Bootloader-based acquisition is the only 100% forensically sound data extraction method for Apple devices. It is the only way to acquire the full set of data from those devices that run iOS 16, albeit with a huge caveat that makes the whole thing more of a brain exercise than a practical forensic tool. Let’s review the iOS 16 compatibility in iOS Forensic Toolkit and go through the whole process step by step.
Supported devices
The checkm8 exploit is compatible with multiple generations of Apple devices. However, only some of those devices are compatible with Apples’ latest iOS builds. Here is the full list of devices that are compatible with both the bootrom-based acquisition method and can run iOS 16 and its variants such as iPadOS and tvOS:
- iPhone 8, iPhone 8 Plus, iPhone X
- iPad 5/6/7
- iPad Pro (1st and 2nd gen)
- Apple TV HD (4th gen) and Apple TV 4K (1st gen)
iPad and iPro devices do not have iPadOS 16 update yet. iPadOS 16.1 soon will be available, but there are some bad news coming.
First, the “…cannot be fixed with a software patch” mantra about the bootloader vulnerability and the checkm8 exploit did not actually work. For the most part, Apple was able to fix it in iOS 16, specifically for devices based on the A11 SoC, which includes the iPhone 8, 8 Plus and iPhone X. The first part of the fix arrived with the release of iOS 14. Back then you had to disable the screen lock passcode in order for checkm8 to work. iOS 16 improved this even further: if the device had a passcode set at any time after it was initially set up, the data volume cannot be unlocked anymore. The file system extraction, let alone keychain decryption, of a passcode-locked iPhone 8/X running iOS 16 is no longer possible if you know the passcode and even if you remove it from the device.
Second, iPadOS 16.1 (and iOS 16.1) will bring significant changes (in particular the ramdisk format) that will prevent our software from working. At this point we cannot say whether this change is made to improve security (probably not). We can fix it, but we need more time.
Prerequisites
A compatible device. This is the trickiest part. If you are working with an iPhone 8, iPhone 8 Plus or iPhone X and it has a passcode set, you are out of luck. With iOS 14 or 15, you had to remove the passcode first (see How to Remove The iPhone Passcode You Cannot Remove for more details), but that does not work anymore with iOS 16. For iOS 16 and an iPhone 8, iPhone 8 Plus or iPhone X you’ll need a phone that never had a passcode at any point after the user set it up.
You’ll need a Mac. For the time being, iOS Forensic Toolkit 8.0 can only be used on a Mac. We do have a Windows build, but it currently lacks support for bootloader-based acquisition. Both Windows and Linux editions with full support for bootloader-based acquisition are currently under development. iOS Forensic Toolkit can work even on older Mac running macOS High Sierra, but we recommend one of the newer models instead. If you have a choice, pick one based on Apple Silicon running macOS Big Sur or Monterey. Note that we have not tested iOS Forensic Toolkit on macOS 13 Venture, although it should work.
Please note that we do not officially support virtual machines or Hakintoshes.
A USB-A to Lightning cable. If your Mac has USB-C or Thunderbolt ports only, you will also need a hub with at least two USB-A ports (one to connect the device, and the other to connect the iOS Forensic Toolkit dongle).
For iPads, there is still no need to remove the passcode prior to the acquisition, but you must know the passcode; however, as noted above, we don’t support iPads running iPadOS 16 yet, sorry (working on that).
Finally, Apple TV does not have passcode protection, so there is nothing to worry about.
Installation
We have two separate installation packages:
- Legacy: for macOS High Sierra, Mojave and Catalina (Intel-based Macs)
- Current: for macOS Big Sur and Monterey (intel or Apple Silicon)
Make sure to download a package compatible with your system.
To install the downloaded package, first mount the installation file (.dmg) using the installation password you received, and copy EIFT8 (or EIFT8L for legacy version) folder to a known location on your computer, such as desktop.
Next, start the Terminal app and remove the quarantine flag:
xattr -r -d com.apple.quarantine <path to EIFT folder>
Now you can cd into the iOS Forensic Toolkit folder and start the program. The general syntax is:
./EIFT_cmd <options>
Entering DFU
Placing the device in DFU is probably the trickiest part of the process. Entering DFU is always manual; you need to press and hold the buttons on the device in a particular order with precise timings. The steps are different for different devices, and every little detail (such as ports and cables) matters.
We posted a lot about DFU. You can start with DFU Mode Cheat Sheet. There is something specific to the Apple TV 4K that does not have a USB port (Apple TV 4K Keychain and Full File System Acquisition); and we have a detailed (and carefully tested) set of instructions for the iPhone 8 and iPhone X range: Entering DFU: iPhone 8, 8 Plus, and iPhone X.
