NAS Forensics: QNAP Encryption Analysis
December 23rd, 2020 by Oleg Afonin
Category: «General»
A year ago, we analyzed the encryption used in Synology NAS devices. We were somewhat disappointed by the company’s choice to rely on a single encryption layer with multiple functional restrictions and security reservations. Today we are publishing the results of our analysis of data encryption used in QNAP devices. Spoiler: it’s very, very different.
Home users and small offices today are served by two major manufacturers of network attached storage devices: QNAP and Synology. Both companies advertise support for hardware-accelerated AES encryption, yet the implementation is very different between the two brand. While Synology, in its home and small office models at least, relies exclusively on per-share, file-based encryption via eCryptFS, QNAP tends to favor volume-based encryption. Yet, things aren’t all black and white, as QNAP also offers folder-based and SED encryption in many (but not all) models. In this research, we’ll be discussing the types of encryption used in QNAP NAS devices.
Supported Encryption Types and Applicable Hardware
The majority of current QNAP NAS devices support at least one type of encryption, while certain types of devices support layered protection with several types of encryption. These encryption layers include:
- Self-encrypting drive (SED). SED encryption support is available in select QNAP models, providing hardware-based encryption for hard drives with encryption support. SED encryption can be used on individual drives as well as on multiple drive storage pools, enabling the creation of fully encrypted storage pools. SED encryption is the lowest encryption layer. In QNAP devices, SED works on the Storage Pool level. The use of SED encryption does not affect performance, yet its scope of protection is limited.
