It’s been a week since Apple has released iOS 14.2 as well as iOS 12.4.9 for older devices. Just a few days later, the developers updated the checkra1n jailbreak with support for new devices and iOS versions. What does that mean for iOS forensics? Let’s have a look; we have done some testing, and our discoveries are positively consistent with our expectations. Just one exception: to our surprise, Apple did not patch the long lasting vulnerability in iOS 12.4.9 that leaves the door open to full file system extraction and keychain acquisition without jailbreaking.
iOS 14.2
Over 100 new emoji, that’s the deal! On a serious note, iOS 14.2 brings a lot of improvements and fixes; please pay attention to the security content.
At this time, there are no known vulnerabilities or publicly available exploits in iOS 13.5.1 and newer. For devices running these versions, you only have the following options:
- Extended logical acquisition (backups, media files, shared files, diagnostics logs)
- Cloud acquisition
- checkra1n jailbreak, followed by the full file system and keychain acquisition
We have successfully tested Elcomsoft iOS Forensic Toolkit (extended logical acquisition) and Elcomsoft Phone Breaker (cloud acquisition) with the new iOS 14.2. No issues found, all the data has been extracted successfully.
As for the checkra1n, the devil is in the details, please keep reading. But a bit on yet another iOS update first.
iOS 12.4.9
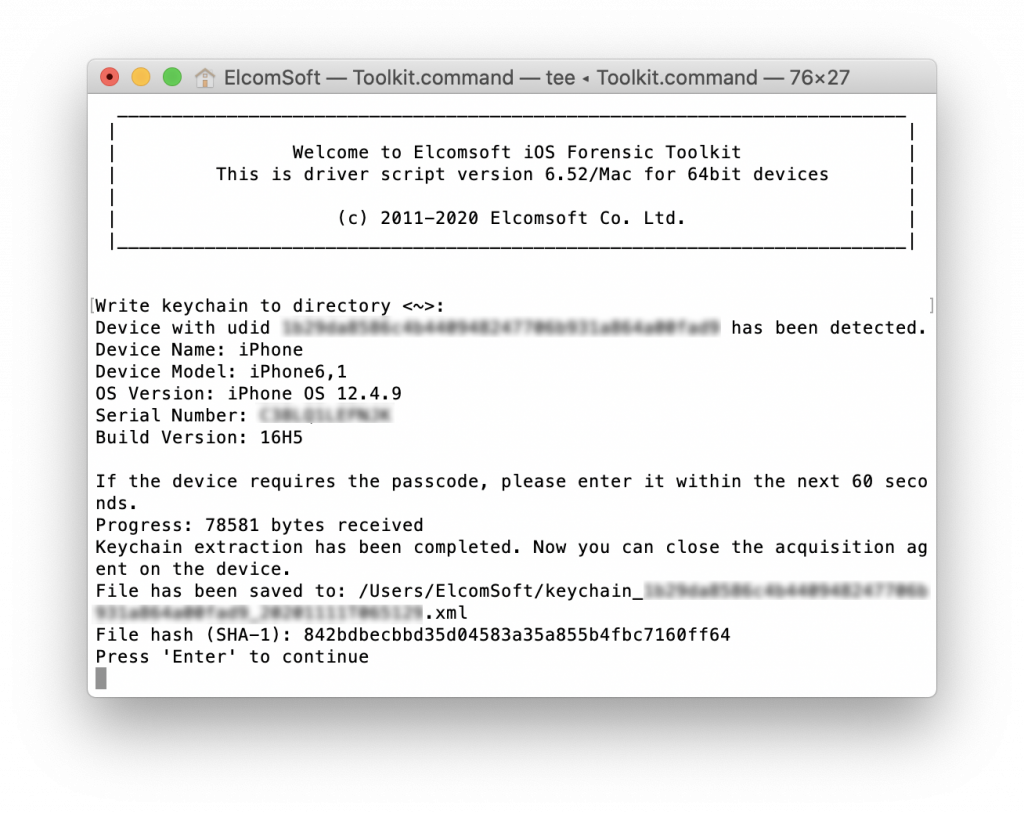
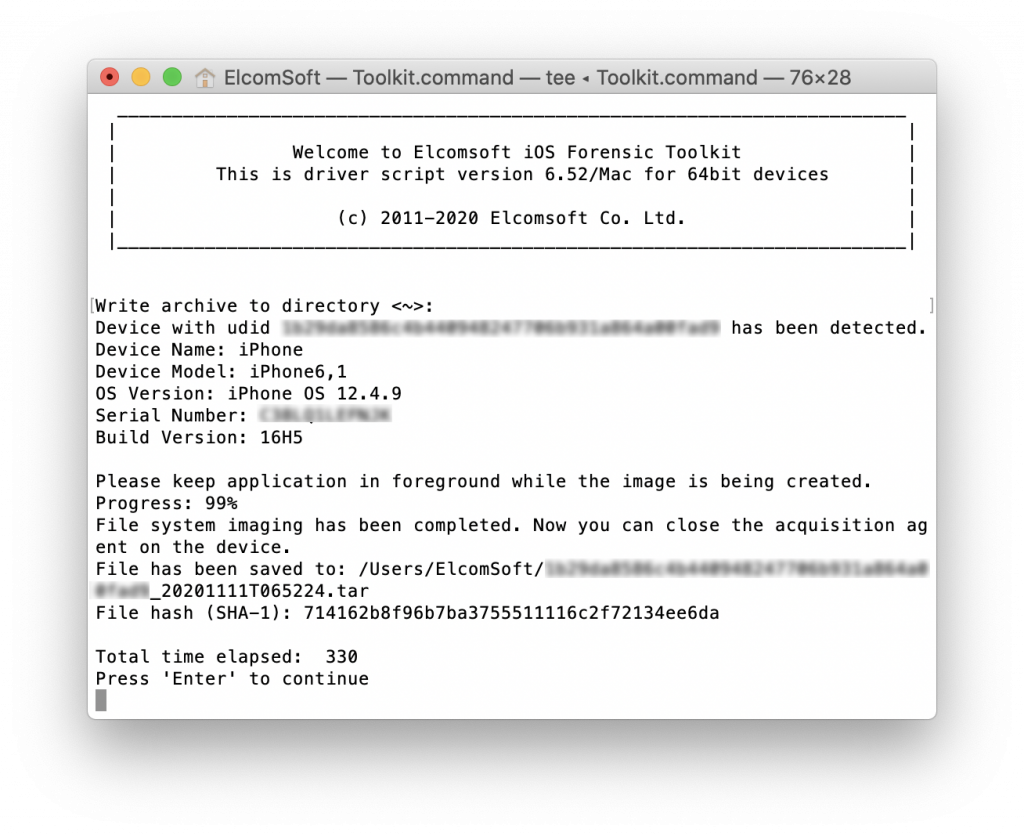
