True physical acquisition is back – but only for a handful of old devices. We’re adding support for unlocking and forensically sound extraction of some of Apple’s legacy iPhones. For iPhone 4, 5, and 5c devices, we’re adding software-based passcode unlocking and device imaging functionality. Moreover, on some models you won’t even need to break the passcode in order to make a full disk image! In this walkthrough we’ll describe the steps required to image an iPhone 4, iPhone 5 or iPhone 5c device.
Imaging the iPhone 4, iPhone 5 and iPhone 5c devices
Once you obtain the passcode (here’s how), you can start imaging the device by extracting and decrypting the keychain, extracting the encryption keys, creating and decrypting the disk image.
First and foremost, do break the passcode. Once you have the passcode, extract the keychain and image the disk. Even if you cannot break the passcode, still do these steps: you will still have access to some data (almost everything in iOS 4 through 7, or just a few bits and pieces in iOS 8 and 9).
Pre-requisites
In order to unlock and image an iPhone 4, 5, or 5c, you’ll need all of the following:
- Elcomsoft iOS Forensic Toolkit 6.70 or newer (Mac edition).
- A Mac computer.
- A USB-A to Lightning cable (no Type-C please, but you may use a Type-C to Type-A adapter).
- A supported iPhone model in a working condition that can be connected to the computer and switched to DFU mode.
Why macOS, and why macOS only? While the iPhone 4 can be broken with a fairly simple (yet very powerful) limera1n exploit, newer models, including the iPhone 5 and 5c, require checkm8. The checkm8 exploit is highly dependent on the USB driver (it’s doing things beyond the standard protocol). You know what we’re talking about if you get that there is no checkra1n installer for Windows.
Why no love for the iPhone 4s? It’s the same thing. The iPhone 4s implementation of the exploit only exists on Arduino with a specific USB controller. If one wanted to do it in Windows or even in macOS, one would need creating a modified USB driver, which (signing issues aside) would be extremely labor-intensive work with poor reward.
Imaging walkthrough
Before you begin, you may want to briefly power the iPhone on to determine the type of the passcode (4-digit, 6-digit or alphanumeric). The type of the passcode can be determined by powering on the iPhone and observing the displayed login prompt.
- Launch Elcomsoft iOS Forensic Toolkit 6.70 or newer.
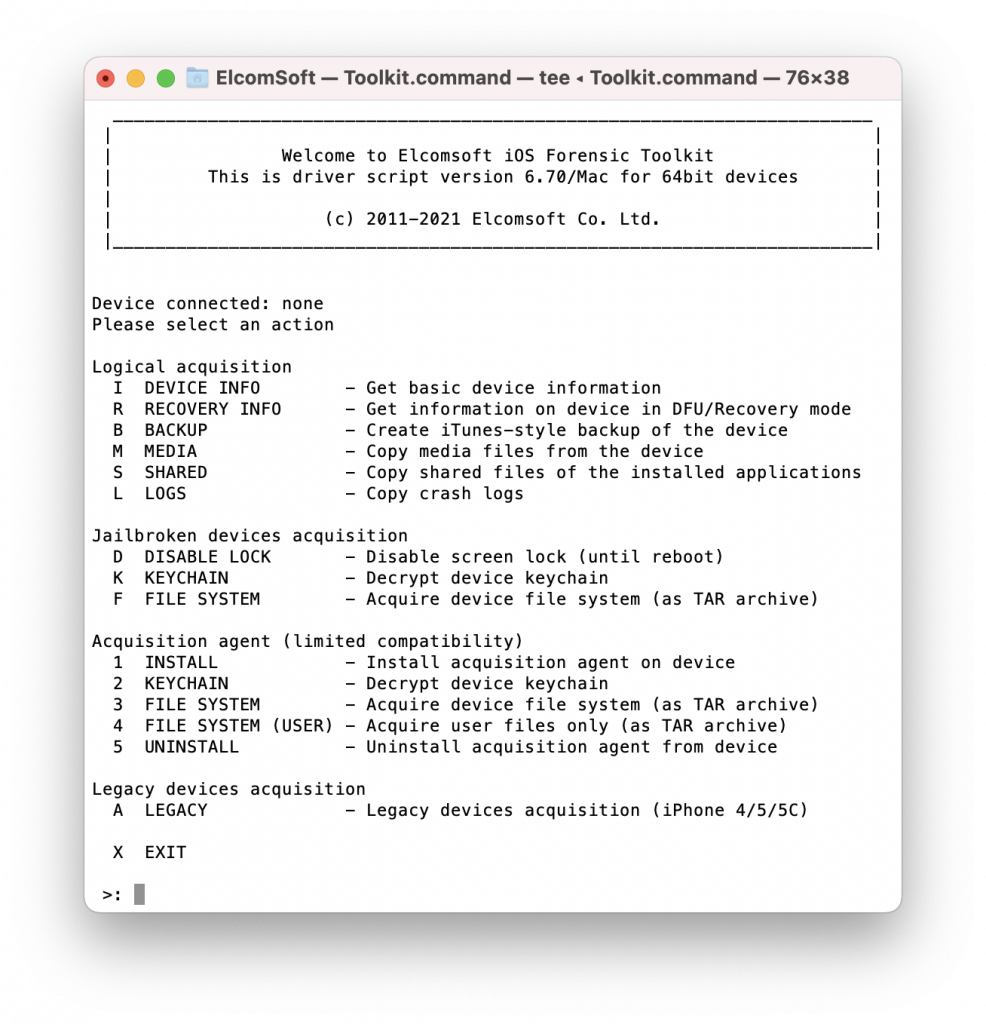
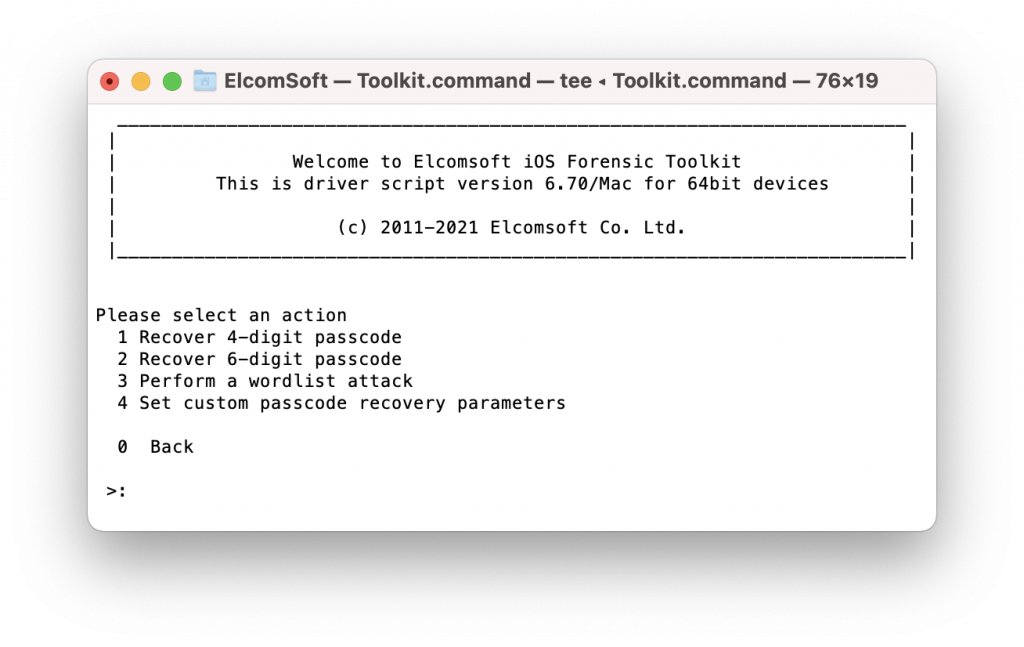
- From the main menu, select “A” (LEGACY).
