Smartphones are used for everything from placing calls and taking photos to navigating, tracking health and making payments. Smartphones contain massive amounts of sensitive information which becomes essential evidence. Accessing this evidence can be problematic or expensive, as was clearly demonstrated during the FBI-Apple encryption dispute, which was about the iPhone 5c used by the San Bernardino shooter in December 2015. With modern technological advances, iPhone 5c unlocks are no longer an issue.
The (in)famous iPhone 5c
Apple released the iPhone 5 in September 2012. The phone shipped with iOS 6.0; the latest version of iOS available for this device is currently iOS: 10.3.4.
In September 2013, Apple released not one but two iPhones: the highly innovative (and expensive) iPhone 5s that was, for the first time, equipped with a hardware security co-processor (Secure Enclave) and a fingerprint reader, and the iPhone 5c, a stripped-down phone based on last-year hardware.
With the release of the iPhone 5c, Apple made a controversial attempt to enter the budget phone market. Its colorful back made of gloss plastic met lukewarm response. However, due to its affordable price and wide mobile carrier acceptance, this 2013 model had become one of the most popular budget phones sold by the US carriers.
The iPhone 5c became the last 32-bit iPhone made by Apple. The iPhone 5c was originally released with iOS 7.0 on board; the latest version of iOS available for this phone today is iOS 10.3.3.
The iPhone 5c became famous after the terrorist shooting in San Bernardino in December 2015, which turned into a heated FBI–Apple encryption dispute. In this dispute, the Federal Bureau of Investigation wanted Apple to create and electronically sign software that would enable the FBI to unlock a work-issued iPhone 5C it recovered from one of the shooters. The iPhone 5c was recovered intact but was locked with a four-digit password and was set to erase the data after ten failed password attempts (a common anti-theft measure on Apple smartphones). Apple declined to create the software, and a hearing was scheduled for March 22. However, a day before the hearing was supposed to happen, the government obtained a delay, saying they had found a third party able to assist in unlocking the iPhone and, on March 28, it announced that the FBI had unlocked the iPhone and withdrew its request. It was eventually found that the phone revealed nothing about the plot.
How exactly the FBI received the correct passcode, who was the contractor that did it, and how much exactly the contractor was paid for the service remains officially unknown. Some news outlets, citing anonymous sources, identified the third party as Israeli company Cellebrite. However, The Washington Post reported that, according to anonymous “people familiar with the matter”, the FBI had instead paid “professional hackers” who used a zero-day vulnerability in the iPhone’s software to bypass its ten-try limitation, and did not need Cellebrite’s assistance. According to FBI Director James Comey, the tool (or service) cost more than $1.3 million. Since neither Cellebrite nor the unnamed “professional hackers” can openly comment on the matter, it still remains unknown who did it. Based on vaguely formulated comments, one might be inclined to believe that Cellebrite were the original contractors. Whether this was or wasn’t the case, the “other third party” would be unable to publicly confirm or deny. No confirmed sources exist.
Today, we released a software-only solution that costs just slightly more than 0,1% of the price allegedly paid by the FBI for the tool that was used for breaking that iPhone. Elcomsoft iOS Forensic Toolkit can brute force the iPhone 5/5c lock screen password, enabling investigators to unlock iPhone devices protected with unknown passcodes.
When speaking of passcode recovery, we must mention the work of Sergei Skorobogatov. In his research project: Security Analysis of Apple iPhone 5c (based on his full research paper titled “The bumpy road towards iPhone 5c NAND mirroring”), Sergei demonstrated a proof-of-concept attack allowing to exploit the iPhone 5c and run an attack on its passcode. Sergei’s work requires disassembling the phone, and is subject to a 5 second delay between passcode attempts. In his work, Sergei claims that breaking a 4-digit passcode is possible in about a day, while 6-digit PIN recovery would take unreasonable time.
Finally, the IP-BOX solution and its many clones were available for iOS versions up to and including iOS 8.1. These boxes are not compatible with any newer versions of iOS, and their speed is similar to Sergei’s solution (around 6 seconds per passcode attempt, or about 17 hours to break a 4-digit PIN).

Compared to both of these, our solution does not require additional hardware (you’ll need a Mac though), does not require disassembling the phone, and runs about 80 times faster.
How does the passcode recovery work, and why is it so important in the world of iOS Forensics? Read along to find out.
Passcode as a hallmark of iOS security
The passcode is the most important part of the iPhone security model. Since iOS 8, the user data including the passwords stored in the keychain is encrypted with a key derived from the user’s passcode. Without breaking the passcode, one would be unable to access essential information in BFU (Before First Unlock) devices. Speaking of such devices, bypassing the screen lock passcode makes little sense as the data will remain securely encrypted.
iOS passcode protection is well-documented. The following excerpt from the extremely comprehensive Apple Platform Security documentation explains the role of the passcode in the iOS ecosystem
By setting up a device passcode, the user automatically enables Data Protection. iOS and iPadOS support six-digit, four-digit, and arbitrary-length alphanumeric passcodes. In addition to unlocking the device, a passcode provides entropy for certain encryption keys. This means an attacker in possession of a device can’t get access to data in specific protection classes without the passcode.
The passcode is entangled with the device’s UID, so brute-force attempts must be performed on the device under attack. A large iteration count is used to make each attempt slower. The iteration count is calibrated so that one attempt takes approximately 80 milliseconds.
