iOS 14 is officially out. It’s a big release from the privacy protection standpoint, but little had changed for the forensic expert. In this article, we’ll review what has changed in iOS 14 in the ways relevant for the forensic crowd.
iOS 14: supported devices
iOS and iPadOS 14 are updated for the same devices that could run iOS 13. This generally means iPhone and iPad devices equipped with Apple A7 through A13 Bionic SoC (iPhone 6s, SE, 7, 8, X, XR, XS, and iPhone 11 generation devices) with two notable exception. iOS 14 is also available for the iPad Air 2 (based on Apple A8x) and iPad mini 4 based on the Apple A8 CPU also found in the iPhone 6 and 6 Plus, which are not supported by iOS 14.
For older 64-bit devices (the iPhone 5s and iPhone 6 range) the latest version is iOS 12.4.8 released in June 2020. 32-bit devices such as the iPhone 5c are stuck with iOS 10.3.3.
Support for checkm8 and checkra1n
Some Apple devices have a hardware vulnerability in the BootROM that cannot be patched by Apple. By exploiting the vulnerability, experts have been able to extract data from unlocked devices.
Apple had made some changes attempting to mitigate SEPOS on devices based on the A10 and newer chips (except on Apple TVs and iBridge). According to checkra1n developers, “if the device was booted from DFU mode and the Secure Enclave receives a request to decrypt user data, it will panic the device. Since checkm8 does not give us control over the Secure Enclave, this is not trivial to workaround. However, with the recently published blackbird vulnerability, we are able to get control of the Secure Enclave on A10 and A10X and disable this mitigation. Support for A10 and A10X devices is being worked on and is expected to be ready in the coming weeks.”
At this time, the developers are not yet positive about whether they can do the same for devices with the A11 chip. As a result, a separate announcement will be made regarding the iPhone 8, 8 Plus, and iPhone X range of devices.
However, Apple had not been able to fully patch the vulnerability in the BootROM. The checkra1n developers have announced immediate availability of the jailbreak for the following devices:
- iPhone 6s, 6s Plus, and SE
- iPad 5th generation
- iPad Air 2
- iPad mini 4
- iPad Pro 1st generation
- Apple TV 4 and 4K
- iBridge T2
Devices that are likely to receive support in the coming weeks:
- iPhone 7 and 7 Plus
- iPad 6th and 7th generation
- iPod touch 7
- iPad Pro 2nd generation
Finally, there following devices will be addressed in a future statement:
The checkra1n jailbreak for iOS 14 can be downloaded from this link.
iOS 14 local backups
iTunes backups are commonly used during logical acquisition. Very little had changed in regards to local backups in iOS 14. If you are using Windows, you’ll need the latest version of iTunes (or forensic software updated to support iOS 14) in order to make local backups. It’s been reported that older versions of iTunes to not see devices updated to iOS 14.
We’ve seen some small changes to the backup format, which will require us to update Elcomsoft Phone Breaker and Elcomsoft Phone Viewer to fully support the new OS. Other than that, the encryption mechanism seems unchanged. The data available in local backups is very similar to that of iOS 13.7, meaning you can expect finding the familiar artifacts stored in the familiar places.
As in iOS 13.7, certain types of data are available if the backup encryption password is set. These include:
- Keychain
- Health data
- Call logs
- Safari history
- Safari open tabs
We have not detected any notable changes to the content of local backups. We are working on an update to Elcomsoft Phone Breaker and Elcomsoft Phone Viewer to accommodate for the small changes in the format.
iCloud backups and sync
We have obtained iCloud backups made from the same device running iOS 13.7 and 14.0. Minor differences in communication protocols aside, there were no immediate changes to the content of cloud backups. We’re still in the process of doing the thorough comparison though. You will need using the current version of Elcomsoft Phone Breaker in order to download iCloud backups. We’ll still need to update Elcomsoft Phone Viewer to let you view them.
As to the iCloud sync, it seems the changes are minor, if there are any. In particular, we’ve been able to successfully sync Significant Locations. You can read more about iOS Significant Locations in our article Significant Locations, iOS 14 and iCloud.
File system images
We’ve been able to use the new checkra1n jailbreak to extract the file system from a test device before and after the update. While we’ll have to spend some more time analyzing the differences, it seems that all the major artifacts are there, and the file paths to the usual suspects have not changed. We are currently working comparing the file system images extracted from the same device running iOS 13.7 and updated to iOS 14.0.
Full file system extraction and keychain decryption for iOS 14 devices are possible with Elcomsoft iOS Forensic Toolkit thanks to checkra1n.
