The first-generation HomePod is a smart speaker developed by Apple that offers high-quality audio and a range of features, including Siri integration and smart home controls. However, as with any electronic device, it can store valuable information that may be of interest in forensic investigations. In this article, we will explore how to use the forensically sound checkm8 extraction to access data stored in the HomePod, including the keychain and file system image. We will also outline the specific tools and steps required to extract this information and provide a cheat sheet for those looking to extract data from a HomePod. By the end of this article, you’ll have have a better understanding of how to extract data from the first-generation HomePod and the potential limitations of this extraction method.
HomePod extraction: cheat sheet
To extract data from a first-generation HomePod, follow these steps:
- Launch iOS Forensic Toolkit 8.0 (Mac)
- Connect the device to the computer with a USB adapter (you will need a custom adapter for connecting the HomePod)
- Place the HomePod into DFU (see below)
- [optional] Run ./EIFT_cmd info to ensure that the HomePod entered DFU
- Run ./EIFT_cmd boot
- Run ./EIFT_cmd unlockdata
- Run ./EIFT_cmd ramdisk keychain -o {filename} to extract the keychain
- Run ./EIFT_cmd ramdisk tar -o {filename} to pull the file system image
- [optional] Run ./EIFT_cmd ssh halt to power off the device. Alternatively, simply pull the plug.
Note: as long as you keep it connected to USB and upside down, it will never boot into the normal OS.
Placing HomePod devices to DFU
Placing the HomePod into DFU is surprisingly simple.
- Power the speaker off by pulling the power cord.
- Turn it upside down (the diagnostic port facing up).
- Connect it to the computer with an adapter.
- Plug it in.
The HomePod boots into DFU.
HomePod extraction steps explained
Once you connect the HomePod to the computer, place the device into DFU as explained in the previous chapter. You can verify the device is in DFU mode by running the following optional command:
./EIFT_cmd info
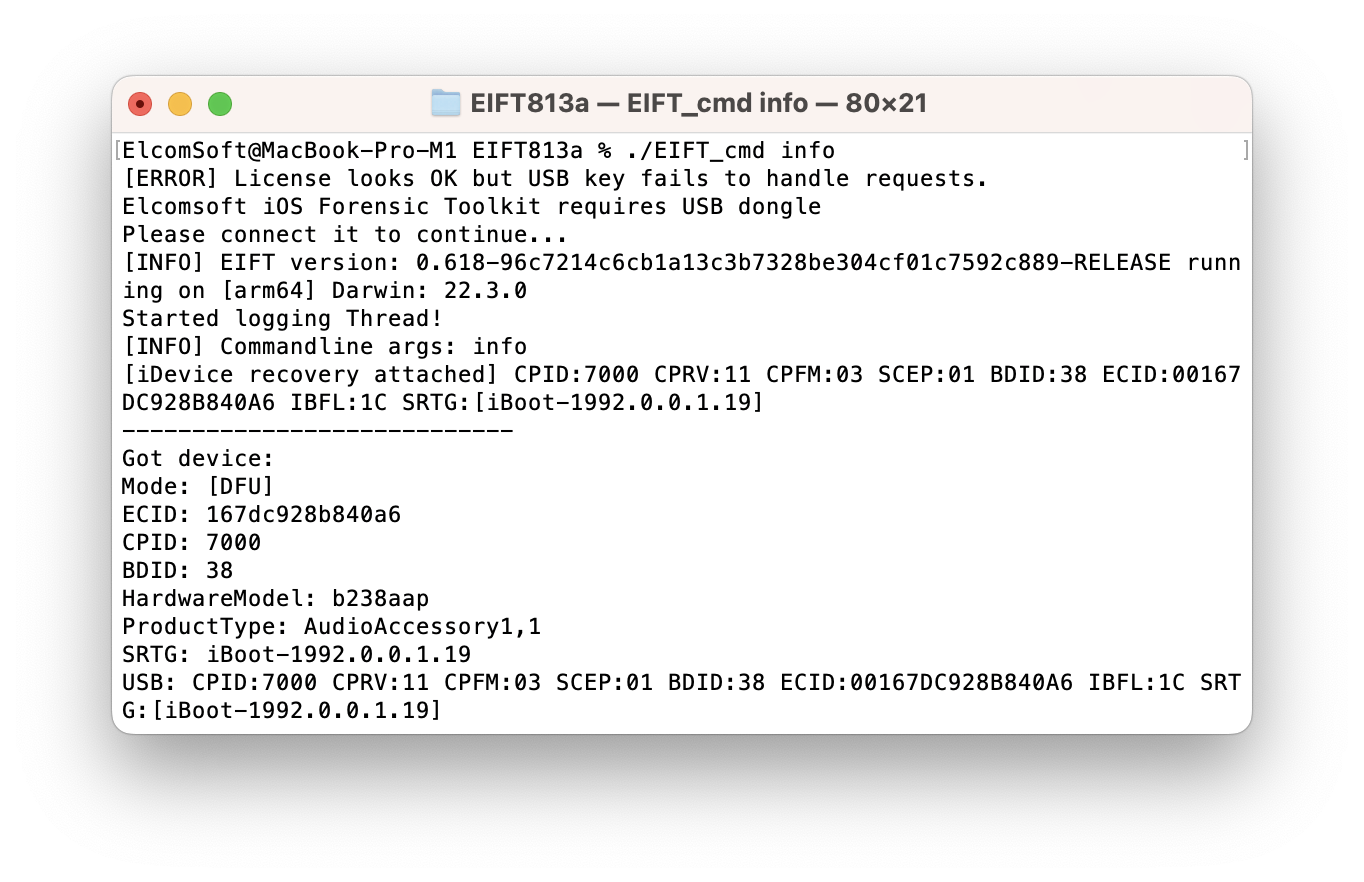
Once “Mode:” says [DFU], apply the exploit with iOS Forensic Toolkit by running the following command:
./EIFT_cmd boot
