The iPhone backup is one of the hottest topics in iOS forensics. iTunes-style backups are the core of logical acquisition used by forensic specialists, containing overwhelming amounts of evidence that is is unrivaled on other platforms. The backups, as simple as they seem, have many “ifs” and “buts”, especially when it comes to password protection. We wrote a thousand and one articles about iOS backup passwords, but there is always something fresh that comes out. Today we have some new tips for you.
The “iTunes” Backups
Although there are several methods for extracting data from an iPhone, iOS backups remain the main source of evidence. Pulling a backup from the device is nearly always possible regardless the iPhone model and iOS version, but only if the device is unlocked or you can unlock it. We published several dozen articles on iTunes backups, and if you are not familiar with this topic, I recommend you to start with The Most Unusual Things about iPhone Backups; I bet you are going to learnt something new.
We put the term “iTunes” in quotes simply because there is no iTunes in macOS anymore starting with macOS Catalina (same for macOS Big Sur). In these new versions of macOS, backups are created via Finder. There is no difference in the data acquired from the device regardless of whether you use Finder or the old iTunes app.
Most forensic packages avoid using the term “backup”. Instead, they prefer to call it “logical acquisition” or “logical extraction”, sometimes “advanced” or “extended”, and sometimes even “method N”. In contrast to Android logical extraction, everything is much simpler with iPhones. The logical advanced/extended acquisition/extraction (whatever they call it) may include the following data:
- General device information (model, name, and some other parameters)
- The backup (iTunes-style)
- Media files (photos, videos, and music, including some metadata)
- Shared files
- Diagnostics logs
And that’s about it. The backup is usually the major source of evidence that includes most of the data from the device.
The Backup Password
As we have already explained, backups are often protected with passwords. There are two separate issues there:
- If a backup password has been configured by the device owner and you do not know it, this is a problem.
- If a backup password is not set, you will need to set it yourself.
Both issues need an explanation. But let’s review the changes made by Apple regarding the backup passwords first:
- iOS prior to and including iOS 9.x: the password can be effectively attacked
- iOS 10.0: weak backup password, implementation flaw, very fast attacks
- iOS 10.1: vulnerability fixed, back to iOS 9 level of protection
- iOS 10.2: very strong password encryption, extremely slow attacks
- iOS 11: made it possible to reset backup passwords in Settings (with some consequences)
- iOS 13: changing the backup password requires the passcode
The problem is that password-protected backups contain more data than ones without password. Speaking of the keychain, even if the keychain records are always there, we can decrypt them from a backup only if the password is set and known.
Long story short: if no other extraction options are available and you can only pull a backup, you need the backup password to be set (and known).
The Backup Password II
Back in 2016, we realized that if a backup password is not set, we just need to set it ourselves, pull the data, and remove the temporary password in the end. See our historical iOS Logical Acquisition: The Last Hope For Passcode-Locked Devices? article, in particular:
We know how to deal with encrypted data. If no backup password is set, the keychain will remain securely encrypted with an unbreakable hardware key. For this reason, we’ll automatically set a temporary password (“123”) when acquiring devices without a backup password. (We’ll reset it back after extraction.) This allows decrypting keychain data that would otherwise remain inaccessible.
Secure Enclave introduced in 64-bit devices (iPhone 5s, 6/6s/Plus) effectively locked us out, blocking access to the hardware key regardless of jailbreak status. As a result, the physical acquisition process can extract but cannot decrypt the keychain, while keychain data backed up without a password remains similarly inaccessible.
We addressed this issue by making iOS Forensic Toolkit set a temporary password (“123”) when performing logical acquisition. After the extraction, the password is reset to its original state. Since password-protected iOS backups allow access to keychain, you can successfully decrypt keychain data by using that password.
There is actually more than that – in every new iOS version, Apple puts more data into password-protected backups only (such as Safari browsing history, Health records etc).
