Last month, we released the tool and published the guide on forensically sound extraction of the iPhone 7 generation of devices. Today, we have added support for the iPhone 8, 8 Plus, and iPhone X, making iOS Forensic Toolkit the first and only forensically sound iPhone extraction tool delivering repeatable and verifiable results for all 64-bit iPhone devices that can be exploited with checkm8. While the previous publication talks about the details on acquiring the iPhone 7, there are some things different when it comes to the last generation of checkm8-supported devices.
Compatibility
This guide is applicable to the last generation of iPhone devices supported by the checkm8 exploit, which includes the iPhone 8/8 Plus/iPhone X range running iOS 11 through 15.3.
If you are about to extract an iPhone 5s, 6, 6s, SE, or 7 (as well as the Plus models, where applicable), please refer to the following guides:
In addition, we strongly recommend reading the following articles: More on checkm8 and USB Hubs and iPhone X, DFU mode and checkm8
The addition of the iPhone 8, 8 Plus, and iPhone X to the list of checkm8-supported devices completes the compatibility matrix. iOS Forensic Toolkit now supports all 64-bit iPhone devices having the bootloader vulnerability that can be exploited with checkm8.
New in beta 4:
- iPhone 8 (iPhone10,1/iPhone10,4): A1863, A1905, A1906, A1907
- iPhone 8 Plus (iPhone10,2/iPhone10,5): A1864, A1897, A1898, A1899
- iPhone X (iPhone10,3/iPhone10,6): A1865, A1901, A1902, A1903

Before you begin
Checkm8 is a complex exploit with several pre-requisites. Make sure you have everything handy before you begin.
- A Mac computer. You will need a Mac to install the exploit and perform the extraction. We support both Intel and M1-based Macs with a universal build of iOS Forensic Toolkit. At this time, Windows is not supported.
- iOS Forensic Toolkit 8.0 beta for Mac. You will require the Mac edition of the tool. Both Windows and Mac editions are included with every purchase of iOS Forensic Toolkit.
- A supported iPhone device (see compatibility matrix). The device must be functional enough to be placed into DFU mode.
- Screen lock passcode must be known or empty. Otherwise, limited BFU extraction may be available, but very little information can be obtained this way.
- iOS 14.x and iOS 15.x: on this generation of iPhone devices, screen lock passcode must be empty to use the exploit. If a non-empty screen lock passcode is set, you will have to boot the device to iOS and manually remove the passcode (be aware of forensic consequences).
- A USB-A to Lightning cable. Note that Type-C to Lightning cables are incompatible with this extraction method.
- You must be able to download the official Apple firmware (download link will be provided during the extraction) that matches iOS version installed on the device.
Acquisition speed and time requirements
The acquisition speed of the iPhone X and other devices of the same generation can be roughly 40 to 45 MB/s, or approximately 150 GB per hour. This means a 64GB device can be typically extracted in less than 30 minutes, while fully loaded 256 GB models can be extracted in about 1.5 hours (the 10 to 15 GB occupied by the operating system are skipped).
Detecting iOS version
Our extraction solution does not use the operating system installed on the iPhone to boot the device. Instead, a separate, patched version of the original Apple firmware is booted in the device RAM. This process requires you to have a copy of the original Apple firmware image that matches the device’s iOS version and build number exactly.
In many cases, the iOS version will be detected automatically by EIFT during the first stage of the exploit. The detection is based on the iBoot version. However, in some cases the iBoot version may correspond to several iOS builds.
If this is the case, you can attempt to use the first version of iOS suggested by EIFT. After you boot and unlock the iPhone using the downloaded image, EIFT will attempt to unlock the disk. If it fails, try using a different iOS firmware image. The worst that could happen is a safe reboot of the device.
Alternatively, you can check the iOS version in [Settings] – [About] on the iPhone itself by tapping iOS version to see the build number.
Note that you can still boot the phone using a close enough iOS build suggested by EIFT. If the wrong build is used, try a different firmware version.
Installing iOS Forensic Toolkit 8.0
The installation procedure has changed since previous releases. To install iOS Forensic Toolkit 8.0 beta 2, follow these steps:
There are two different DMG images. One for macOS Catalina and older; and one for Big Sur and newer. The file names are as follows:
- iOS-Toolkit-8-beta4-Mac-legacy.dmg for Catalina and older
- iOS-Toolkit-8-beta4-Mac.dmg for Big Sur and Monterey (with M1 support)
Command line parameters
For the past several years, iOS Forensic Toolkit was distributed with console-based, menu-driven UI. EIFT 8.0 beta4 uses a console-based, command-line interface we’ve introduced with the second beta of the tool. There are good technical reasons for this, but please reserve your questions until the final release version of iOS Forensic Toolkit 8.0.