- Volume encryption. This type of encryption is available in most QNAP models. Volume encryption is software based; it works on the level of individual volumes. Volume encryption can protect single-disk and static volumes as well as volumes located on multi-disk storage pools. Volume encryption does affect the performance, albeit the effect is relatively minor.
- Folder-based encryption. This is the same kind of encryption we’ve seen in Synology, and analyzed in Forensic Analysis of Synology NAS Devices. The implementation of folder-based encryption in QNAP is somewhat less comprehensive compared to Synology’s; we’ll cover the differences in the corresponding chapter.
SED Encryption
A self-encrypting drive (SED) is a drive with encryption hardware built into the drive controller. Select QNAP models support self-encrypting drives, allowing to set up a SED secure storage pool that only contains SED hard drives with hardware encryption enabled. SED is the perfect first layer of encryption. Unfortunately, we could not test SED encryption with the QNAP TS-453Be due to the lack of a spare self-encrypting drive.
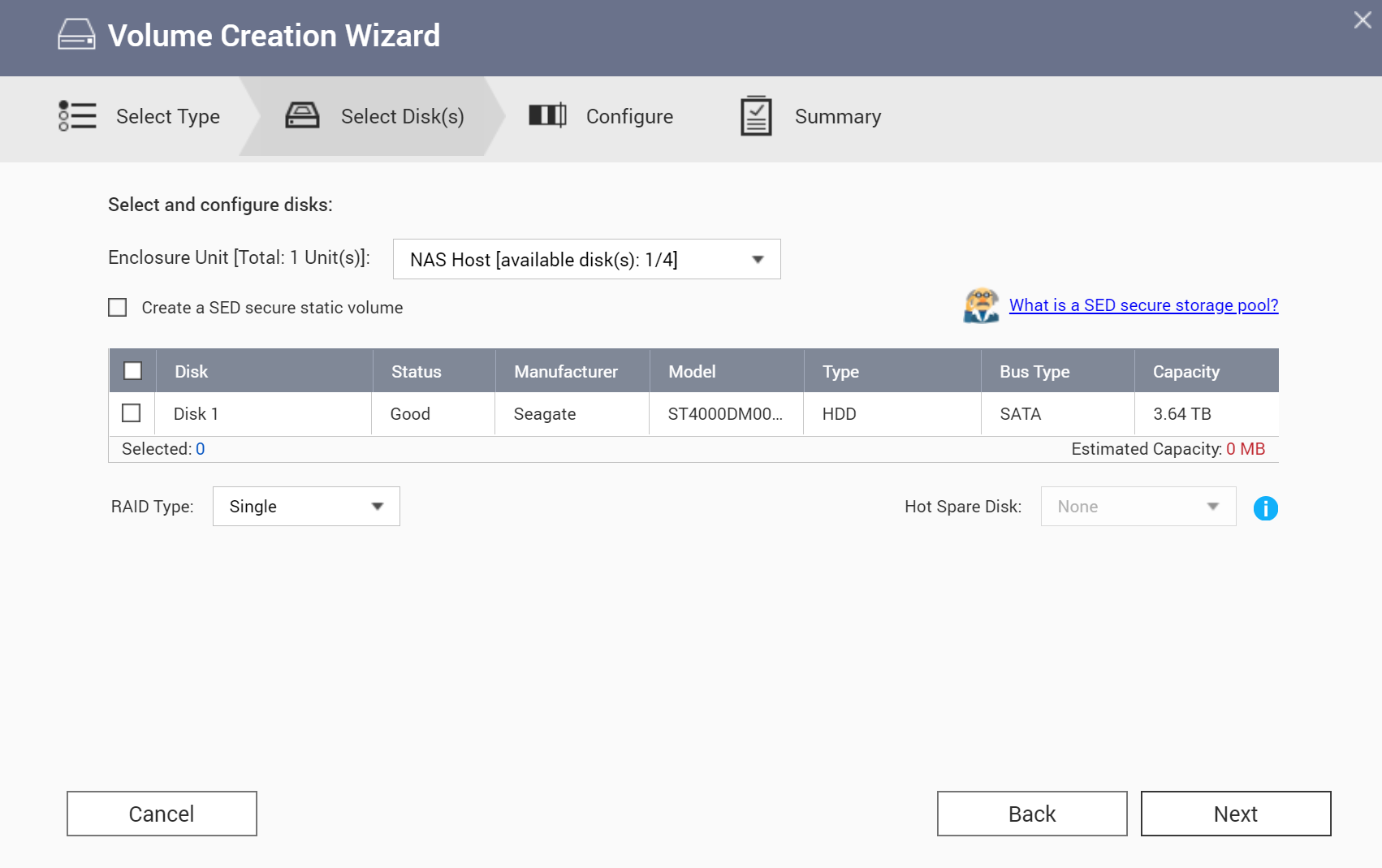
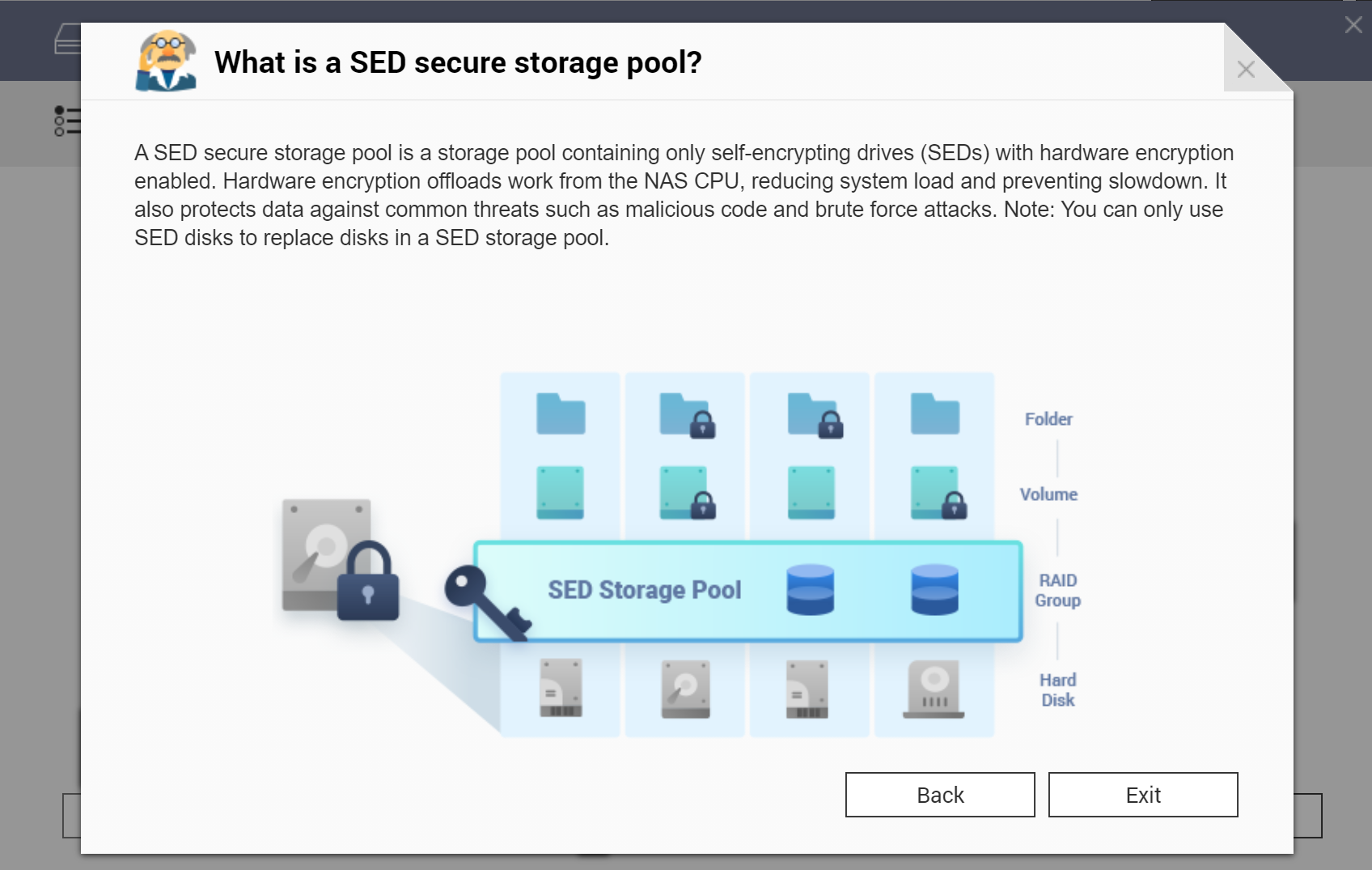
Note that SED encryption applies on the Storage Pool level (such as single disk/RAID/JBOD etc.) Logical volumes created on regular or SED volumes can feature additional software encryption.
