Elcomsoft iOS Forensic Toolkit 8.20 for Mac and 7.80 for Windows now includes a new mechanism for low-level access, which enables the extraction of certain parts of the file system from the latest Apple devices. This partial extraction raises questions regarding what data can and cannot be extracted and how missing information can be accessed. Learn about the partial file system extraction, its benefits and limitations.
Introduction
With the increasing usage of mobile devices in daily lives, the need for digital forensics on these devices has also grown. One of the most commonly used mobile operating systems is Apple’s iOS. For forensic investigators, gaining access to the file system of an iOS device is crucial in order to extract relevant data for analysis. However, due to the security measures implemented by Apple, this can be a challenging task. In this article, we will explore the concept of “partial” file system extraction on iOS devices built on Apple’s latest chips. We will discuss what data can be accessed through this method, as well as what limitations exist when utilizing known vulnerabilities to gain elevated privileges and extract data from the device’s file system. Through understanding partial file system extraction, investigators can gain a better understanding of what data can and cannot be obtained from an iOS device, and how to best approach digital forensics on these devices.
Some vendors implemented support for the new exploit without fully understanding its implications, making incorrect claims about the availability of a larger data set than actually accessible. In this article, we will try to clearly demonstrate what is and what is not accessible with the new exploit.
Compatibility
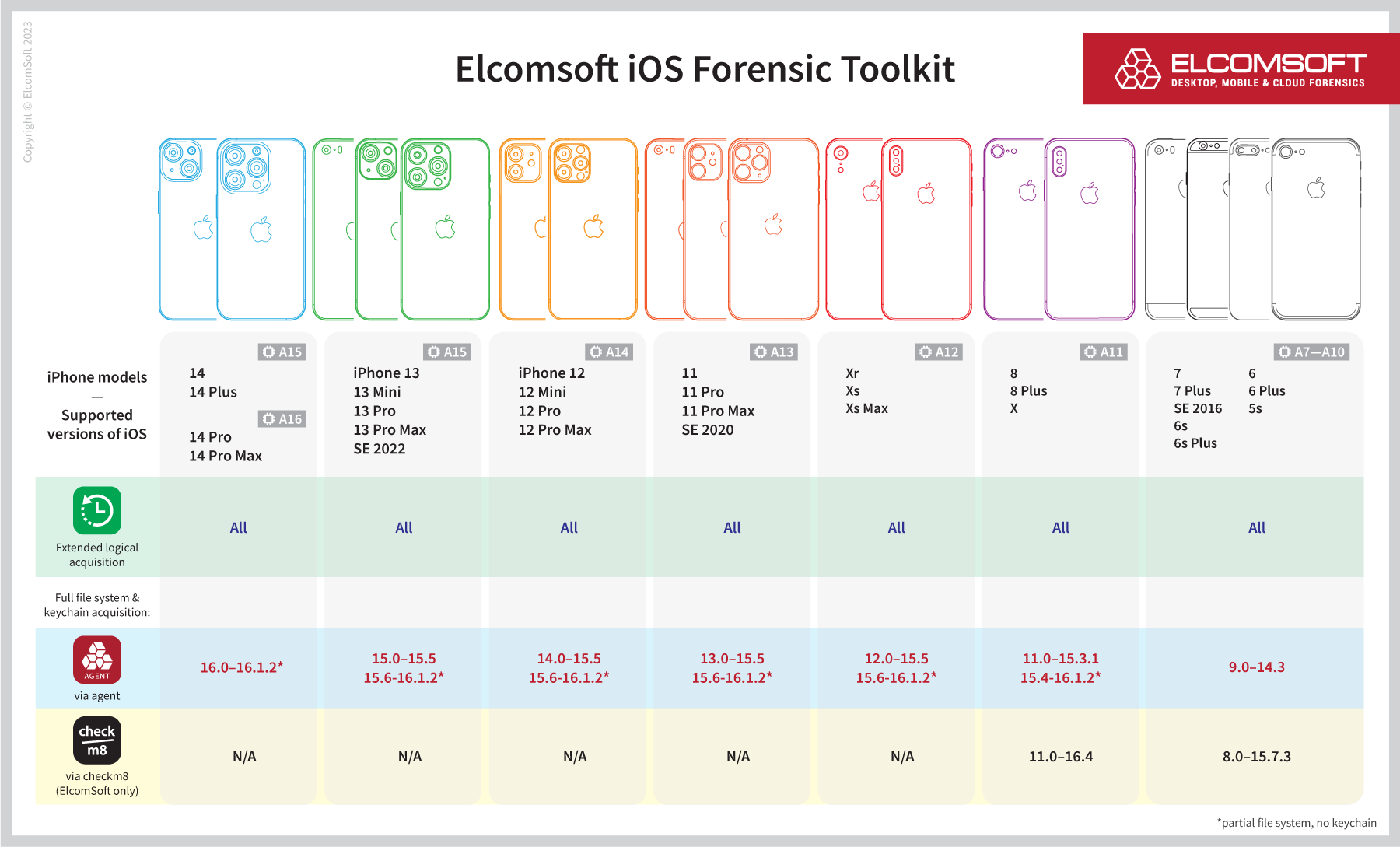
The new extraction process is supported for all current Apple devices with iOS 15.6-16.1.2 (iOS 15.4-16.1.2 on some devices). Full file system extraction with keychain is supported on older versions of iOS, while many older devices are supported via the forensically sound checkm8 extraction process. Please refer to the following image for detailed support matrix.