The available parameters include:
Main commands
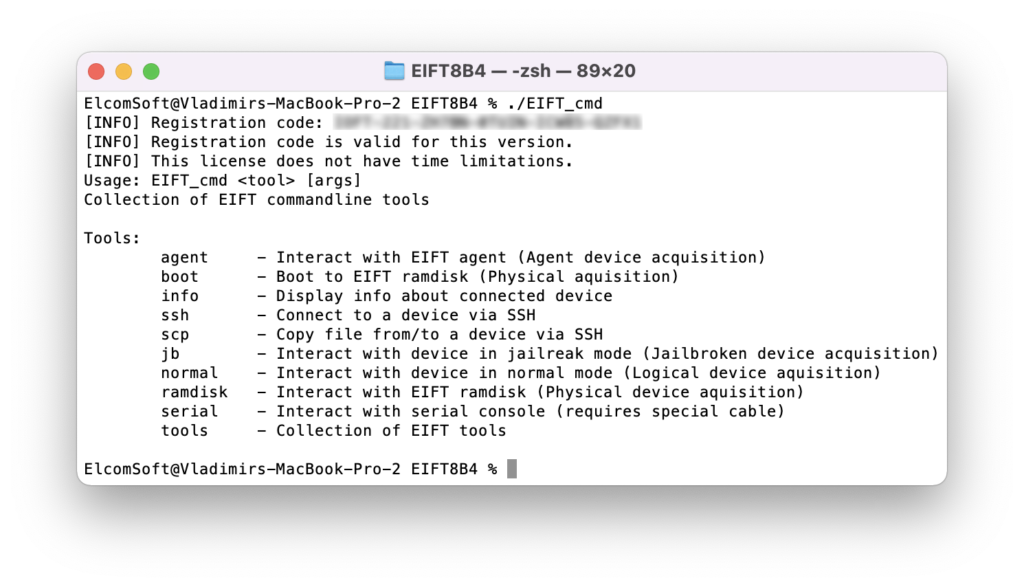
You do not need to use any of the following “advanced” commands unless instructed (or unless you know what you are doing):
Device information
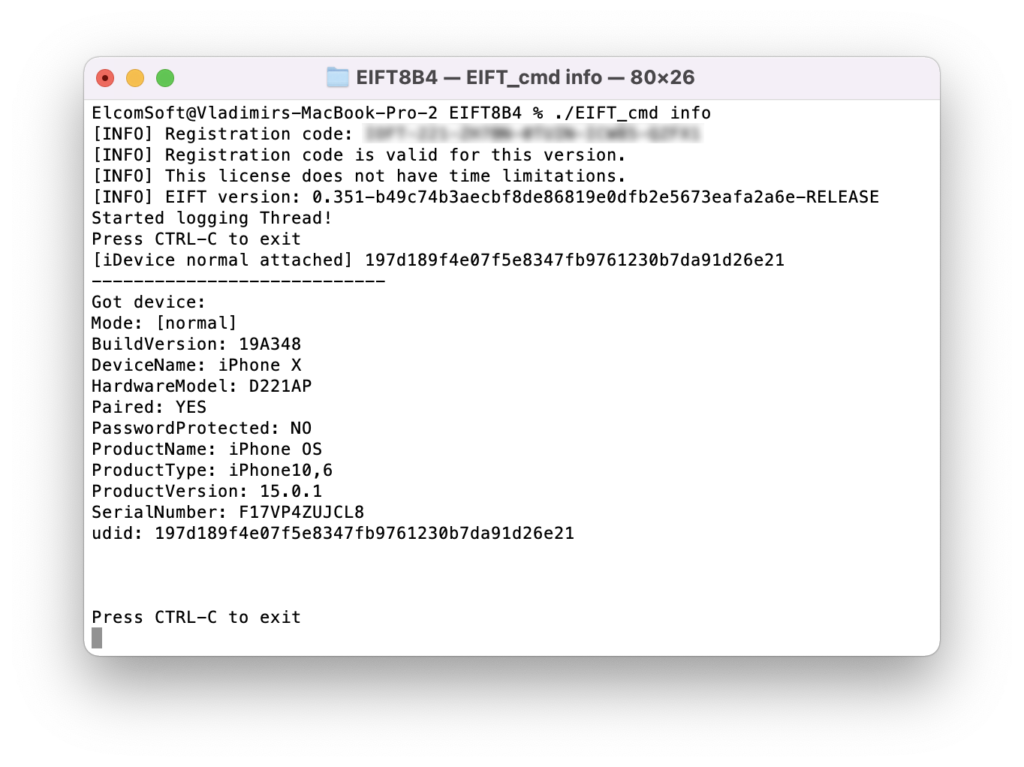
Commands related to logical acquisition
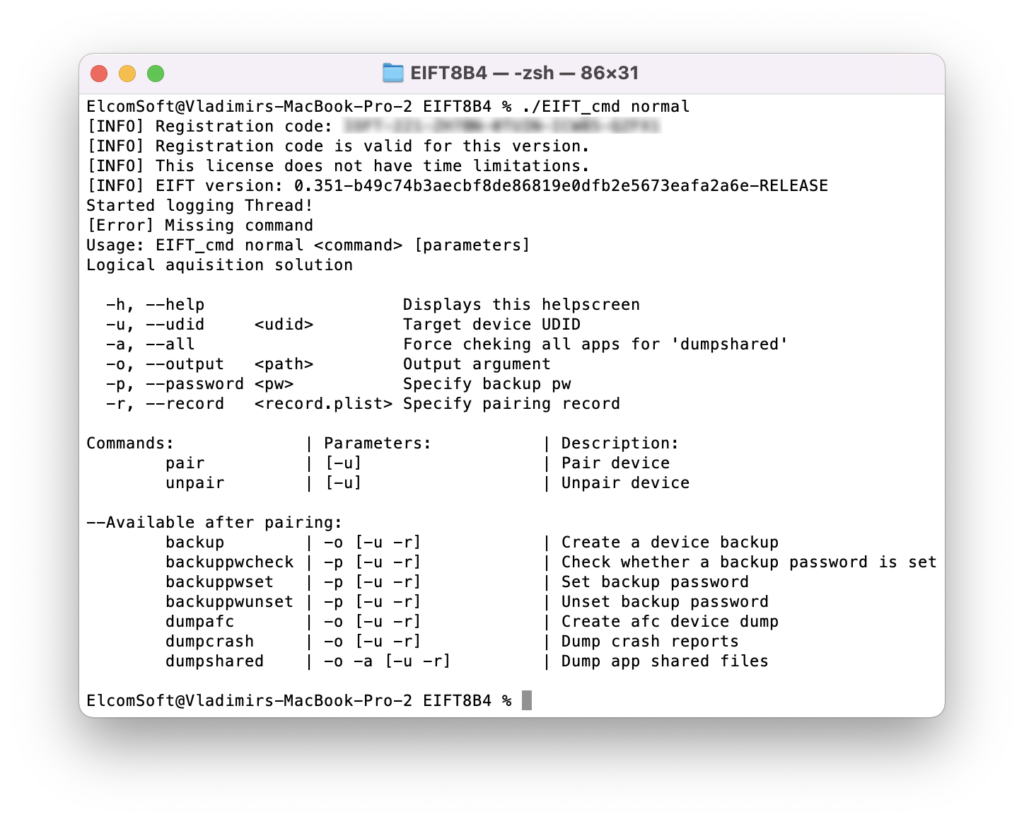
Commands for agent-based extraction
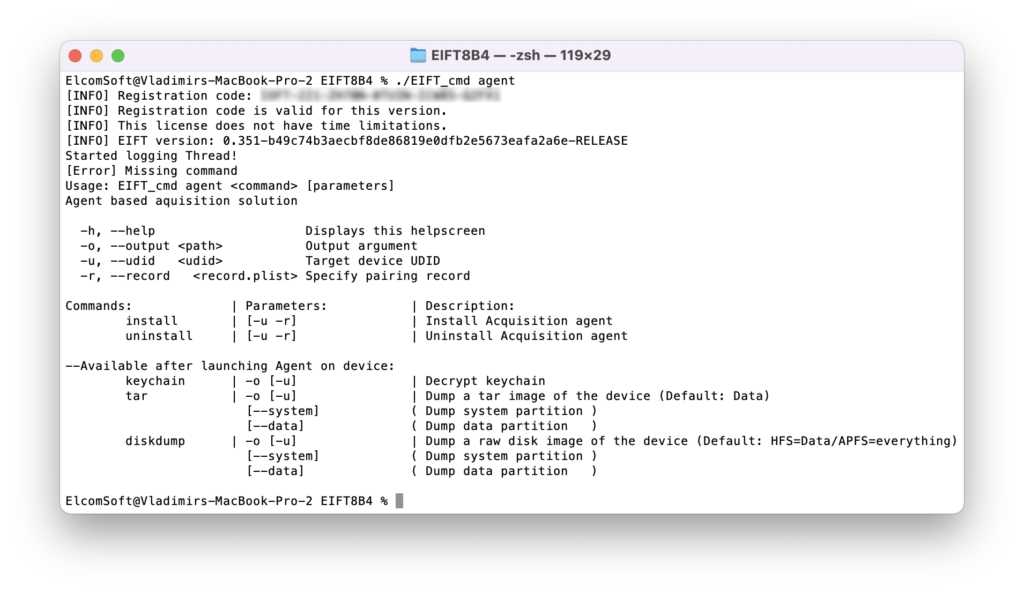
Commands for jailbreak-based extraction
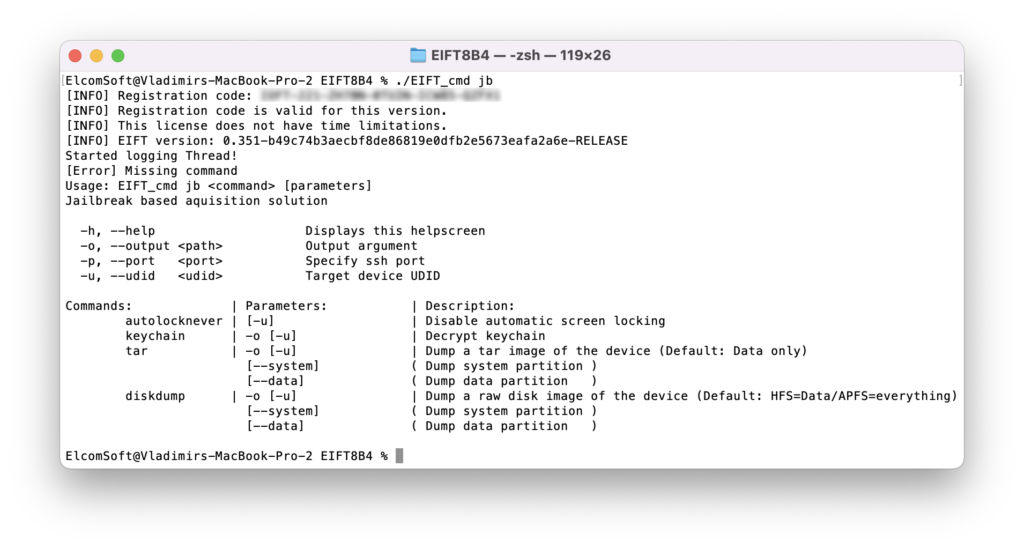
Ramdisk-related commands (when extracting via bootloader exploit)
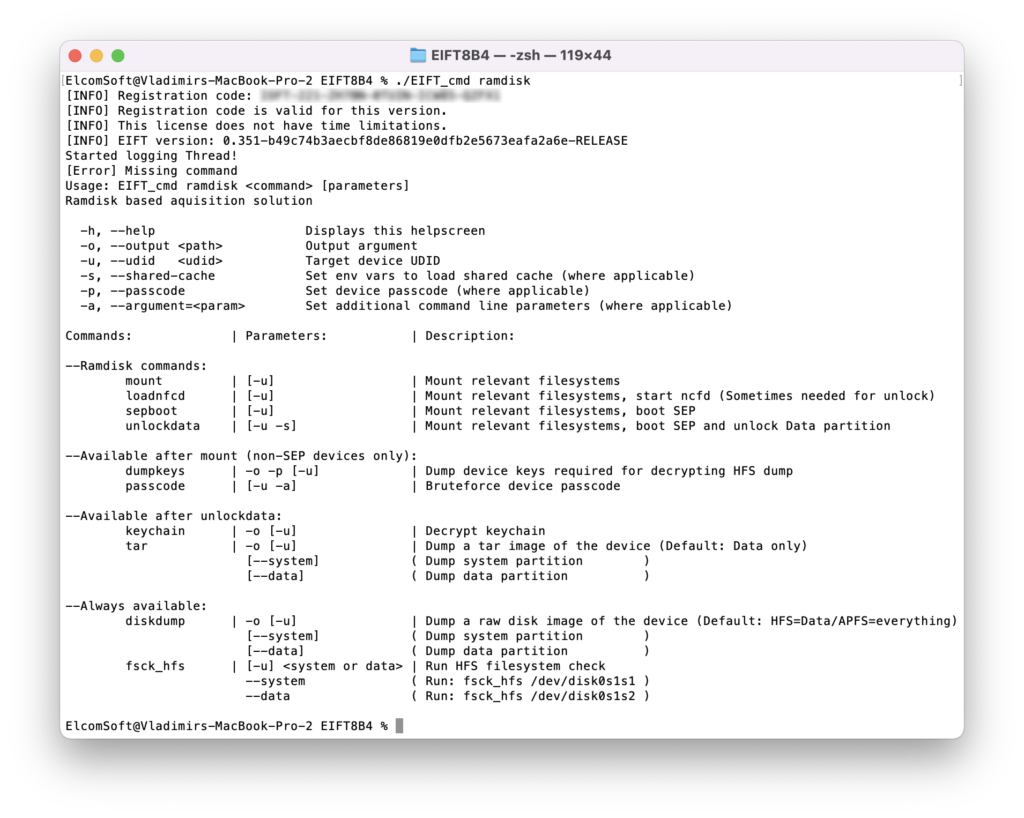
Tools

Bootloader-level extraction cheat sheet
Technically speaking, bootloader-level extraction was the most challenging to implement. This extraction methods requires experts to possess a certain level of skills and experience in handling iOS devices and placing them into DFU. The cost of a mistake is high: shall you fail to follow the sequence of precisely timed key presses, and the device may start booting iOS, which breaks the “forensically sound” part of the extraction. For this reason:
Practice DFU mode and familiarize yourself with the extraction process on a different iPhone device before you start the extraction.
