Location data is one of the most sensitive pieces of personal information. In today’s world, aggregated location data is as sensitive and as valuable as the user’s passwords. Once this data is transmitted to the OS manufacturer’s cloud service or any of the third-party vendors, the user has the right to know exactly what information is collected; who, when, and how has access to it. In today’s article, we will talk about one of the iOS lesser known features called “Significant locations”.
Significant Locations
The release of iOS 8 brought us “Frequent locations”, a feature well hidden in iOS settings ([Privacy] | [Location Services] | [System Services] | [Frequent Locations]). Apple does not describe in details how the location data is collected and analyzed, and what exactly counts as a “frequent” location.
From iOS 10 upwards, which includes iOS 14 beta, the feature is called “Significant Locations”. It is still accessible from the same menu item.
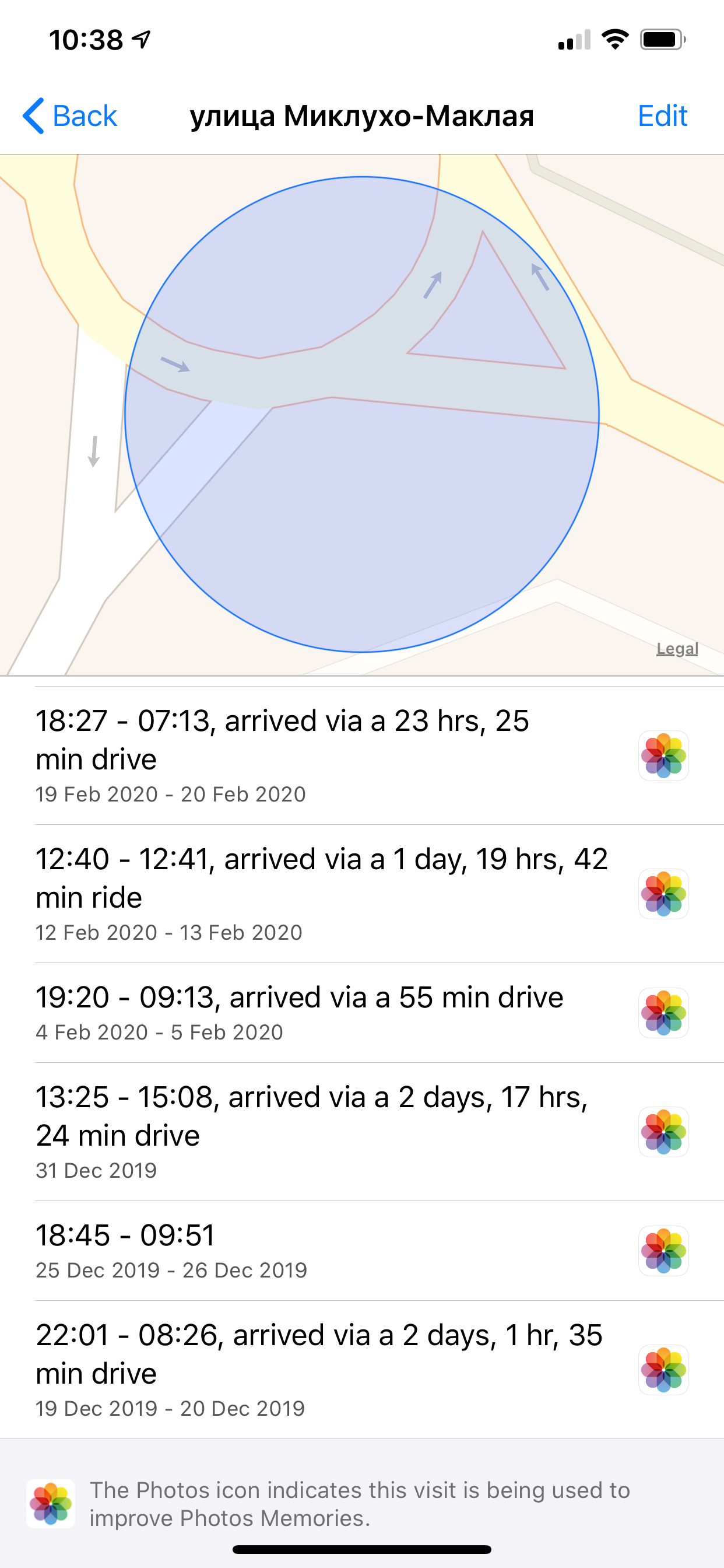
As you can see, the feature displays not only the exact timestamps, but also the means of transport that brought you there (currently it’s either “drive” or “walk”; never seen anything else), and the duration of that drive or walk.