Touch ID and Face ID can be used to enhance this equation by enabling the user to establish a much stronger passcode than would otherwise be practical. This increases the effective amount of entropy protecting the encryption keys used for Data Protection, without adversely affecting the user experience of unlocking an iOS or iPadOS device multiple times throughout the day.
To further discourage brute-force passcode attacks, there are escalating time delays after the entry of an invalid passcode at the Lock screen. On devices with Secure Enclave, the delays are enforced by the Secure Enclave coprocessor. If the device is restarted during a timed delay, the delay is still enforced, with the timer starting over for the current period.
Source: Apple Platform Security
Speaking of legacy iPhones, the iPhone 5 and iPhone 5c in particular, we have measured the time delay between passcode attempts. The result was exactly 13.6 passcodes per second, or 73.5ms per attempt. This is very close to Apple’s target of 80ms. Since there is no Secure Enclave in these iPhone models, the escalating time delays are enforced in software by the operating system as opposed to being enforced by the Secure Enclave coprocessor. This in turn means that one can theoretically (and practically) disable the delay provided that one has access to certain system files.
Last but not least, the iPhone 5 and iPhone 5c are not equipped with biometric identification hardware. The passcode is the only mean to secure the device. Remember the “Touch ID and Face ID can be used to enhance this equation by enabling the user to establish a much stronger passcode than would otherwise be practical” part? Since there are no alternative means for securely unlocking these iPhone models, users are very likely to choose short, simple PIN codes instead of the longer alphanumerical passcodes to avoid “adversely affecting the user experience of unlocking an iOS device multiple times throughout the day”.
Which passcodes are the most common?
The types of passcodes most frequently selected by the users depend on several factors: the default setting in iOS, and the factor of convenience, which takes into account the presence or lack of the Touch ID/Face ID and the speed and convenience of typing a certain passcode.
The defaults
iOS 6 had a single setting named Simple passcode, which was enabled by default. The resulting passcode, by default, would then consist of only 4 digits. If the user disabled the setting, they could use an alphanumeric passcode of any length. However, if the user had entered any number of digits other than four, the lock screen would display a digit-only keyboard (and a variable size text field). Therefore, our unofficial classification of the types of passcodes available in iOS 6 has the following options:
- 4-Digit Numeric Code
- Custom Numeric Code (other than 4-Digit Numeric Codes)
- Custom Alphanumeric Code
In iOS 9 (as well as iOS 10) the following four options were available:
- 4-Digit Numeric Code
- 6-Digit Numeric Code
- Custom Numeric Code
- Custom Alphanumeric Code

According to multiple sources, ever since iOS 9 Apple shifted to six-digit passcodes, making them the default option. We could not verify this claim for the two iPhone models in question. Our internal tests of setting up iPhone 5 and iPhone 5c devices after a factory reset resulted in iOS consistently offering to set a 4-digit numeric code. Even more interesting is the observation that, once you attempt to change your 6-digit passcode, iOS will still offer setting a 4-digit PIN. We believe this to be part of the “convenience factor”, as a 6-digit passcode would be undoubtedly “adversely affecting the user experience of unlocking an iOS device multiple times throughout the day” as noted in the Apple Platform Security documentation.
The convenience factors
What kind of passcodes are users likely to have on their pre-Touch ID devices? In May, 2020, Philipp Markert, Daniel V. Bailey, Maximilian Golla, Markus Dürmuth, and Adam J. Aviv performed a study of user-chosen 4- and 6-digit PINs collected on smartphones for device unlocking. In their study, the researchers combined multiple datasets originating from various leaks and testing some 1220 participants. The study helped determine the most commonly used 4-digit and 6-digit PINs.
The researchers have made the following findings, which may seem rather controversial. In their study, the researchers found there was little benefit to longer 6-digit PINs as compared to 4-digit PINs. The study’s participants tended to select more-easily guessed 6-digit PINs when considering the first 40 guesses of an attacker. Moreover, their results show that currently employed PIN blacklists are ineffective. Through quantitative and qualitative feedback, the researchers found that participants perceive that blacklisting will improve their PINs without impacting usability. (source)
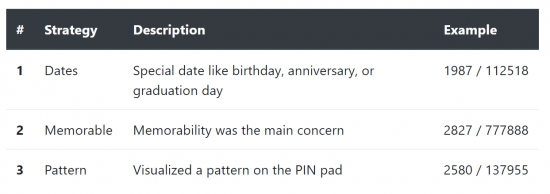
Commonly used passcodes
We strongly recommend reading the entire research to get a better understanding on how users choose their screen lock passcodes. What really matters though is the list of the most commonly used (thus insecure) 6-digit PINs. There are only 2910 entries in this list, and it only takes about 4 minutes to test them all. Examples on this list include the world hit 123456, repeated digits, as well as the digital passcodes representing certain combinations (e.g. 131313 or 287287). Following this list are the 6-digit PINs based on the user’s date of birth; there are around 74K possible combinations that take about 1.5 hours to try. Only after these options are exhausted do we start the full brute-force attack that lasts around 21 hours.
Conclusion
The iPhone 5 and 5c are now almost 7 years old, yet many of them are still stored in forensic labs, waiting to be extracted. In some parts of the world, these inexpensive iPhones are still in active circulation. It took years for the first exploit to appear at an outrageous price, and even more time for reasonably priced solutions. Today, we are bringing the cost of high-speed iPhone 5 and 5c unlocks down, offering a software-only solution that requires no soldering, no disassembling and no extra hardware. See iPhone 5 and 5c Passcode Unlock with iOS Forensic Toolkit for details.





