We often write about full file system acquisition, yet we rarely explain what it is, when you can do it, and which methods you can use. We decided to clarify low-level extraction of Apple mobile devices (iPhones and iPads, and some other IoT devices such as Apple TVs and Apple Watches).
What
Data acquisition is the first and most important step in mobile forensics. Multiple extraction methods exist, but you rarely have a choice: often, only one or two will be available for a given device in a given condition.
These methods extract different types and amounts of data. Full files system extraction is exactly what is says on the tin: you get every bit of data from the device except unallocated data, right from the root folder and including all applications data, temporary files, logs, system files (which is important if you suspect a malware infection), detailed location history etc.
How does it compare to other methods? The difference is huge; the simplest (and almost always available method) is logical extraction. Logical acquisition is the most compatible and the easiest to use (yet not as simple as it sounds) returning the least amount of data; it is not fit for file system extraction, but still returns a copy of the keychain if you do it right.
While logical extraction is 100% compatible regardless of the device model and version of iOS (or iPadOS, watchOS, tvOS), it returns a limited set of data. Most common categories such as contacts, calls, notes, media files are there, but that’s really far from what you can actually get with full file system extraction. A lot of data is simply missing with logical extraction.
Also, the keychain. Remember the “do it right” part? With logical extraction, you can sometimes decrypt the keychain, but not every record. Some records including encryption keys and authentication tokens are only available with full file system extraction.
Also, do not forget that logical extraction of Apple TV and Apple Watch is very limited: there are no backup services there, and all you can get is media files and some logs. With full file system extraction, you get everything.
When
The answer is probably obvious, but we still want to say it: do full file system extraction whenever you can (there are several models and iOS versions compatibility issues).
If you only need such things as call log or notes, you can get about without a copy of the file system. You will only waste your time if you try, without getting any extra value. If, however, you require as much evidence as possible extracted in the cleanest possible way, get the whole file system if you can.
Unfortunately, many modern devices running up to date versions of iOS are incompatible with low-level extraction methods. In that case, you will be limited to logical acquisition – but there is a lot of ticks & tricks about it.
How
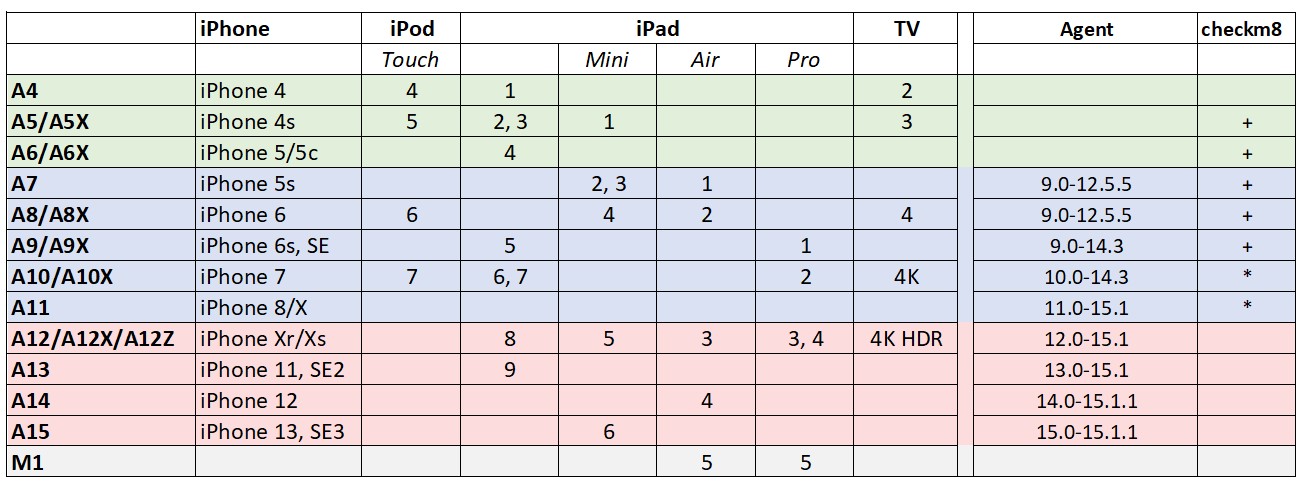
You need low-level extraction to access the file system. Low-level extraction comes in many flavors. The hardware-bound checkm8 extraction is the cleanest of the pack, while software-based extraction agent works on any hardware if it runs a compatible version of iOS. Agent-based acquisition is second best to checkm8, delivering robust file system extraction for all Apple devices running a compatible version of iOS. Agent-based extraction comes as close to being forensically sound as possible, only installing a lightweight app and not altering any user data
What makes a certain iOS version ‘compatible’ with the agent? The extraction agent obtains the required level of privileges by exploiting one of the known vulnerabilities in iOS kernel. To do this, the app packs a number of kernel-level exploits and uses one or another to escape its sandbox and access the file system. Such exploits require time and effort to find and to implement, while Apple actively patches known vulnerabilities in iOS updates. This is why the latest versions of iOS are generally immune to exploits developed for earlier builds (although we know of several exceptions).
How do these methods compare? Checkm8 extraction is based on a hardcoded bootloader exploit available on Apple’s legacy models. The acquisition agent gains the required level of privileges by exploiting vulnerabilities in iOS (thus being software-bound). Both return almost the same set of data, but have their own pros and cons. Here they are:
checkm8
+ works with all iOS versions
+ does not care about MDM
+ forensically sound
– does not work with modern devices
– you may need to remove the passcode (and so lose some data)
agent
+ works with all devices up to iPhone 13 Pro Max and even M1-based 5th gen iPad Pro
+ do not need to remove the passcode
– mot exactly forensically sound, make some changes to the system
– limited compatibility with iOS versions
– MDM may prevent the method from working
– requires Apple Developer account to use
Conclusion
Make a copy of the file system and extract the keychain if you can, and you will not be disappointed. Do not expect a “one click” solution there, though; low-level extraction is always tricky no matter which method you use. But it is worth it.