The data collected used to always stay at your device only. It was never synced or included in iTunes or iCloud backups, so you could only extract it with full file system acquisition (e.g. using Elcomsoft iOS Forensic Toolkit). Once you restore the device from a backup, this data is lost. At least this is how it should be, by design.
However, a couple of years ago we discovered that some location data might be synced in the cloud, see Apple Probably Knows What You Did Last Summer. Apparently, this was a leak that was plugged by Apple; we’ve never seen this data syncing since then. The beta version of iOS 14 (or was that iOS 13 but we just missed?) brought some new development.
Privacy Issues and “end-to-end” Encryption
Let’s start with Location Services & Privacy:
By enabling Location Services, location-based system services such as these will also be enabled:
- Significant Locations: Your iPhone and iCloud connected devices will keep track of places you have recently been, as well as how often and when you visited them, in order to learn places that are significant to you. This data is end-to-end encrypted and cannot be read by Apple. It is used to provide you with personalized services, such as predictive traffic routing, and to build better Memories in Photos.
Are you familiar with Apple’s “end-to-end encryption”? We wrote about it recently, see iCloud Backups, Synced Data and End-to-End Encryption. However, look at iCloud security overview containing the comprehensive list of data “transmitted and stored in iCloud using end-to-end encryption”:
- Apple Card transactions (requires iOS 12.4 or later)
- Home data
- Health data (requires iOS 12 or later)
- iCloud Keychain (includes all of your saved accounts and passwords)
- Maps Favorites, Collections and search history (requires iOS 13 or later)
- Memoji (requires iOS 12.1 or later)
- Payment information
- QuickType Keyboard learned vocabulary (requires iOS 11 or later)
- Safari History and iCloud Tabs (requires iOS 13 or later)
- Screen Time
- Siri information
- Wi-Fi passwords
- W1 and H1 Bluetooth keys (requires iOS 13 or later)
Messages in iCloud also uses end-to-end encryption.
As you probably know, we can access some of this data including iCloud Keychain, Health, Maps, Messages, Safari History, Screen Time (not complete) and Wi-Fi passwords, with Elcomsoft Phone Breaker. This list is continuously expanded (e.g. we will soon extract the Home data as well).
However, there are more questions than answers there.
- What does “stored in iCloud” mean? What is the purpose of that? One obvious reason may be to sync the data across devices. But did you see, for example, any Apple Card transactions synced or restored from iCloud?
- If the data is synced across all devices connected to the account, “end-to-end encryption” is not the correct term. The real “end-to-end” means that some specific data can be decrypted only by a specific device or system.
- What is, for example, “Siri information”? Apple does not describe what information Siri collects. We know that Amazon Alexa and Google assistant collect all the requests (original audio recordings plus recognized texts), but what is the reality about Siri?
- What are “W1 and H1 Bluetooth keys” stored for, and what can be done with them if a malicious person gains access to them?
- ScreenTime data: if you use the “Share across devices” option, you may notice that collected app usage statistics looks different on other devices. Here the syncing does not work properly. Yes, I can see my MacMook stats right from my iPhone, and vice versa; there are even traces of Apple Watch usage (just not Apple TV for some reason). However, the most accurate data is only available on the originating device.
I have a feeling that Apple do have a “real” end-to-end encryption mechanism, but it is well hidden in the cracks. We experimented a lot with ScreenTime data, and found that only a very limited amount of data (in particular, the settings and restrictions, plus the ScreenTime passcode, surprisingly) are stored in iCloud, while the real stats are synced directly across devices. That might be applicable for some other categories as well, including Significant Locations. Or not.
iOS 14 Issues
In our lab, we have about 50 test devices. Most of these are iPhone and iPad devices running all versions of iOS from iOS 3 to 13.6 beta. Lately I was playing with iOS 14 beta a bit, to see what has been changed from the forensic point of view.
The first thing I have noticed is “approximate location”:
Here is a very good technical explanations from WWDC on how it works, and it is probably more interesting then the keynote everybody watched: What’s new in location.
However, that should not affect Significant Locations collected, but again, this feature is not documented by Apple at all.
