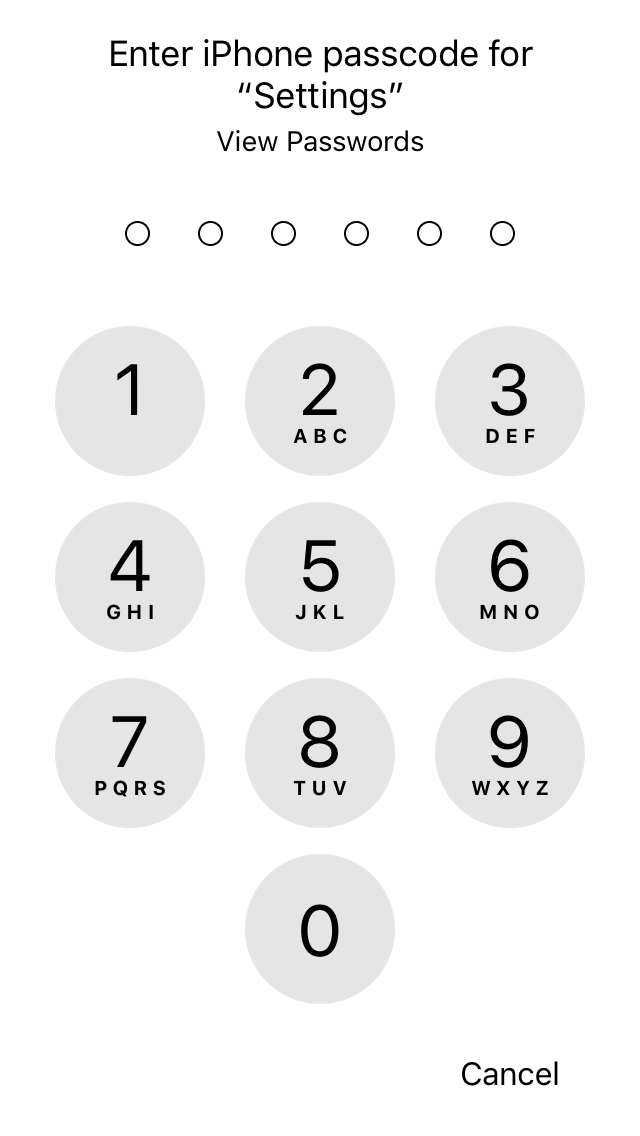
If the Touch ID sensor fails to recognize your finger several times, you will be prompted for the passcode.
Once you are there, you can view all account passwords one after another, or long tap on any item to copy the password.
As far as we know, there is no protection against this attack for unmanaged devices. Whoever has your iPhone and your passcode will also have unrestricted access to your stored passwords.
Using Restrictions to Prevent Changes to Your Apple Account and Activation Lock Status
You can set Restrictions to protect your device from on-device account changes such as deactivating Find my iPhone or changing your Apple ID password. To do that, you’ll need to activate the Accounts restriction:
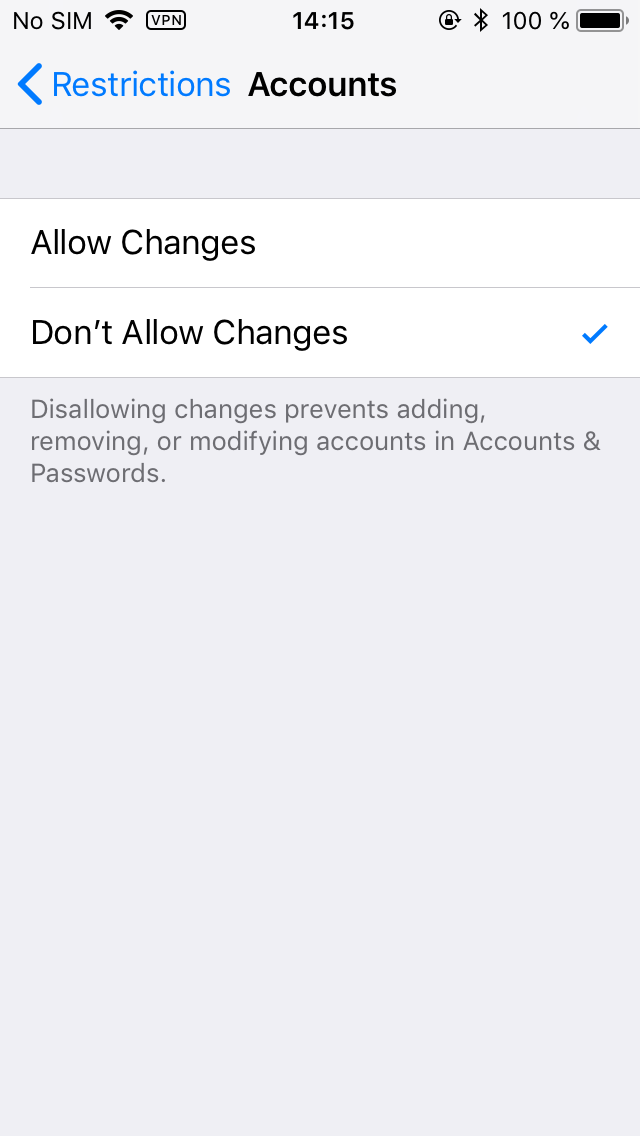
Once you do that, no one will be able to modify your accounts. They’ll simply be greyed out until the moment the corresponding Restriction is lifted:
Do note that this serves more against someone who randomly gets your iPhone in their hands, who does not have much time and experience. As demonstrated, Apple ID/iCloud passwords can be obtained from other places such as Accounts & Passwords. For whatever reason, there does not appear to be a restriction to protect those passwords against curious eyes.
