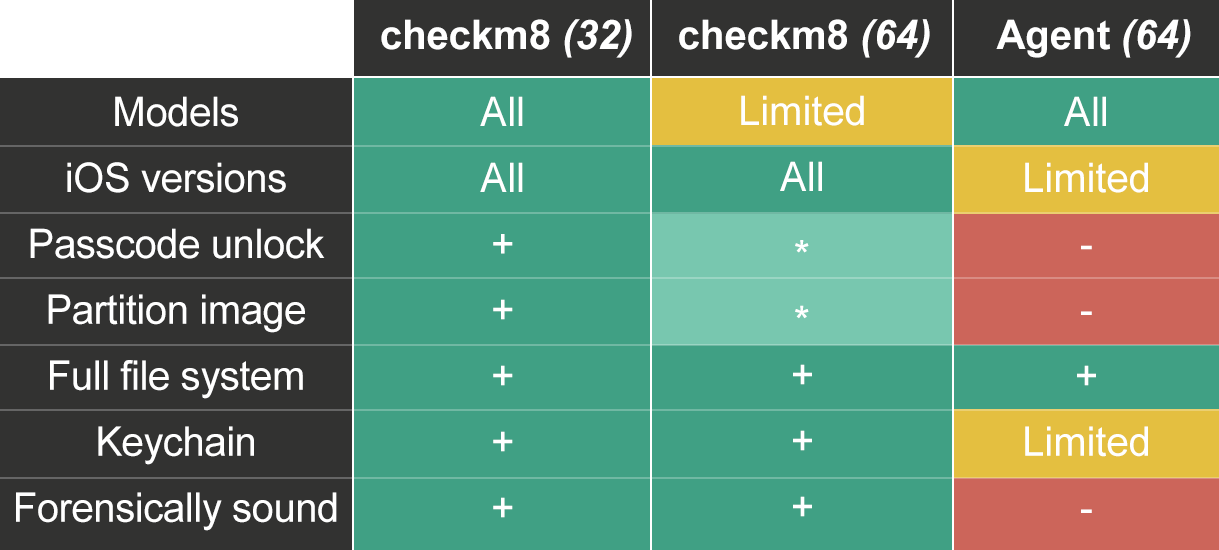
The seventh beta of iOS Forensic Toolkit 8.0 for Mac introduces passcode unlock and forensically sound checkm8 extraction of iPhone 4s, iPad 2 and 3. The new solution employs a Raspberry Pi Pico board to apply the exploit. Learn how to configure and use the Pico microcontroller for extracting an iPhone 4s!
Introduction
We are introducing a hardware add-on to help experts use checkm8-based extraction on supported iPhone and iPad devices. The Raspberry Pi Pico board can be used to streamline the process of placing the iPhone or iPad into DFU and performing the initial steps of the exploit. By offloading this job onto the hardware board we are making the process easier for the expert while adding support for Apple hardware for which software-only support is unfeasible or plain impossible.
For most devices susceptible to the checkm8 exploit experts can do with or without the Pico board. However, there is one notable exception, which includes the entire range of Apple devices based on the A5 SoC: the iPhone 4s, iPod Touch 5, iPad 2 and 3, the original iPad mini and Apple TV 3. Due to device specifics, the exploit requires a fine-grained control that we get by using a microcontroller. To achieve this task, checkm8 developers had only released the exploit for Arduino boards, while we opted for the Raspberry Pi Pico instead.
If you need to unlock and/or extract an iPhone 4s, you will require a custom firmware image for the Pico board. The firmware image is included with iOS Forensic Toolkit free of charge. We are planning to add support for newer generations of Apple devices in near future.
Compatibility
This guide is applicable to the iPhone 4s, iPod Touch 5, iPad 2 and iPad 3, iPad Mini, Apple TV 3 devices running any version of iOS. In the table below, this guide is applicable to the first column checkm8 (32).
Before you begin
Checkm8 is a complex exploit with several pre-requisites, while the iPhone 4s uses a different USB controller requiring a very special approach for entering pwned DFU. Make sure you have everything handy before you begin.
- A Mac or Linux computer. You will need a Mac or a Linux PC to install the exploit and perform the extraction. We support both Intel-based and M1-based Macs with a universal build of iOS Forensic Toolkit. For Linux, we currently only support Intel-based computers.
- iOS Forensic Toolkit 8. You will require the Mac or Linux edition of the tool.
- A compatible iPhone 4s, iPod Touch 5, iPad 2 or iPad 3, iPad Mini, Apple TV 3 device. At this time, devices based on the A5 (S5L8940), A5 Rev A (S5L8942) and A5X (S5L8945) are supported. The device must be functional enough to be placed into DFU mode.