In short, we recommend starting iOS Forensic Toolkit first with boot command and -w flag (which means “wait for device in DFU mode”) like this:
./EIFT_cmd boot -w
The programs will keep looking for connected devices and will indicate once such device is connected or disconnected (in any mode), which makes things simpler.
Usage
If you did everything right, the bootloader exploit will be applied automatically and immediately as soon as iOS Forensic Toolkit founds a device connected in DFU mode. The tool will then detect the installed iOS version; unfortunately, in some cases the exact iOS version cannot be determined, and the tool will print out the closest range of iOS builds.
You will then have to provide the tool with a path to a proper firmware image; a download link will be printed out by iOS Forensic Toolkit. If the exact iOS version could not be determined, you will receive several download links; in that case, select the first one from the list. You can either download the firmware and specify name and path to the local file in iOS Forensic Toolkit, or just paste the download link instead, in which case iOS Forensic Toolkit will download only the mandatory data, which is a bit faster.
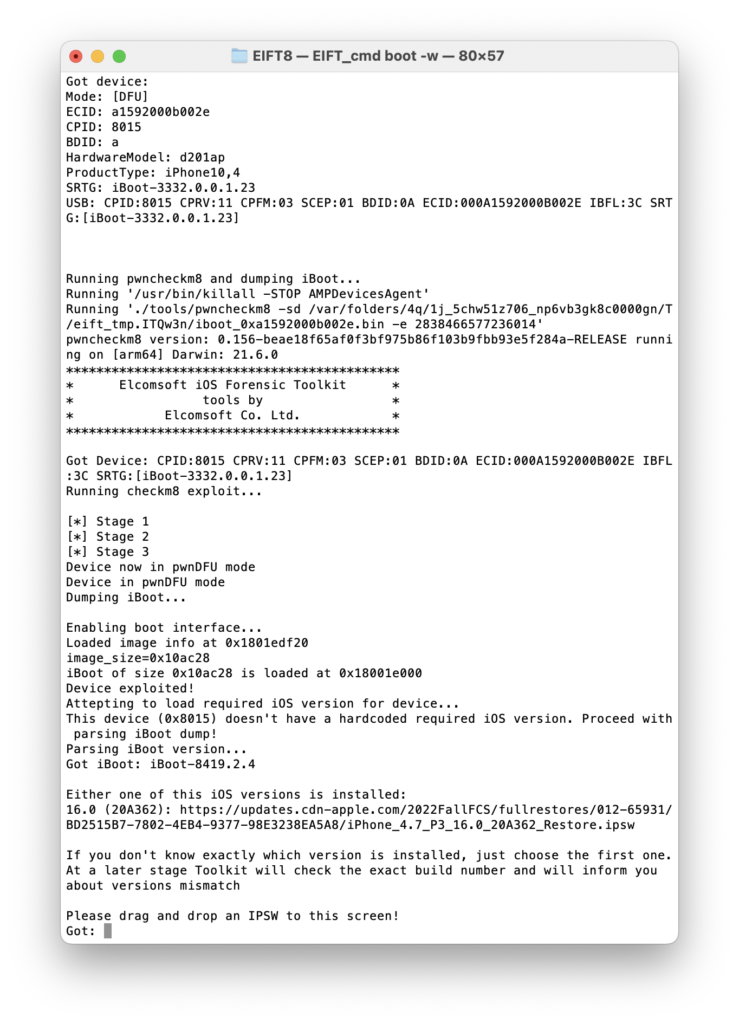
iOS Forensic Toolkit will perform further steps, booting a proper ramdisk and making the necessary patches in the device’s volatile memory. If everything is OK, the device screen will display the Exploited message.

You can now acquire the data by following the steps:
./EIFT_cmd ramdisk unlockdata
The command unlocks the data partition. Yes, you do NOT need to run “ramsisk loadnfcd” command (that mounts the relevant filesystems and starts ncfd daemon) as before. It is still needed for iOS 15 and lower, though.