Can Restrictions Protect Against a Jailbreak?
In today’s mobile forensics, extracting the content of the device can be performed with the help of a jailbreak. This is probably a more dangerous thing compared to even GrayShift. While GrayShift sells its products exclusively to law enforcement in few select countries, pretty much everyone can jailbreak your device using a public jailbreak (of course, if one exists for your combination of hardware and iOS version). Later on, the intruder can use SSH to image the file system of your device. While currently a public jailbreak only exists for versions of up to iOS 11.1.2, we’re closely watching the progress of iOS 11.3.1 jailbreak, which may be released very soon.
Can you proof your phone against a jailbreak? While GrayShift loads unpublished exploits directly onto an iPhone, public jailbreaks operate in a very different manner. All public jailbreaks released for iOS 10 and 11 require sideloading (installing) a signed IPA file onto your device. Once the jailbreak tool is installed and its certificate is confirmed (trusted) from the settings, the tool can be launched to jailbreak your device.
The only thing Restrictions can do to prevent this scenario is disallowing the Installing Apps permission:
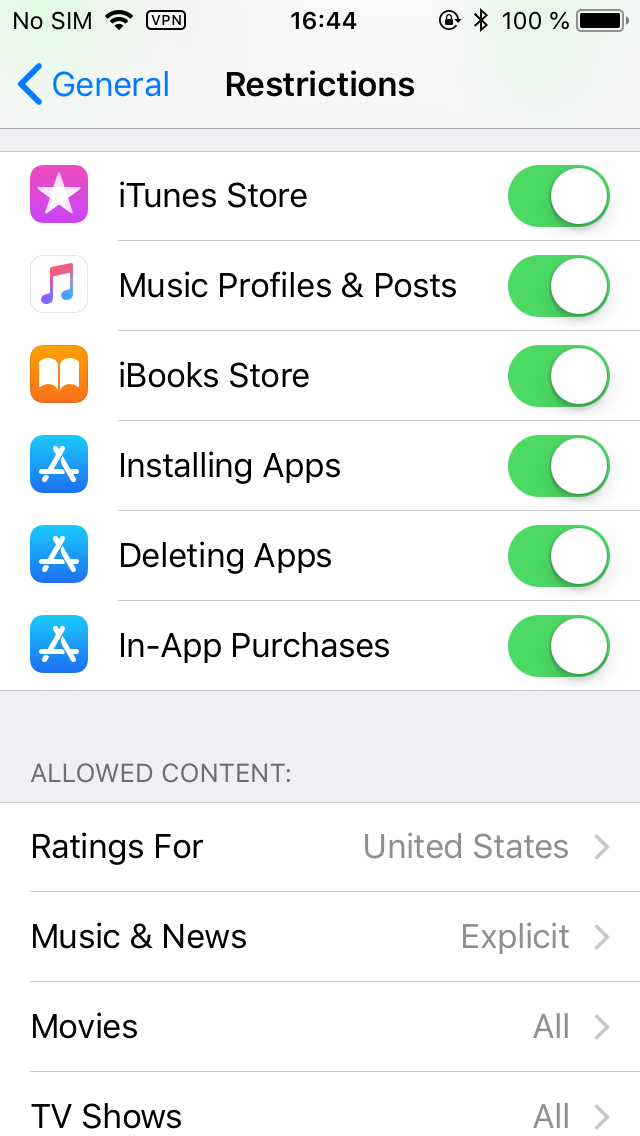
However, this would be a major inconvenience for many users, so I don’t see many users actually using this feature (unless they want it for other reasons).