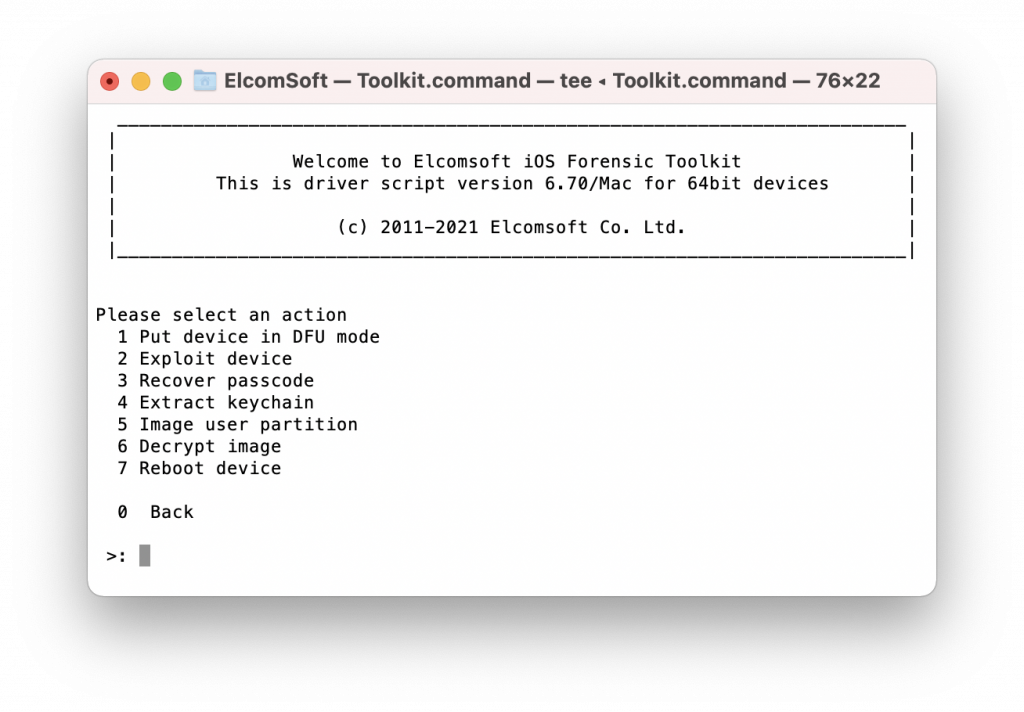
- Using the [1] command, switch the iPhone to DFU mode. The switch cannot be performed automatically; EIFT will display step by step instructions with precise timings to help you switch the device into DFU. Note: for the purpose of installing the exploit, you may get a higher success rate if you switch to Recovery first, followed by DFU mode.
- Using the [2] command, install the exploit. In the Terminal window, you will see the following output:
