Keychain is an essential part of iOS and macOS that securely stores the most critical data: passwords of all kinds, encryption keys, certificates, credit card numbers, and more. Extracting and decrypting the keychain, when possible, is a must in mobile forensics. We seriously improved this part in the latest build of iOS Forensic Toolkit.
There are several methods of keychain extraction; we reviewed them in Extracting and Decrypting iOS Keychain: Physical, Logical and Cloud Options Explored. The different methods will return different results. When analyzing an encrypted backup with logical acquisition, you never get all the items. Excluded are the encryption keys for some secure messengers such as Signal and Wickr, and many other bits and pieces. Keychain obtained with our extraction agent is always complete, and contains all those keys, as well as some extremely useful data such as the local backup password, which can be used to unlock older backups containing the data already removed from the device itself.
TL&DR
- iOS keychain contains valuable evidence
- Low-level extraction decrypts all keychain items
- New release: iOS Forensic Toolkit now supports keychain extraction for all devices running iOS 15.1.1 and older on all supported devices (previously up to and including iOS 14.4.1)
- In older releases, experts had to unlock the device with screen lock passcode during keychain extraction (and even then, some keychain items could be missing). New release: no need to unlock, all keychain items reliably decrypted.
- M1-based iPad Pro now supported.
- Keychain extraction walkthrough (with screenshots)
What is it all about
The ultimate goal of a forensic expert is extracting as much data from the device as possible. Logical acquisition is the simplest to use and the most compatible method that supports all devices and all versions of iOS (see Logical Acquisition: Not as Simple as It Sounds), but as we recently explained in Full File System and Keychain Acquisition: What, When, and How, a different approach may yield a significantly better return.
For devices up to and including the iPhone X (as well as many iPods and iPads, most Apple TV models, and Apple Watch S3), we have an excellent, forensically sound extraction method based on a bootloader exploit. However, for devices based on Apple’s A12 and newer SoC, this method is not applicable, and the only solution to extract the full file system and keychain is to use our unique agent-based method delivering about the same result.
The extraction agent uses kernel-level exploits, and so has limitations on which versions of iOS are supported. At the time of this writing, the agent supports iOS 15.1.1 and older versions. File system extraction is relatively simple (once we have a proper exploit), while keychain has some additional protection layers and is harder to decrypt. Because of that, we only supported keychain extraction on iOS 14.4.1 and older. This is changing today with an updated version of Elcomsoft iOS Forensic Toolkit released today. The new build closes the gap in iOS version support, and allow keychain decryption for the all versions of iOS for which the file system extraction is supported. This means that full file system extraction and keychain decryption are both available for all versions of iOS up to and including iOS 15.1.1, for all devices up to and including the iPhone 13 Pro Max.
Besides, there is one notable improvement in keychain extraction. In earlier versions, you had to enter the device passcode (sometimes even twice) during the process, or use Touch ID or Face ID on the phone. Regardless, from time to time some keychain records would not be extracted. With this update, we made the process completely flawless: there is no need to do anything on the phone, and the full keychain is always decrypted.
Last but not least, we have added full file system and keychain extraction for the latest model of iPad Pro (5th gen) based on the M1 SoC. The iPad was released over a year ago with iOS 14.5.1 onboard; we currently support all versions of iOS 14 versions (up to 14.8.1), as well as iOS 15.0 to 15.1 (the same range as for the iPhones).
Keychain extraction with iOS Forensic Toolkit
Installing the Toolkit
For EIFT 7.x, just follow the standard installation procedure. The Windows version will guide you through the whole process and install the Elcomsoft iOS Forensic Toolkit icon in Start menu. For the macOS version, mount the DMG installation image and copy the product icon into Applications.
For EIFT 8.0 beta, installation requires some manual work. Once the proper DMG image is mounted (there are two: one for macOS Big Sur and Monterey, supporting both Intel and M1-based Macs; and the other one for macOS High Sierra, Mohave and Catalina), first copy the EIFT folder to desktop (or any other folder of your choice). Then, remove the quarantine flag from that folder by running the following command from the console:
xattr -r -d com.apple.quarantine <path to folder>
Now cd to that folder and launch EIFT:
./EIFT_cmd <parameters>
Agent installation
Connect the device to the computer with a Lightning cable or USB Type-C for select iPad models, and establish the trust relationship first.
In EIFT v7, the agent can be installed by choosing the [1] command from the menu; in EIFT v8, run the following command:
./EIFT_cmd agent install
You will be then prompted for an Apple ID and password, and might be requested to pass two-factor authentication.
Important: do not use the device owner’s user’s Apple ID. For more details accounts and limitations, please refer to iOS Low-Level Acquisition: How to Sideload the Extraction Agent. Regular and developer can be used in Windows and macOS.
Note: agent installation may fail if the date and time on the device are incorrect.
Once the agent is installed, you should see Acquisition application icon on the device main screen.
Usage
On the device, launch the extraction agent by tapping its icon:
In EIFT v7, run menu item [2] (keychain extraction); you will be prompted for output path for keychain path. In EIFT v8, run the following command:
./EIFT_cmd agent keychain -o <filename>
The extraction agent will use known exploits to obtain the required level of privileges, then read and decrypt keychain items and save them into an XML file for further analysis. You can analyze the extracted records with Elcomsoft Phone Breaker or review them manually. Please note that file name (to save the keychain) should be unique; if the file already exists, extraction will fail.