According to QNAP documentation, the system allows saving the SED encryption key, which enables the system to automatically unlock and mount the SED pool when the NAS starts up. If the encryption key is not saved, the user must specify the encryption password every time the NAS restarts. QNAP warns users that “Saving the encryption key can result in unauthorized data access if unauthorized personnel are able to physically access the NAS.”
Volume Encryption
Volume encryption is the default encryption type available in most QNAP NAS devices equipped with either Intel or ARM processors. Volume encryption locks the entire volume, which in turn may be located on a single disk or multiple-disk storage pool, including a SED secure storage pool as a second encryption layer.
Volume encryption: executive summary
QNAP implements volume-based AES encryption with a 256-bit key length. The encryption provider is standard Linux cryptsetup (LUKS); however, QTS wraps user-provided passphrases to turn them into LUKS keys with a tool named storage_util that likely does not have a Linux equivalent. The encryption key is produced based on the user-provided passphrase. Users can change the encryption passphrase at any time. A 256-byte encryption key file can be produced and downloaded while setting up encryption or at any time later (the user will be prompted for the passphrase). Users can unlock encrypted volumes by either typing the original plain-text password or by uploading the exported key file through the QTS user interface. QNAP provides means for storing encryption keys on the NAS in a “secret location” (presumably, on the built-in DOM storage). We have not searched for stored encryption keys, although this could be possible by analyzing the content of the DOM storage.
Implementation: cryptsetup (LUKS); proprietary tool (storage_util) for wrapping the passphrase (must be run on a QNAP device, not necessarily the one used to create an encrypted volume).
Encrypting existing data: not supported. Users can encrypt new volumes only.
Decrypting encrypted volumes: not supported. Volume must be re-created from scratch.
Revoking compromised keys or changing leaked passwords: supported. If an encryption key is compromised, users can simply change it from the user interface. In our tests, the change of an encryption key requires unmounting and re-mounting the volume, which took around 5 minutes on our test system.
Encryption key: plain-text passphrase (wrapped with a QNAP proprietary tool) or 256-byte key file (must be manually exported).
Potential vulnerabilities: encryption key can be stored on the NAS device for automatically mounting volumes on startup. If this is the case, the encryption key may be extracted from the NAS device and used to access the data. Note that, unlike Synology, QNAP does not offer the ability to store the encryption key on an external USB device. The usual warning “Saving the encryption key can result in unauthorized data access if unauthorized personnel are able to physically access the NAS.” applies.
Locking the encrypted volume is possible from the user interface. Surprisingly, locking an encrypted system volume in our tests was never instant. Instead, the locking process always took several minutes (!) to complete. A percentage bar is displayed during this procedure to allow users to monitor the process. This could do with the encrypted volume being the only volume in the system, hosting the many Qnap system apps and services.

The encryption key can be downloaded and saved into a file with the .key extension. The file size is 256 bytes. This file can be used to unlock the volume should the user forget their password. We verified that the content of the key file is different after the user changes the encryption password. However, since the content of the key file is different even if the user saves it twice without changing the password, it is difficult to judge whether the system uses the same or different encryption keys after the password is changed.
Unlocking the volume is possible by providing either the original password or uploading the encryption key.