Once you’re able to place the iPhone into DFU 10 times out of 10, follow these steps with the real device.
Below are the steps for the following 64-bit devices: iPhone 8/8 Plus/iPhone X.
- Place the device into Recovery
- From Recovery, place device into DFU
- ./EIFT_cmd boot
- ./EIFT_cmd ramdisk loadnfcd
- ./EIFT_cmd ramdisk unlockdata -s
- ./EIFT_cmd ramdisk keychain -o {filename}
- ./EIFT_cmd ramdisk tar -o {filename}
- ./EIFT_cmd ssh halt
checkm8 extraction step by step
First, place the device DFU. We strongly recommend switching the iPhone to Recovery first before entering DFU. For the iPhone 8/8 Plus/iPhone X generation, a different set of steps is required; please see iPhone X, DFU mode and checkm8 for details.
After that, execute the following command:
./EIFT_cmd boot
The command launches the exploit. The code detects the iOS version installed on the device and provides a download link. If there are multiple potential matches, several download links will be displayed; we recommend taking the last link from the list. Download the file from the link, and drop the .ipsw file onto the console window.
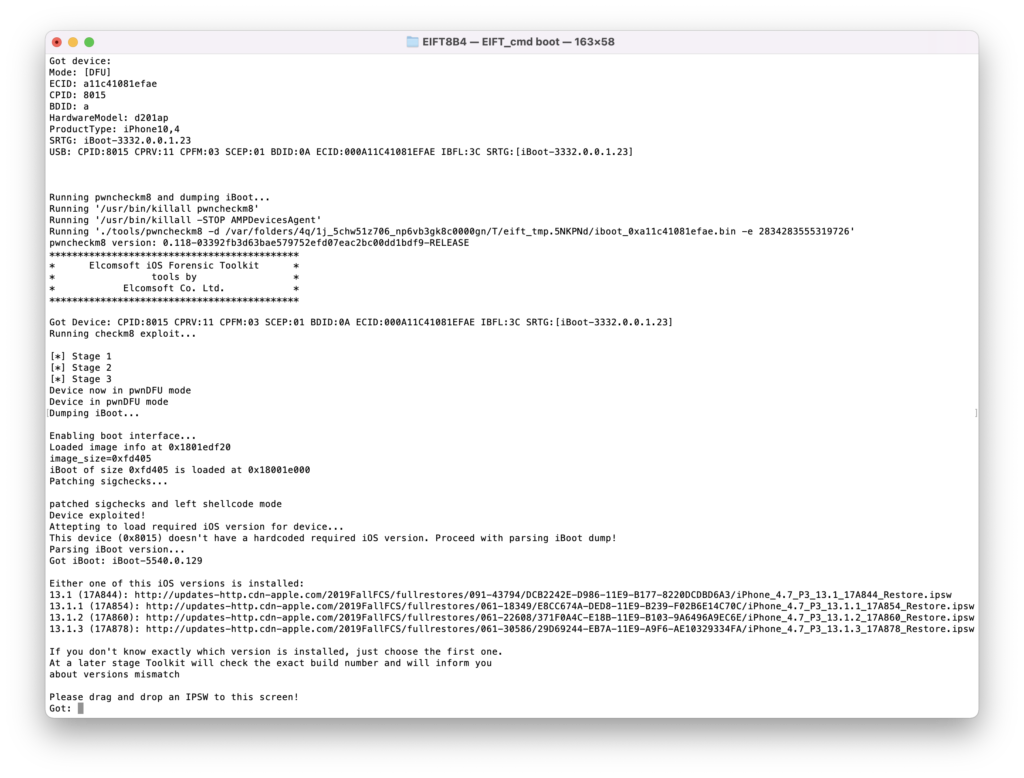
Our extraction solution does not use the operating system installed on the iPhone to boot the device. Instead, a separate, patched version of the original Apple firmware is booted in the device RAM. This process requires you to have a copy of the original Apple firmware image that matches the device’s iOS version and build number exactly.
In many cases, the iOS version will be detected automatically by EIFT during the first stage of the exploit. The detection is based on the detected iBoot version and device hardware. However, in some cases the iBoot version may correspond to several iOS builds. If the wrong build is used, you will have an option to either repeat the process with a different version of firmware, or continue with the current firmware image (which works in many cases).