iOS Forensic Toolkit will detect the HomePod in DFU mode and automatically apply the exploit. The toolkit detects the OS version installed on the device, and provides a download link to an Apple firmware image.
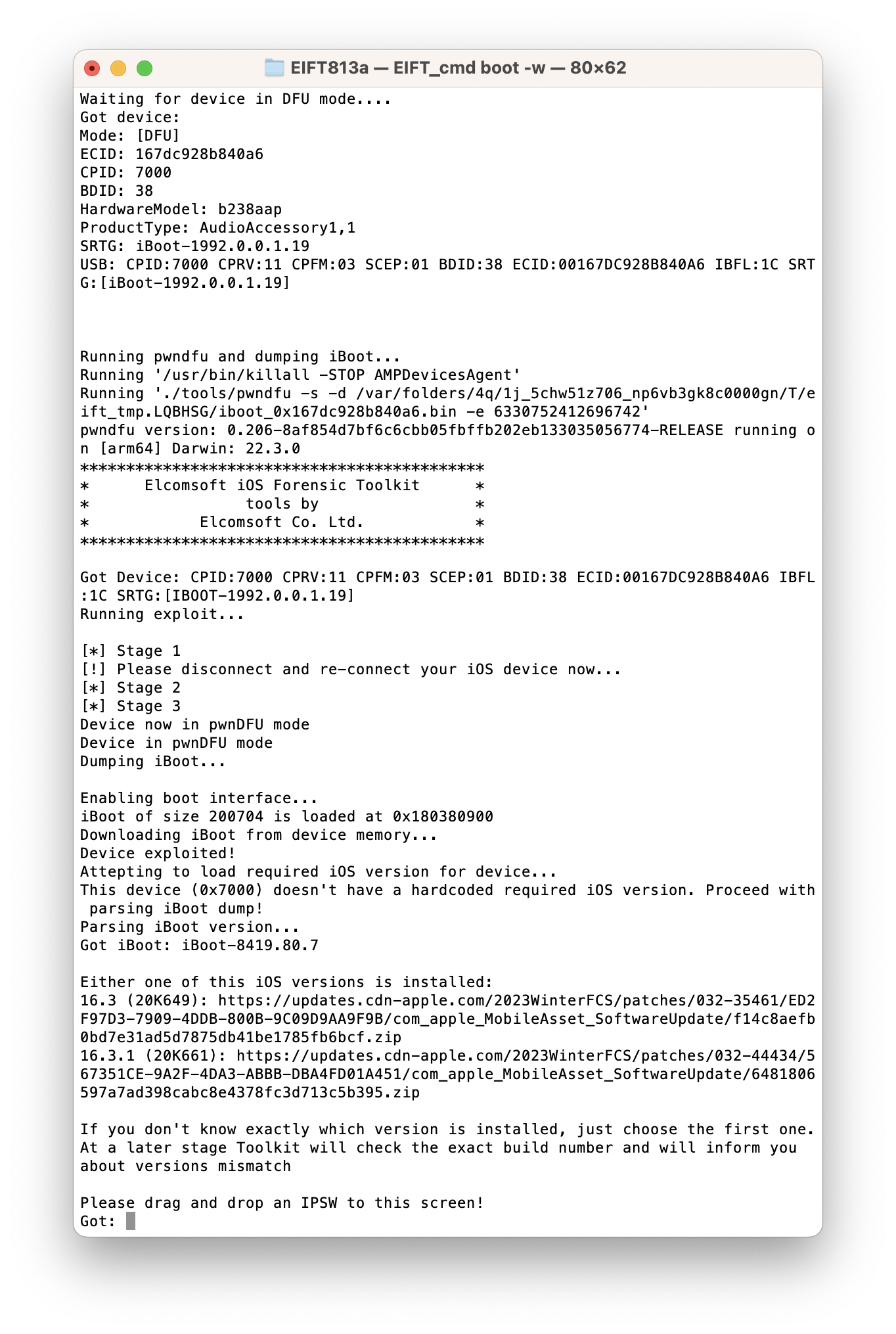
If there are multiple potential matches, several download links will be displayed. We recommend starting from the last link from the list. Please note that if a link to a wrong OS version is provided the HomePod will panic and will not boot. If this happens, try a different OS version.
Download the file from the link, and drop it onto the console window, then press ENTER. Alternatively, you can simply paste the firmware download link instead. If you do that, the tool will only download parts of the firmware image that are required to boot the HomePod.
Notably, Apple does not publish full IPSW images for HomePod devices. Our tool can use OTA update images for the purpose of applying the exploit.
