The challenge of encrypted disks and virtual machines
One of the primary challenges in digital forensics lies in decrypting data stored on encrypted disks or containers. Encrypted disks, such as Windows BitLocker and Apple FileVault2, are designed to be resistant to “cold” attacks. Analyzing a live session before shutting down a computer can aid in extracting encryption keys, rendering lengthy brute-force attacks unnecessary. Extracting BitLocker keys can be accomplished through Windows command-line tools (assuming the account in question has administrative access to the system), while third-party disk encryption tools may be dealt with by capturing a full memory dump to locate on-the-fly encryption keys (OTFE keys) with Elcomsoft Forensic Disk Decryptor or similar tools. Shutting down the computer unmounts encrypted disks and containers and clears OTFE keys from the computer’s memory.
Virtual machines in general offer multiple benefits, and the main one is the complete isolation from the normal working environment. Virtual machines are also a tool commonly used in the criminal world. Many types of virtual machines can be securely encrypted. Using an encrypted VM gives criminals an opportunity to cover their activities under a virtual umbrella, reducing the risks of an accidental leak of incriminating evidence. Shutting down a computer prematurely can deny access to critical information stored within encrypted virtual machines.
Preserving volatile virtual machines and private chats sessions
Volatile virtual machines pose a unique challenge for investigators. Unlike their persistent counterparts, volatile VMs do not commit changes to the container, leaving the VM image file unaltered and potentially void of incriminating evidence. By shutting down a computer hosting a volatile VM, investigators risk losing vital changes and activity history within the VM.
In a fashion similar to encrypted VMs, certain instant messaging applications employ volatile private chat sessions, where all data resides solely in the computer’s RAM instead of being stored in a database on the disk. Powering off the computer erases all traces of these confidential communications.
The issue of plausible deniability in hidden containers
Hidden containers, an integral part of modern disk encryption techniques, are designed to provide users with the shield of plausible deniability. Without knowledge of the correct password and encryption settings, access to hidden containers becomes impossible, making their content and even existence unprovable.
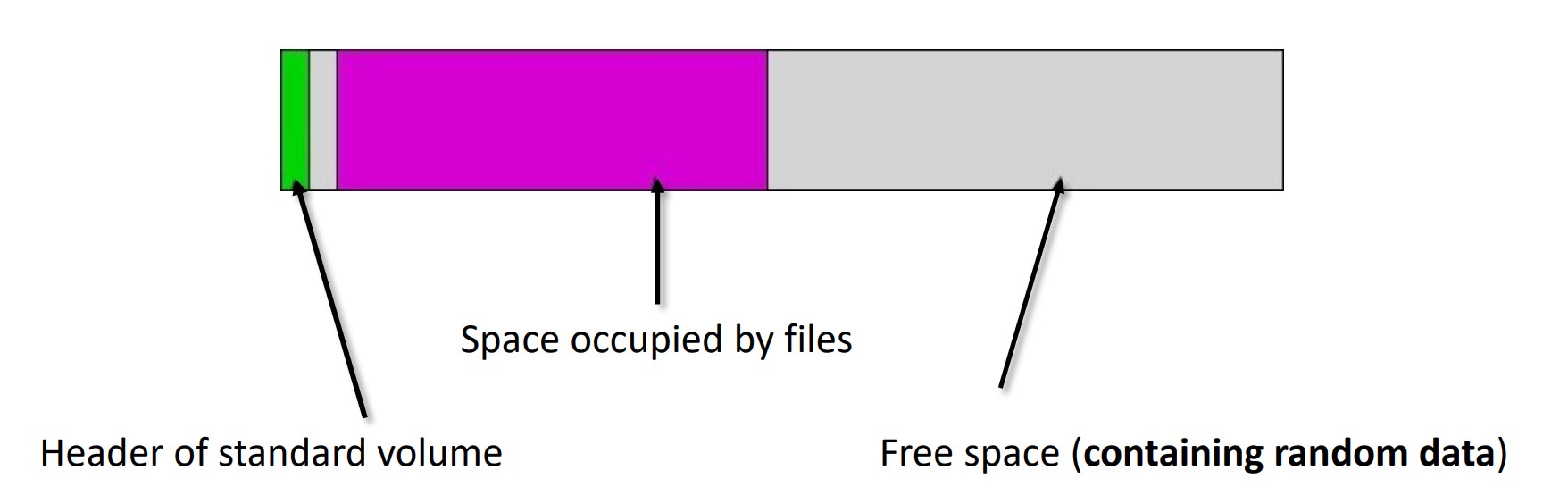
Figure 1: VeraCrypt standard encrypted container. A password unlocks and mounts the encrypted volume. Unless the container is stored on an SSD drive with trim passthrough, distinguishing between encrypted data and random data is impossible.