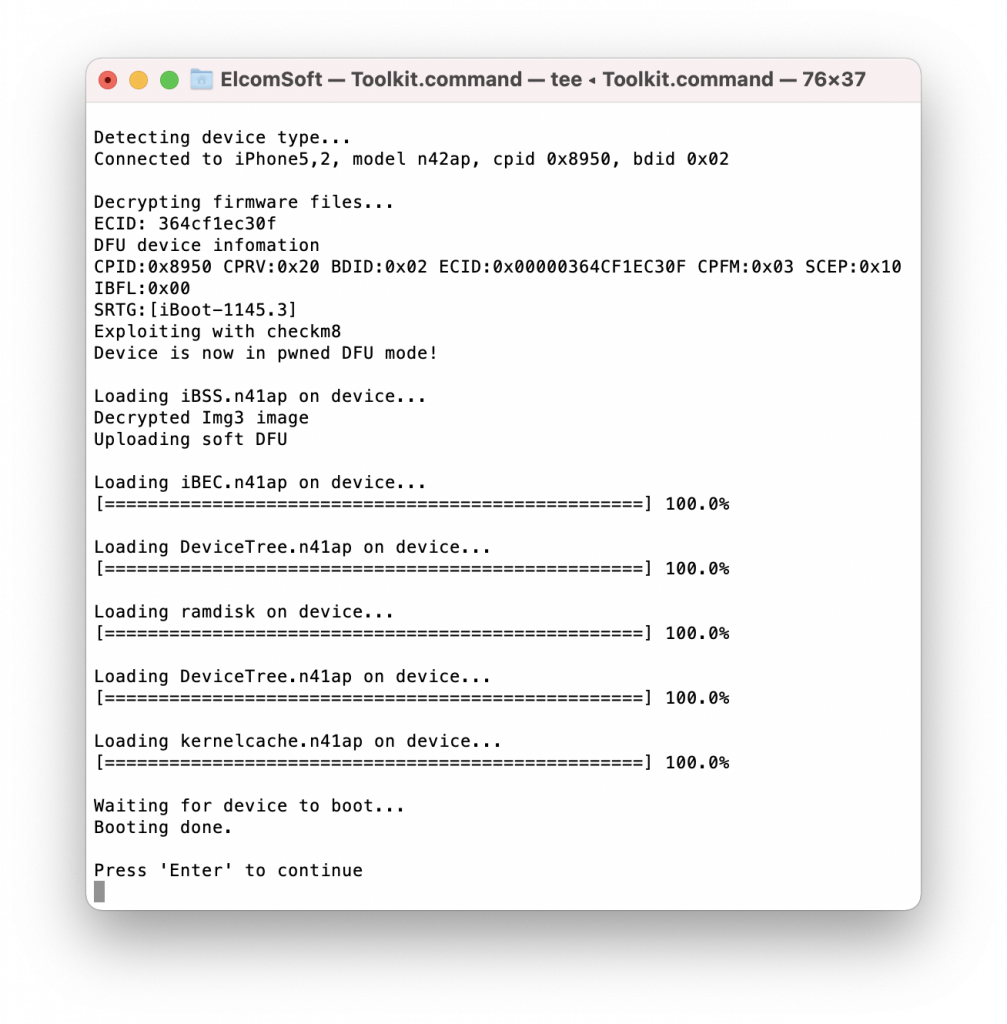
The iPhone screen may look different depending on the model. The iPhone 4 will display the following screen:
The iPhone 5 will look different: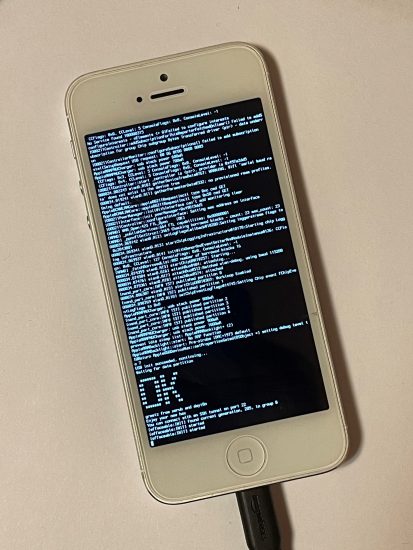
- Recover the passcode, if you haven’t already done so. The type of the passcode can be determined by powering on the iPhone and observing the login prompt.
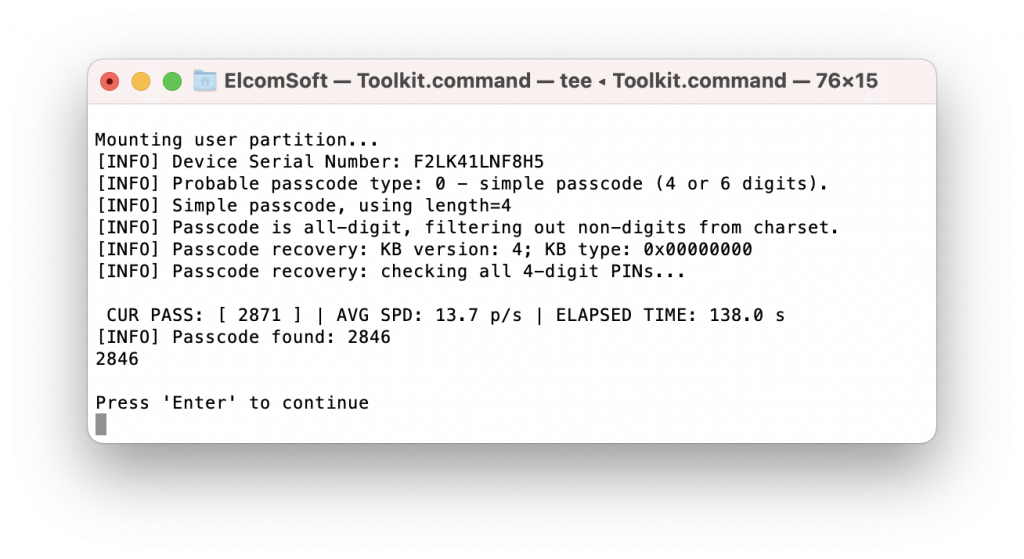