Backups in macOS Big Sur
We try to track every change in the backup engine, mostly on iOS devices but not on the host system (Windows or macOS). In macOS Big Sur, backup encryption options are really confusing:
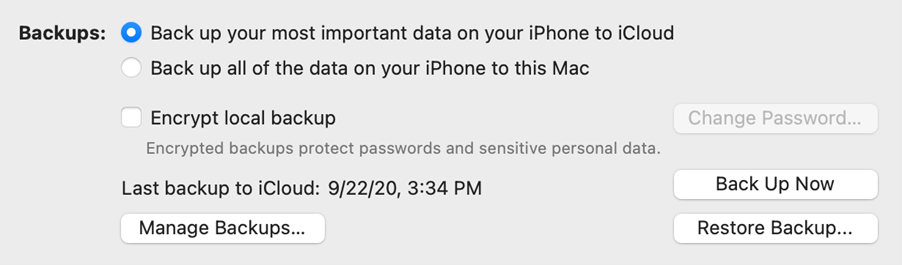
If you switch to the local backup, you now get the following:
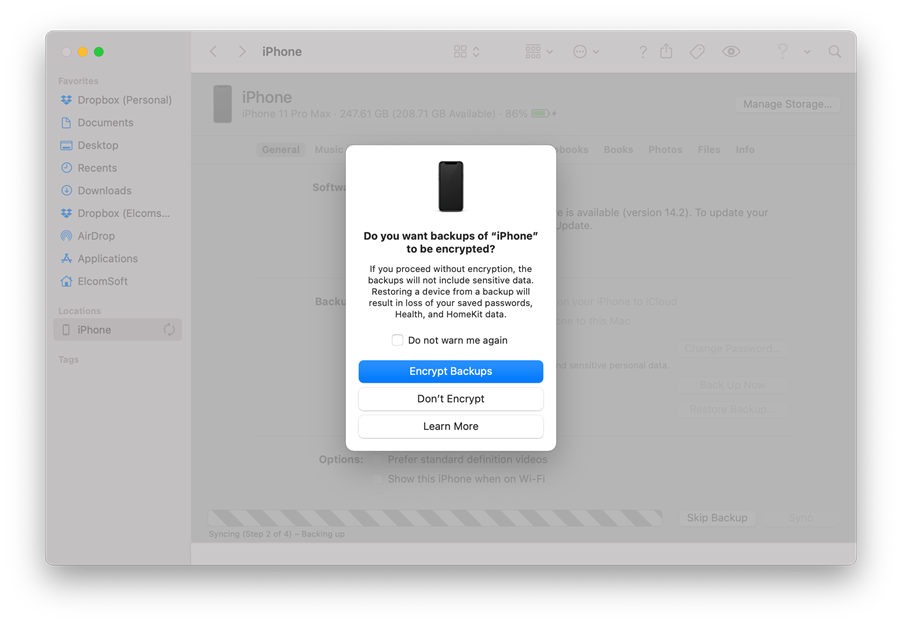
Use iOS Forensic Toolkit instead (if you are doing backup extraction), and we will take care of the backup password on our end to make sure you get most of the data available.
Default Backup Passwords
Following our example, other mobile forensic vendors started to set temporary backup passwords. And that’s a good move.
Here are the default backup passwords set by various forensic packages (including ours):
- Elcomsoft iOS Forensic Toolkit: 123
- Cellebrite UFED: 1234
- MSAB XRY: 1234
- Belkasoft Evidence Center: 12345
- Oxygen Forensic Detective: oxygen
- Magnet AXIOM: mag123
If you are analyzing a password-protected backup acquired with so-called “logical acquisition” and have no idea what the password is, try one from the list first. If it does not work, you can also try the device passcode (you should know it) or the password to Apple ID (surprisingly, it often works).
Recovering Backup Passwords
What if the backup password is not the default one, and it has been set by the device owner? We have a comprehensive guide The Four Ways to Deal with iPhone Backup Passwords. If you have no choice but try to break it, we’ve got good news for you: now you can do it much faster with NVIDIA RTX 3080 or 3090. Still, for iOS versions 10.2 and newer, the maximum backup password cracking speed we were able to achieve is only 350 passwords per second. Compare that with more than 220 thousand passwords per second for older iOS versions! It is much better than just a few passwords per minute on an Intel CPU, and allows to crack at least short and simple passwords in a reasonable time: 7 digits, or 6 letters in a single case, or 5 mixed-case letters and numbers.