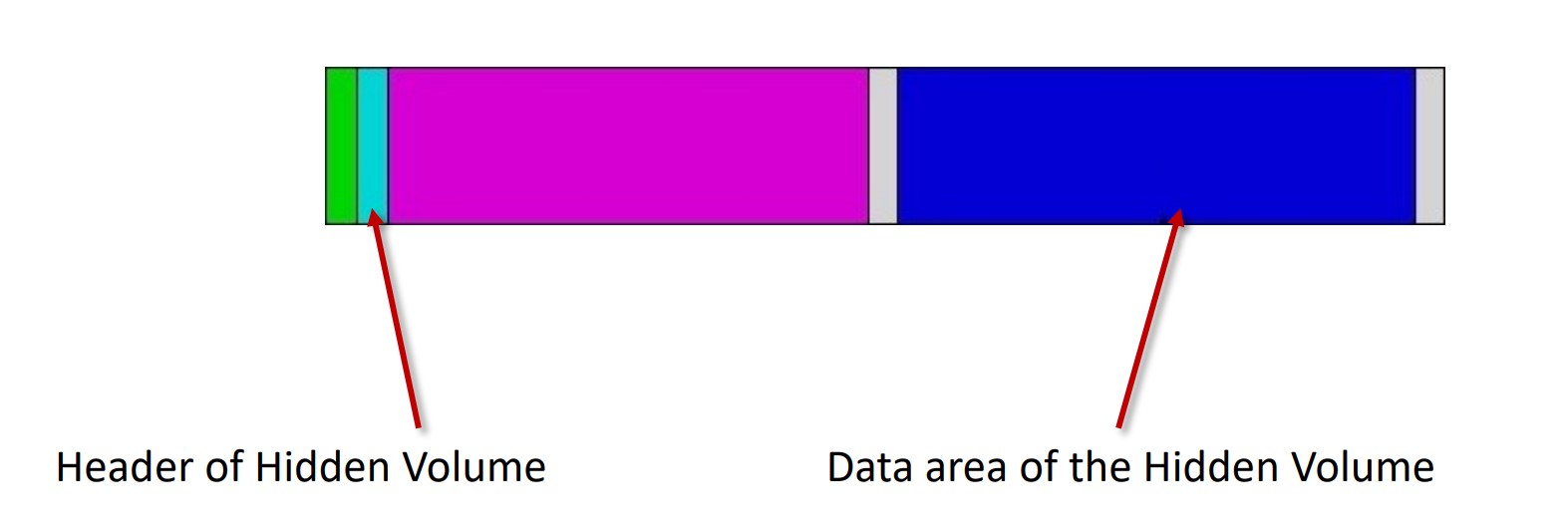
Figure 2: VeraCrypt hidden container. One password unlocks and mounts the standard encrypted volume, while a different password must be used to unlock and mount the hidden volume.
The essence of hidden crypto containers lies in their ability to camouflage sensitive data within the main encrypted storage container. The main and hidden containers use different passwords, and may even use different encryption settings. The perpetrator may give out a password to the main container, leaving forensic experts in a situation where incriminating evidence becomes not only inaccessible but even its existence transforms into an unprovable uncertainty.
Conclusion
Securing access to crucial digital evidence poses a challenge. In the world of digital forensics, the right handling of digital evidence can make all the difference. By adhering to proper preservation steps, investigators can avoid the loss of vital evidence stored in encrypted disks, virtual machines, private chats, hidden containers, and more.