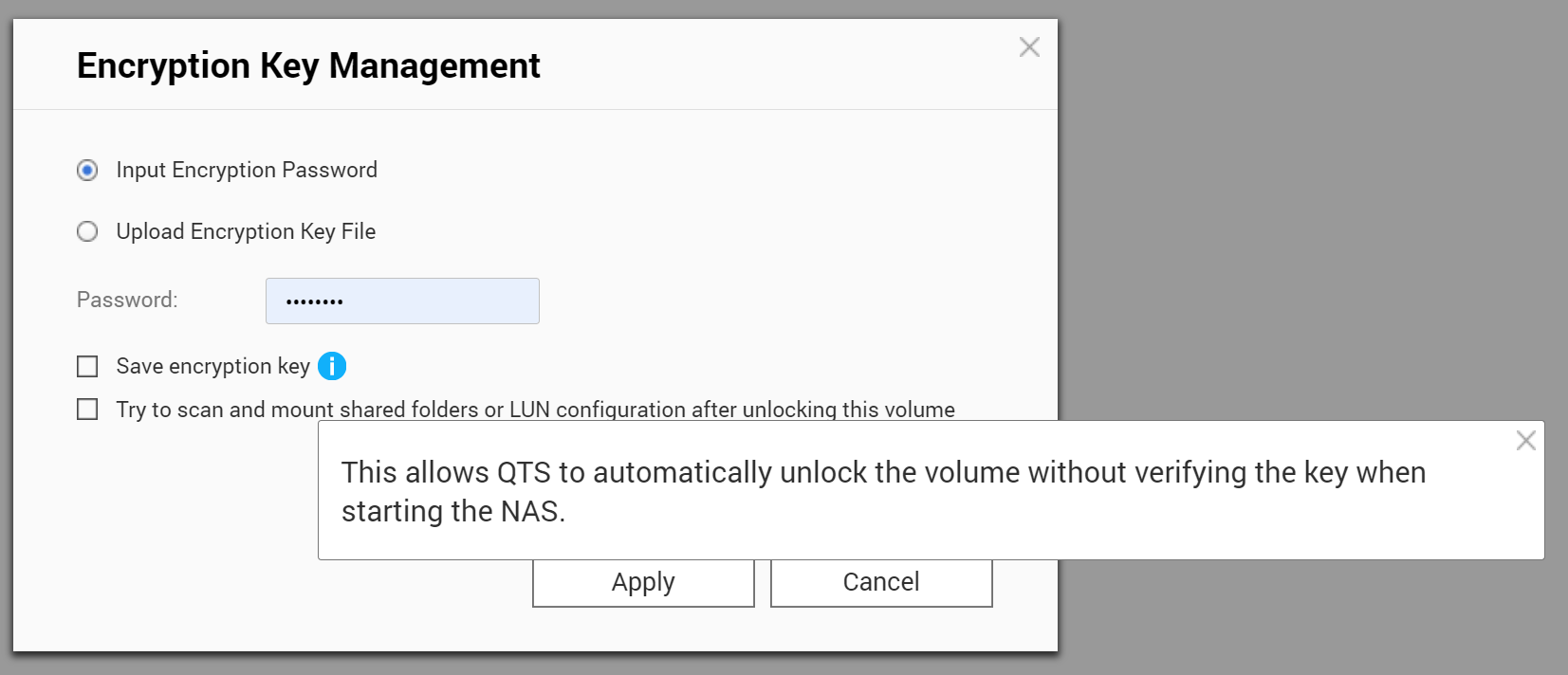
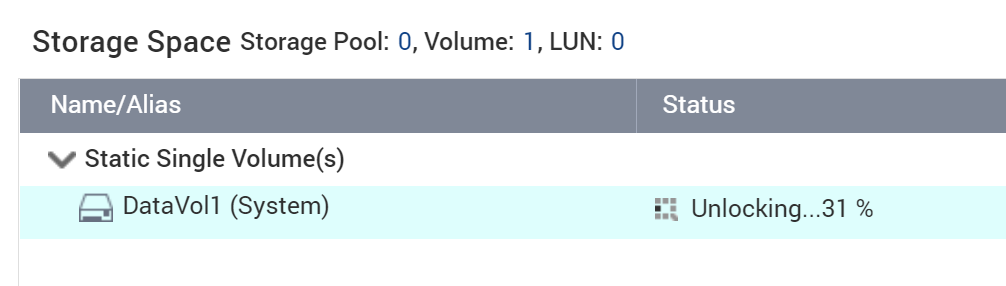
Unlocking the encrypted volume is also far from being instant. The process, once initiated, takes several minutes (about 5 minutes on our QNAP TS-453Be). Being as slow as it is, locking and unlocking volumes is obviously not considered part of the users’ everyday routine (or it might be the case of poor optimization). Either way, it’s slow. Very slow.