In many cases, the OS version will be detected automatically by EIFT during the first stage of the exploit. The detection is based on the detected iBoot version and device hardware. However, in some cases the iBoot version may correspond to several OS builds. If the wrong build is used, you will have an option to either repeat the process with a different version of firmware, or continue with the current firmware image (which works in many cases).
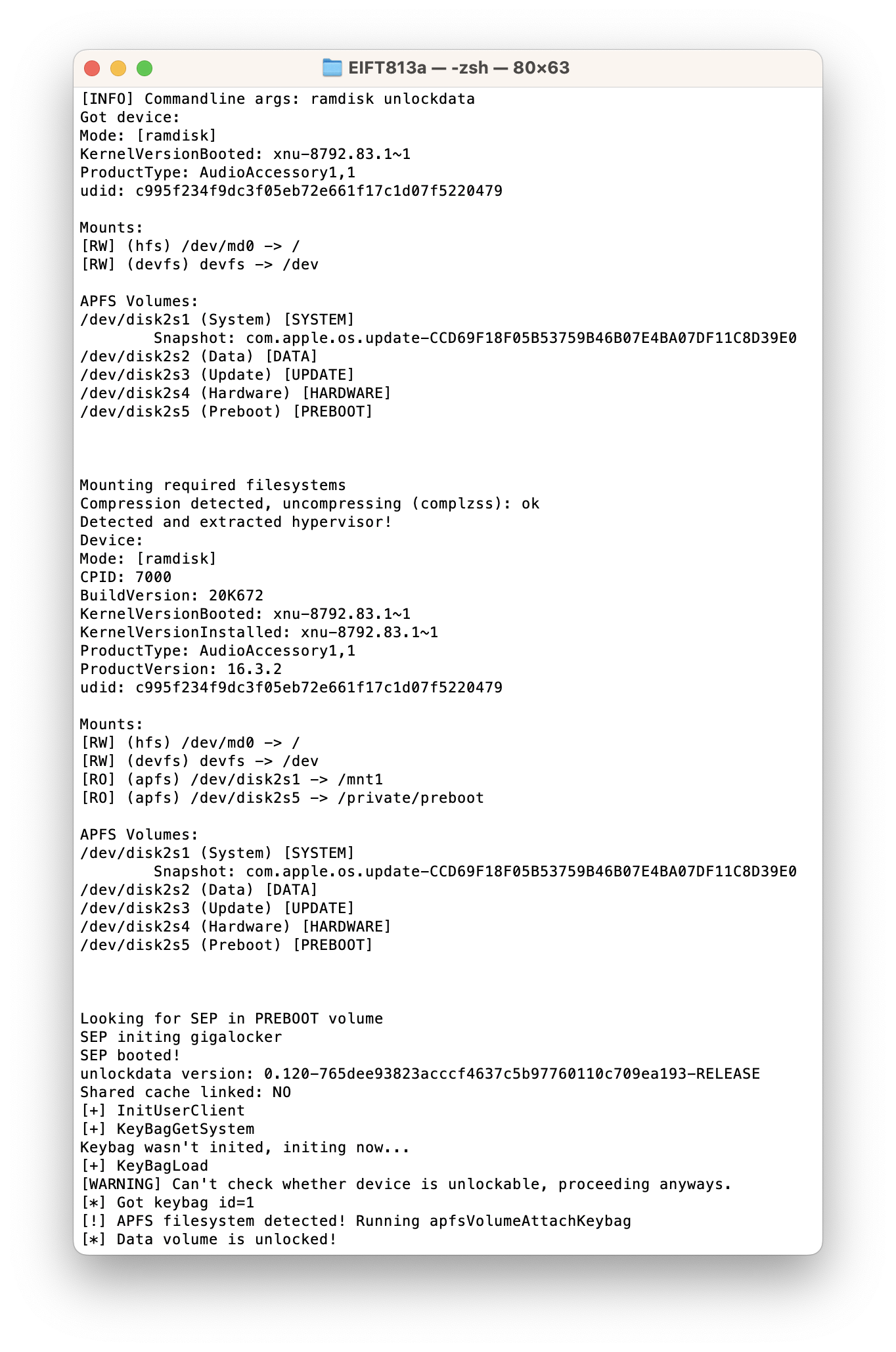
./EIFT_cmd ramdisk unlockdata
This command unlocks the data partition and mounts it read-only. Since the HomePod does not have a passcode, you will not need to provide one.
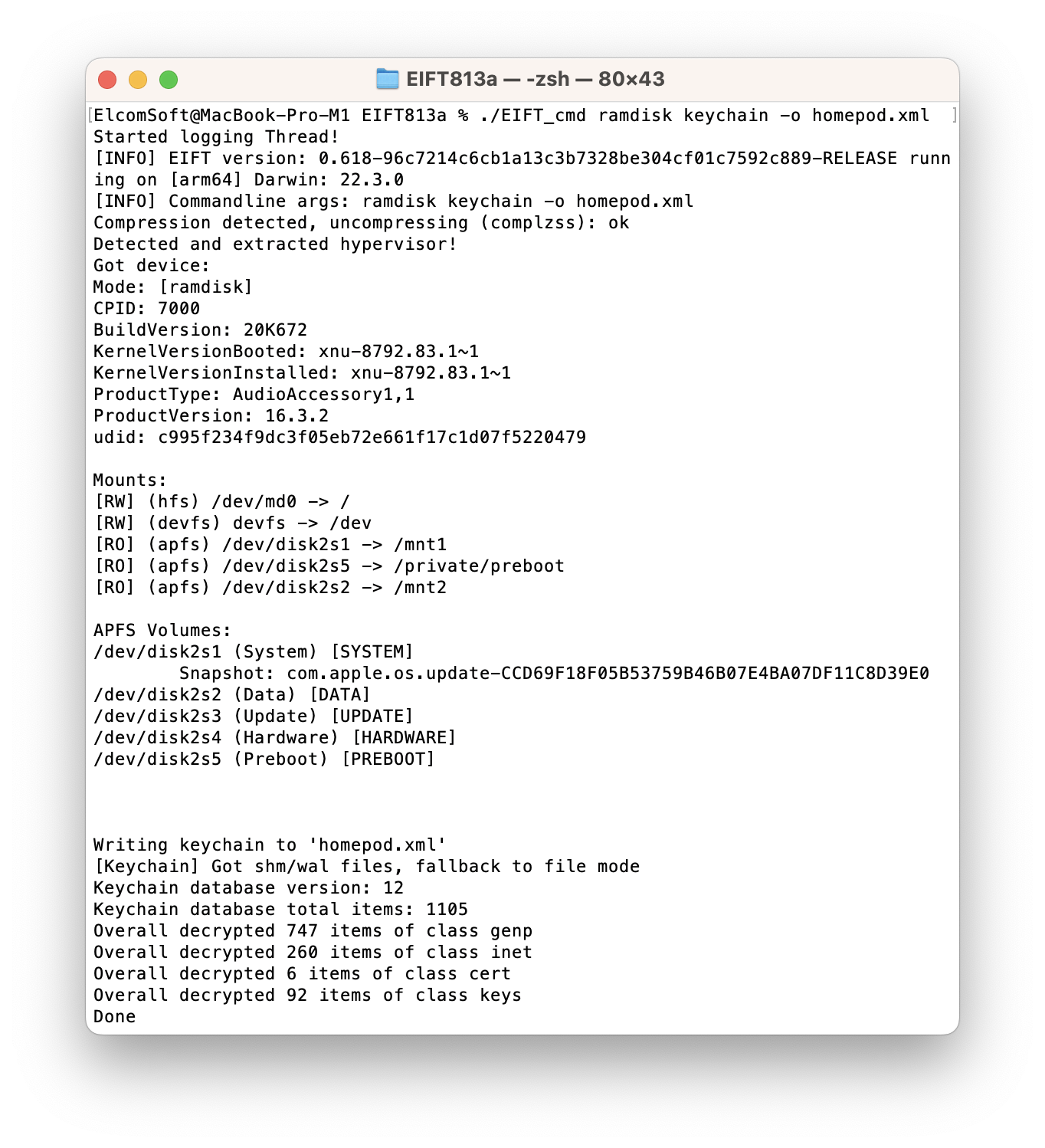
./EIFT_cmd ramdisk keychain -o {filename}
This command extracts and decrypts the keychain. If no path is specified, it will be saved into the current folder. Note that the number of keychain records extracted can be limited compared to the content of an iPhone or iPad device. Since the HomePod cannot have a passcode, the HomePod devices cannot access any end-to-end encrypted data in iCloud, which includes the iCloud keychain.
./EIFT_cmd ramdisk tar -o {filename}
This command images file system. The checksum (hash value) is calculated on the fly and displayed once the extraction is finished.
On the test device, the command dumped some 3.84 GB of data; your mileage may vary. In the next article we’ll analyze that data to see what is and what is not available.
You can power off the HomePod by either pulling the plug or running ./EIFT_cmd ssh halt first.
Conclusion
Accessing information stored in the first-generation HomePod requires a specific set of tools and steps, including the use of forensically sound checkm8 extraction and a custom USB adapter. By following the outlined steps and using iOS Forensic Toolkit 8.0, it is possible to extract the keychain and file system image from the HomePod. However, it is important to note that the amount of data that can be accessed from the HomePod may be limited compared to other Apple devices, and the HomePod cannot access any end-to-end encrypted data in iCloud. Nonetheless, this extraction method can be useful in forensic investigations and shed light on the potential data that can be obtained from HomePod devices. We strongly believe that analyzing IoT devices such as the HomePod, Apple TV, and Apple Watch is essential for investigations.