What is “partial” file system extraction?
iOS Forensic Toolkit includes a custom low-level extraction agent, which is an app that, when installed on an iOS device, attempts privilege escalation by trying to exploit one or more vulnerabilities in the operating system. For certain versions of iOS, kernel-level exploits are available that allow the extraction agent to break out of the “sandbox” and gain access to the full file system on the device.
The particular exploit we used in iOS 15.6-16.1.2 (iOS 15.4-16.1.2 on some devices) exploits a vulnerability in the iOS virtual memory management to escalate privileges within the sandbox. Currently, the exploit cannot fully break out of the sandbox, as some protective mechanisms that affect access to certain folders are implemented directly in the kernel. Therefore, only a part of the file system containing third-party app data is available for extraction.
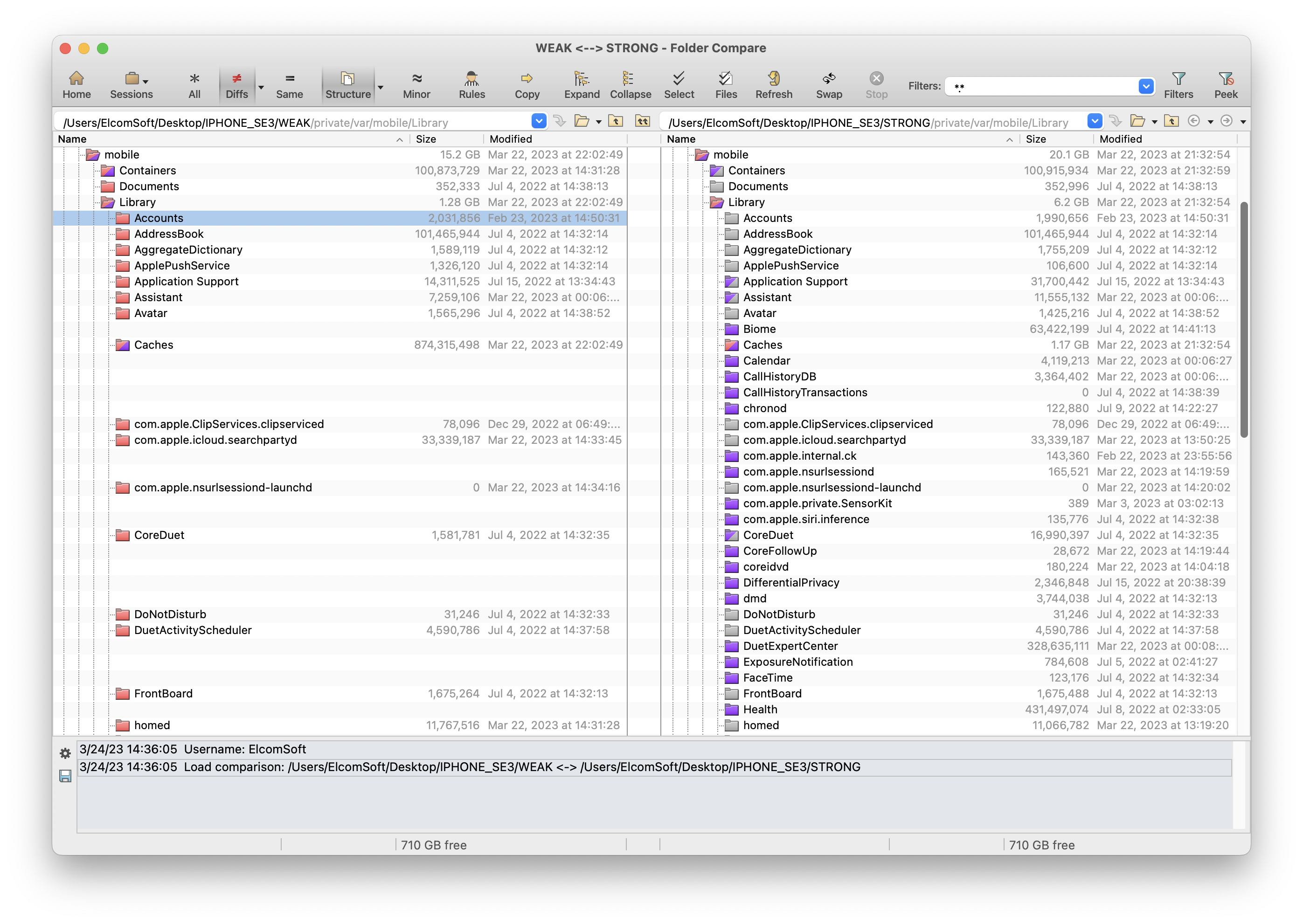
We have repeated the extraction on the same device using various extraction methods.
- Fully featured exploit (full file system): 19.9 GB
- Weak exploit (partial file system): 17.7 GB
- Local backup: 14.7 GB
The ‘partial’ file system image contains a large data set. However, the two data sets are not identical. The local backup contains some information that is not available in the partial file system image, and vice versa.
What data is available?
The available data includes chats and communication histories of third-party instant messaging apps (such as Telegram, but not iMessage, which is a built-in app), data of third-party email clients (except the built-in Mail app), and a lot more. In particular, we observed the following data extracted with the new ‘partial’ process:
- Data from Twitter, Telegram, WhatsApp, and Gmail apps
- All media files including snapshots (.ktx)
- Notes (however, only cloud notes were extracted; we haven’t seen any local notes)
- App installation logs