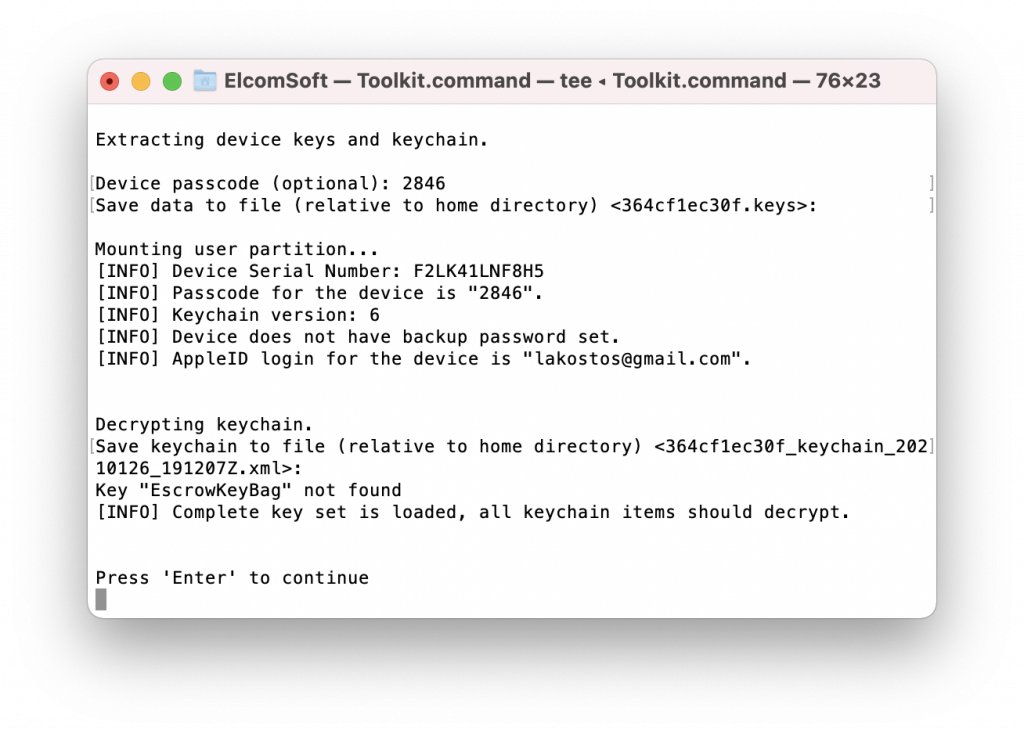
- Go back to the LEGACY menu, and select [4] to extract the keychain. This step is obligatory to decrypt the user partition. Note that the keychain cannot be completely decrypted without the screen lock passcode:
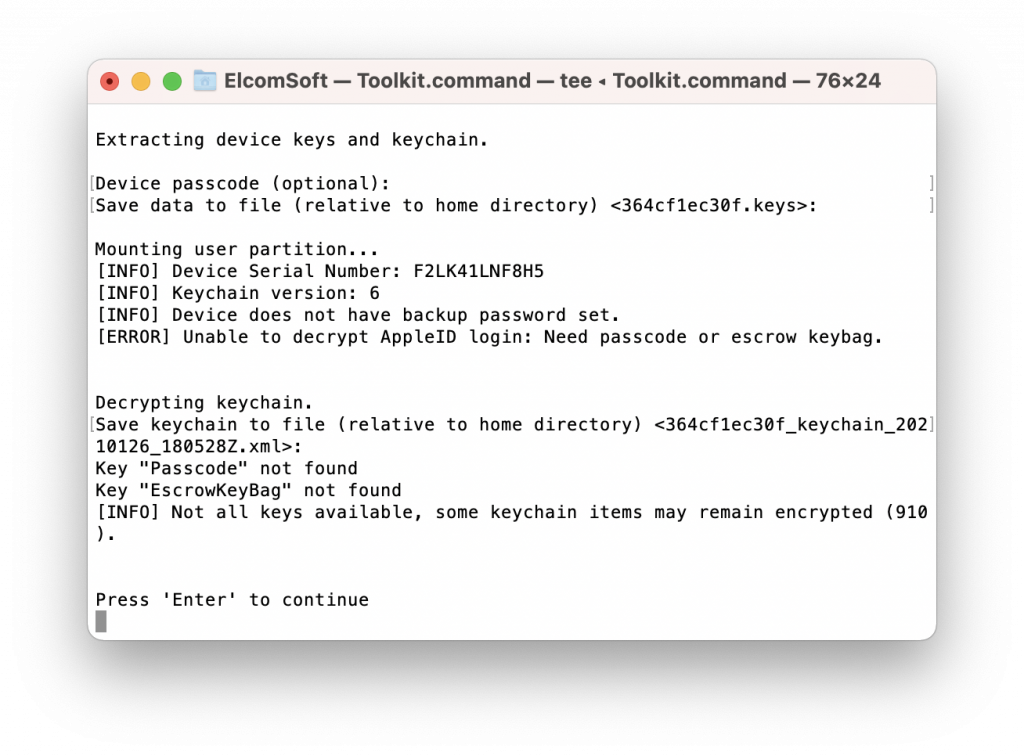 If you know the passcode, provide it in order to decrypt the keychain:
If you know the passcode, provide it in order to decrypt the keychain:
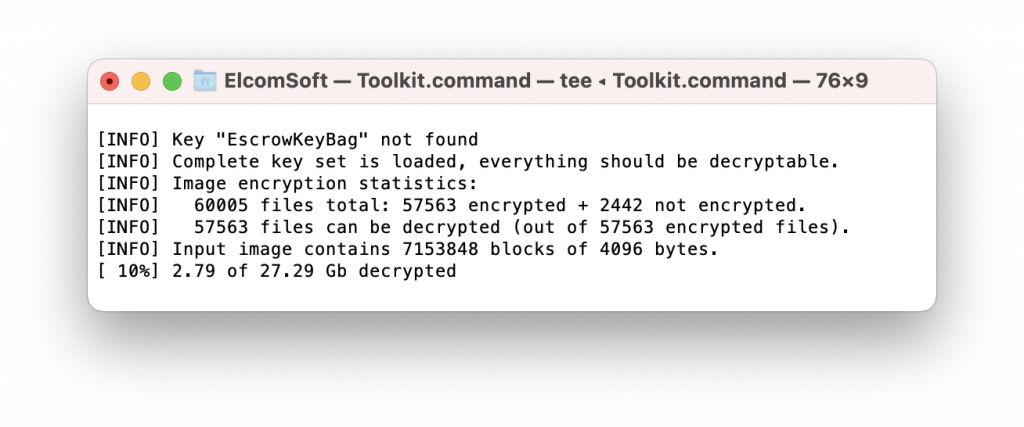
