From time to time, we stumble upon a weird issue that interferes with the ability to install a jailbreak. One of such problems appearing literally out of the blue is the issue of being unable to remove the screen lock password on some iPhone devices. What could be the reason and how to work around the issue? Read along to find out!
The problem
Why would you even need to remove the passcode that you know? There could be many reasons, but if you are working in the forensics, the most common one is the file system and keychain acquisition.
Note: we do not recommend removing the passcode unless you cannot do without it. This operation has several irreversible consequences that will affect your acquisition result. Still, sometimes removing the passcode is the only way to gain access to the full set of data. Either way, we strongly recommend performing extended logical acquisition first. Pull a backup, even if encrypted; acquire media files via the AFC protocol, and collect diagnostic logs.
If the device is running iOS 9.0 through 13.7, the simplest, fastest and safest way to get the complete file system image is using the agent-based acquisition technique in Elcomsoft iOS Forensic Toolkit. You cannot use this method (yet) with iOS 14. The only way to gain access to the data is jailbreaking with checkra1n or using the direct checkm8-based acquisition available in some forensic packages.
The problem is that certain models (the iPhone 8, iPhone 8 Plus, and iPhone X range) checkra1n/checkm8 only work if the passcode is not set. Hence, you need to remove it first. There are several factors that may prevent you from doing so, and the most common one is MDM (Mobile Device Management), see Passcode MDM payload settings for Apple devices.
However, even if the device is not managed, you might not be able to remove the passcode. When the device is in Airplane mode, the Turn Passcode Off command simply refuses to work in the current version of iOS. If you put the device online (which is also strongly discouraged as the device may be remotely locked or wiped), it simply prompts you for the Apple ID password that is often not known.
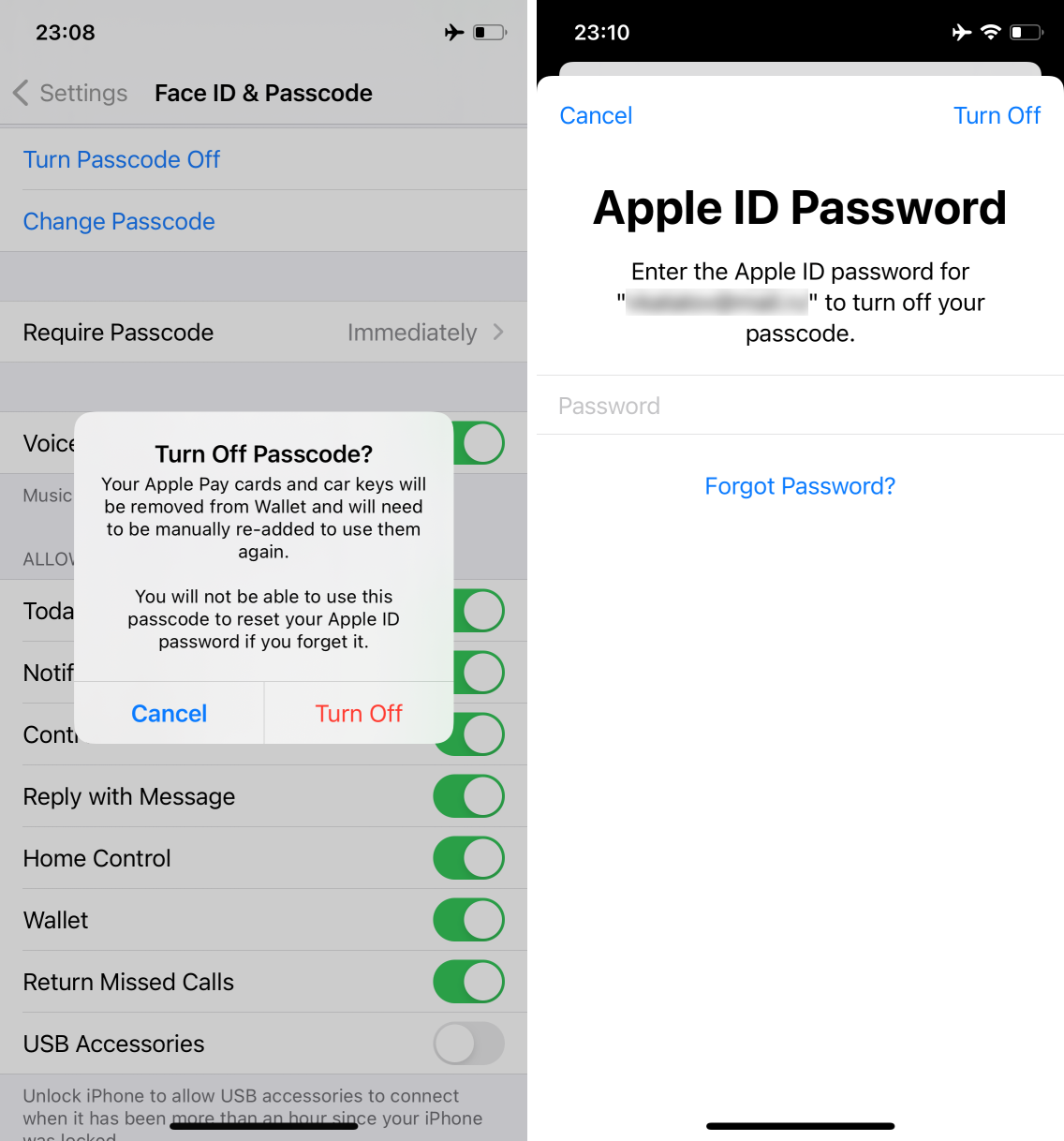
One solution may be changing the Apple ID password (it is often possible without the original password, depending on iCloud settings), but it is far from perfect. Alternatives do exist, though, at least in some cases.