- Some Apple Maps data
- Known Wi-Fi networks
Some system databases extractable with the new process:
- accounts3.db (contains information about all user accounts)
- interactionC.db (lots of information to correlate contact information with application activity)
- CellularUsage.db
- DataUsage.sqlite (per app network usage stats)
- CurrentPowerlog.PLSQL (events such as app launch, lock/unlock, camera, Lightning connections etc.)
- com.apple.MobileBluetooth.ledevices.other.db (seen Bluetooth devices)
- com.apple.routined (significant locations, iOS 15 only)
What is unavailable?
Data from system and built-in apps, as well as many system databases, including the keychain, remains inaccessible. We recommend using advanced logical acquisition to access this information. Password-protected backups include both user passwords (keychain) and data from many system apps, such as Safari browsing history. Particularly missing are biome data, knowledgeC, ScreenTime data and many system databases. Location data in /private/var/mobile/Library/Caches/com.apple.routined/ and /private/var/root/Library/Caches/locationd/ is not accessible.
Compared to the full exploit, the partial extraction has some omissions:
Getting the missing data
We recommend this newly added partial file system extraction method as complimentary to advanced logical acquisition. In addition to information extracted through the advanced logical process, the new low-level extraction method pulls sandboxed data and working sets of third-party apps that do not allow their data in local backups. This includes many instant messaging apps, some third-party Web browsers and email clients, and multiple other apps. The local backup, on the other hand, will deliver information that cannot be obtained with partial file system extraction, which includes calendars, Safari browsing history, and, for password-protected backups, passwords and authentication data stored in the keychain.
The following are examples of data available with each extraction method.