- If the screen lock passcode is unknown, you will have an option to recover it.
- A Raspberry Pi Pico board built to specification (see below).
Building the Pico board
You will need a Raspberry Pi Pico to apply the checkm8 exploit to the iPhone 4s. Since the Pico board has a single USB port, which will be used to connect to the iPhone, you will also need a power source. We recommend the following configuration:
- A Raspberry Pi Pico board with soldered pin headers:

- A battery “UPS” solution for the board such as the Pico-UPS-A-EN (Amazon link, manufacturer) as well as a compatible battery.
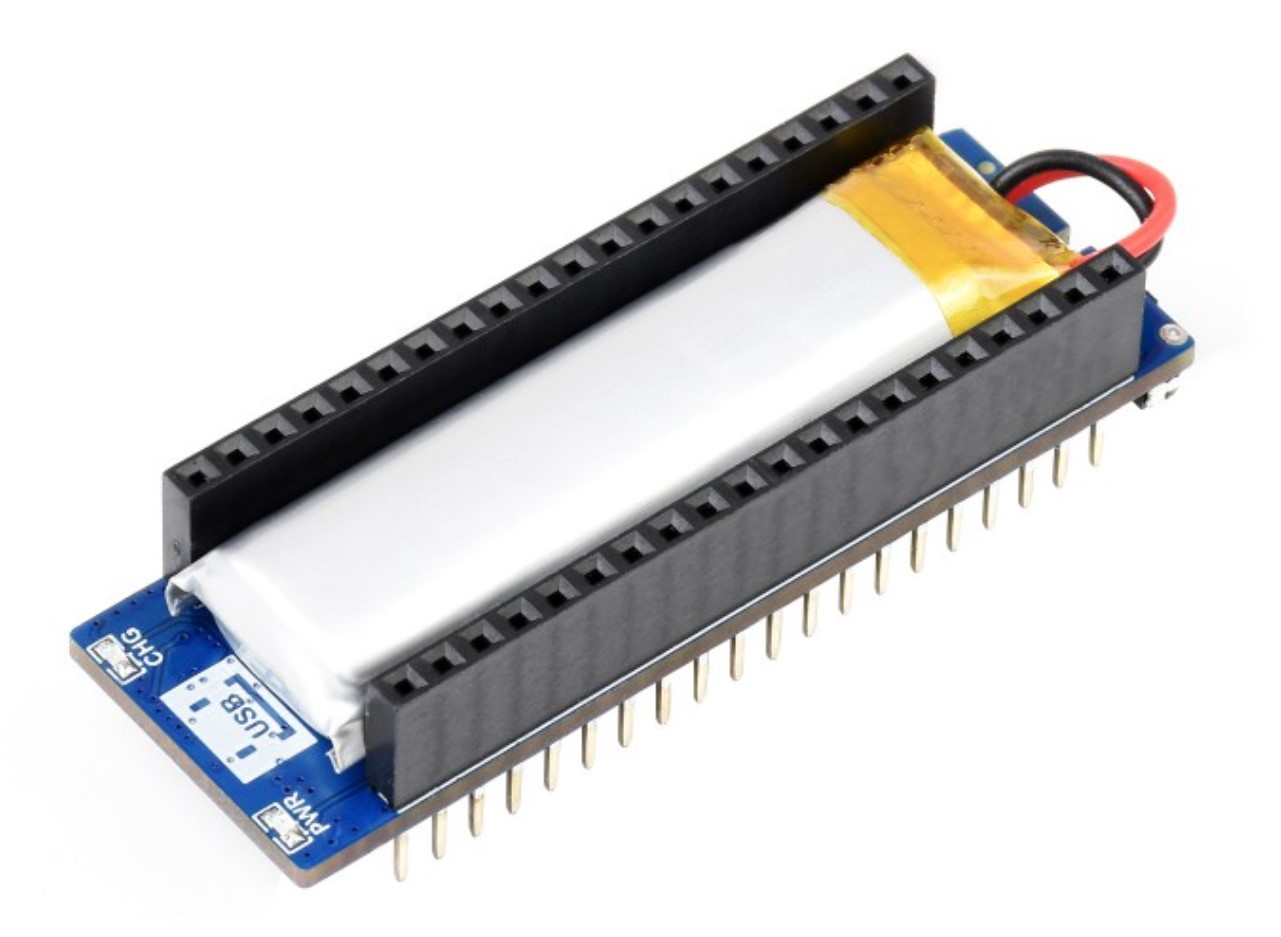 We used the following battery backup based on a single 14500N element because we had it handy; battery not shown and must be purchased separately:
We used the following battery backup based on a single 14500N element because we had it handy; battery not shown and must be purchased separately:
- An micro-USB OTG cable:

- A regular USB to micro-USB cable to flash the Pico board.