The solution
One of the possible reasons of such behavior is Apple Pay. As you may know, Apple Pay requires a passcode to be set, and the removal of the passcode will also remove all payment cards and clear transaction history. We have absolutely no idea why one must sign in to iCloud to reset the passcode when the cards have been set up. Quite possibly there might be some other system components (or may be even third-party iCloud-enabled apps) that prevent the passcode from being removed.
In some cases, however, there are no cards in the Wallet, but the passcode still cannot be removed. What you can try is using the Reset All Settings command. In our tests, it worked just fine in Airplane mode (even without removing the payment cards in advance, as well as in the situations when there are no cards but turning the passcode off does not work).
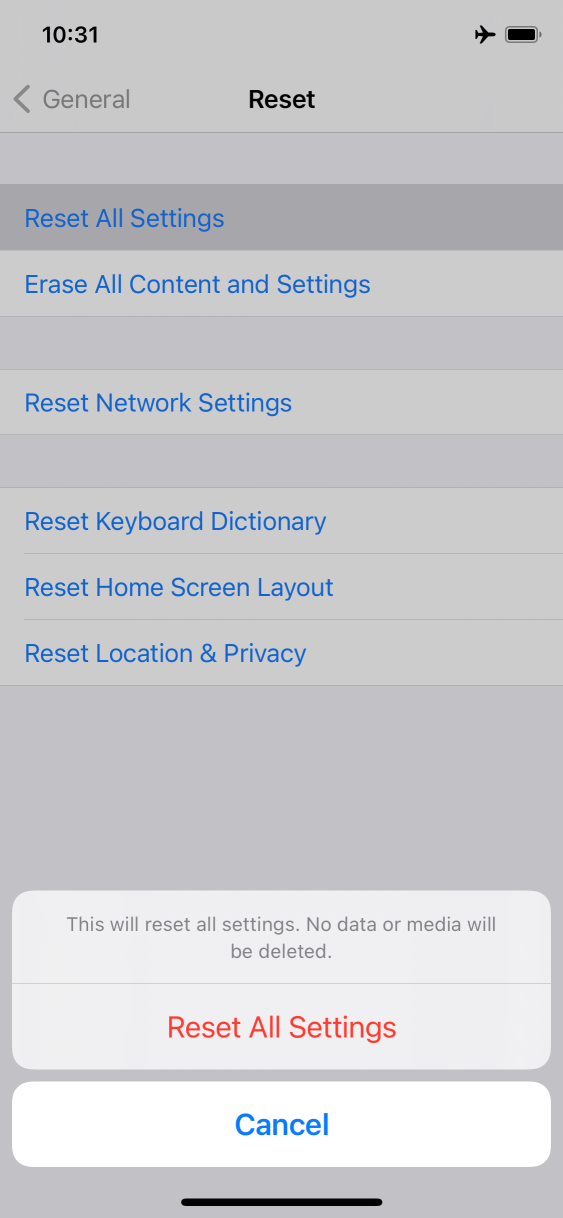
Note that Reset All Settings not only removes the passcode, but also clears the backup encryption password and all saved passwords to Wi-Fi access points. Also, if the Screen Time password is set, it has too be entered to reset all settings, but that’s another story (see How To Access Screen Time Password and Recover iOS Restrictions Password for possible solutions).