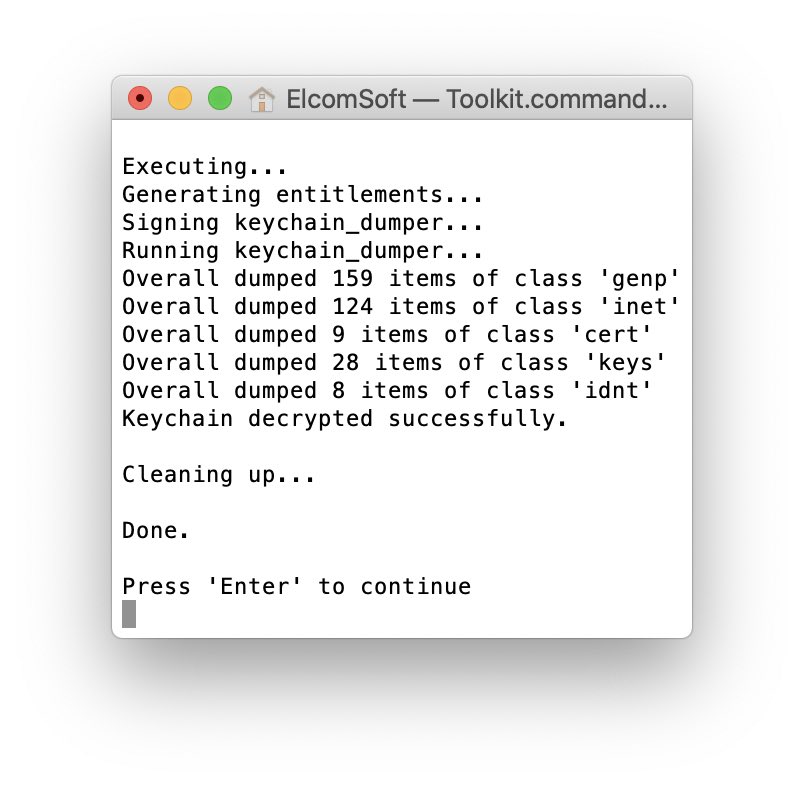
We’ve been able to perform both AFU and BFU extractions using the test device (iPhone 6s). We’re waiting for the availability of checkra1n for the latest generation of affected devices (the iPhone 7 and 7 Plus, iPhone 8, 8 Plus and X range) to verify AFU/BFU extraction.
When analyzing the file system images, we found some changes in Apple Maps data (altered paths and seemingly more data available). In addition, some extra data is available for threaded messages. Finally, we’ve seen the additional app permissions, which may be important when investigating incidents.
TL;DR: iOS 14 acquisition
So what are your options to acquire information from devices running iOS 14?
First, remember that extended logical acquisition always works for all models (from the original iPhone to the upcoming iPhone 12), regardless of the iOS versions. That includes not only backups, but also media files (including full metadata), shared application files and diagnostics logs. And it may work even for locked devices, if you have a valid pairing record and the USB restricted mode has not been activated.
- iPhone 6s and iPhone SE: the checkra1n jailbreak is available, so it is easy to perform the full file system and keychain acquisition. For locked devices, partial acquisition is possible.
- iPhone 7: checkra1n will be updated soon to support this model.
- iPhone 8 and iPhone X: the situation is not clear. There is a small chance that checkra1n will support it too, but no ETA (and no warranty of any kind).
- iPhone Xr, iPhone Xs, iPhone 11, iPhone 12: for now, only extended logical acquisition (see above); however, the chances that our agent acquisition method will support some of these devices are high. Stay tuned! For now, we support iPhone Xr/Xs/11 running iOS 13 only (from iOS 13.0 to 13.5).
- Missing iPhone 6, iPhone 5s, iPhone 5 and older models? They simply cannot run iOS 14 (and iOS 13, actually).
Finally, you can perform a cloud acquisition. Just like the first method (extended logical), it works for all models and iOS versions. From the one side, you need the iCloud credentials; from the other side, you can acquire the data even without access to the device itself, and access the data that belongs to other devices connected to the same account, including the most secure categories such as iCloud keychain, Health data, encrypted iMessage conversations and more. Quite often this method returns more information than all other methods combined, including deleted data. Just use proper tools like Elcomsoft Phone Breaker.
More information
You may be interested in the findings published in the D20 Forensics blog:
In addition, Smarter Forensics had published the article Rotten to the core? Nah, iOS14 is mostly sweet, which is also worth checking out.
iOS 14 adds a bunch of privacy-oriented features. The two articles we recommend checking out are:
Conclusion
The work on iOS 14 forensics is still in progress. Unlike in previous iOS releases that had a number of apparent changes, we haven’t witnessed anything major in iOS 14 that could affect the work of forensic experts. We are still doing the in-depth analysis of file system images and backups obtained from the same devices prior to and immediately after an update. If we discover anything worth mentioning, we’ll post in our blog.