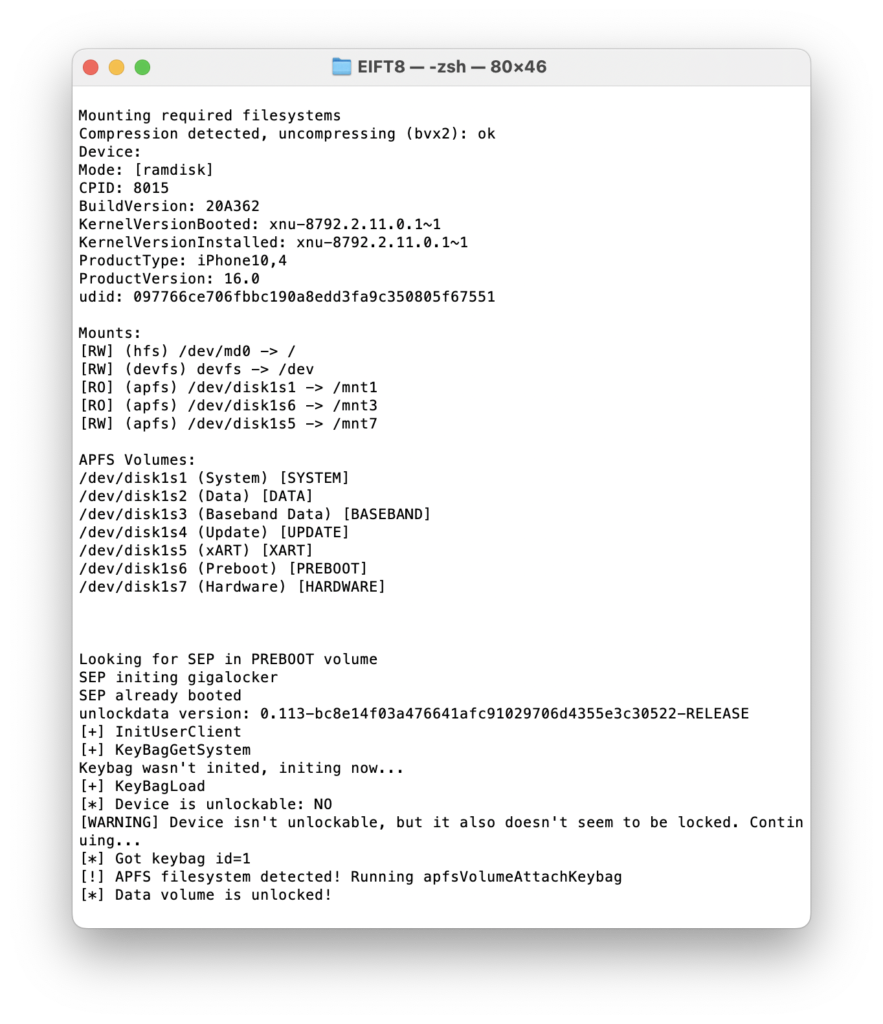
If the passcode is set (or was set before, and later removed), the command fails. There is currently absolutely no way to acquire the data (keychain and full file system) from iPhone 8/X devices running iOS 16 protected with the passcode using checkm8 exploit, at least for now.
./EIFT_cmd ramdisk keychain -o <path to keychain file>
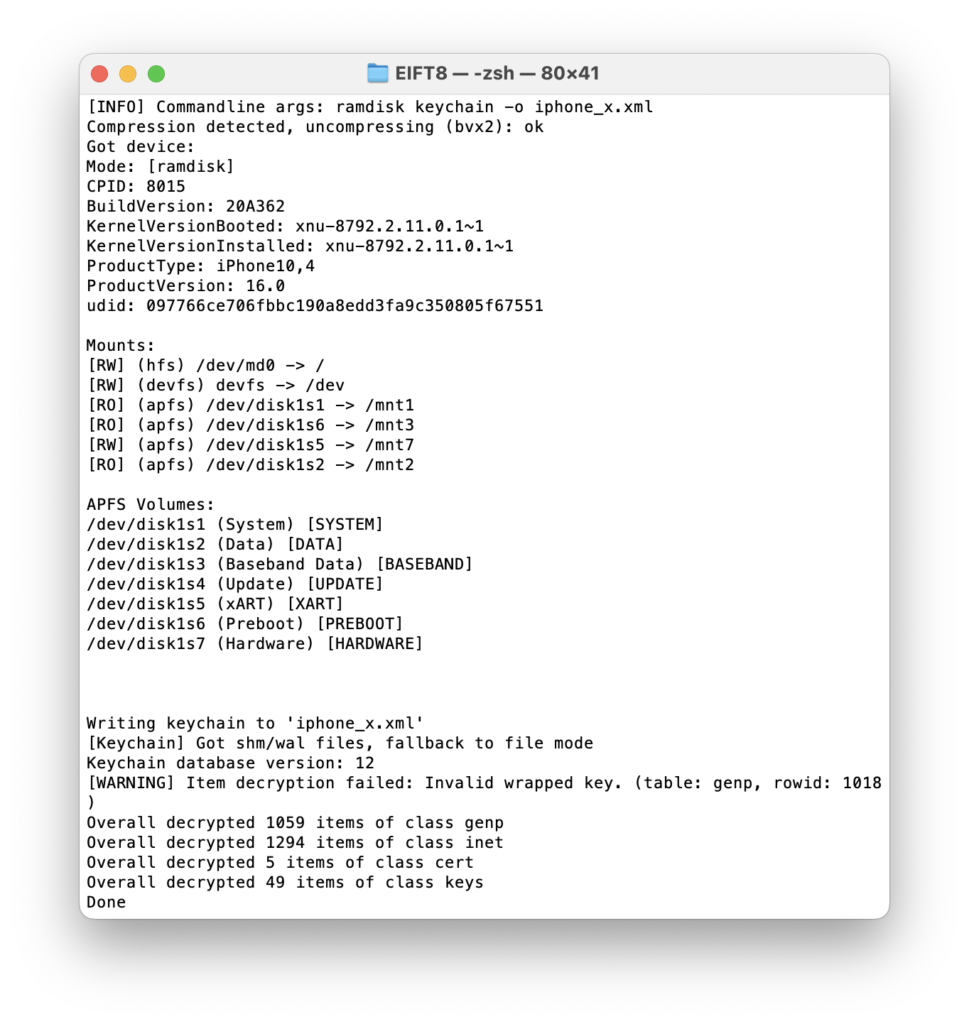
The keychain is should be normally extracted first as it contains some of the most valuable data: see Keychain: the Gold Mine of Apple Mobile Devices for details.