That was still a nasty surprise. I have created an iCloud backup of the test device running iOS 14 beta, then reset the device and restored it from the backup. And… Significant Locations magically re-appeared! This device had *never* left the lab, and has been used at only one location. But the data is there:
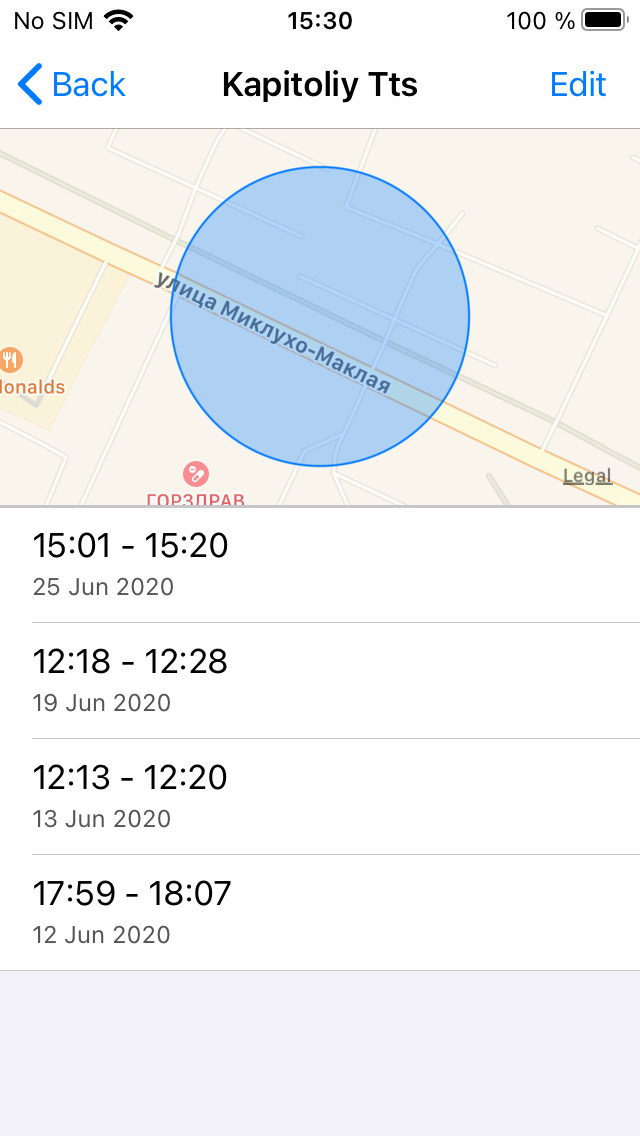
Then I compared it with the data collected on my main device (iPhone 11 Pro Max):
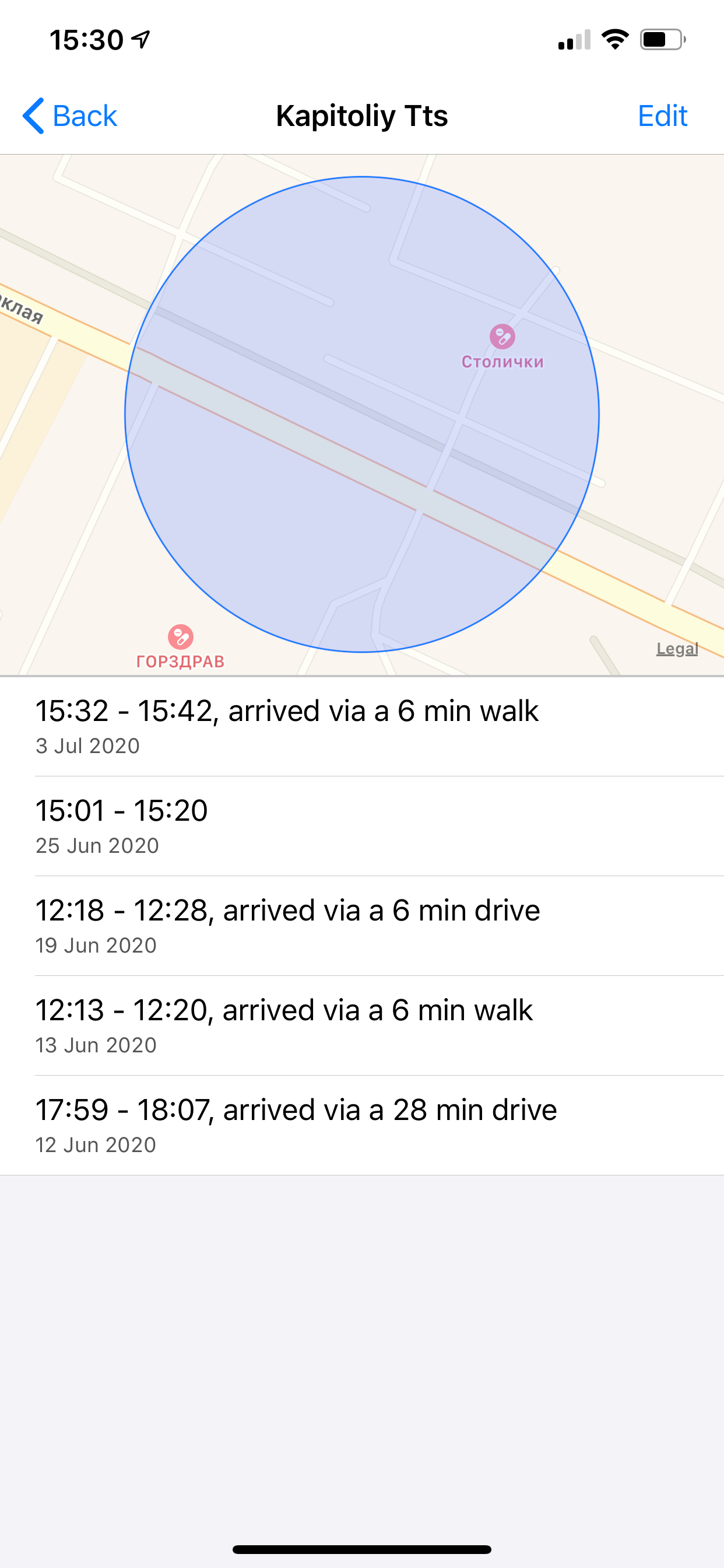