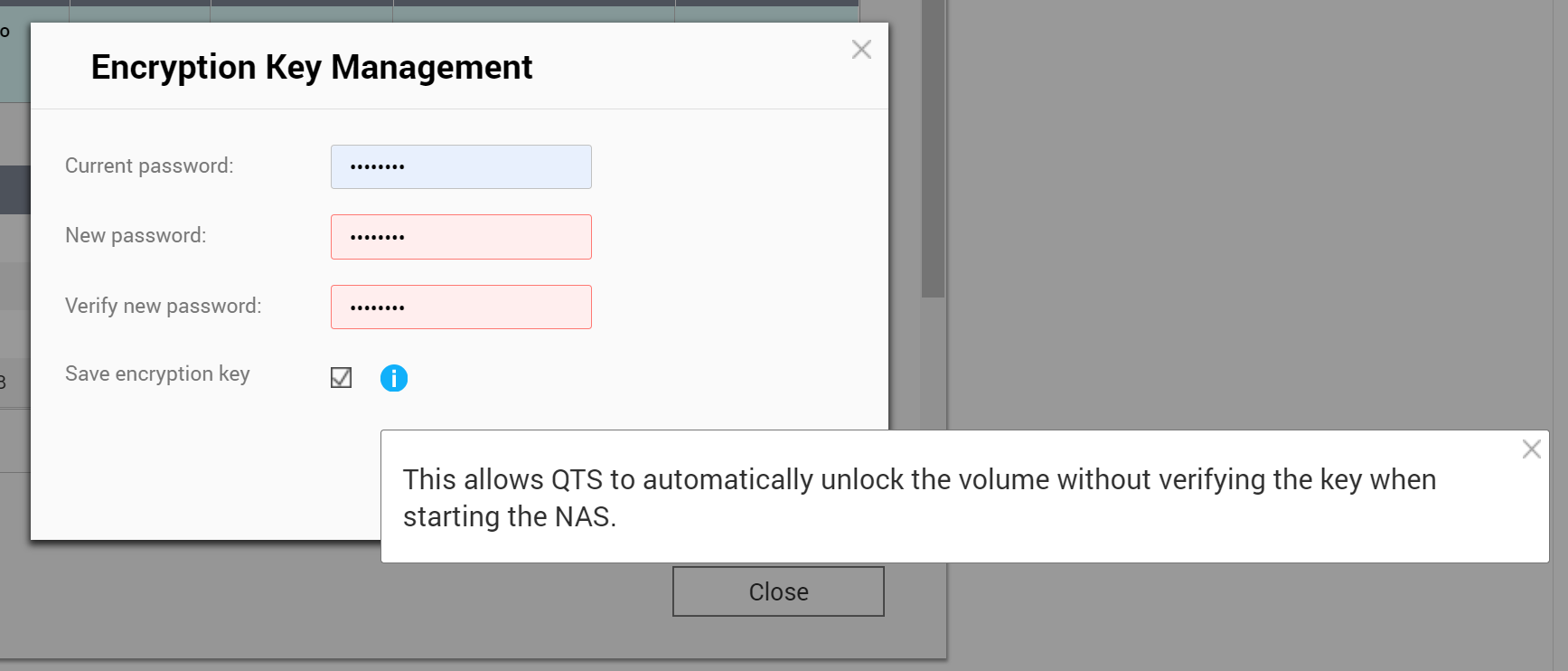
Changing the encryption password is possible via the user interface, albeit it is just as slow as everything else about encryption. While changing the password, users have an option to save the encryption key onto the NAS device (allegedly the built-in DOM storage). By saving the encryption key, the NAS can automatically unlock the volume on startup without prompting the user for the encryption key.
On our test system, it took approximately 4 minutes of “Applying, please wait” until the password was actually changed. It appears that, in the background, the NAS was locking the volume (which takes around 5 minutes), then changing the password. After the password change operation, the volume would be in the locked state. Unlocking the volume takes another 5 minutes, so based on this performance the users are unlikely to change their passwords often.
Volume encryption: technical details
QNAP relies on the tried and proven LUKS standard and uses AES-256 encryption. A step by step guide is available for Mounting QNAP encrypted volumes if the password is known.
It is important to note that QNAP encodes (wraps) user-provided passwords before they can be used with cryptsetup. This in turn means that you will need access to a QNAP NAS device (not necessarily the same device that was used to encrypt the volume) in order to encode (wrap) the passphrase. The following command is used to encode the passphrase (must be executed via SSH on a QNAP NAS device):
/sbin/storage_util --encrypt_pwd pwd=YOUR_PASSWORD
The system will return the encoded version of the password:
Encrypted passwd is: …………………………………..
You can then use the resulting encoded string as the passphrase for cryptsetup luksOpen, which can be executed on a QNAP NAS or on a Linux computer.
cryptsetup luksOpen /dev/mapper/cachedev1 myencrypteddisk
Alternatively, you can encode the password into a key file:
/sbin/storage_util --encrypt_pwd pwd=YOUR_PASSWORD > /tmp/keyfile.key
You can then use the key file to mount the encrypted volume with cryptsetup luksOpen.
cryptsetup -v luksOpen /dev/mapper/cachedev1 ce_cachedev1 --key-file=/keylocation/keyfile.key --key-slot 0
There are multiple discussions on the QNAP Community Forum with additional hints and instructions:
Folder Encryption
In addition to volume encryption, QNAP NAS models based on an Intel processor additionally support per-share file-based encryption. The implementation is very similar to that used by Synology and Asustor.
Encrypted folders can be created on regular volumes as well as on encrypted volumes, delivering an additional layer of protection. QNAP allows encrypting existing folders, as well as permanently decrypting encrypted ones.
Folder encryption: executive summary
QNAP implements folder-based AES encryption with a 256-bit key length. The encryption key is produced based on the user-provided password. Users cannot change the encryption key. They are not allowed to change or revoke compromised passwords either. An encryption key file can be produced and downloaded while setting up an encrypted folder or at any time later (the user will be prompted for a password). Users can unlock encrypted volumes by either typing the original plain-text password or by uploading the exported key file through the QTS user interface. QNAP provides means for storing encryption keys on the NAS in a “secret location” (presumably, on the built-in DOM storage). We have not searched for stored encryption keys, although this could be possible by analyzing the content of the DOM storage.