If the process was successful, you will see the following information:
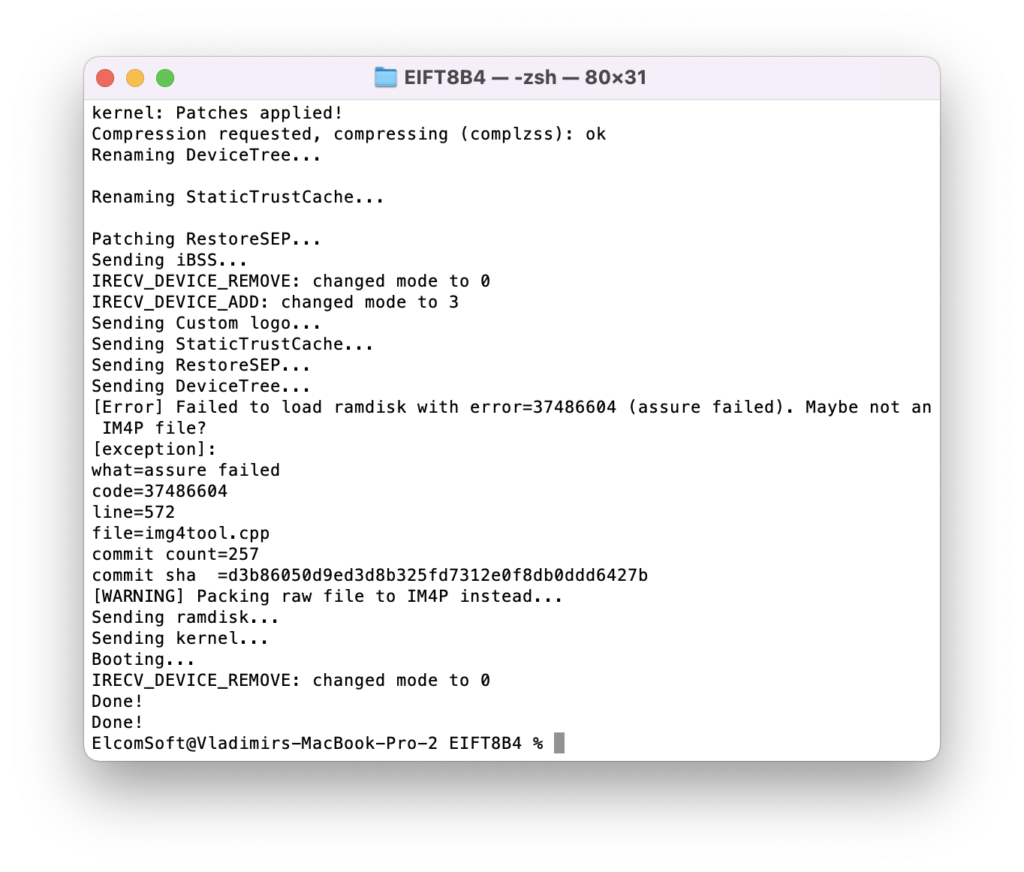
The iPhone will display the following screens:


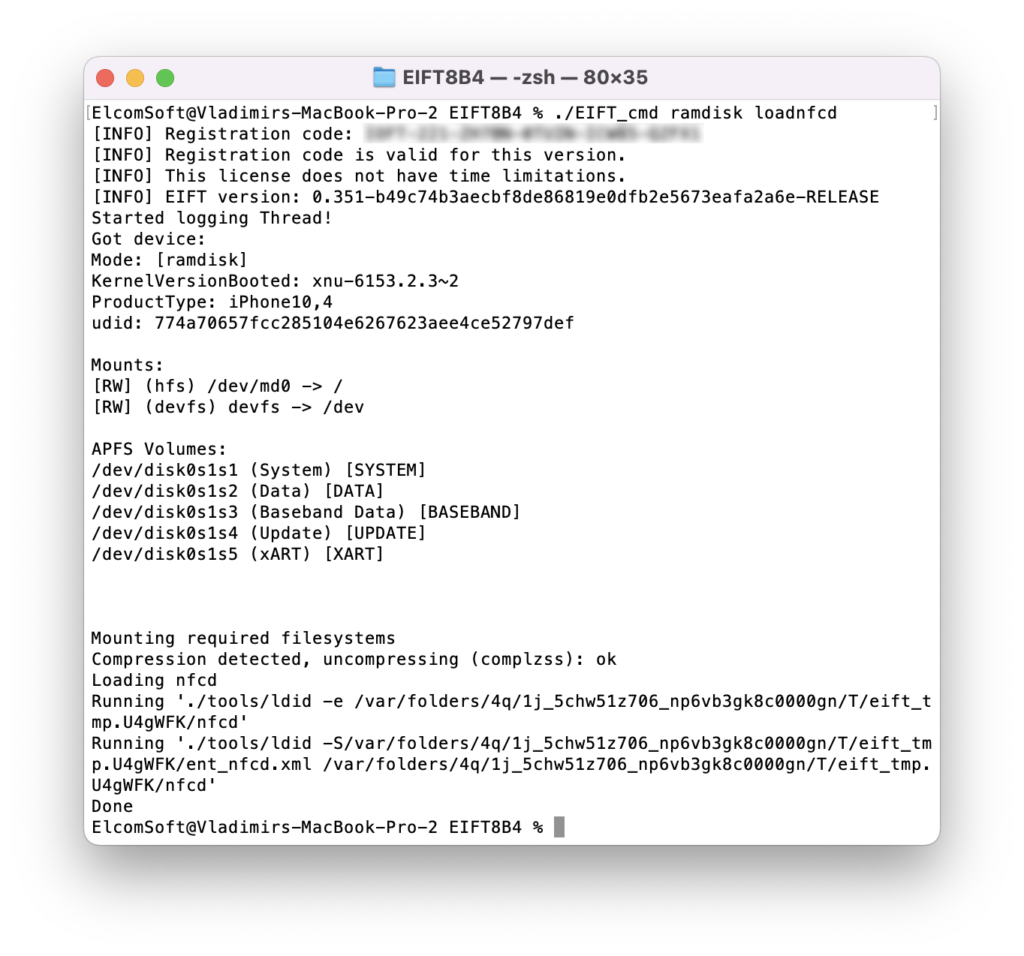
./EIFT_cmd ramdisk loadnfcd
This command is recommended although not absolutely required; you can proceed right to unlock, and run that one only if unlock fails.