Only one (last) last record is missing. All the other data (other locations, including my home and my office) also match, as well as many other places.
We carefully analyzed the local (iTunes) backup first, but have not found significant locations there. As I wrote above, the databases are not included in backups, and are available with full file system acquisition only (at least it always worked that way). I am now downloading the iCloud backup of the same iOS 14 device, but according to our experience, iCloud backups usually contain less data then local ones.
So it looks like significant locations were not restored but synced. We have not seen this behavior before. We will probably have to release the V2 of our Cloudy Times: Extracting and Analyzing Location Evidence from Cloud Services article, even if we will not be able to extract this data (in case it uses real end-to-end encryption).
Significant Location analysis
The main database to explore is now the Cloud-V2.sqlite (it was Cloud.sqlite prior to iOS 13), located in the mobile/Library/Caches/com.apple.routined folder. There are the other two (Cache.sqlite and Local.sqlite), but we are now talking about the data that is probably synced across iCloud.
You can use Elcomsoft Phone Viewer to explore the full file system acquired from the device (including location data), but I recommend to look deeper into the database manually as it is really interesting.
First, the ZRTLEARNEDVISITMO table. Mine has over 300 records:
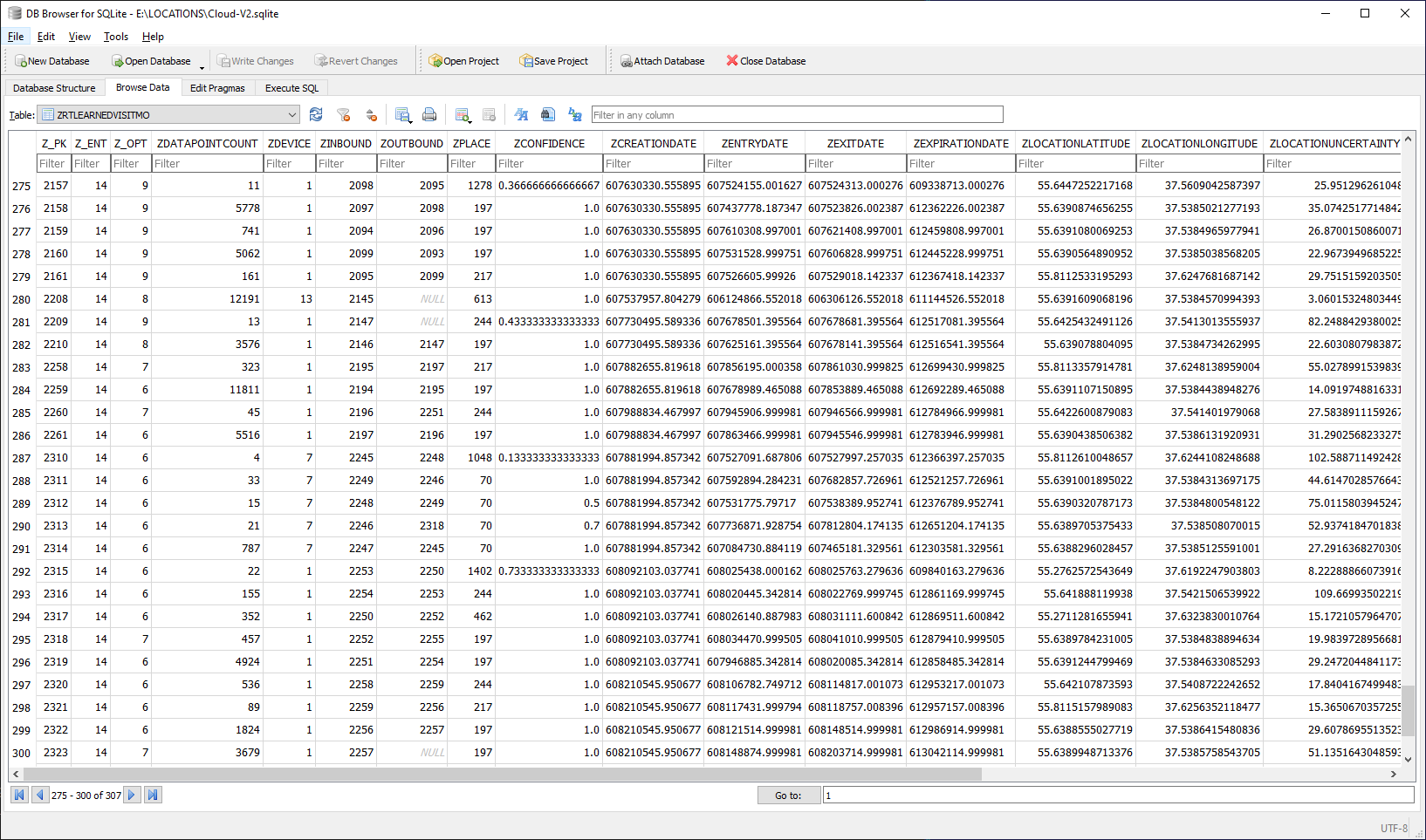