As you know, iPhone 5s and iPhone 6 (there are still millions of these devices on the market) did not receive iOS 14 or even iOS 13. For these devices, Apple continues maintaining the iOS 12 branch, thus releasing iOS 12.4.9. No notable improvements were found, but have a careful look at iOS 12.4.9 security content. Our biggest surprise was that this iOS release does not patch any of the system vulnerabilities that allowed us to implement the file system extraction and keychain acquisition without jailbreaking for iPhone 5s and iPhone 6, which makes our tool covering most iOS versions these device can run (see iOS Extraction Without a Jailbreak: Finally, Zero-Gap Coverage for iOS 9 through iOS 13.5 on All Devices).
checkra1n 0.12
The biggest news last week is not iOS updates though, but the new checkra1n release.
Despite the fact that the checkm8 exploit is a hardware-based one and “cannot be patched by Apple” as many forensic vendors love to say, iOS 14 partially fixed it; more information here.
Still, checkra1n developers were able to implement full iOS 14 support for iPhone 6s and iPhone SE (first generation). And the latest version of checkra1n 0.12 beta has the following major improvements:
- Official support for iOS 14.1 and 14.2
- Official support for A10/A10X devices on iOS 14.x
- Limited support for A11 devices on iOS 14.x (Options > Skip A11 BPR check)
Confused about A10/A11 and how the SoC names are related to iPhone and iPad models? Consult to our Apple Mobile Devices Cheat Sheet.
In other words: checkra1n now also fully supports not just the iPhone 6s and iPhone SE, but also iPhone 7 and 7 Plus, as well as some iPad models (6th and 7th gen and iPad Pro 2nd gen). All of that, including iOS 14.1 and 14.2 that have been just released.