Note 1: only Intel-based QNAP devices support folder-based encryption.
Note 2: the ability to encrypt shares located on encrypted volumes is relatively new to QNAP. QTS 4.3.5 release notes mention that “Shared folders on an encrypted volume cannot be encrypted. For details, see Volumes.” This is no longer the case, and shared folder on an encrypted volume can be encrypted, which we will demonstrate.
Implementation: eCryptFS.
Encrypting existing data: supported. Users can encrypt existing shares containing data.
Decrypting encrypted folders: supported. Users can decrypt encrypted shares.
Revoking compromised keys or changing leaked passwords: not supported. If an encryption key is compromised, users must take the quest of decrypting and re-encrypting the data, which may take many hours or even days.
Encryption key: plain-text password or key file (must be manually exported while the encrypted share is mounted and unlocked).
The original password is used as a Media Encryption Key. The concept of Key Encryption Keys is not utilized in this implementation; as a result, users cannot change their encryption password (aside of fully decrypting and re-encrypting the share).
Potential vulnerabilities: encryption key can be stored on the NAS device for automatically mounting encrypted folders on startup. If this is the case, the encryption key may be extracted from the NAS device and used to access the data. Note that, unlike Synology, QNAP does not offer the ability to store the encryption key on an external USB device. The usual warning “Saving the encryption key can result in unauthorized data access if unauthorized personnel are able to physically access the NAS.” applies.
Folder encryption can be activated when creating a folder or at a later time.
Users can download the binary encryption key for backup purposes. The encryption key file is saved as “foldername_keyfile” without an extension, and contains 256 bytes of data. Saving another copy of the encryption file produces a file with different content.
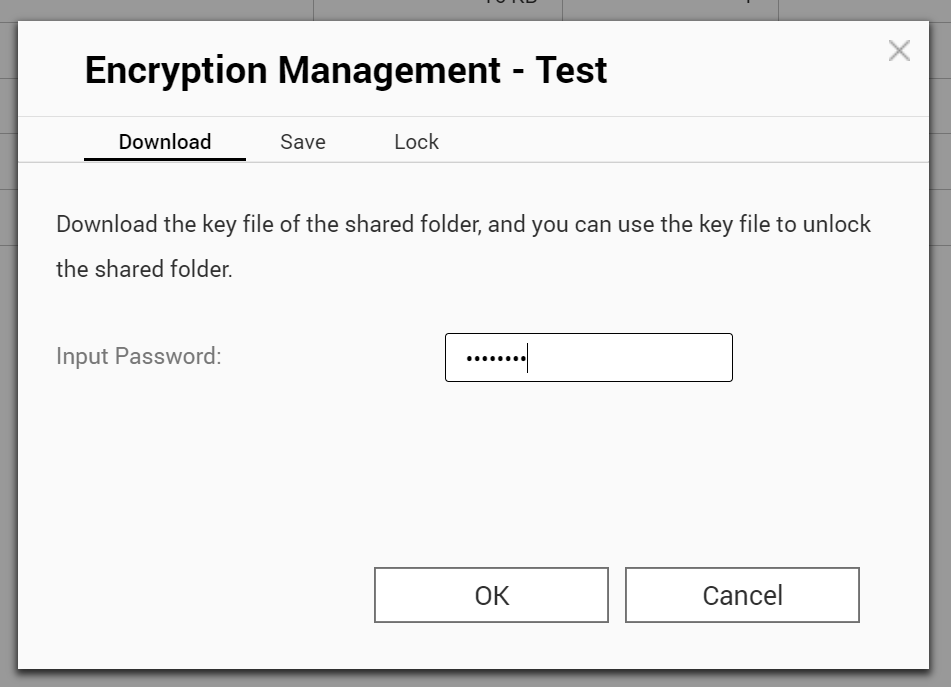
Users have an option to mount encrypted folders automatically on startup; the feature is available under the “Save” tab. Note that the corresponding check box is selected by default, which means that newly created encrypted folders will have their encryption keys stored somewhere on the NAS device by default.
If the user unticks the check box, the next time they open the “Save” tab, the system will prompt for the password in order to save the encryption key.
