Last month, we introduced a new low-level mechanism, which enabled access to parts of the file system from many Apple devices. The partial extraction process relies on a weak exploit that did not allow full sandbox escape. Today, the limitations are gone, and we are proud to offer the full file system extraction and keychain decryption for the entire iOS 15 range up to and including iOS/iPadOS 15.7.2.
TL&DR
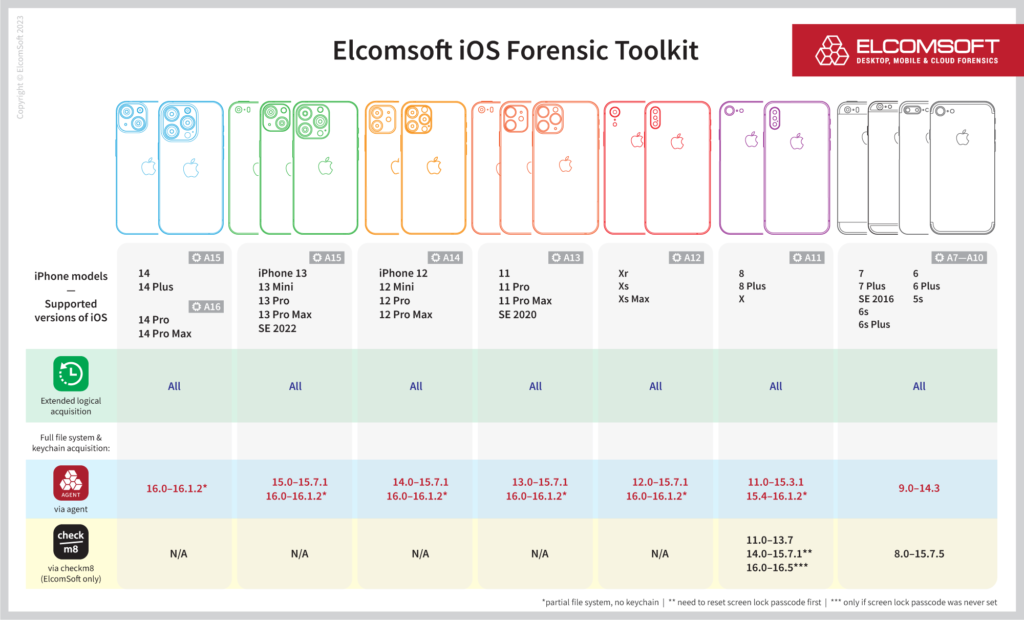
The previously announced partial file system extraction mechanism has been refined, now delivering the full file system and all keychain records for many devices running all versions of iOS 15 up to and including iOS/iPadOS 15.7.2. iPhone Xs/Xr and newer devices are supported, while older devices such as the iPhone 8/iPhone X still rely on the checkm8 extraction process (though agent extraction is also available for some versions). Devices running iOS 16.0 through 16.1.2 are still using the partial extraction process.
The updated compatibility matrix:
Before: partial file system extraction
iOS Forensic Toolkit includes a custom low-level extraction agent. Technically, the extraction agent is an app that, when installed on an iOS device, attempts privilege escalation by attempting to exploit one or more vulnerabilities in the operating system. For the most part, the exploits used in the extraction agent are kernel-level exploits allowing full sandbox escape with low-level access to the file system and keychain records.
For versions of iOS newer than iOS 15.6 no kernel exploits are currently available. Instead, we used a weak exploit that obtains higher-level privileges through a vulnerability in the iOS virtual memory management. Since this is not a proper kernel-level exploit, we’ve been unable to fully escape the sandbox, as some protective mechanisms that affect access to certain folders are implemented directly in the kernel. Therefore, we’ve only been able to access parts of the file system, mostly containing data of third-party apps.
This approach left many kinds of data out. The partial extraction process did not return data from built-in system apps and many system databases; it did not work for the keychain either. We recommended using advanced logical acquisition to access some of the missing data, and yet some bits and pieces remained unavailable even when combining the results of the partial low-level extraction process and advanced logical acquisition. Most notably this included some system artifacts and essential keys stored in the keychain such as the keys used to encrypt chat histories in protected messengers such as Signal and Wickr.
After: full file system extraction and keychain decryption
The limitations are over, at least for iOS 15. The newest release of iOS Forensic Toolkit now includes full support for all versions of iOS/iPadOS 15, which includes iOS 15.6, 15.6.1, 15.7, 15.7.1, and 15.7.2. With additional research (and some efforts) we’ve been able to fully escape the sandbox and gain access to previously inaccessible types of data, which includes the full file system and all keychain records regardless of their protection class. The latter in particular enables access to chat histories in protected messengers such as Signal and Wickr that use extra encryption to protect their working databases. The full low-level extraction closes all remaining gaps in data that were unavoidable when combining partial file system extraction with password-protected backups.
The list of supported devices includes:
- A12: iPhone Xr, iPhone Xs, iPhone Xs Max
- A13: iPhone 11, iPhone 11 Pro, iPhone 11 Pro Max, iPhone SE (2nd gen)
- A14: iPhone 12, iPhone 12 Mini, iPhone 12 Pro, iPhone 12 Pro Max
- A15: iPhone 13, iPhone 13 Mini, iPhone 13 Pro, iPhone 13 Pro Max, iPhone SE (3rd gen)
- All corresponding iPad models including iPad Air 5 and iPad Pro 5 (Apple M1)
For older devices including the iPhone X, iPhone 8 and iPhone 7 ranges we recommend using checkm8 extraction, which delivers equally strong results.