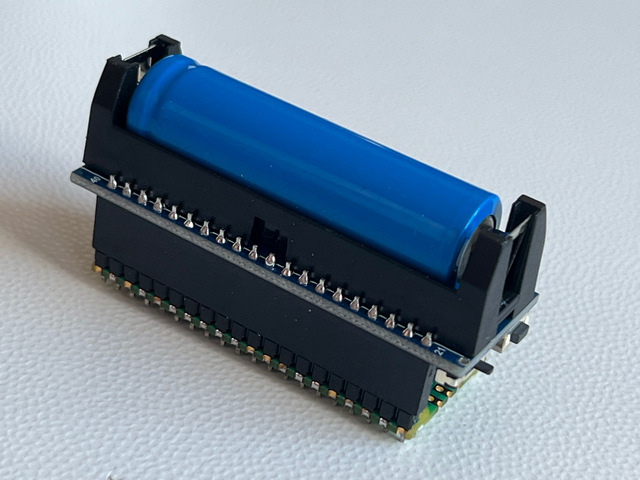
The finished board will look as follows:

A word on battery backup
The listed battery backup solution for the Pico board based on a single 14500 element will only provide 3.7V, which is enough to apply the exploit but NOT enough to place the iPhone into DFU. For placing the device into DFU you’ll have to do it manually (and then connect the iPhone to the Pico board).
Flashing the Pico board
Before connecting the iPhone to the Pico board, you will need to flash it with a custom firmware image. The firmware image is provided with iOS Forensic Toolkit.
To flash the Raspberry Pi Pico board, follow these steps.
- Make sure that the latest build of iOS Forensic Toolkit 8 is installed. You will need the beta 7 or newer.
- Press and hold the button on the Pico board.
- Connect the board to the computer with a regular micro-USB cable.
- The board will appear as an external storage.
- Drag and drop the “picom8.uf2” file from the EIFT root folder onto the storage.
- The Pico board will be flashed and rebooted.
- After the board finishes rebooting, it is ready for work.
Command line parameters
Once again, refer to checkm8 Extraction of iPhone 8, 8 Plus and iPhone X to understand the basic command line parameters of iOS Forensic Toolkit. We’ll use those commands in the subsequent step-by-step guide.
iPhone 4s checkm8 extraction
First, you will need to place the iPhone into DFU. You will need to connect the device to a computer first to put into DFU mode, then disconnect from computer and connect to the Pico board.
- The device will not go into DFU mode if less than 5V are applied.
- The device will not go into DFU mode if it’s not connected to anything at all.
To place the device into DFU, follow these steps:
- Plug the iPhone into the computer.
- Turn it off.
- Press and hold the Power button for 3 seconds.
- Press and hold the Home button without releasing the Power button for 10 seconds.
- Release the Power Button but keep holding the Home button.
- Keep holding the Home button until you are alerted by iTunes saying that it has detected a device in Recovery Mode.
The phone screen should remain blank. If the iTunes logo is present, you are in Recovery and not DFU. If this is the case, repeat the steps to get into DFU.
Once the iPhone is in DFU, connect it to the Raspberry Pi Pico board to apply the exploit. The exploit is applied automatically by the board. A repeated short blink and long pause of the LED will indicate success once the device is exploited. For error codes and for more information on LED status please refer to the user manual provided with EIFT.
Once the exploit has been applied, disconnect the iPhone from the Pico board and connect it to the computer. You will then use iOS Forensic Toolkit normally by following the unlock and extraction process for 32-bit devices (iPhone 4 and 5/5c).
Notes on applying the exploit
Sometimes it takes two to three tries for the exploit to work. The Pico board may indicate an error; if that happens, place the iPhone into DFU again and connect it to the Pico for another try.
Once device is exploited, the rest of the process is the same as for the other 32-bit devices. Please use the steps described the following guide for accurate data extraction:
Conclusion
The iPhone 4s and iPad 2 and 3 are undoubtedly legacy. Despite that, these devices are still relatively common. They may still contain valuable evidence ranging from personal pictures to messages and other data, not to mention the passwords. The hardware-based approach made it possible to create a truly reliable and complete solution for unlocking and extracting the device and decrypting the user’s passwords. As opposed to software-only solutions, the Pico-based one is very reliable, as there are no dependencies on the host system or version, USB controller and voltage, cables, and so on (everyone who worked with checkm8 knows what I am talking about).