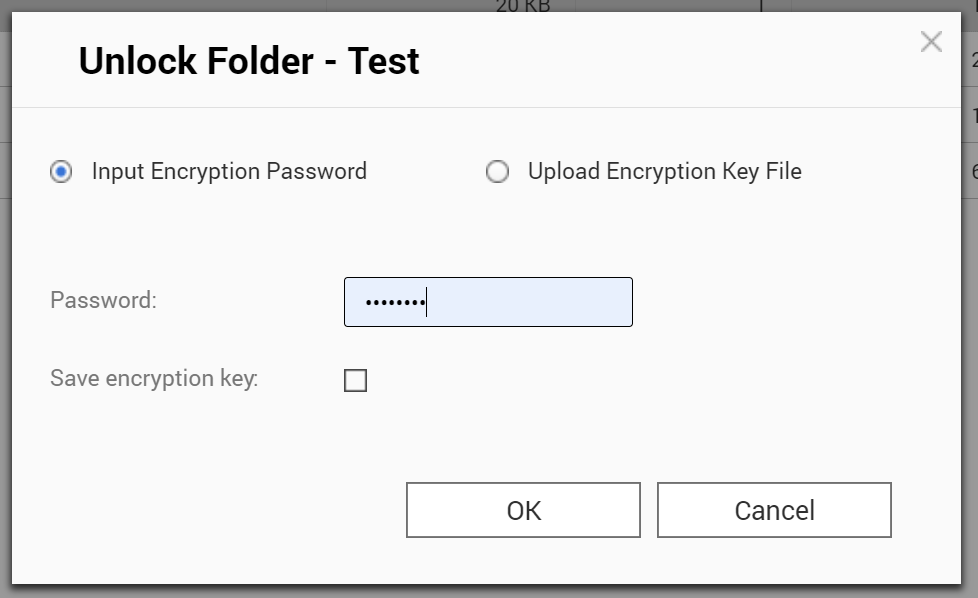
Users can manually lock and manually unlock encrypted folders, which is near instant. Once locked, unlocking the encrypted folder is possible by either providing the encryption password or uploading the encryption key file.
QNAP folder encryption uses the familiar encrypting file system eCryptFS, which is also utilized for similar tasks in Synology and Asustor NAS devices. QNAP’s implementation therefore has similar restrictions, some of which are displayed in the warning message when users encrypt share folders.
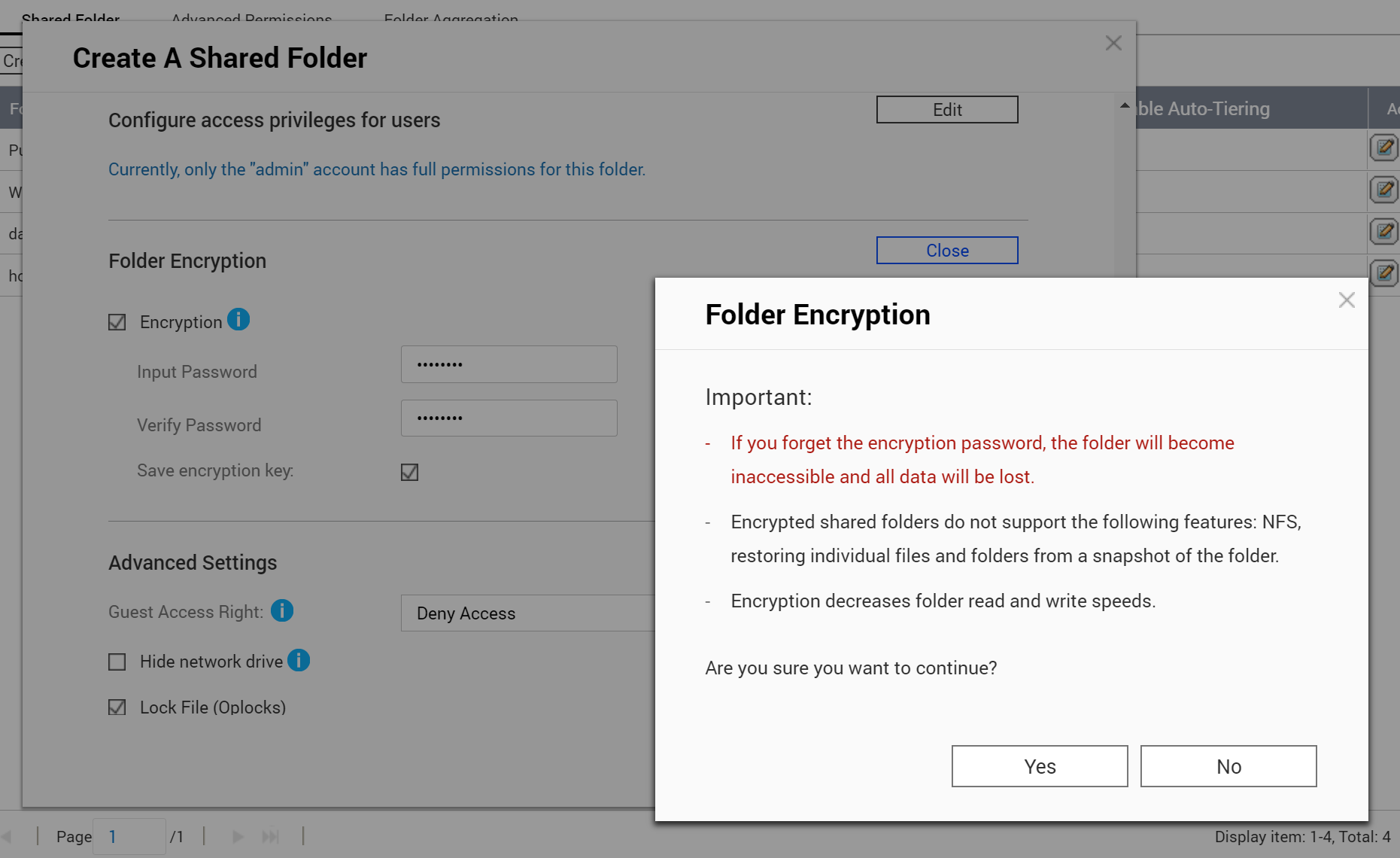
What is not mentioned, however, is the typical eCryptFS restriction on the length of file names. Compare that to Synology’s warning message:
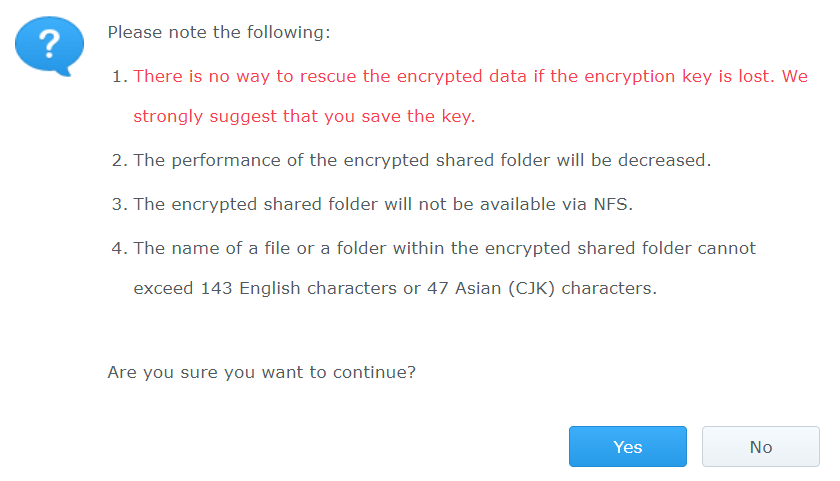
We tested file names of different lengths, and discovered that the same naming restrictions apply. You cannot use file names longer than 143 Latin characters or 47 CJK characters.
Instructions on mounting eCryptFS shares are available in our Synology and Asustor articles, as well as on QNAP user forums.
Multi-Layer Encryption Performance
As mentioned above, Intel-based QNAP NAS devices enable layered protection by allowing t0 encrypt shared folders on encrypted volumes, which may in turn be stored on a SED-encrypted storage pool. We tested the ability to access an encrypted share on a locked volume by attempting to unlock the share. This worked as expected (or, rather, it did not work, just as we expected). An attempt to access a folder on a locked volume failed even though the correct password (for the encrypted folder) has been specified.