Creation date, entry date, exit date, expiration data (?), latitude and longitude. Pay special attention to ZCONFIDENCE and LOCATIONUNCERTAINTY, only Apple knows what it is.
Next, ZRTMAPITEMMO; it is about places, not visits:
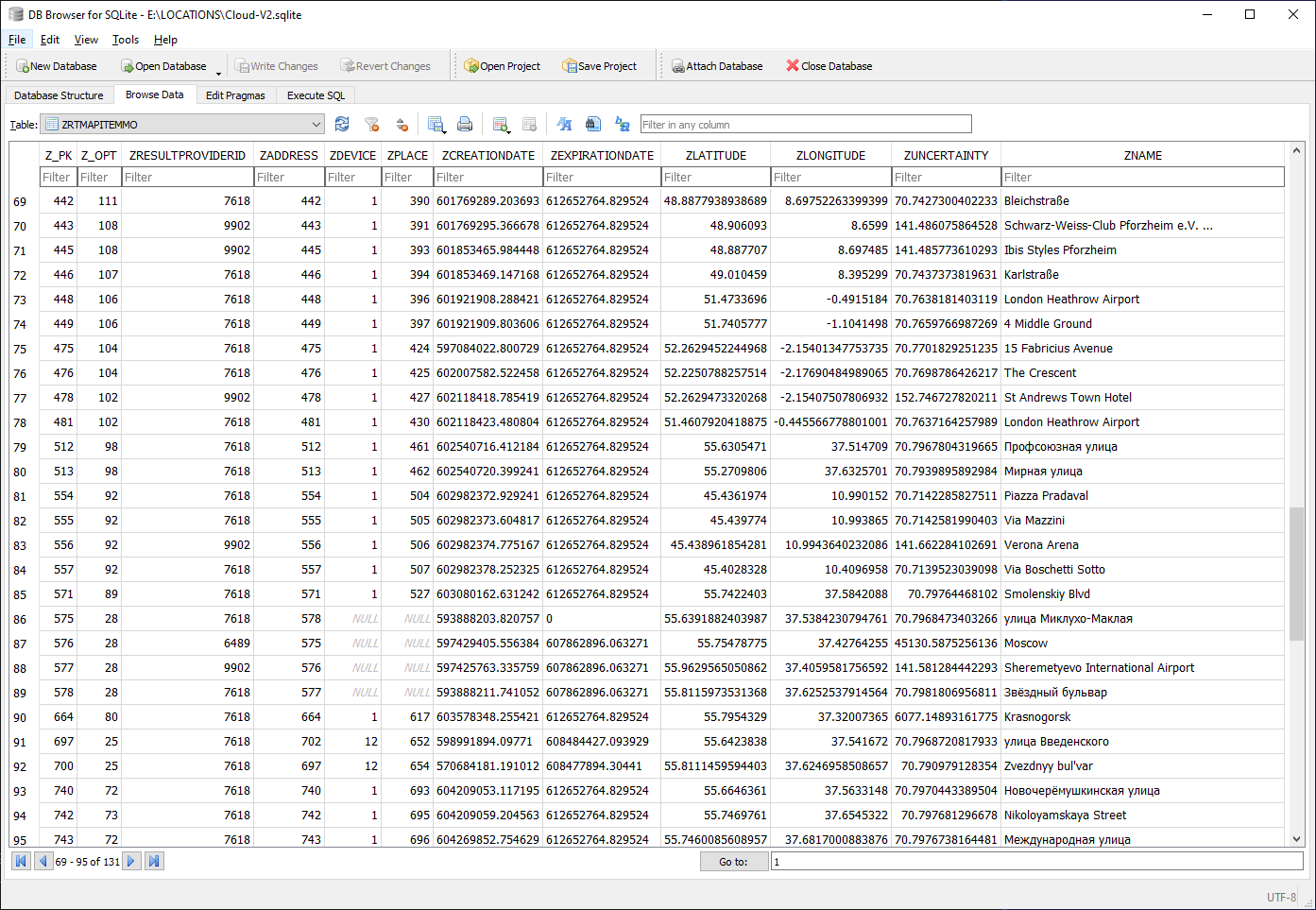
Anything else? Sure, for example ZRTLEARNEDVISITMO:
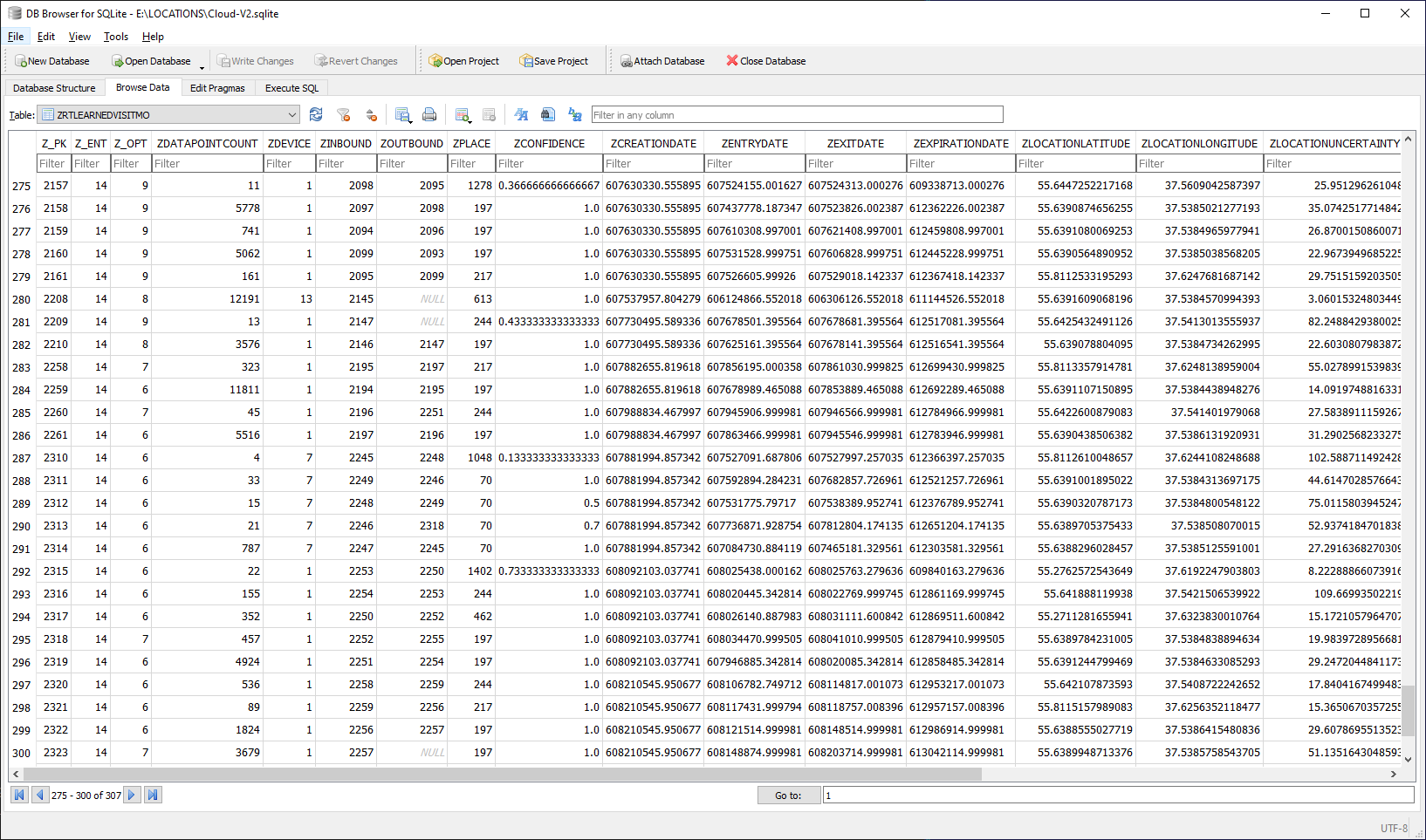
ZRTADDRESSMO also looks interesting, especially the ZINLANDWATER and ZOCEAN fields.
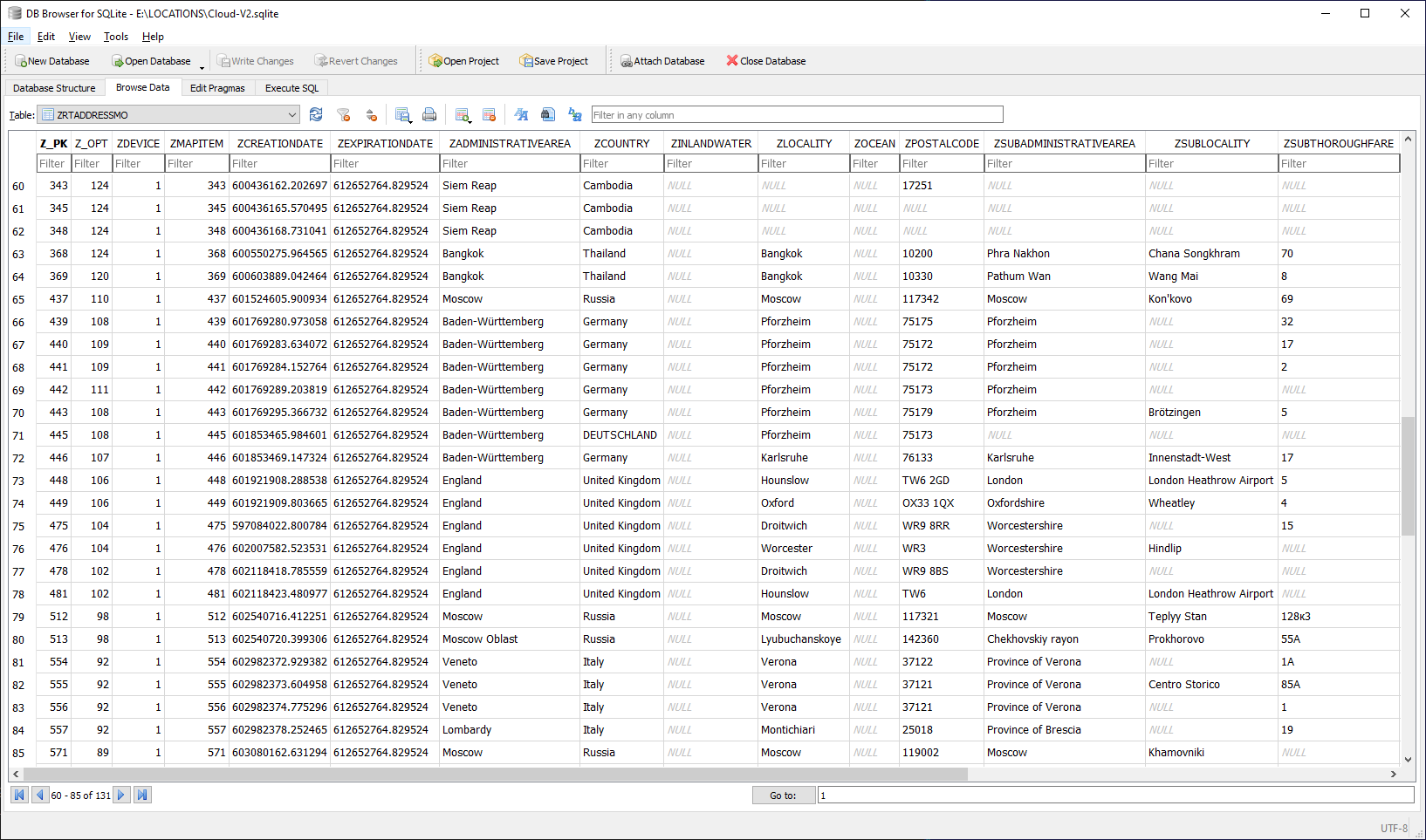