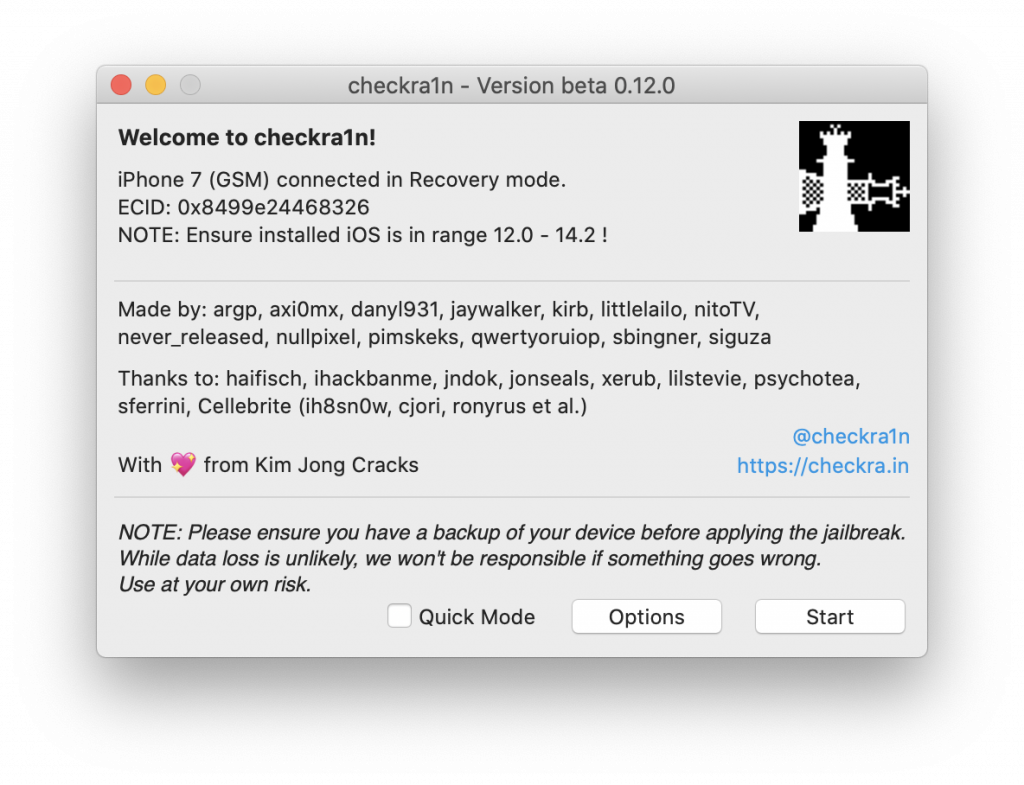
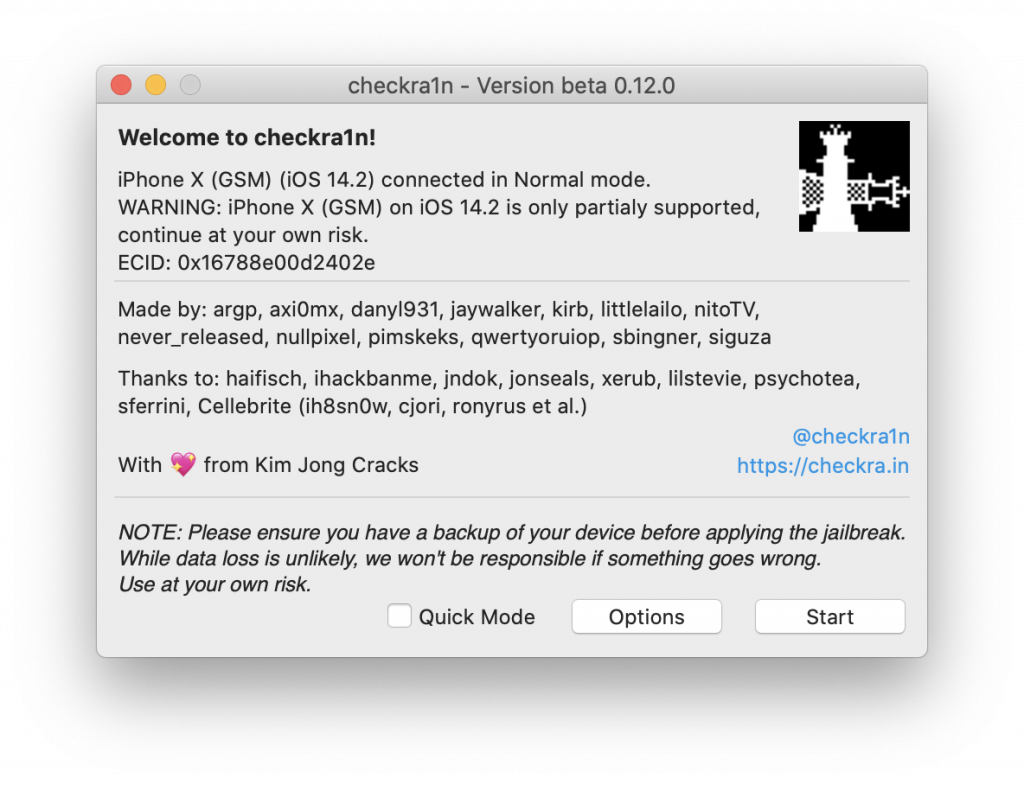
What about the iPhone 8 (8 Plus) and iPhone X? They received only partial support. More on that below.