./EIFT_cmd ramdisk tar -o <path to file system image> 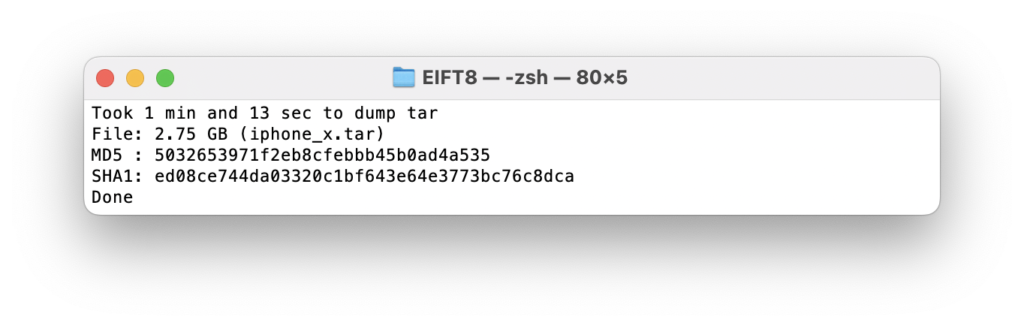 By default, only the data partition is extracted, and it is the recommended setting. The system partition does not contain any user-specific data, and its extraction will slow down further analysis. Only pull the system partition if the device is jailbroken or you think that it might be compromised with something like Pegasus spyware.
By default, only the data partition is extracted, and it is the recommended setting. The system partition does not contain any user-specific data, and its extraction will slow down further analysis. Only pull the system partition if the device is jailbroken or you think that it might be compromised with something like Pegasus spyware.
iOS Forensic Toolkit saves the file system in a form of a .tar archive that can be analyzed, for example, with open-source iLEAPP software. Of course, commercial software like Cellebrite UFED, Magnet AXIOM, MSAB XRY or Oxygen Forensic Detective will also work. Some of these products may not support iOS 16 file system analysis at this point, but I am sure they will. For the time being, it looks like iLEAPP does the job (and it is free!)
Troubleshooting & error reporting
I bet you will get some troubles entering DFU at first; this is normal. Just follow the instructions exactly (and remember about the hub and USB-A cable).
Still, applying the exploit may fail, sometimes because the device is in a “wrong” DFU mode (see the DFU article above for more details); if this happens, just try again.
The other error you may encounter occurs when the output file with the same name (keychain or .tar archive with the file system) already exists; just check that the output file name is unique.
From time to time, you may get an error when booting the ramdisk or data unlocking the data partition. Such errors may occur randomly, and they are completely unpredictable. If this happens, we would love to receive the complete log file(s) created by iOS Forensic Toolkit to develop a solution; the log files are saved at:
~/Elcomsoft/EIFT/logs
By request, we can provide you with a debug version of iOS Forensic Toolkit that logs even more information that may help us locate and fix the problem.
TL;DR
So, here is the sequence of commands once iOS Forensic Toolkit is installed:
- Start terminal and change current folder to EIFT
- ./EIFT_cmd -w
- Place the device in DFU mode
- Supply the firmware file or link
- ./EIFT_cmd ramdisk unlockdata
- ./EIFT_cmd ramdisk keychain -o <path to keychain file>
- ./EIFT_cmd ramdisk tar -o <path to file system image>
Conclusion
Despite limitations, our implementation of checkm8-based extraction is still the best and most forensically-sound acquisition method for supported devices. With the release of iOS 16, the iPhone 8, 8 Plus and iPhone X became practically invulnerable to the “unpatchable” bootloader exploit. Forensic specialists will be unable to extract real-life devices that are (or ever were) protected with a passcode, at least not until a SEP exploit emerges. There is also a possibility that an OS-level vulnerability will be discovered in iOS 16, making agent-based extraction possible. This, however, is a distant project as Apple complicated a lot of things in iOS 16.