And finally, the ZRTDEVICEMO table that contains the list of devices the location data is collected from, which includes several iPhones, a MacBook and even an Apple Watch:
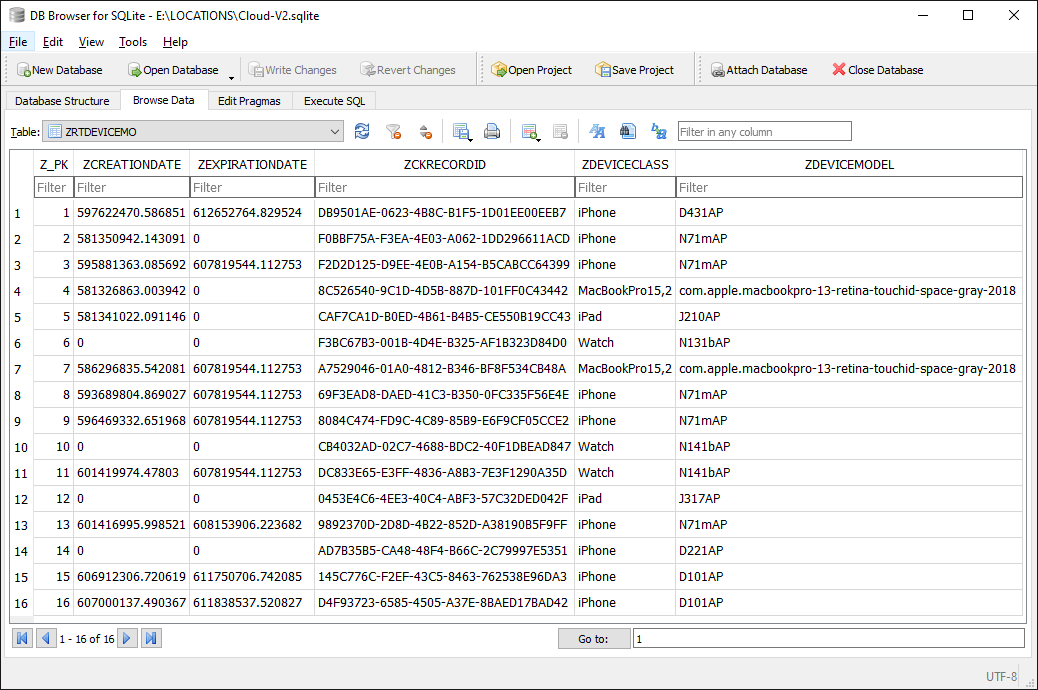
Timestamps are in the Apple Cocoa Core Data format, the number of nanoseconds since midnight, January 1, 2001, GMT.
Conclusion
Apple definitely needs more transparency on how it treats personal data including locations. We need a clear disclosure on what is collected, processed, shared and synced. And, well, how it is protected.