The exploiting stage may take up to a minute for some versions of iOS, although usually it is much faster. Saving the decrypted keychain is lightning fast.
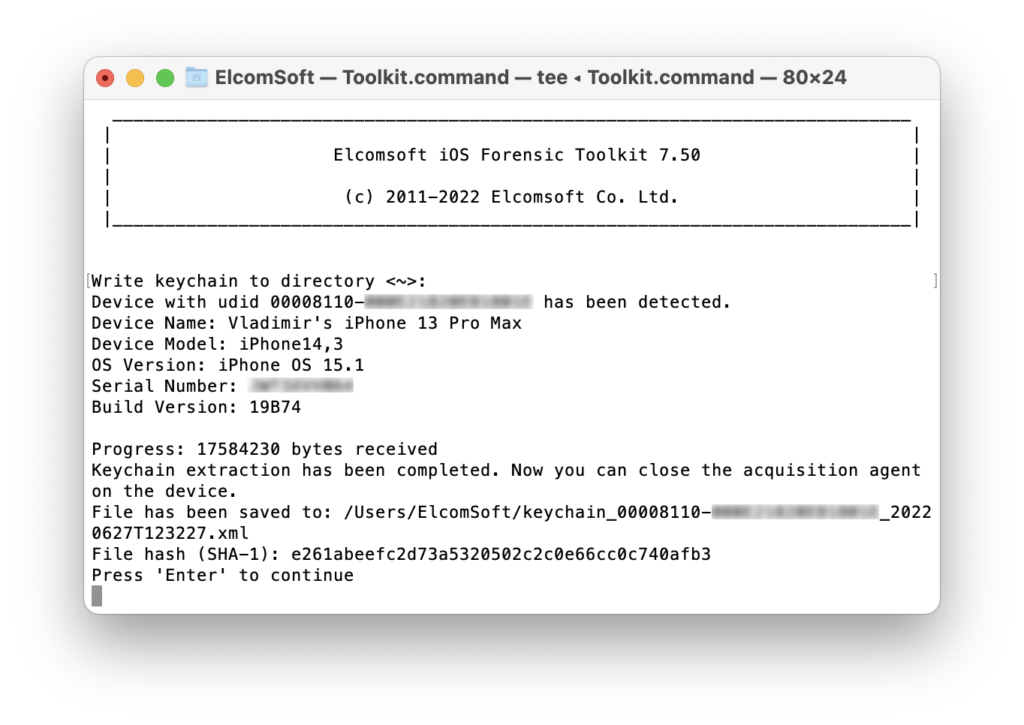
Sometimes keychain extraction does not work from the first run: you either get “All exploits failed” on the device screen (in that case, just reboot the device and try again; there is no need to reinstall the agent, just run it and run the acquisition), or device is just rebooted. Some exploits we use require 3-5 tries.
You can now extract the full file system as well (in a form of .tar archive), as described in the user’s manual – and finally, remove the agent from the device (note: some traces are always left).
Compatibility
You can extract the file system and decrypt the keychain via checkm8 or the extraction agent from the following devices:
- iPhone 5s, iPhone 6, iPhone 6s, iPhone SE (1st gen), iPhone 7, iPhone 8, iPhone X: all iOS versions they can run
- iPhone Xr/Xs, iPhone 11, iPhone 12, iPhone SE (2nd gen), iPhone 13: up to and including iOS 15.1.1
iPhone SE (3rd gen, 2022) is not on the list as it was released with iOS 15.4 onboard. We also have not listed other devices (such as iPod Touch, all iPad models including Mini/Air/Pro, Apple Watch and Apple TV); basically, the support is the same as for the iPhones according to the SoC they are based on.

And here is another representation for your convenience:
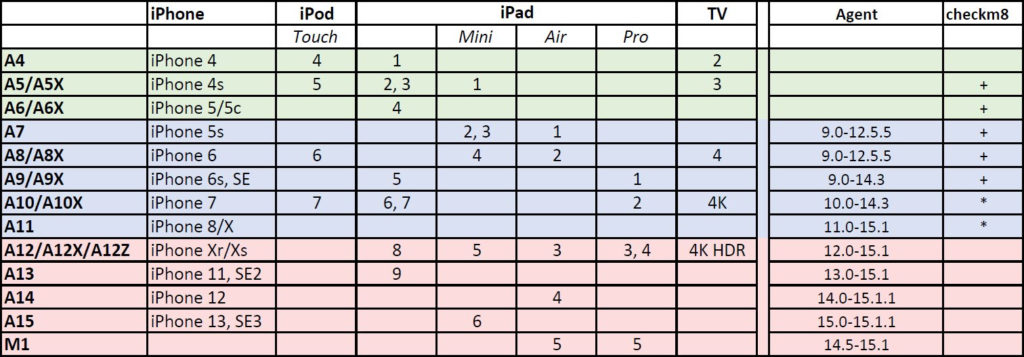
The asterisk means that we do support this model, but device passcode needs to be removed in advance (iOS 14 and iOS 15 only). We are working on removing this limitation for the iPhone 7. Please also note that agent acquisition is not available for for Apple TV (checkm8 works though).
We are working hard on supporting newer versions of iOS, including iOS 15.2 and up. Stay tuned!
Conclusion
Keychain extraction is often missed in mobile device forensics process. Always extract the keychain when and if you are able to; this will provide a lot of extra evidence compared to just the file system.