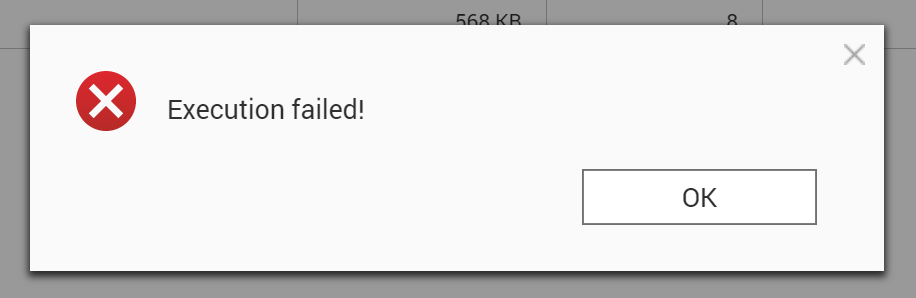
This proves that QNAP NAS devices do indeed have effective layered protection.
How does this two-layer encryption affect performance? We tested read and write performance using a single gigabit connection.
Writing a single large file to an encrypted share on an encrypted volume resulted in the performance of about 95 MB/s, peaking at 100 MB/s. Read performance was roughly 94 MB/s, peaking at 96 MB/s.
Writing to an unencrypted folder on the same encrypted share resulted in 107 MB/s writes and 95 MB/s reads.
Finally, writing to an unencrypted folder on an unencrypted volume resulted in 115 MB/s writes and the same 96 MB/s reads.
Conclusion
QNAP implements layered protection, allowing to protect against various threats by selectively activating the required encryption layers. Self-encrypting disk (SED) encryption effectively protects data in an event a hard drive needs warranty service, and enables instant secure destruction of the data. Volume encryption achieves a similar purpose in multiple-disk configurations and/or when SED is not available on given hardware. The final layer, folder-based encryption, protects data on per-share or per-user basis, enabling administrators to produce encrypted backups of encrypted folders without passing (or even knowing) the user’s encryption passphrase.

