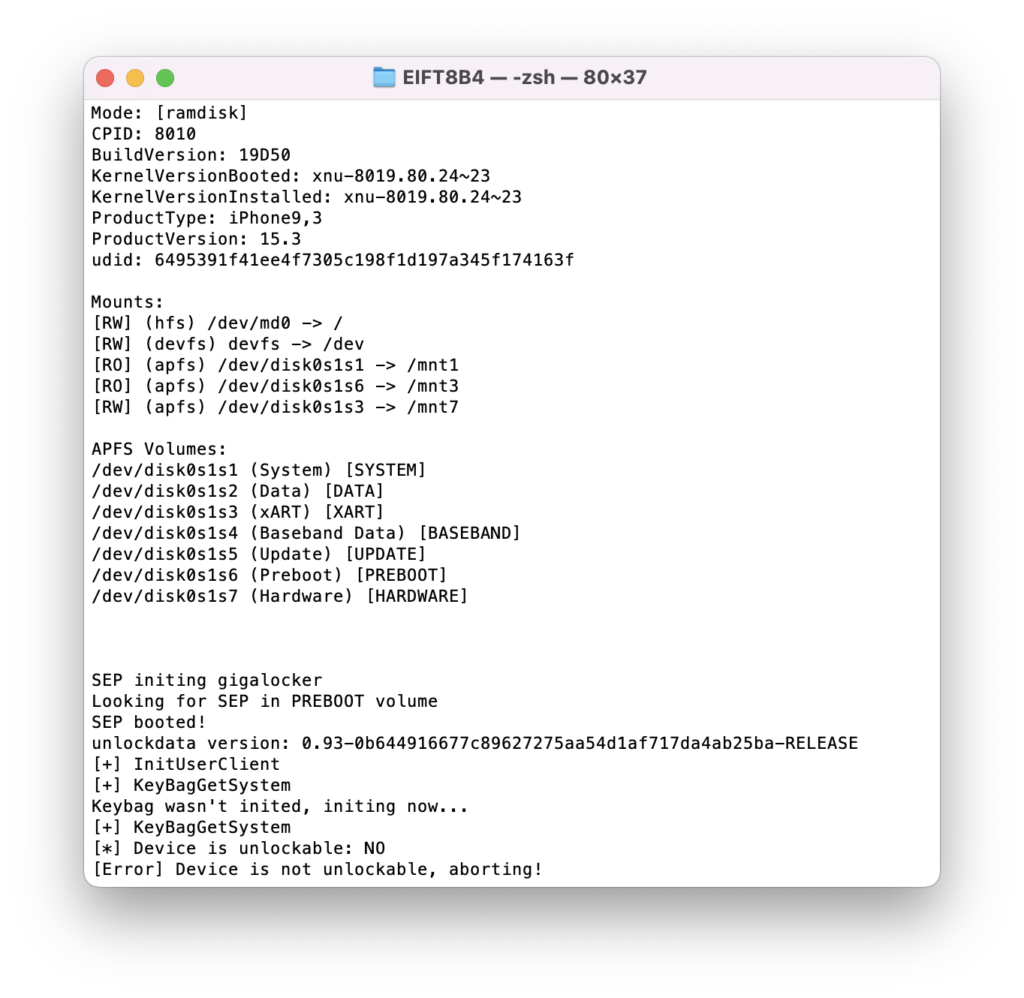
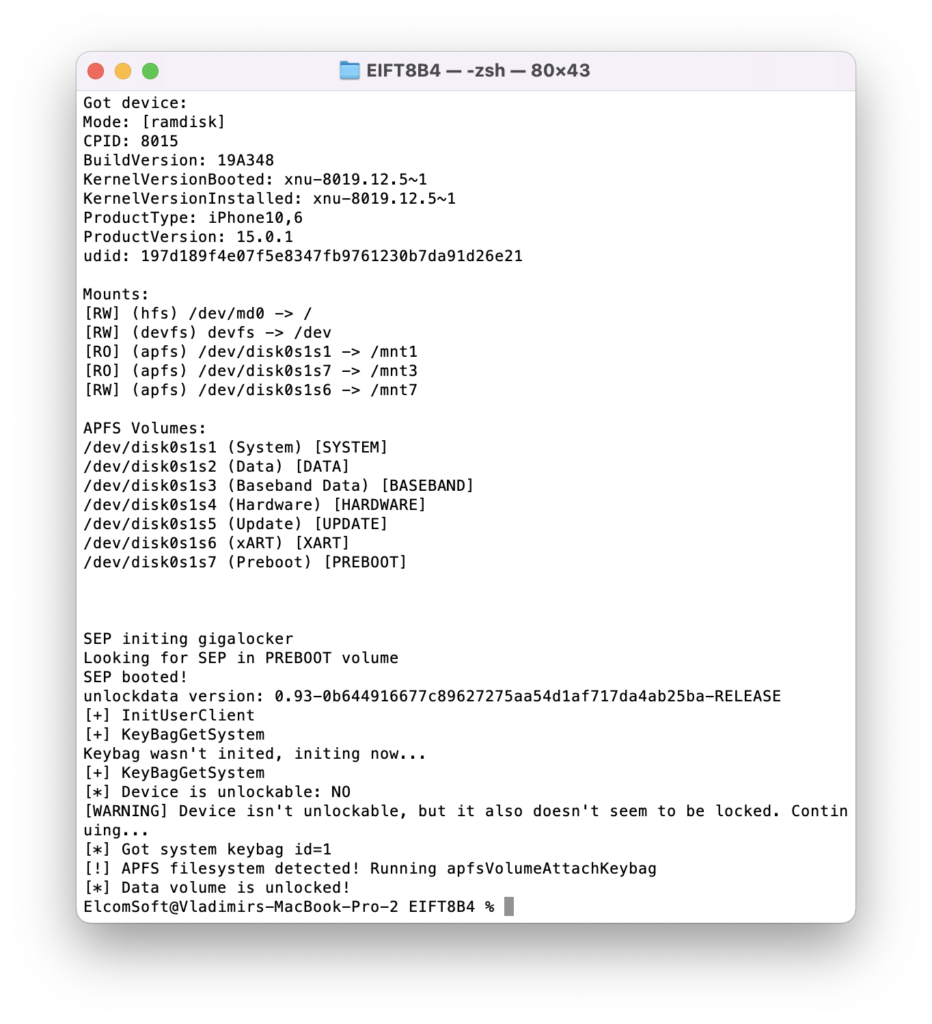
./EIFT_cmd ramdisk unlockdata -s
This command unlocks the data partition and mounts it read-only. If there is no passcode set:
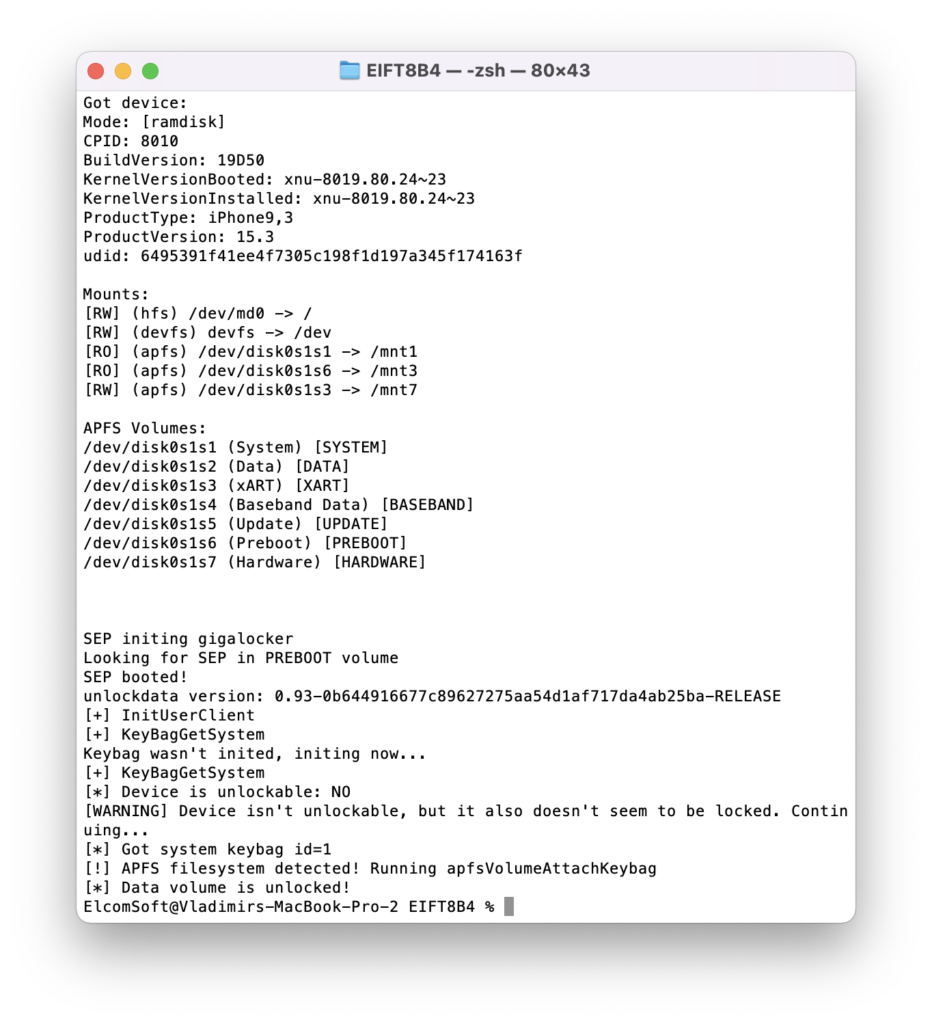
If passcode is set, you will be prompted for it:
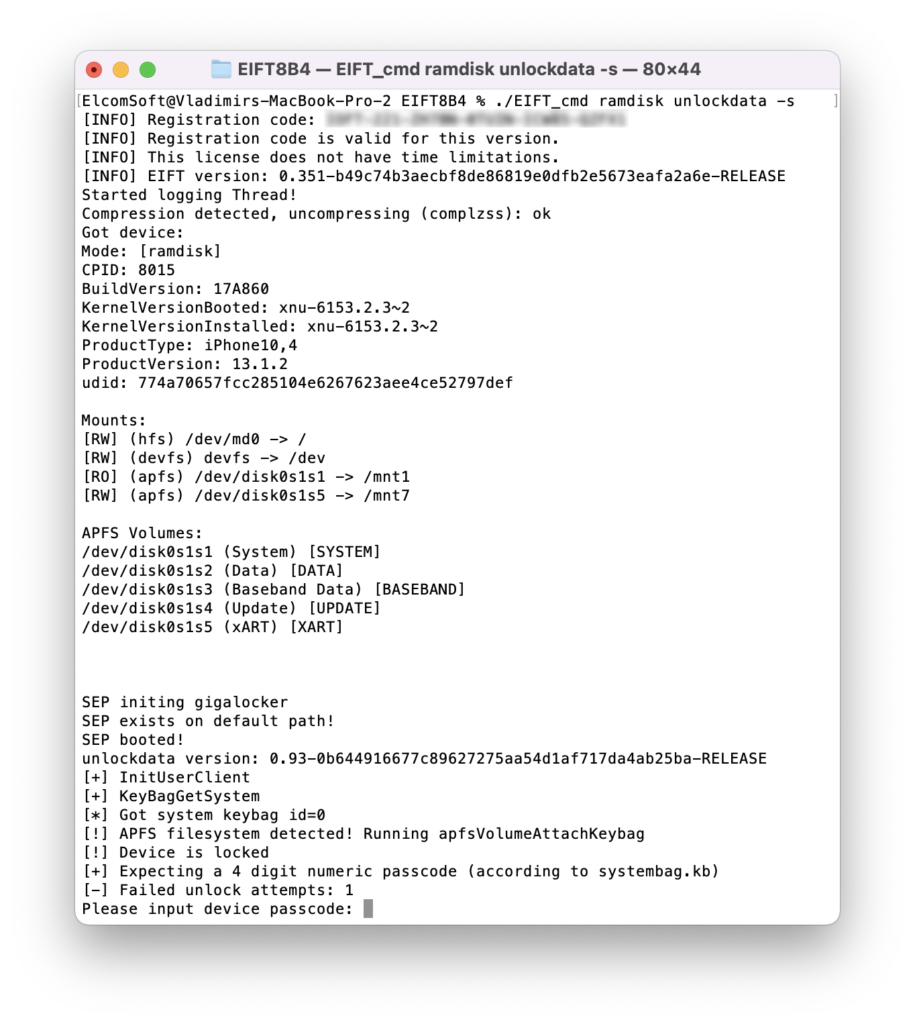
If you enter the wrong passcode, an error will be displayed. With correct passcode, the volume is fully unlocked and you can proceed with data (keychain and file system) extraction). If you don’t know the passcode, press ENTER on the screen below. In this case, a very limited BFU extraction will be performed.