macOS issues
Before we proceed further, please note that the checkra1n jailbreak is only available for macOS and Linux. iOS Forensic Toolkit also works more reliably and has extended functionality on macOS, although we have the Windows version too. Two major features that are not available in the Windows version:
We recommend using macOS 10.13 (High Sierra) or 10.14 (Mojave) for iOS Forensic Toolkit. The tool is compatible with macOS 10.15 (Catalina) and 11.0 (Big Sur) as well, but there is one extra step in the product installation: you have to clear the quarantine flag from the iOS Forensic Toolkit image before installation. Also, there are some nuances on using the lockdown/pairing records for extended logical acquisition of locked devices. Please read the Installing and using iOS Forensic Toolkit on macOS 10.15 Catalina before contacting our technical support saying “hey, it does not work”.
BFU acquisition (and iPhone X issues)
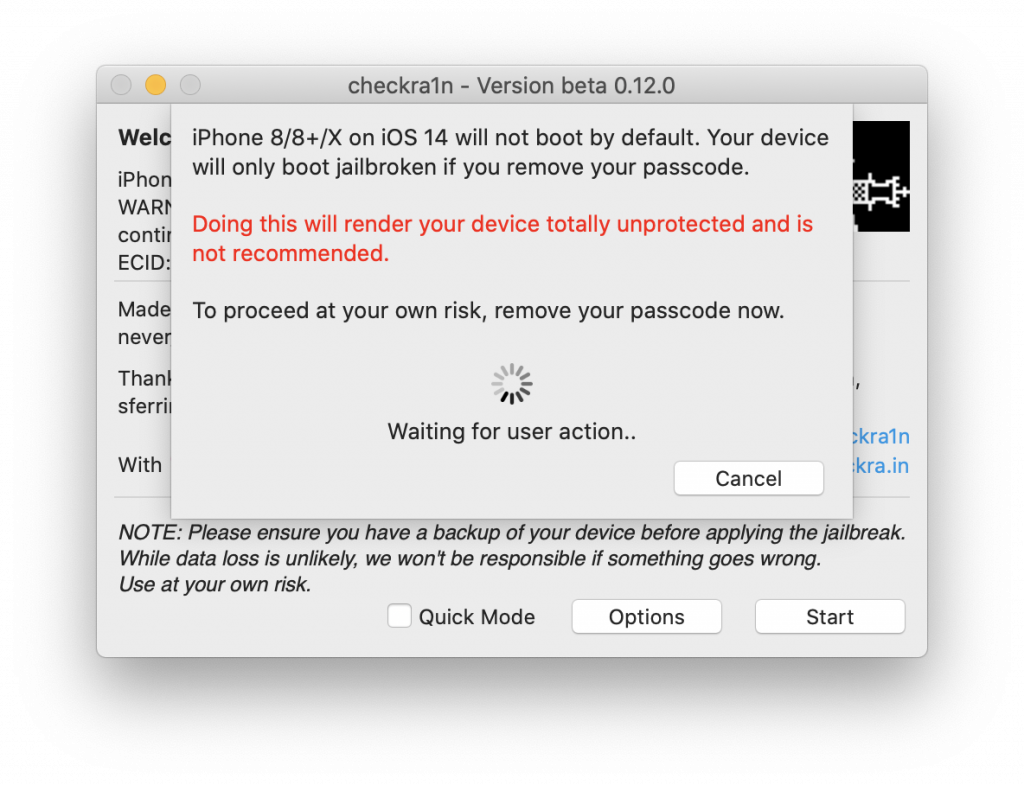
Noted the Limited support for A11 devices on iOS 14.x in checkra1n 0.12 release notes? It applies to iPhone 8 and iPhone X (no iPads based on that SoC, btw). That means that you can only install checkra1n on devices that do not have the passcode set, which has the following forensic consequences:
- If you know the passcode, you have to remove it first to perform the file system extraction and keychain acquisition. Note that removing the passcode has some important consequences; see The Worst Mistakes in iOS Forensics
- If the passcode is not known and you want to perform BFU acquisition, you are out of luck.