Extended logical
- Calendars, notes, contacts, call history
- SMS and iMessage
- Safari history, bookmarks, tabs
- Photos and videos
- Passwords from the keychain (source: password-protected backup)
Partial file system
- Chats in third-party instant messengers (except iMessage), e.g. Telegram
- Databases of social networking apps
- Downloaded mail and other data from third-party mail clients
- Data from some third-party Web browsers
- Data from user-installed apps, which is mostly unavailable in backups
- Some system databases that are not included in backups
Extraction steps
The extraction steps for partial file system extraction differ very little compared to other agent-based extractions; the differences are around iOS 16, which requires an extra step. Please refer to the following article for details:
iOS Forensic Toolkit installation notes
- macOS: do not forget to remove the quarantine flag for v8.
- Windows: temporarily disable Windows Defender or another antivirus before installing and using the tool. Antivirus software may fire a false malware detection warning caused by the exploits implemented in the software.
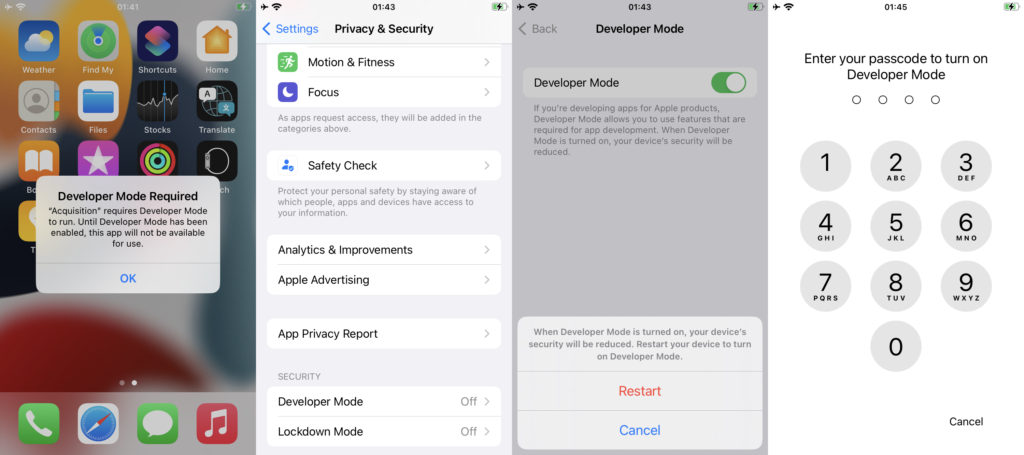
Important: When extracting iOS 16.x devices, you will need to enable Developer Mode on the device to sideload the extraction agent. The Developer Mode is available in Settings > Privacy & Security. You will need to enter the screen lock passcode to enable Developer Mode.
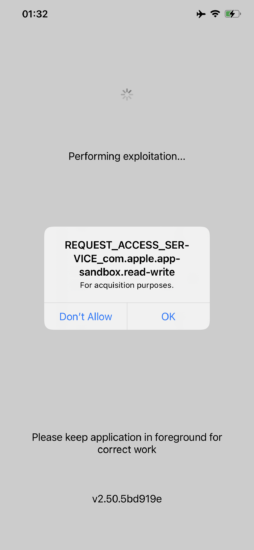
The agent prompts for additional permissions; tap OK to grant:
Note that agent-based extraction is available in both iOS Forensic Toolkit 8.20 (Mac only, command-line interface) and 7.80 (Mac and Windows, menu-driven interface).
Conclusion
The latest builds of iOS Forensic Toolkit introduced a new partial low-level extraction support for Apple devices using A11 through A16 Bionic chips, as well as iPad models based on Apple M1 and M2 chips. While this method can extract parts of the file system, including the sandboxes and working data set of third-party apps, many built-in and system apps and databases are excluded due to limitations caused by the exploit used. This newly added method is recommended as complementary to advanced logical acquisition, as it can extract information that cannot be obtained with a local backup, such as data from certain instant messengers and third-party apps. However, local backups are still necessary to obtain information like calendars, Safari browsing history, and passwords stored in the keychain. We will continue to research the vulnerability used in this release to expand the amount of extractable information.