./EIFT_cmd ramdisk keychain -o {filename}
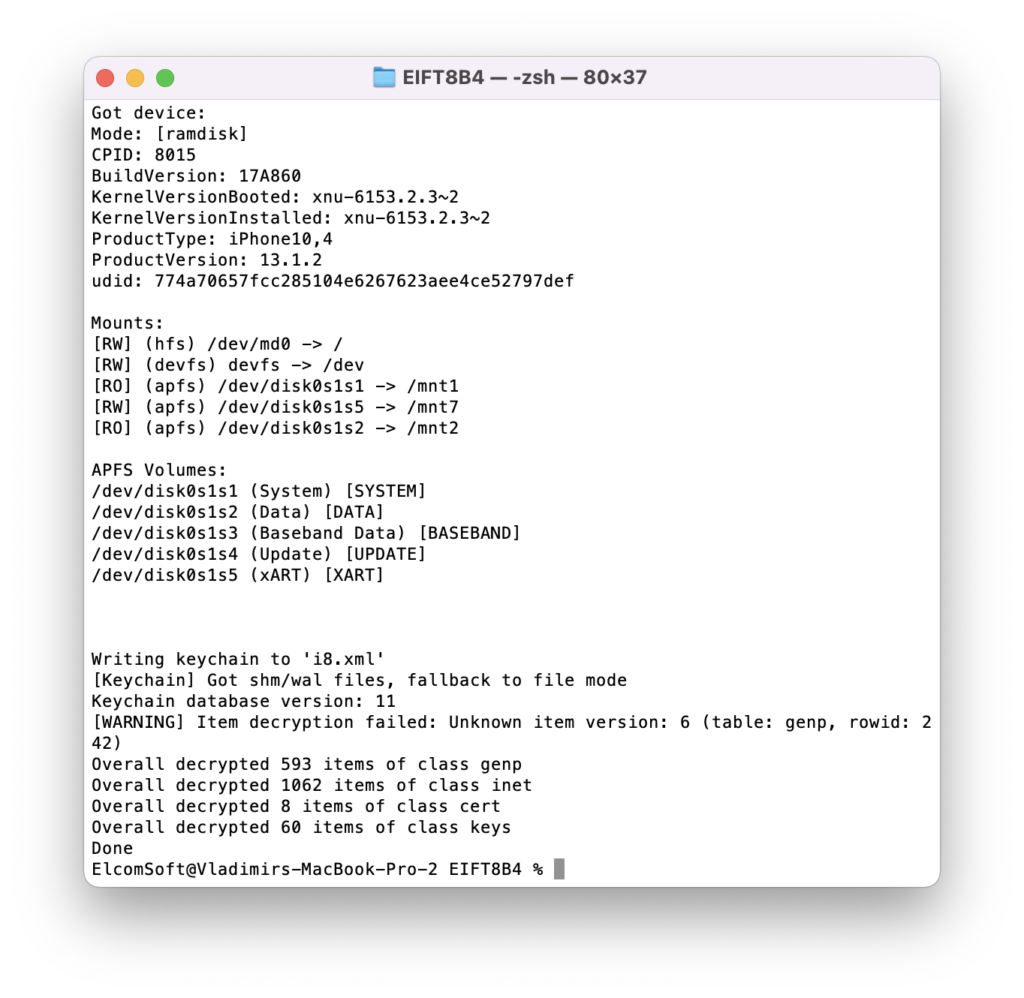
This command extracts and decrypts the keychain. If no path is specified, it will be saved into the current folder. Keychain extraction is supported for all versions of iOS (up to iOS 15.3 at the time of this writing).
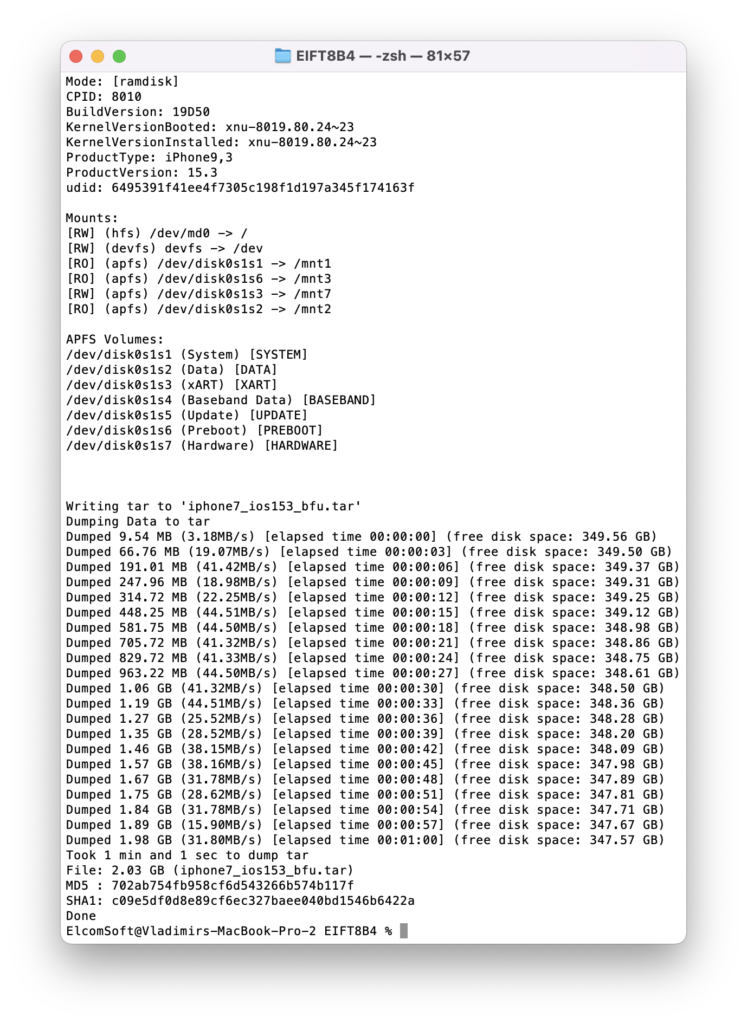
./EIFT_cmd ramdisk tar -o {filename}
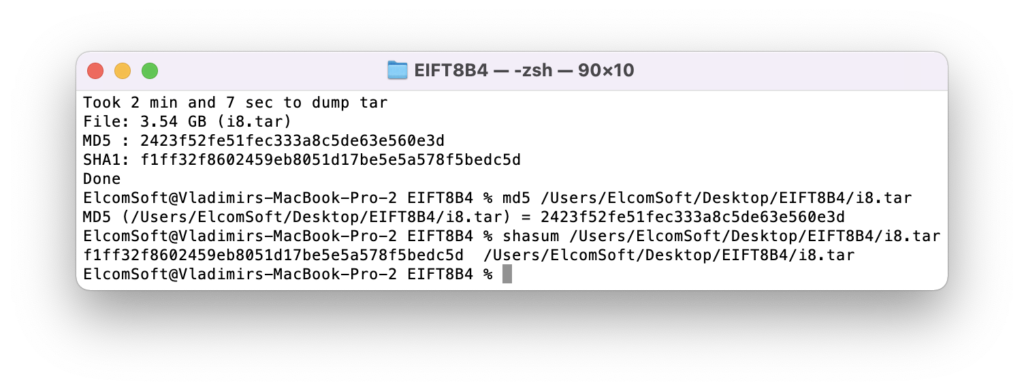
This command images file system. The checksum (hash value) is calculated on the fly and displayed once the extraction is finished.
./EIFT_cmd ssh halt
This command powers off the iPhone. Always use this command at the end of the extraction as it is not possible to power off the iPhone with the buttons. If you try pressing and holding the power button, the iPhone will reboot and load the installed version of iOS, which breaks forensically sound extraction.
BFU extraction
If you do not know the screen lock passcode, just press ENTER when prompted. Despite “Device is not unlockable” error, you will be still able to perform a limited BFU (Before First Unlock) extraction.