Acquiring data from Apple devices, specifically those not susceptible to bootloader exploits (A12 Bionic chips and newer), requires the use of agent-based extraction. This method allows forensic experts to obtain the complete file system from the device, maximizing the amount of data and evidence they can gather using the iOS Forensic Toolkit. In this article, we will discuss some nuances of agent-based iOS device acquisition.
Please note: for technical reasons, support for iOS 9 through 11 was removed from recent versions of the extraction agent. From now on, the earliest version of iOS supported by the extraction agent is iOS 12. For this reason, if you need to extract a device running an earlier version of iOS than iOS 12, you’ll have to use iOS Forensic Toolkit 8.23 or 7.81.
How does it work?
Technically speaking, agent-based extraction involves gaining extended (usually root) privileges and bypassing the device’s sandbox restrictions. This enables access to the data in all the folders, and allows experts accessing all the files on the device, as well as the keychain. However, this process is far from simple. Apple iOS employs multiple layers of protection, making it challenging to breach. Mere kernel read/write access is insufficient; several exploits (a chain of exploits) are necessary to achieve the desired outcome.
The first step in the process is to install our app, known as the Agent, onto the target iPhone. However, this task presents a considerable challenge. But first let’s briefly explore the concept of sideloading.
What is sideloading?
Sideloading refers to the installation of apps on a device through methods other than the official App Store. This method involves using tools like Apple’s own Xcode or a third-party app, or utilizing an unofficial signing service (mostly using leaked enterprise certificates) directly on the device. To sideload an app on devices running iOS 16, users must enable Developer Mode in the device settings beforehand. Older versions of iOS do not require a special mode to sideload. Generally, Apple does not support sideloading, except for internal app testing and development using the official SDK. Official sideloading support might be coming to iOS 17 in conformance with the new EU directive, yet at this time we don’t know much about it.
After sideloading the app onto the device using a non-developer account, one must navigate to Settings > General > Device Management and trust the developer certificate associated with the sideloaded app. The certificate will be validated through ppq.apple.com. This additional step is required to allow the device recognize the app and allow it to run. This requires allowing the device to connect to an Apple server, which in turn has certain forensic consequences. There are several ways to solve this issue, one of which is using an Apple account enrolled into the Developer Program, and another using a software or hardware firewall to restrict device connectivity.
The importance of Apple ID
If the device is not jailbroken (we can safely assume it is not), sideloading the agent requires an Apple ID. No alternative methods exist. Whether you possess an Apple Developer account or not determines the approach you can take, and this distinction is crucial. Non-developers can sideload apps onto iOS devices only from macOS, but it necessitates bringing the device online, which poses certain risks (explained below).
Apple Developer accounts
Having an aged Apple Developer account is ideal for our purposes. With this type of account, sideloading the agent, or any other app, becomes a straightforward process. Furthermore, it is important to note that with iOS 15 and 16, sideloaded apps need additional verification during the first run, and presently, no workarounds exist for this limitation. However, if the account was registered prior to June 6, 2021, there is no requirement to bring the device online when launching the app for the first time (which only applies to devices running iOS 15 and 16 anyway). The request is processed through humb.apple.com.
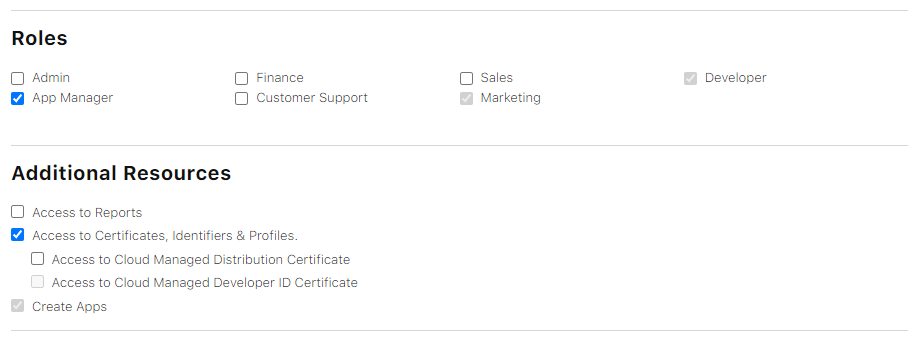
For those using a corporate developer account rather than a personal one, keep in mind that Developer privileges alone are insufficient to sideload apps; App Manager privileges are also necessary.
An Apple Developer account allows you to sideload an app on up to 100 devices of each type (iPhone and iPad, in our case) per year. Nevertheless, there is a catch. After the tenth device, a delay of up to 72 hours occurs before adding a new device to the account and permitting app sideloading. The reasoning behind this limitation remains unknown, and it is highly unlikely that it is an anti-forensic measure.
Regular accounts
Regular, non-developer accounts can also be utilized for sideloading the agent (macOS only). However, it is important to have a trusted device connected to the account. Nonetheless, this is not the only obstacle. The main challenge lies in the requirement to verify the app’s certificate online from the device. The risks associated with allowing the device to access the internet are evident: it may actively sync and may be subject to remote lock/wipe commands.
Signing an app using a non-developer account also has a limitation: a maximum of three devices per week. Of course, you can create a new Apple ID, but remember to have a trusted device associated with it.
A brief note on firewalls
What should you do if the agent’s certificate needs verification or if the agent attempts to connect to the internet during its initial run? Solutions do exist:
The hardware-based solution is more robust, but requires additional hardware (Raspberry Pi or Orange Pi), adapters and cables. However, it is essential to note that these solutions are not foolproof, as Apple may modify the app verification process at any time.
Conclusion
If you possess an Apple Developer account created before June 2021, congratulations! You have an easier path ahead. Otherwise, paid accounts may not be worth the investment (unless you’re using Windows) since you will still need to bring the device online. However, rest assured, we have a solution to address this hurdle.