- Enter [5] to image the user partition. This may take a long time depending on the device capacity.
- Enter [6] to decrypt the user partition you’ve imaged. Note: you will need to extract the keychain first, as the encryption keys are stored there.
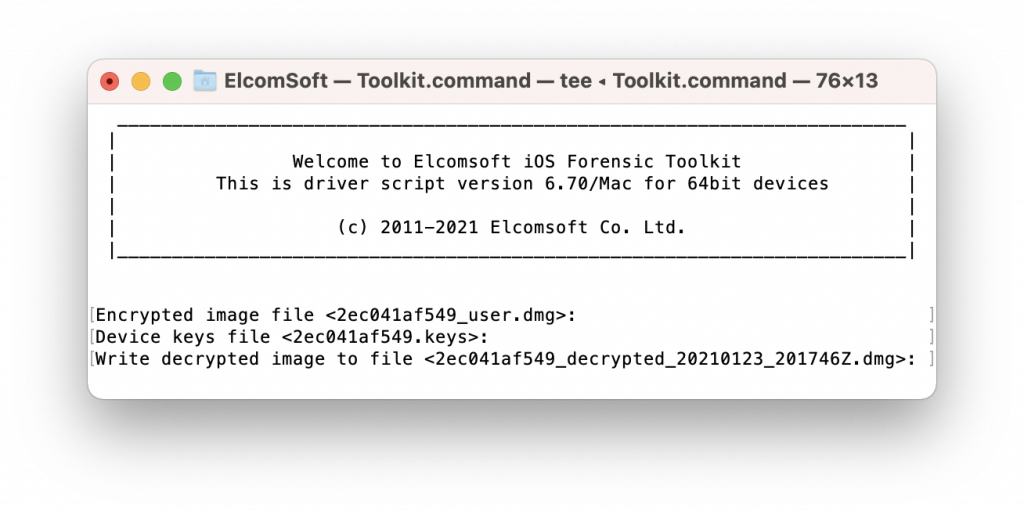
- If you failed to recover the passcode, only some data will be decrypted:

- If you were able to recover the passcode and extract the keychain, the complete data set will be decrypted.