In case if you are not familiar with BFU: it means “Before First Unlock”, and this term is not official. BFU acquisition is intended for the case when the phone is locked with an unknown passcode. Thanks to checkra1n, you can still extract some data from the device, such as account information, list of installed apps, message drafts, some media files, and even parts of the keychain, see BFU Extraction: Forensic Analysis of Locked and Disabled iPhones. Moreover, some iOS apps leave their data unencrypted (and so available in BFU mode), detailed in Snapchat – A False Sense Of Security? by James Duffy.
One more thing. If you perform BFU acquisition, please do not forget to set the port number (in the iOS Forensic Toolkit script) to 44 instead of 22. Speaking technically, by the time when the checkm8 exploit completed its work and the user partition is mounted (but Cydia is not installed, so no OpenSSH), only the DropBear SSH client is active on the devices. For some reason, it opens SSH on port 44 instead of the default 22.
Testing
We have tested iOS Forensic Toolkit on the following configurations:
- iPhone 7 (A1778), iOS 14.2, BFU (passcode is not known)
- iPhone 7 (A1778), iOS 14.2, AFU (passcode entered)
- iPhone X (A1901), iOS 14.2, AFU (passcode is not set)
We spent considerable time testing the new iOS builds and the new version of checkra1n to make sure that everything works as intended on both Windows and macOS, the extracted files open successfully in Elcomsoft Phone Viewer and Forensic Forensic Detective, and there are no further surprises.
As noted above, for the iPhone 7 it is still possible to perform BFU extraction of devices locked with an unknown passcode. In this case, you do not receive the full file system (as a solid part of it is still encrypted), but something is better than nothing. On our test device, we obtained 12 GB of data (counting the system files though) in BFU mode, compared to about 40 GB of the full file system image. In case if you curious, standard (iTunes-style) backup takes about 17 GB (no system files there).
For the iPhone 8 and iPhone X, even the limited extraction is no longer possible. If the device is running 14.0 to 14.2 and the passcode is not known, there is nothing we can do. Still, checkra1n is very useful for these devices as it allows to perform the file system and keychain acquisition of unlocked devices.
To summarize, we obtained the results we were hoping for. Sometimes, checkra1n did not work from the first try (although we followed the checkra1n Installation Tips & Tricks carefully). We had to reboot MacBook and the device occasionally (otherwise iOS Forensic Toolkit failed to connect, and it is not clear it that that was a problem of macOS or our software).
Conclusion
If you are a forensic expert, you might be hoping for a step-by-step manual covering all possible combinations of devices and operating systems. For example, we have not covered the USB restricted mode issues; fortunately, the new checkra1n still ignores USB restrictions, allowing to perform the partial acquisition or locked and disabled devices. We are working on a guide like that. For now, we know the following:
- If the device is unlocked (passcode known or not set), use Agent acquisition if possible; this is the most safe, easy and forensically sound method available.
- if Agent acquisition is not available or the passcode is not known, use checkra1n (BFU/AFU)
- If neither Agent nor chechra1n are compatible with your device, you are limited to extended logical acquisition.
- If the passcode is not known and the device is not vulnerable to the checkm8 exploit, all you can do is cloud acquisition (or request the data from Apple). You may receive even more data than counted above.











