Real-Time Surveillance via Apple iCloud
November 19th, 2021 by Oleg Afonin
Category: «General»
Is surveillance a good or a bad thing? The answer depends on whom you ask. From the point of view of the law enforcement, the strictly regulated ability to use real-time surveillance is an essential part of many investigations. In this article we’ll cover a very unorthodox aspect of real-time surveillance: iCloud.
Smartphones have become commonplace. These personal communication devices are used for everything from browsing the Internet to socializing with other users, taking pictures, shopping and doing a lot more. The “lot more” may include activities that some users would prefer to hide. Modern smartphones are designed to keep everything stored on the device securely encrypted to keep the data away from attackers with physical access to the device. There are ways that do not require physical access to the device in order to access the user’s data: one can get lots and lots of information about the user, often in real time, by accessing the vendor’s cloud service. This effectively turns smartphones into always-on personal surveillance devices.
Before we begin, it is important to realize several things: what Apple knows about its users; what Apple does not know (or does not want to know) about them; and what you can extract based on what you know. Sounds confusing? Read along!
What Apple knows
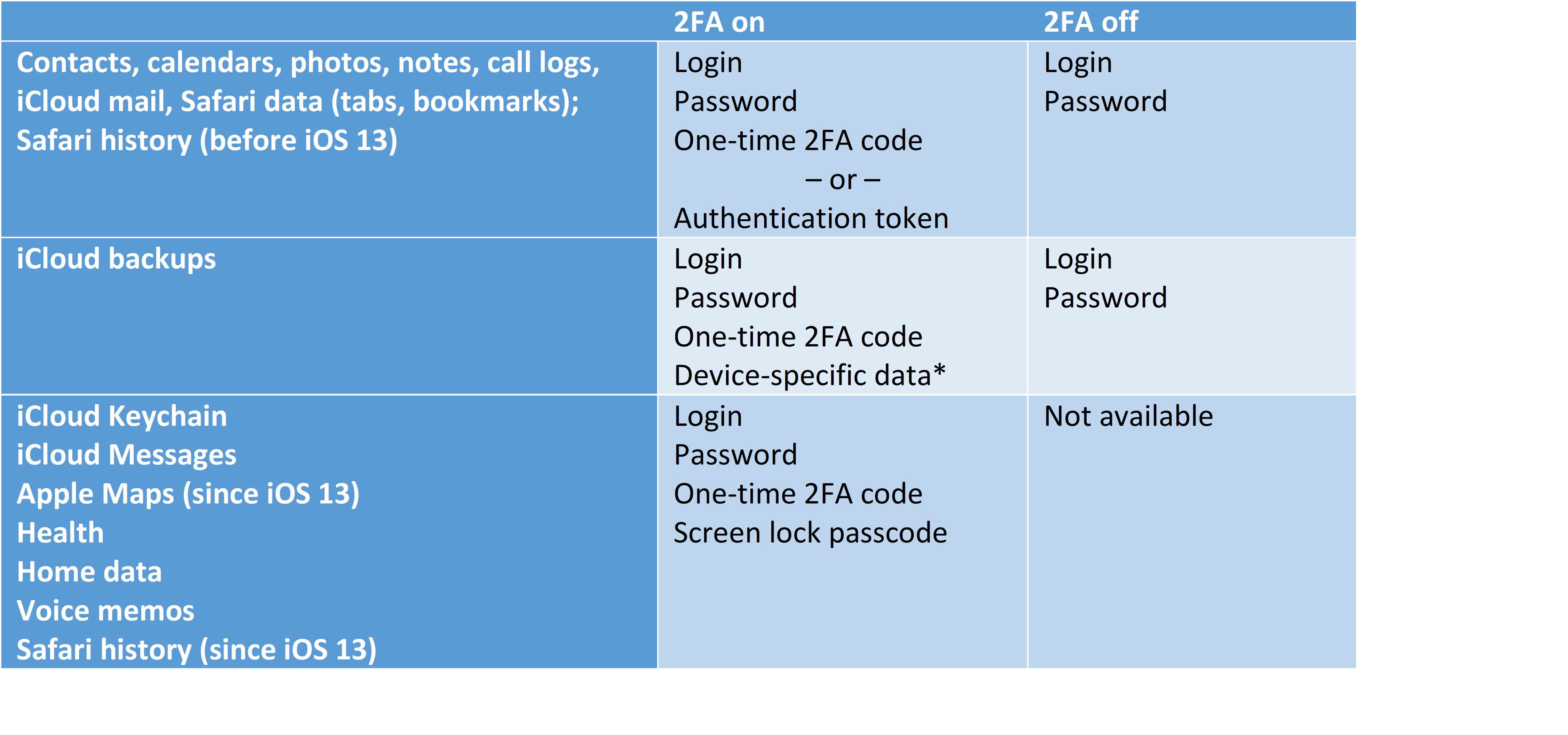
What Apple knows about its users is not necessarily what you will be able to get. Some parts of the data are specific to Apple the company, such as the user’s visits to Apple Store or their Genius Bar appointments. Some parts of the data are simply not stored in iCloud (or at least we don’t know if they are). Some other data, such as the user’s keychain passwords, are stored in iCloud but Apple does not have access to that data because of end-to-end encryption.
So what does Apple know about its users? At this time, the following types of data are synchronized with iCloud without end-to-end encryption:
- Account information
- Photos (iCloud Photo Library), if enabled and if there is enough space in the user’s iCloud account
- Contacts, notes, calendars
- Call history
- Wi-Fi access points and passwords
- Apple Wallet
- iCloud Mail
- Books (iBooks), including PDF documents and third-party books added by the user
- Stocks, Weather
- Shortcuts
- iMovie, Clips
- iCloud Drive: Pages, Numbers, Keynote documents, other files
All of that data is synchronized with iCloud automatically and almost in real-time.