How Secure Are Restrictions?
You can only use a 4-digit PIN as your Restrictions password. This makes only 10,000 combinations. An inexpensive PIN recovery box with customized delays can be theoretically used to attack your Restrictions password.
iOS has a progressively increasing delay between unsuccessful attempts. There is no limit on the number of attempts; the iPhone will not be locked, and the data will not be erased. As a result, consider Restrictions password to be no more secure than the time required to try all 10,000 combinations.
The delays between unsuccessful attempts to break Restrictions passcode will progressively increase to 1, 5, 15, and 60 minutes. After 10 unsuccessful attempts, there will be 60 minutes before another attempt is allowed.
With 1 attempt per hour, it takes 10,000 hours, or about 416 days, to try all possible combinations of the Restrictions password. While this is probably enough to protect non-classified information, it’s still significantly less secure compared to a strong, random password protecting your iTunes backups. From purely security standpoint, we believe that Restrictions are not a strong enough alternative to not being able to reset the backup password at all.
Restrictions have no effect on and cannot protect you against passcode recovery tools such as GrayKey.
Protecting Your Data When Crossing the Border
In some jurisdictions such as the United States, you may be forced to unlock your iPhone when entering the country. While you have the right to refuse, you will be detained indefinitely until you agree to comply. No, this does not happen to “alien” persons, and no, it does not only happen to “foreigners”: A US-born NASA scientist was detained at the border until he unlocked his phone. The rational thing to do is complying with the request (or you will be detained until you comply), possibly first asking to make a written note that you disagree to such a search and comply unwillingly.
What can happen to your unlocked iPhone once they take it away? While manual search is a possibility, there is a chance that border officials will simply connect your phone to their computer and perform logical acquisition, pulling your photos and shared files and making a backup that will, in turn, contain all your browser and account passwords stored in the keycnain.
In iOS 11, Apple attempted to address this very situation, requiring anyone attempting to pair your iPhone with their computer to enter your passcode. Simply unlocking the iPhone is not enough to establish a new pairing relationship, which makes it impossible accessing photos or making backups on a computer (it doesn’t mean they can’t view your photos on the device though). However, you may be required to reveal your passcode (or be indefinitely detained), in which case the officials will be able to make a local backup, potentially accessing all passwords to all your accounts, social networks etc.
In previous versions of iOS, you could use iTunes to set a very long, completely random backup password to backup prior to traveling. You could print that password and leave it back home. If the password is long enough (and completely random), you would not be able to memorize it, and you would be able to explain it if asked for this password. In other words, even if they paired your iPhone and pulled the backup, they’d have to spend a million years attempting to break the password.
This changed in iOS 11. Apple now allows resetting backup passwords by tapping the “Reset All Settings” command and confirming it with your passcode. After it, one can easily make a new backup, and that backup (if they do it the right way and specify a temporary password) will contain pretty much everything including your passwords.
Enabling Restrictions effectively blocks the “Reset All Settings” command, adding an extra prompt for a 4-digit Restriction password. While it is true that you could be asked for this Restriction password (and would have to comply, or be detained indefinitely), you could ask another person (a family member?) to set this password for you without telling you what this password is.
Protecting Lockdown Records
Lockdown files (iTunes pairing records) extracted from your computer can be used to perform logical acquisition of your iPhone. GrayShift claim instant unlock for iPhone devices if a valid lockdown record is available. While USB Restricted Mode does put a restriction on the use lockdown records, it does not mean you shouldn’t protect them on your computer.
What can you do to protect lockdown records? The only thing you can do (and this is a very good thing) is enabling full-disk encryption. If you’re using Windows, enable BitLocker encryption; Mac users can use FileVault 2. While full-disk encryption is not a silver bullet (we have tools to instantly unlock encrypted partitions if you leave your computer powered on and tools to brute-force the password, and Microsoft Account passwords can be attacked and recovered, too), the use of encryption still helps securing stuff on your computer.
Conclusion
In this publication, we researched what Apple does to help you keep your data private, and what you can do to secure access to information on your iPhone. On the other side of the coin are forensic experts and law enforcement guys trying to break in to bad guys’ phones (like, really bad guys). At this time, there is no single technology that could be made to only protect the good guy and not the bad one. We do have a problem with “encryption backdoors” and “escrow keys” handed to law enforcement just in case simply because we believe the potential of their misuse greatly overcomes the potential benefit for society. However, there is no question that forensic experts will do everything possible to help law enforcement do their work. And this is a good thing.