What Apple does not know
As we have mentioned above, some types of data, such as the user’s keychain passwords, are stored in iCloud but Apple does not have access to that data because of end-to-end encryption.
- Safari history, bookmarks, open tabs
- Apple Maps (searches, routes)
- iCloud Keychain (the passwords)
- Messages (SMS, iMessages, attachments)
- Apple Health (steps, heart rate if wearing Apple Watch, etc.)
- Screen Time password
- Voice memos
These types of data are additionally encrypted (on top of the “normal” iCloud encryption) with a key that is re-encrypted with the user’s device passcode (or multiple passcodes if there are several devices with different passcodes). Since Apple does not know the user’s device passcode, it does not have access to the user’s passwords or messages and does not know which Web sites they visit in Safari or what tabs they have open on their device. Apple refers to this protection scheme as “end-to-end encryption”. As a rule of thumb, Apple will not provide these types of data when serving legal requests; however, you may still be able to access them almost in real-time if you know the user’s password or have access to one of their trusted devices.
A trusted device can be used for surveillance
What happens if you lose your iPhone? If it meets certain conditions, it can be used to establish surveillance over your entire iCloud ecosystem, which includes data from all other devices.
Which iPhones can be used for surveillance?
- It’s an old model (up to and including the iPhone 8/8 Plus/X range), and the screen lock passcode is known or empty, or
- It runs an old version of iOS (up to and including iOS 14.3 at this time, while 14.5.1 is in the works), and the screen lock passcode is known or empty.
There are additional caveats. While the iPhone 8/X can be exploited, one will have to remove the screen lock passcode to install checkra1n if they are running iOS 14 or later. This effectively prevents access to the data protected with end-to-end encryption, yet all other information will remain accessible. In addition, if these models are running iOS 15, you won’t be able to install checkra1n at all as it currently only supports iOS 14.x and older versions.
Granted, it is extremely unlikely that you lose an old iPhone with its passcode conveniently written on the back, and you hadn’t updated it for a year, but you’ll be surprised how many of these devices are kept in the backroom of many forensic experts.
The tool
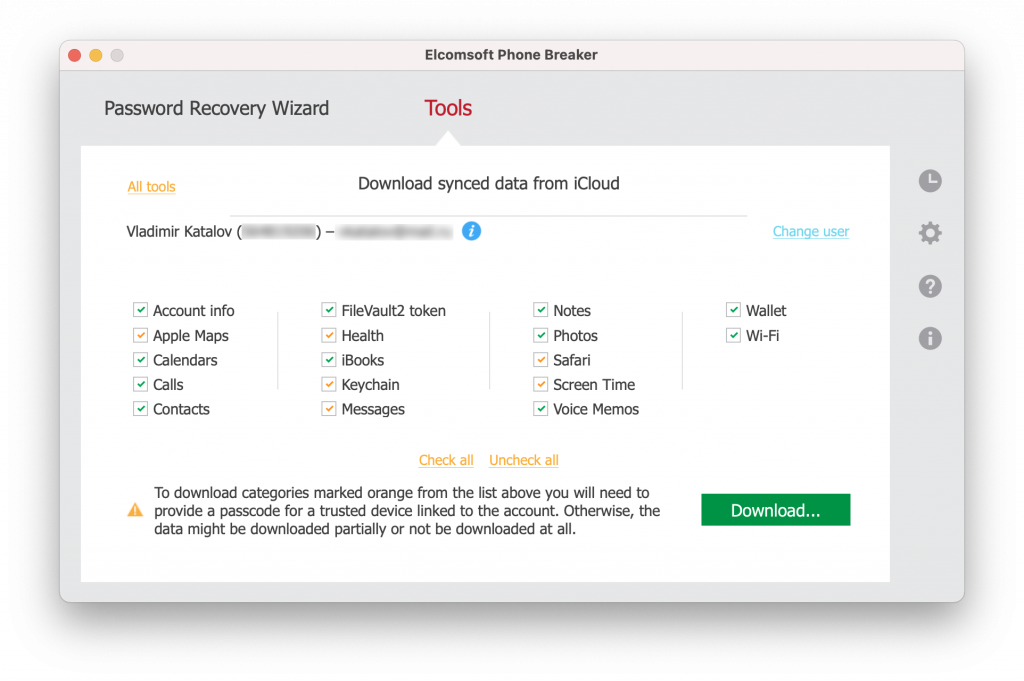
We have a tool for that! Elcomsoft Phone Breaker makes it possible to download the content of the user’s iCloud, enabling access to synchronized data, including end-to-end encrypted categories. At this time, Elcomsoft Phone Breaker is the only third-party solution on the market allowing to access end-to-end encrypted data and iCloud backups saved by iPhone and iPad devices running any version of iOS.
Additional information
We have more information on the subject, namely in these articles:
Conclusion
iCloud account credentials can be used to establish real-time surveillance over the users of Apple’s ecosystem. The most relevant types of data include iCloud messages (SMS and iMessage), Web sites and tabs opened in the Safari browser, as well as Health data (steps and heart rate). It is not a coincidence that all of these categories are end-to-end encrypted, requiring the use of one of the user’s screen lock passcodes to access and decrypt.
iCloud Photos, if enabled, are also a great source of data that is not protected with end-to-end encryption. Aside of their documental and artistic context, the photos typically store precise location information in the accompanying EXIF tags, which is one of the more important types of information for the purpose of real-time surveillance.




